Contents
- Integration with LogRhythm
- Step 1. Adding a Custom Log Source type
- Step 2. Importing Kaspersky CyberTrace rules and events
- Step 3 (optional). Adding Kaspersky CyberTrace events
- Step 4 (optional). Adding Kaspersky CyberTrace rules
- Step 5. Adding Kaspersky CyberTrace policy
- Step 6. Adding a log source to System Monitor Agent
- Step 7. Configuring log forwarding to Kaspersky CyberTrace
- Step 8 (optional). Performing the verification test
- Step 9 (optional). Creating alerts about incoming Kaspersky CyberTrace service events
- Step 10 (optional). Displaying alert events in LogRhythm
Integration with LogRhythm
This chapter describes how to integrate Kaspersky CyberTrace with LogRhythm.
The actions described in these sections must be performed in LogRhythm Console under a user account that has administrator privileges.
To integrate LogRhythm with Kaspersky CyberTrace:
- Add the Kaspersky CyberTrace log source type to LogRhythm.
- Import files with Kaspersky CyberTrace rules.
- Optionally, add Kaspersky CyberTrace events to LogRhythm.
- Optionally, add Kaspersky CyberTrace rules to LogRhythm.
- Add a Kaspersky CyberTrace policy to LogRhythm.
- Accept the Kaspersky CyberTrace log source in LogRhythm.
- Configure LogRhythm to forward logs to Kaspersky CyberTrace.
- Optionally, perform the verification test.
- Optionally, create alerts about incoming Kaspersky CyberTrace service events.
- Optionally, configure LogRhythm to display alert events.
Step 1. Adding a Custom Log Source type
This section describes how you can add the Kaspersky CyberTrace log source type to LogRhythm.
To add the Kaspersky CyberTrace log source type to LogRhythm:
- Run LogRhythm Console.
- Select Deployment Manager > Tools > Knowledge > Log Source Type Manager.
The Log Source Type Manager window opens.
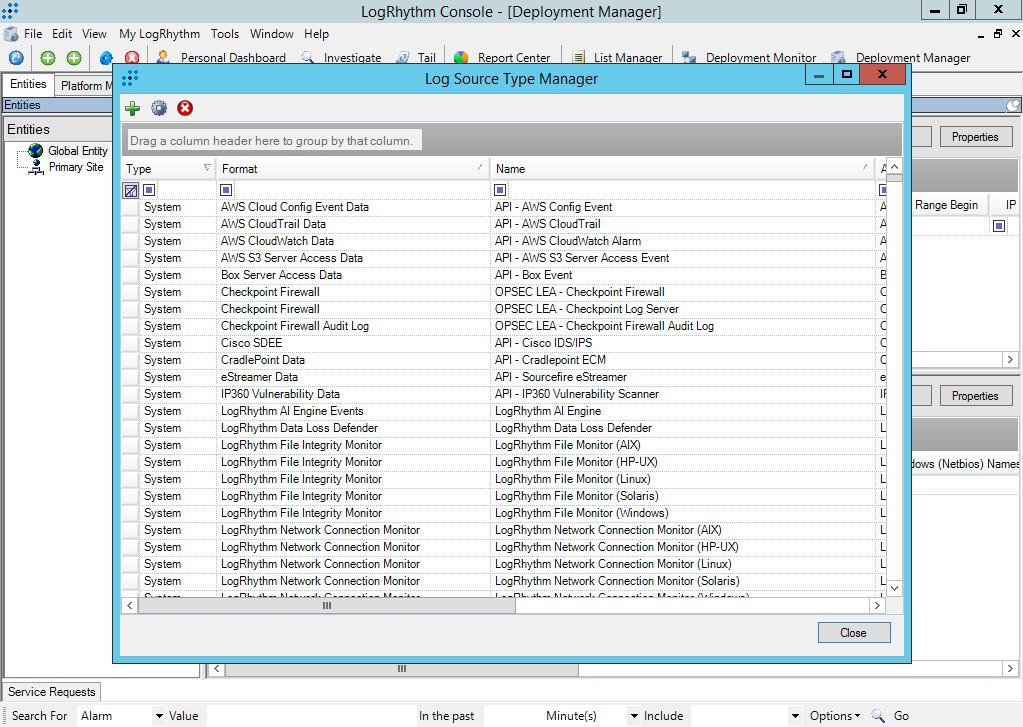
Log Source Type Manager window
- Click the New button (
 ).
). - In the Log Source Type Properties window that opens, enter the following data:
Field
Data
Name
Kaspersky CyberTrace
Full Name
Kaspersky CyberTrace
Abbreviation
CyberTrace
Log Format
Syslog
Brief Description
Kaspersky CyberTrace is an application set that allows you to check URLs, IP addresses, and hashes of files contained in events that arrive in a SIEM software product.
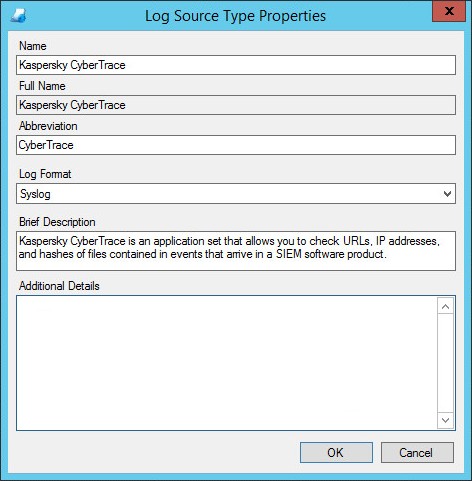
Log Source Type Properties window
We recommend specifying a source name as well as in the Name field from the table above. Otherwise, importing Kaspersky CyberTrace rules and events will be performed incorrectly. In this case, you must add Kaspersky CyberTrace events and corresponding MPE rules manually, as described in step 3 and step 4 (make sure to specify the log source name similar to the name that you entered in the Log Source Type Properties window).
