Step 4 (optional). Importing Feed Service rules to RSA NetWitness
The Kaspersky CyberTrace distribution kit contains the CyberTrace_Rules.zip file in the integration/rsa/additional_elements directory. This file contains a set of rules, which you can use to create reports, alerts, and dashboards.
To import the Feed Service rules to RSA NetWitness:
- On the RSA NetWitness menu, select Dashboard > Reports.
In RSA NetWitness 11, you select Monitor > Reports instead.
- Click the Settings split button (
 ) and select Import.
) and select Import.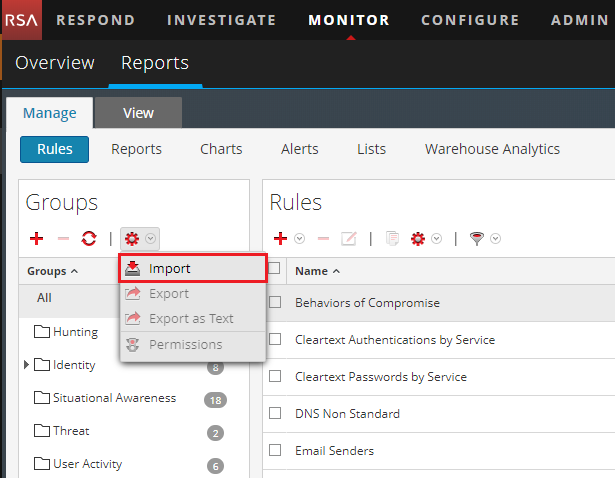
Importing rules
- Choose the CyberTrace_Rules.zip file.
- In the Import Rule window, select the Rule check box and the List check box.
If you import the CyberTrace_Rules.zip file for the first time, you may leave these check boxes cleared.
- Click the Import button.
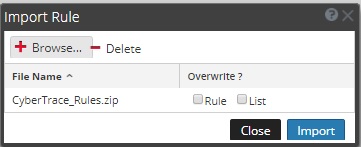
Importing Feed Service rules
The rules imported to RSA NetWitness are listed in the table below.
Rule |
Description |
CyberTrace Detect Botnet |
Selects those detection events from Feed Service that have the Botnet category. The following fields are selected:
|
CyberTrace Detect Malware Hash |
Selects hash detection events from Feed Service. The following fields are selected:
|
CyberTrace Detect Malware IP |
Selects IP address detection events from Feed Service. The following fields are selected:
|
CyberTrace Detect Malware URL |
Selects URL detection events from Feed Service. The following fields are selected:
|
CyberTrace Detect Stat |
Selects all the categories involved in the detection process. The following fields are selected:
|
CyberTrace Service events |
Selects service events from Feed Service. The following fields are selected:
|
CyberTrace Top 10 IP |
Selects Top 10 detected IP addresses. The following fields are selected:
|
CyberTrace Top 10 URL |
Selects Top 10 detected URLs. The following fields are selected:
|
CyberTrace Top 10 Hash |
Selects Top 10 detected hashes. The following fields are selected:
|
CyberTrace Detected users |
Calculates the number of detection events per user. |