RSA NetWitness troubleshooting
This section lists actions that you can undertake and problems that you might encounter while integrating Kaspersky CyberTrace with RSA NetWitness.
If you encounter a problem while using Kaspersky CyberTrace, the specialists at Kaspersky can assist you. Contact your technical account manager (TAM) for more information about solutions to problems.
Checking whether events arrive from RSA NetWitness at Feed Service
There are several ways to check whether RSA NetWitness sends events to Feed Service:
- You can check whether the Feed Service log files contain messages about arriving of events from RSA NetWitness.
In this case the Feed Service logging configuration file (
bin/kl_feed_service_log.conf) must contain thedbgstring in theWriteLogelement. - You can use the netcat utility to send events from the computer on which RSA NetWitness is installed and then check whether the corresponding messages are added to the Feed Service log files.
- You can stop Feed Service and use the netcat utility to listen for events from RSA NetWitness by running the following command:
nc -l -p [port] -s [IP]Here
[IP]and[port]are the IP address and port to which RSA NetWitness sends events for Feed Service. - You can use the tcpdump utility to listen on the port where events from RSA NetWitness must arrive.
The tcpdump utility listens on port
[port]if you run the utility by using the following command:tcpdump -neX port [port]Note that the tcpdump utility may use a different flag (not
-neX) depending on the operating system it runs on.
If no event arrives from RSA NetWitness, check the following:
- Check whether all steps listed in section "Forwarding events from RSA NetWitness" are performed correctly.
- Check whether the events arrive at RSA NetWitness from the source device.
You can check it in the same way as you check whether RSA NetWitness sends events to Feed Service.
- Check that the computer on which Feed Service is installed is accessible from the computer on which RSA NetWitness is installed.
You can check it by using the ping utility.
Checking whether Feed Service matches events against Kaspersky Threat Data Feeds
Use the Feed Service log files to check whether the URL fields, hash fields, and IP address fields of events are matched against Kaspersky Threat Data Feeds. The log files must contain messages like those provided in the following example.
|
If there are no such messages in the log files, check whether the Feed Service configuration file contains the correct regular expressions. You can also check the used regular expressions by using Kaspersky CyberTrace Web.
Checking whether Feed Service sends events to RSA NetWitness
You can check whether Feed Service sends events to RSA NetWitness in the following ways:
- By consulting Feed Service log files.
Following is an example of messages written to the log when an event is successfully sent to RSA NetWitness.
|
Following is an example of a message written to the log when an event could not be sent to RSA NetWitness.
2020/05/20 17:09:12.987 DBG 26341 siem Failed to send notification KL_ALERT_FailedToUpdateFeed (error: 0x80000072 (Unknown exception)) |
- By using the tcpdump utility on the computer that receives events from Feed Service.
The tcpdump utility listens on the IP address
[IP]and port514if you run the utility by using the following command:tcpdump -neX src [IP] and port 514In this command specify the IP address at which Feed Service sends events.
Note that the tcpdump utility may use a different flag (not
-neX) depending on the operating system it runs on.
If Feed Service sends no event, check the following:
- Check that the Feed Service log files contain messages about detecting URLs, hashes, or IP addresses.
If there are no such messages, see the information in subsection "Checking whether Feed Service matches events against Kaspersky Threat Data Feeds". It may also be that the feeds do not contain checked URLs, hashes, and IP addresses.
- Check that the Feed Service configuration file contains the correct destination IP address and port.
Problem: RSA NetWitness does not display events from Feed Service
If RSA NetWitness displays no events from Feed Service, check whether the procedure in section "Step 2. Sending events from Feed Service to RSA NetWitness" is performed correctly.
Note that RSA NetWitness may display events from a device with a delay of 10 minutes.
Problem: The configurator displays an error message when the IP address and port of Log Decoder are specified in the OutputSettings > ConnectionString setting.
An error message like the following can be displayed:
Can't connect using the specified string. Press [Enter] to specify another string, or type "ok" to continue with 10.10.0.127:514
Check that the computer on which RSA NetWitness is installed is accessible from the computer on which Feed Service is installed (for example, by using the ping utility).
Problem: Some fields of events from Feed Service are not displayed in the metafields in RSA NetWitness
If some fields of events from Feed Service are not displayed in the metafields in RSA NetWitness, do the following:
- Check whether the metafields mentioned in the v20_cybertracemsg.xml configuration file have their
flagsparameter set toNonein the/etc/netwitness/ng/envision/etc/table-map-custom.xmlconfiguration file.If these fields are absent from table-map-custom.xml, add them as follows:
<mapping envisionName="url" nwName="url" flags="None" format="Text" envisionDisplayName="URL"/> - Check whether all the fields described in section "Forwarding events from Feed Service to RSA NetWitness" are contained in the following configuration files:
- index-logdecoder-custom.xml (if you do not use Concentrator)
- index-concentrator-custom.xml
You can browse the contents of these files by selecting Administration > Services. Then select Concentrator (or Log Decoder), click the Settings split button (
 ), and select View > Config > Files. A drop-down list is displayed that contains all these files.