- Click OK.
The new log source type will appear in the Log Source Type Manager window.
- Make a note of the value in the Log Source Type ID column. You will need it further in step 2 for importing Kaspersky CyberTrace rules and events.
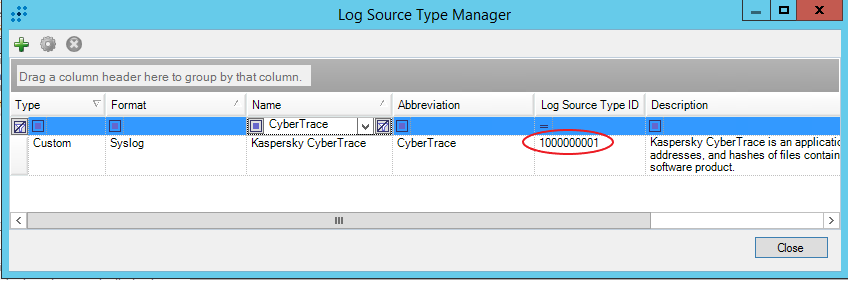
Kaspersky CyberTrace log source type
Step 2. Importing Kaspersky CyberTrace rules and events
This section describes how you can import files that contain Kaspersky CyberTrace rules and events to LogRhythm.
If for any reason the import fails, you can configure adding Kaspersky CyberTrace events and Kaspersky CyberTrace rules manually.
To import files with Kaspersky CyberTrace rules to LogRhythm:
- For each file of the
mperule_%event_name%.xmlformat from theintegration/logrhythm/events/directory, perform the following actions:- Open the file in a text editor.
- Replace the values of both the
MPERuleToMST > MsgSourceTypeIDand theMsgSourceType > MsgSourceTypeIDelements with the log source type ID, you have made a note of in the previous step.For example,
<MsgSourceTypeID>1000000001</MsgSourceTypeID>must change to<MsgSourceTypeID>%CYBERTRACE_ID%</MsgSourceTypeID>, where%CYBERTRACE_ID%stands for the log source type ID of Kaspersky CyberTrace. - Save the file.
- Open LogRhythm Console.
- Select Deployment Manager > Tools > Knowledge > MPE Rule Builder.
The Rule Builder form opens.
- For each file edited in step 1 above, perform the following actions:
- Select File > Import.
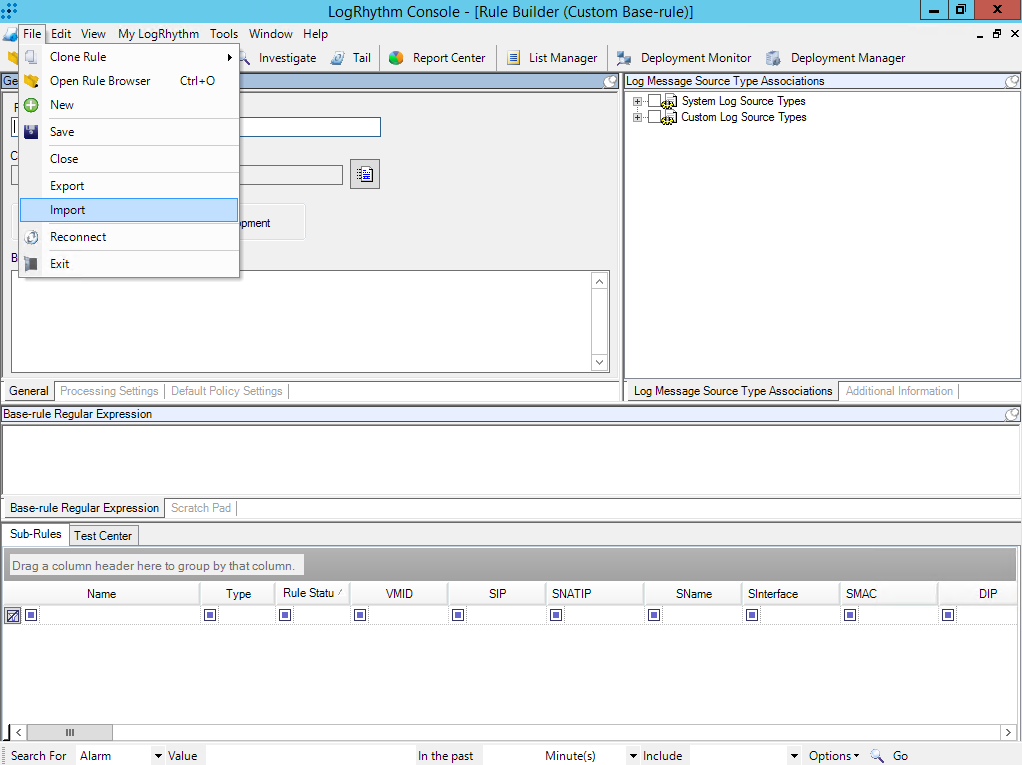
- In the Import Actions window, click Yes.
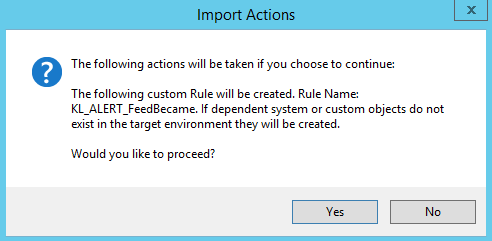
If the import succeeds, the Rule Import Status window opens.
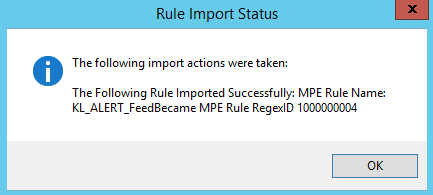
- On the toolbar of the Rule Builder form, click the Open rule library (
 ) button.
