Configuring LDAP authentication
Kaspersky CyberTrace supports LDAP user authentication to allow logging in as a domain user. This section explains how to configure this type of authentication by using Kaspersky CyberTrace Web.
Kaspersky CyberTrace supports the use of Active Directory only if the domain controller is running Windows. The use of Active Directory with Linux-based domain controllers is possible, but not guaranteed.
The LDAP section allows you to perform the following actions:
- Enable LDAP authentication
- Test the connection to the LDAP server
- Specify connection settings
- Configure accounts filtering
Enabling LDAP authentication
To enable LDAP authentication,
Click the LDAP auth enabled toggle button.
The LDAP server will now be used for user authentication.
When LDAP authentication is enabled, you still can interact with Kaspersky CyberTrace under a local user account.
Testing the connection to the LDAP server
Go through the procedure below to make sure that a connection to the LDAP server is established.
To test the connection to the LDAP server:
- Click the Test connection with LDAP link.
The Test connection with LDAP window opens.
- Specify the following settings:
- User name for test connection
- User password for test connection
- Click Test.
A connection test can be performed only if you specified all the necessary settings for connecting to the server.
Connection settings
In the Connection settings section of the LDAP tab, you can specify the following settings:
- IP address or FQDN (fully qualified domain name) and port of the LDAP server
This setting is stored in the
AuthenticationServer > ConnectionStringelement of the kl_feed_service.conf file. - SSL-secured connection
You can enable the use of a secure connection to the LDAP server by using Kaspersky CyberTrace Web.
This setting is stored in the
useEncryptionattribute of theAuthenticationServer > ConnectionStringelement of the kl_feed_service.conf file.On Linux, if secure connection is enabled, Kaspersky CyberTrace uses certificates from
/etc/ssl/certsto authenticate the LDAP server. - Path to the LDAP database
The path to the database containing user accounts that can access Kaspersky CyberTrace.
Accounts filtering
The Accounts filtering section contains filtering rules for administrator and analyst accounts.
You can configure the following properties:
- Account format
You can select one of two formats:
- User Principal Name
If this option is selected, users must provide a user name that is not an email address when performing authentication (for example user, but not user@domain.com).
- SAM Account Name
If this option is selected, users must provide a user name in the following format when performing authentication: Domain\User.
- User Principal Name
- Administrator accounts filter
The filter for LDAP user accounts that defines which users must be assigned the Administrator role depending on their common name in Active Directory.
If this value is not specified, all users who login using LDAP authentication and pass the analyst account filter will be assigned the Analyst role.
This setting is stored in the
AuthenticationServers > AdministratorAccountsFilterelement of the kl_feed_service.conf file. - Analyst account filter
The filter for LDAP user accounts that defines which users must be assigned the Analyst role depending on their common name in Active Directory.
If this value is not specified, all users who login using LDAP authentication and do not pass the administrator account filter will be assigned the Analyst role.
This setting is stored in the
AuthenticationServers > AnalystAccountsFilterelement of the kl_feed_service.conf file.As an example, in the figure below the filters are configured so that the users who are members of the
Adminsgroup will be assigned the Administrator role, and the users who are members of either theOperatorsor theAnalystsgroup will be assigned the Analyst role.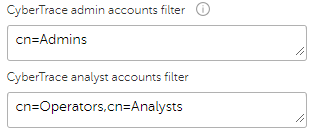
Example of accounts filters
If the AdministratorAccountsFilter and AnalystAccountsFilter elements of the kl_feed_service.conf file contain values, and the user that is trying to log in is not included in any of the specified groups, Kaspersky CyberTrace will return an error and deny access to the web user interface for this user.