), and select View > Config > Files. A drop-down list is displayed that contains all these files.After you have edited the files, restart Log Decoder or Concentrator so that the new settings will be in place.
Update only the configuration file of Concentrator (index-concentrator-custom.xml) if both Log Decoder and Concentrator are used, Concentrator receives data from Log Decoder, and Log Decoder receives events from Feed Service. Also, you can leave the configuration file of Log Decoder (index-logdecoder-custom.xml) unchanged if you do not use Log Decoder as the source of data in which you search for events or if you do not use Log Decoder to create reports or dashboards.
If the configuration files do not contain necessary fields, add these fields as described at https://community.rsa.com/docs/DOC-41760. For example, the index-concentrator-custom.xml file must contain the following lines:
<key description="virusName" format="Text" level="IndexValues" name="virusname" defaultAction="Open" />
<key description="user.src" format="Text" level="IndexValues" name="user.src" defaultAction="Open" />
<key description="ip.src" format="IPv4" level="IndexValues" name="ip.src" defaultAction="Open"/>
<key description="action" format="Text" level="IndexValues" name="action" defaultAction="Open" />
<key description="msg" format="Text" level="IndexKeys" name="msg" defaultAction="Open" />
<key description="event.source" format="Text" level="IndexValues" name="event.source" defaultAction="Open" />
<key description="device.ip" format="IPv4" level="IndexValues" name="ip.dst" defaultAction="Open"/>
<key description="ip.dst" format="IPv4" level="IndexValues" name="ip.dst" defaultAction="Open"/>
<key description="url" format="Text" level="IndexValues" name="url" defaultAction="Open"/>
<key description="checksum" format="Text" level="IndexValues" name="checksum" defaultAction="Open"/>
Make sure that the values of the name and format fields in the configuration files are equal to the values of the nwName and format fields, respectively, in the table-map-custom.xml file.
Problem: After the Kaspersky CyberTrace dashboard is imported, no data is displayed
A dashlet displays an error message instead.
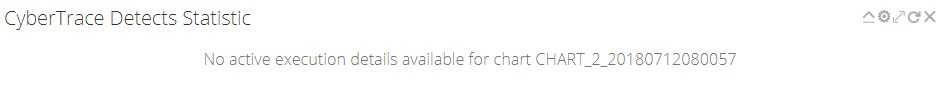
Dashlet displays no data
To fix this error, reconfigure the dashlet as follows:
- In the top right area of the dashlet, click the Settings button.
The Settings button
The Options window opens.
- Click Browse.
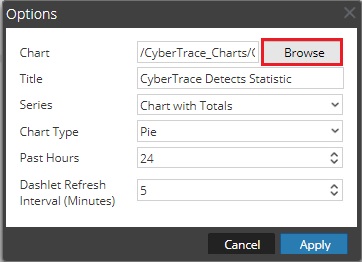
Dashlet parameters
The Select Chart window opens.
- Select the chart to be used in the dashlet.
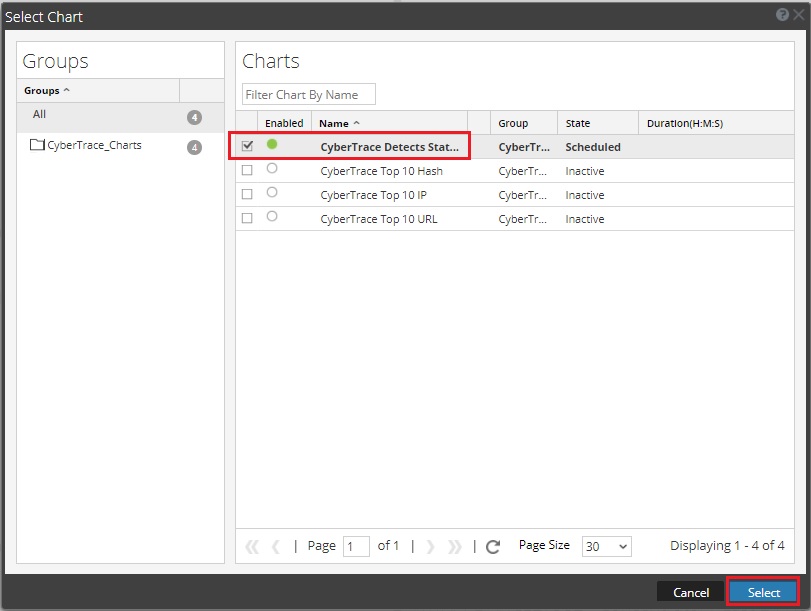
Selecting a chart
- Click Apply.
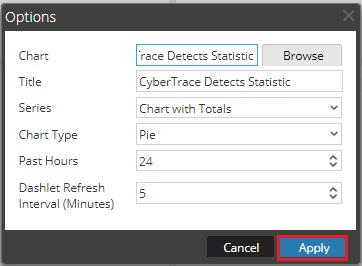
The Apply button
Problem: Feed Utility displays the "peer certificate cannot be authenticated with given CA certificates" error message
The certificate cannot be authenticated. Make sure that root certificates are installed on your system. If root certificates are not installed, install them using a standard procedure for installing root certificates on your operating system.
Page top