) button.The Rule Browser window opens.
- Double-click the event that was imported in step b.
A window with rule settings opens.
Note that the imported rule arrives in LogRhythm in the
Developmentstatus and may not appear in the list of all rules. You can configure display in the Rule Browser window that opens by selecting View > Show Development rules.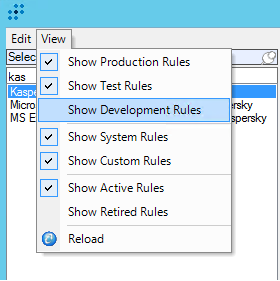
- In the General settings window that opens, in the Rule Status section, select Production or Test.
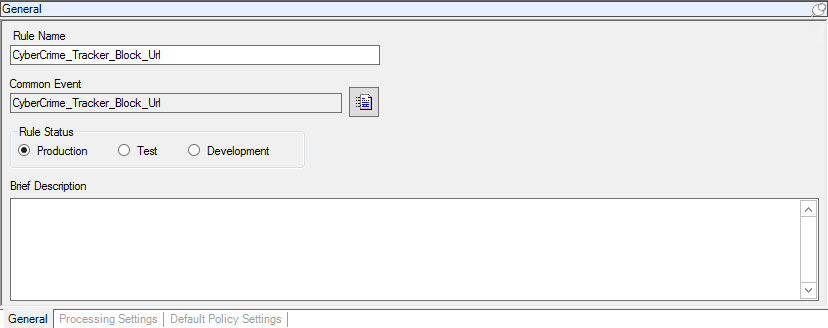
- Click Save.
The corresponding common events and MPE Rules will be added to LogRhythm for all events. The full list of the events is described in the section about adding Kaspersky CyberTrace events. The full list of MPE rules and their settings is described in the section about adding Kaspersky CyberTrace rules.
- Select File > Import.
Some of the imported Kaspersky CyberTrace events might have a low Risk Rating according to the LogRhythm classification. Depending on the filters configuration, LogRhythm might ignore such events. Please check the classification and make sure that the Risk Rating of imported events allows LogRhythm to accept and process them correctly.
Page topStep 3 (optional). Adding Kaspersky CyberTrace events
This section describes how you can add Kaspersky CyberTrace events to LogRhythm manually.
Skip this step, if the importing of Kaspersky CyberTrace rules and events succeeds.
To add Kaspersky CyberTrace events to LogRhythm:
- Run LogRhythm Console.
- Select Deployment Manager > Tools > Knowledge > Common Event Manager.
Common Event Manager menu item
The Common Event Manager window opens.
- Add the events provided in the tables below. If you do not use all commercial and OSINT feeds, some of the events might not be necessary.
- Events of the
"Security : Compromise"classification
Event
Description
KL_APT_Hash_MD5
Hash of a malicious file used in an APT campaign is detected by Kaspersky CyberTrace.
KL_APT_Hash_SHA1
Hash of a malicious file used in an APT campaign is detected by Kaspersky CyberTrace.
KL_APT_Hash_SHA256
Hash of a malicious file used in an APT campaign is detected by Kaspersky CyberTrace.
KL_APT_IP
IP address used in an APT campaign is detected by Kaspersky CyberTrace.
KL_APT_URL
URL used in an APT campaign is detected by Kaspersky CyberTrace.
KL_BotnetCnC_Hash_MD5
Botnet hash is detected by Kaspersky CyberTrace.
KL_BotnetCnC_Hash_SHA1
Botnet hash is detected by Kaspersky CyberTrace.
KL_BotnetCnC_Hash_SHA256
Botnet hash is detected by Kaspersky CyberTrace.
KL_BotnetCnC_URL
Botnet C&C URL is detected by Kaspersky CyberTrace.
KL_Exploit_Hash_MD5
Hash of exploit is detected by Kaspersky CyberTrace.
KL_Exploit_Hash_SHA1
Hash of exploit is detected by Kaspersky CyberTrace.
KL_Exploit_Hash_SHA256
Hash of exploit is detected by Kaspersky CyberTrace.
KL_ICS_Hash_MD5
ICS hash is detected by Kaspersky CyberTrace.
KL_ICS_Hash_SHA1
ICS hash is detected by Kaspersky CyberTrace.
KL_ICS_Hash_SHA256
ICS hash is detected by Kaspersky CyberTrace.
KL_InternalTI_URL
URL of the InternalTI list of Kaspersky CyberTrace.
KL_InternalTI_IP
IP of the InternalTI list of Kaspersky CyberTrace.
KL_InternalTI_Hash_MD5
Hash of the InternalTI list of Kaspersky CyberTrace.
KL_InternalTI_Hash_SHA1
Hash of the InternalTI list of Kaspersky CyberTrace.
KL_InternalTI_Hash_SHA256
Hash of the InternalTI list of Kaspersky CyberTrace.
KL_IoT_Hash_MD5
Hash of IoT is detected by Kaspersky CyberTrace.
KL_IoT_Hash_SHA1
Hash of IoT is detected by Kaspersky CyberTrace.
KL_IoT_Hash_SHA256
Hash of IoT is detected by Kaspersky CyberTrace.
KL_IoT_URL
URL that infects Internet of Things-enabled (IoT) devices is detected by Kaspersky CyberTrace.
KL_IP_Reputation
Malicious or suspicious IP address is detected by Kaspersky CyberTrace.
KL_IP_Reputation_Hash_MD5
Hash of a file hosted on a malicious or suspicious IP address is detected by Kaspersky CyberTrace.
KL_IP_Reputation_Hash_SHA1
Hash of a file hosted on a malicious or suspicious IP address is detected by Kaspersky CyberTrace.
KL_IP_Reputation_Hash_SHA256
Hash of a file hosted on a malicious or suspicious IP address is detected by Kaspersky CyberTrace.
KL_Malicious_URL
Malicious URL is detected by Kaspersky CyberTrace.
KL_Malicious_URL_Hash_MD5
Hash of a file hosted on a malicious URL is detected by Kaspersky CyberTrace.
KL_Malicious_URL_Hash_SHA1
Hash of a file hosted on a malicious URL is detected by Kaspersky CyberTrace.
KL_Malicious_URL_Hash_SHA256
Hash of a file hosted on a malicious URL is detected by Kaspersky CyberTrace.
KL_Malicious_Hash_MD5
Malicious hash is detected by Kaspersky CyberTrace.
KL_Malicious_Hash_SHA1
Malicious hash is detected by Kaspersky CyberTrace.
KL_Malicious_Hash_SHA256
Malicious hash is detected by Kaspersky CyberTrace.
KL_Mobile_Malicious_Hash_MD5
Mobile malicious hash is detected by Kaspersky CyberTrace.
KL_Mobile_Malicious_Hash_SHA1
Mobile malicious hash is detected by Kaspersky CyberTrace.
KL_Mobile_Malicious_Hash_SHA256
Mobile malicious hash is detected by Kaspersky CyberTrace.
KL_Mobile_BotnetCnC_Hash_MD5
Mobile botnet C&C hash is detected by Kaspersky CyberTrace.
KL_Mobile_BotnetCnC_Hash_SHA1
Mobile botnet C&C hash is detected by Kaspersky CyberTrace.
KL_Mobile_BotnetCnC_Hash_SHA256
Mobile botnet C&C hash is detected by Kaspersky CyberTrace.
KL_Mobile_BotnetCnC_URL
Mobile botnet C&C URL is detected by Kaspersky CyberTrace.
KL_Phishing_URL
Phishing URL is detected by Kaspersky CyberTrace.
KL_Ransomware_URL
URL that hosts ransomware is detected by Kaspersky CyberTrace.
KL_Ransomware_URL_Hash_MD5
Hash of ransomware is detected by Kaspersky CyberTrace.
KL_Ransomware_URL_Hash_SHA1
Hash of ransomware is detected by Kaspersky CyberTrace.
KL_Ransomware_URL_Hash_SHA256
Hash of ransomware is detected by Kaspersky CyberTrace.
KL_Vulnerable_File_Hash_MD5
Hash of vulnerable software and related exploits is detected by Kaspersky CyberTrace.
KL_Vulnerable_File_Hash_SHA1
Hash of vulnerable software and related exploits is detected by Kaspersky CyberTrace.
KL_Vulnerable_File_Hash_SHA256
Hash of vulnerable software and related exploits is detected by Kaspersky CyberTrace.
AbuseCh_Feodo_Block_IP
IP address from the Abuse.Ch_Feodo_Block_IP feed is detected by Kaspersky CyberTrace.
AbuseCh_Ransomware_Block_URL
URL from the Abuse.Ch_Ransomware_Block_URL feed is detected by Kaspersky CyberTrace.
AbuseCh_Ransomware_Block_Domain
Domain from the Abuse.Ch_Ransomware_Block_Domain feed is detected by Kaspersky CyberTrace.
AbuseCh_Ransomware_Block_IP
IP address from the Abuse.Ch_Ransomware_Block_IP feed is detected by Kaspersky CyberTrace.
AbuseCh_Ransomware_Common_URL
URL from the Abuse.Ch_Ransomware_Common_URL feed is detected by Kaspersky CyberTrace.
AbuseCh_SSL_Certificate_Block_IP
IP address from the AbuseCh_SSL_Certificate_Block_IP feed is detected by Kaspersky CyberTrace.
AbuseCh_SSL_Certificate_Hash_SHA1
Hash from the AbuseCh_SSL_Certificate_Hash_SHA1 feed is detected by Kaspersky CyberTrace.
BlocklistDe_Block_IP
IP from the BlocklistDe_Block_IP feed is detected by Kaspersky CyberTrace.
CyberCrime_Tracker_Block_Url
URL from the CyberCrime_Tracker_Block_Url feed is detected by Kaspersky CyberTrace.
EmergingThreats_Block_IP
IP address from the EmergingThreats_Block_IP feed is detected by Kaspersky CyberTrace.
EmergingThreats_Compromised_IP
IP address from the EmergingThreats_Compromised_IP feed is detected by Kaspersky CyberTrace.
- Alert events:
Event
Description
Classification
KL_ALERT_ConfigurationUpdated
This event is generated if Feed Service has reloaded the configuration file.
Audit : Configuration
KL_ALERT_FeedBecameAvailable
This event is generated if a feed that can be used with the current certificate has become available.
Audit : Other Audit Success
KL_ALERT_FeedBecameUnavailable
This event is generated if a feed that is being used with the current certificate has become unavailable.
Audit : Other Audit Failure
KL_ALERT_OutdatedFeed
This event is generated if a feed has not been updated during the specified period.
Audit : Other Audit Failure
KL_ALERT_ServiceUnavailable
This event is generated when the watchdog module has detected that Feed Service has crashed or frozen.
Audit : Other Audit Failure
KL_ALERT_ServiceStopped
This event is generated when Feed Service is stopped successfully.
Audit : Startup and Shutdown
KL_ALERT_ServiceStarted
This event is generated when Feed Service is started successfully.
Audit : Startup and Shutdown
KL_ALERT_UpdatedFeed
This event is generated when a feed is updated and loaded by Feed Service.
Audit : Other Audit Success
KL_ALERT_FailedToUpdateFeed
This event is generated when Feed Service fails to load a new feed (for example, due to the limitation on the number of indicators that is imposed by the license key) and continues using an old feed.
Audit : Other Audit Failure
KL_ALERT_LicenseExpires
This event is generated to inform you that the license key that is being used will expire in less than 30 days.
Audit : Policy
KL_ALERT_LicenseExpired
This event is generated when your license key has expired.
Audit : Policy
KL_ALERT_EPSLimitExceeded
This event is generated when the limit on the number of processed events per second (EPS) imposed by the licensed key or licensing level has been exceeded.
Audit : Policy
KL_ALERT_EPSHardLimit
This event is generated when Feed Service limits the number of events processed per second (EPS) to the maximum number of events for the current license key or licensing level. The limit applies regardless of the number of incoming events.
Audit : Policy
KL_ALERT_LicenseChanged
This event is generated when Kaspersky CyberTrace starts to use another license key or licensing level.
Audit : Configuration
KL_ALERT_RetroScanError
This event is generated when the retrospective scan task failed.
Audit : Other Audit Failure
KL_ALERT_RetroScanCompleted
This event is generated when the retrospective scan task succeeded.
Audit : Other Audit Success
KL_ALERT_RetroScanStorageExceeded
This event is generated when the limit on the size of the saved events has been exceeded.
Audit : Policy
KL_ALERT_IndicatorsStoreLimitExceeded
This event is generated when the limit on the size of the saved indicators has been exceeded.
Audit : Policy
KL_ALERT_IndicatorsStoreHardLimit
This event is generated when Kaspersky CyberTrace limits adding and updating of indicators.
Audit : Policy
KL_ALERT_FreeSpaceEnds
This event is generated when the available disk space becomes low.
Audit : Policy
Alert events may contain context fields, as described in the section about the alert events of Kaspersky CyberTrace.
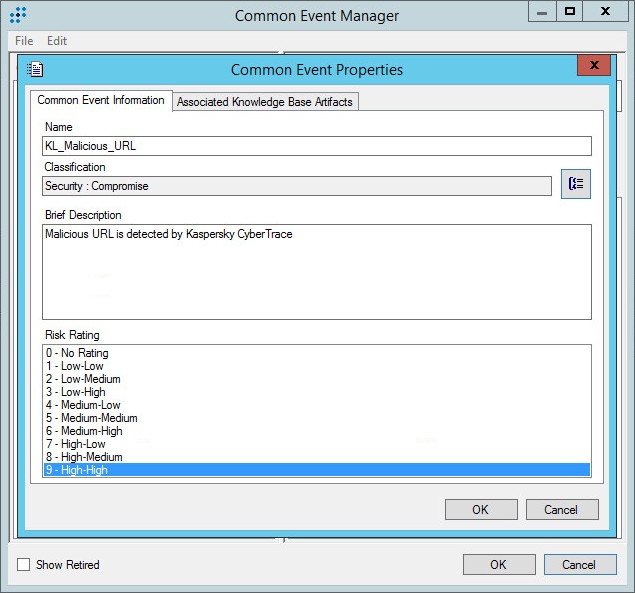
Common Event Properties window
- Events of the
After the events are added, the Common Event Manager window must contain the events as shown in the figure below.
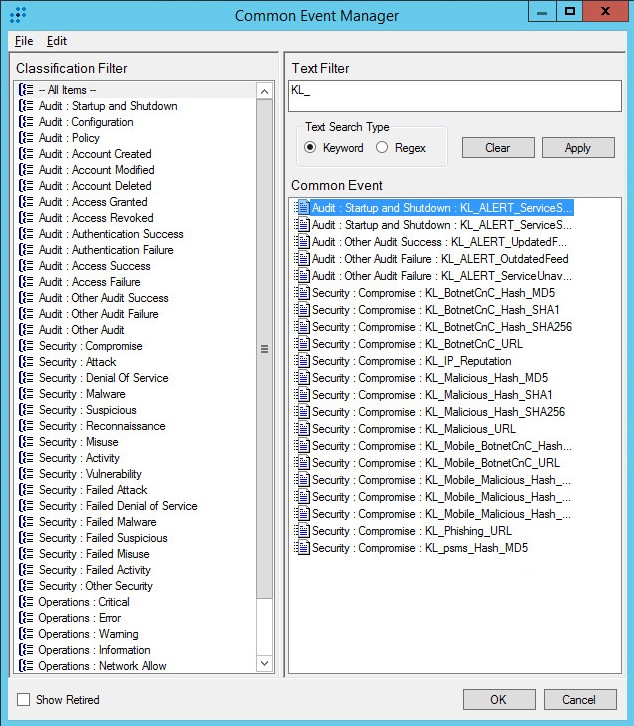
Added events
Page topStep 4 (optional). Adding Kaspersky CyberTrace rules
This section describes how you can add Kaspersky CyberTrace rules to LogRhythm manually.
Skip this step, if importing Kaspersky CyberTrace rules and events succeeds.
To add Kaspersky CyberTrace rules to LogRhythm:
- Run LogRhythm Console.
- Select Deployment Manager > Tools > Knowledge > MPE Rule Builder.
The Rule Builder form opens.
- For every event, add a rule by clicking the Create a new rule button (
 ).
).For every rule do the following:
- In the General section, click the button next to the Common Event box and select the required event.
The event will be displayed in the box.
- In the Log Message Source Type Associations section, specify
Kaspersky CyberTraceas the log source type. - To set the rule status, select the Production or Test radio button.
When creating regular expressions (in the Base-rule Regular Expressions section), follow the instructions provided in the LogRhythm Help section "Use MPE Rule Builder - Parsing Fields and Tags".
We recommend that you use the regular expressions provided in the table below.
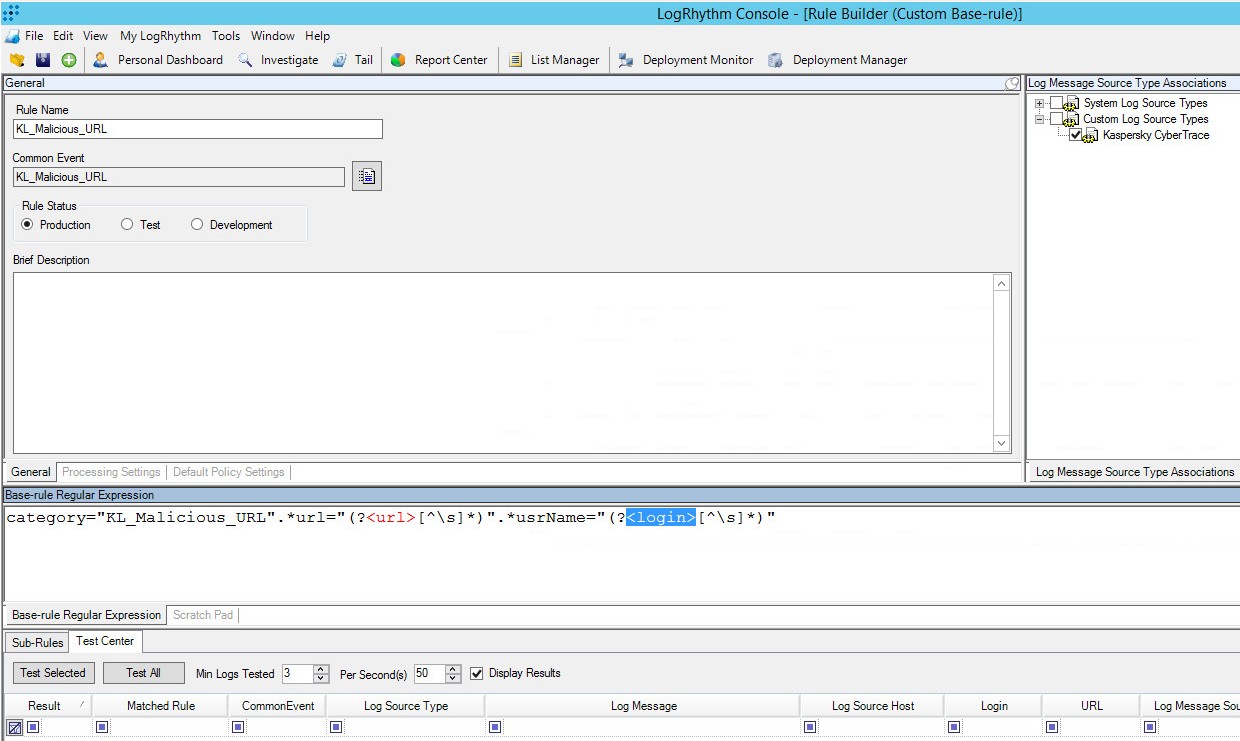
Rule Builder form
- In the General section, click the button next to the Common Event box and select the required event.
The following list contains regular expressions for each event. If you want to use other regular expressions, use the example events from the second column of the table to check the regular expressions of your choice.
- AbuseCh_Feodo_Block_IP
Regular expression
Event example for checking regular expressions
category=AbuseCh_Feodo_Block_IP.*ip=(?<object>[^\s]*).*usrName=(?<login>[^\s]*)May 2 16:41:40 category=AbuseCh_Feodo_Block_IP matchedIndicator=103.11.83.52 url=- src=- ip=103.11.83.52 md5=- sha1=- sha256=- usrName=VerifTestUserName ip=103.11.83.52 source=https://feodotracker.abuse.ch/downloads/ipblocklist.txt - AbuseCh_Ransomware_Block_URL
Regular expression
Event example for checking regular expressions
category=AbuseCh_Ransomware_Block_URL.*url=(?<url>[^\s]*).*usrName=(?<login>[^\s]*)May 2 16:41:40 category=AbuseCh_Ransomware_Block_URL matchedIndicator=00005ik.rcomhost.com/7fg3g url=00005ik.rcomhost.com/7fg3g src=- ip=- md5=- sha1=- sha256=- usrName=- source=https://ransomwaretracker.abuse.ch/downloads/RW_URLBL.txt url=00005ik.rcomhost.com/7fg3g - AbuseCh_Ransomware_Block_Domain
Regular expression
Event example for checking regular expressions
category=AbuseCh_Ransomware_Block_Domain.*url=(?<url>[^\s]*).*usrName=(?<login>[^\s]*)May 2 16:41:40 category=AbuseCh_Ransomware_Block_Domain matchedIndicator=pagaldaily.com url=pagaldaily.com src=- ip=- md5=- sha1=- sha256=- usrName=- domain=pagaldaily.com source=https://ransomwaretracker.abuse.ch/downloads/RW_DOMBL.txt - AbuseCh_Ransomware_Block_IP
Regular expression
Event example for checking regular expressions
category=AbuseCh_Ransomware_Block_IP.*ip=(?<object>[^\s]*).*usrName=(?<login>[^\s]*)May 2 16:41:40 category=AbuseCh_Ransomware_Block_IP matchedIndicator=83.217.11.193 url=- src=- ip=83.217.11.193 md5=- sha1=- sha256=- usrName=VerifTestUserName ip=83.217.11.193 source=https://ransomwaretracker.abuse.ch/downloads/RW_IPBL.txt - AbuseCh_Ransomware_Common_URL
Regular expression
Event example for checking regular expressions
category=AbuseCh_Ransomware_Common_URL.*url=(?<url>[^\s]*).*usrName=(?<login>[^\s]*)May 2 16:41:40 category=AbuseCh_Ransomware_Common_URL matchedIndicator=83.217.11.193/linuxsucks.php url=83.217.11.193/linuxsucks.php src=- ip=- md5=- sha1=- sha256=- usrName=- ASN=199669 IPList=[{ ip=83.217.11.193}] country=RU domain=83.217.11.193 first_seen=12.08.2018 00:46 malware=Locky registar= source=https://ransomwaretracker.abuse.ch/feeds/csv/ status=offline threat=C2 url=83.217.11.193/linuxsucks.php - AbuseCh_SSL_Certificate_Block_IP
Regular expression
Event example for checking regular expressions
category=AbuseCh_SSL_Certificate_Block_IP.*ip=(?<object>[^\s]*).*usrName=(?<login>[^\s]*)May 2 16:41:40 category=AbuseCh_SSL_Certificate_Block_IP matchedIndicator=83.217.11.193 url=- src=- ip=83.217.11.193 md5=- sha1=- sha256=- usrName=VerifTestUserName ip=83.217.11.193 source=https://sslbl.abuse.ch/blacklist/sslblacklist.csv - AbuseCh_SSL_Certificate_Hash_SHA1
Regular expression
Event example for checking regular expressions
category=AbuseCh_SSL_Certificate_Hash_SHA1.*sha1=(?<object>[^\s]*).*usrName=(?<login>[^\s]*)May 2 16:41:40 category=AbuseCh_SSL_Certificate_Hash_SHA1 matchedIndicator=3395856ce81f2b7382dee72602f798b642f14140 url=- src=- ip=- md5=- sha1=3395856ce81f2b7382dee72602f798b642f14140 sha256=- usrName=VerifTestUserName MD5=86255ec982e822f6b57855d3866618ae data_added=2015-09-22 - BlocklistDe_Block_IP
Regular expression
Event example for checking regular expressions
category=BlocklistDe_Block_IP.*ip=(?<object>[^\s]*).*usrName=(?<login>[^\s]*)May 2 16:41:40 category=BlocklistDe_Block_IP matchedIndicator=83.217.11.193 url=- src=- ip=83.217.11.193 md5=- sha1=- sha256=- usrName=VerifTestUserName ip=83.217.11.193 - CyberCrime_Tracker_Block_Url
Regular expression
Event example for checking regular expressions
category= CyberCrime_Tracker_Block_Url.*url=(?<url>[^\s]*).*usrName=(?<login>[^\s]*)May 2 16:41:40 category=CyberCrime_Tracker_Block_Url matchedIndicator=83.217.11.193/linuxsucks.php url=83.217.11.193/linuxsucks.php src=- ip=- md5=- sha1=- sha256=- usrName=- ASN=199669 IPList=[{ ip=83.217.11.193}] country=RU domain=83.217.11.193 first_seen=12.08.2018 00:46 malware=Locky status=offline threat=C2 url=83.217.11.193/linuxsucks.php - EmergingThreats_Block_IP
Regular expression
Event example for checking regular expressions
category=EmergingThreats_Block_IP.*ip=(?<object>[^\s]*).*usrName=(?<login>[^\s]*)May 2 16:41:40 category=EmergingThreats_Block_IP matchedIndicator=101.200.81.187 url=- src=- ip=101.200.81.187 md5=- sha1=- sha256=- usrName=VerifTestUserName ip=101.200.81.187 source=https://rules.emergingthreats.net/fwrules/emerging-Block-IPs.txt - EmergingThreats_Compromised_IP
Regular expression
Event example for checking regular expressions
category=EmergingThreats_Compromised_IP.*ip=(?<object>[^\s]*).*usrName=(?<login>[^\s]*)May 2 16:41:40 category=EmergingThreats_Compromised_IP matchedIndicator=100.24.121.249 url=- src=- ip=100.24.121.249 md5=- sha1=- sha256=- usrName=VerifTestUserName ip=100.24.121.249 source=https://rules.emergingthreats.net/blockrules/compromised-ips.txt - KL_ALERT_FeedBecameAvailable
Regular expression
Event example for checking regular expressions
alert=KL_ALERT_FeedBecameAvailable.*feed=(?<object>[^\s]*)May 2 16:41:40 alert=KL_ALERT_FeedBecameAvailable feed=Botnet_CnC_URL_Data_Feed.json - KL_ALERT_FeedBecameUnavailable
Regular expression
Event example for checking regular expressions
alert=KL_ALERT_FeedBecameUnavailable.*feed=(?<object>[^\s]*)May 2 16:41:40 alert=KL_ALERT_FeedBecameUnavailable feed=Botnet_CnC_URL_Data_Feed.json - KL_ALERT_OutdatedFeed
Regular expression
Event example for checking regular expressions
alert=KL_ALERT_OutdatedFeed.*feed=(?<object>[^\s]*)May 2 16:41:40 alert=KL_ALERT_OutdatedFeed feed=Botnet_CnC_URL_Data_Feed.json - KL_ALERT_ServiceStarted
Regular expression
Event example for checking regular expressions
alert=KL_ALERT_ServiceStartedMay 2 16:41:40 alert=KL_ALERT_ServiceStarted - KL_ALERT_ServiceStopped
Regular expression
Event example for checking regular expressions
alert=KL_ALERT_ServiceStoppedMay 2 16:41:40 alert=KL_ALERT_ServiceStopped - KL_ALERT_ServiceUnavailable
Regular expression
Event example for checking regular expressions
alert=KL_ALERT_ServiceUnavailableMay 2 16:41:40 alert=KL_ALERT_ServiceUnavailable - KL_ALERT_UpdatedFeed
Regular expression
Event example for checking regular expressions
alert=KL_ALERT_UpdatedFeed.*feed=(?<object>[^\s]*).*records=(?<quantity>[^\s]*)May 2 16:41:40 alert=KL_ALERT_UpdatedFeed feed=Botnet_CnC_URL_Data_Feed.json records=23 - KL_ALERT_FailedToUpdateFeed
Regular expression
Event example for checking regular expressions
alert=KL_ALERT_FailedToUpdateFeed.*feed=(?<object>[^\s]*)May 2 16:41:40 alert=KL_ALERT_FailedToUpdateFeed feed=Botnet_CnC_URL_Data_Feed.json - KL_ALERT_LicenseExpires
Regular expression
Event example for checking regular expressions
alert=KL_ALERT_LicenseExpires.*license_name=(?<object>[^\s]*)May 2 16:41:40 alert=KL_ALERT_LicenseExpires expiration_date=23.02.2020 license_name=kl_license - KL_ALERT_LicenseExpired
Regular expression
Event example for checking regular expressions
alert=KL_ALERT_LicenseExpired.*license_name=(?<object>[^\s]*)May 2 16:41:40 alert=KL_ALERT_LicenseExpired expiration_date=23.02.2020 license_name=kl_license - KL_ALERT_EPSLimitExceeded
Regular expression
Event example for checking regular expressions
alert=KL_ALERT_EPSLimitExceeded.*current_eps=(?<quantity>[^\s]*)May 2 16:41:40 alert=KL_ALERT_EPSLimitExceeded current_eps=6500 license_limit_eps=5000 - KL_ALERT_EPSHardLimit
Regular expression
Event example for checking regular expressions
alert=KL_ALERT_EPSHardLimit.*license_limit_eps=(?<quantity>[^\s]*)May 2 16:41:40 alert=KL_ALERT_EPSHardLimit license_limit_eps=5000 - KL_ALERT_LicenseChanged
Regular expression
Event example for checking regular expressions
alert=KL_ALERT_LicenseChanged.*license_name=(?<object>[^\s]*)May 2 16:41:40 alert=KL_ALERT_LicenseChanged expiration_date=23.02.2020 license_name=kl_license license_level=EnterpriseTIP - KL_ALERT_ConfigurationUpdated
Regular expression
Event example for checking regular expressions
alert=KL_ALERT_ConfigurationUpdatedMay 2 16:41:40 alert=KL_ALERT_ConfigurationUpdated - KL_ALERT_RetroScanError
Regular expression
Event example for checking regular expressions
alert=KL_ALERT_RetroScanError.*error=(?<object>[^\s]*)May 2 16:41:40 alert=KL_ALERT_RetroScanError error=Service is unavailable - KL_ALERT_RetroScanCompleted
Regular expression
Event example for checking regular expressions
alert=KL_ALERT_RetroScanCompleted.*iocs_rescaned=(?<object>[^\s]*).*iocs_detected=(?<quantity>[^\s]*).*retroscan_report=(?<url>[^\s]*)May 2 16:41:40 alert=KL_ALERT_RetroScanCompleted iocs_rescaned=1998 iocs_detected=82 retroscan_report=https://127.0.0.1:443/retroscan/81650945-f186-437b-8945-9f31715d32da - KL_ALERT_RetroScanStorageExceeded
Regular expression
Event example for checking regular expressions
alert=KL_ALERT_RetroScanStorageExceeded.*storage_size_limit=(?<object>[^\s]*)May 2 16:41:40 alert=KL_ALERT_RetroScanStorageExceeded storage_size_limit=9876 - KL_ALERT_IndicatorsStoreLimitExceeded
Regular expression
Event example for checking regular expressions
alert=KL_ALERT_IndicatorsStoreLimitExceeded.*current_indicators_count=(?<object>[^\s]*).*license_limit_indicators=(?<quantity>[^\s]*)May 2 16:41:40 alert=KL_ALERT_IndicatorsStoreLimitExceeded current_indicators_count=489002001 license_limit_indicator=5000000 - KL_ALERT_IndicatorsStoreHardLimit
Regular expression
Event example for checking regular expressions
alert=KL_ALERT_IndicatorsStoreHardLimit.*license_limit_indicators=(?<quantity>[^\s]*).*msg=(?<object>[^\s]*)May 2 16:41:40 alert=KL_ALERT_IndicatorsStoreHardLimit license_limit_indicators=5000000 msg=Indicators store limit exceeded - KL_ALERT_FreeSpaceEnds
Regular expression
Event example for checking regular expressions
alert=KL_ALERT_FreeSpaceEnds.*msg=Free space left: (?<object>[^\s]*) MbMay 2 16:41:40 alert=KL_ALERT_FreeSpaceEnds msg=Free space left: 7322 Mb - KL_APT_Hash_MD5
Regular expression
Event example for checking regular expressions
category=KL_APT_Hash_MD5.*matchedIndicator=(?<object>[^\s]*).*usrName=(?<login>[^\s]*)May 2 16:41:40 category=KL_APT_Hash_MD5 matchedIndicator=7A2E65A0F70EE0615EC0CA34240CF082 url=- src=192.168.0.0 ip=- md5=7A2E65A0F70EE0615EC0CA34240CF082 sha1=- sha256=- usrName=VerifTestUserName MD5=7A2E65A0F70EE0615EC0CA34240CF082 detection_date=01.06.2018 00:00 publication_name=TestRecordMb - KL_APT_Hash_SHA1
Regular expression
Event example for checking regular expressions
category=KL_APT_Hash_SHA1.*sha1=(?<object>[^\s]*).*usrName=(?<login>[^\s]*)May 2 16:41:40 category=KL_APT_Hash_SHA1 matchedIndicator=7A2EE06E65A0F70EE0615EC0CA342470EE0CF082 url=- src=192.168.0.0 ip=- md5=- sha1=7A2EE06E65A0F70EE0615EC0CA342470EE0CF082 sha256=- usrName=VerifTestUserName MD5=7A2E65A0F70EE0615EC0CA34240CF082 SHA1=EA2EE06E65A0F70EE0615EC0CA342470EE0CF082 SHA256=2EE072EEA2EE615EC006E65A0CF0F70EA342E0615EC0F70ECA342470EE0CF082 detection_date=01.06.2018 00:00 publication_name=TestRecord - KL_APT_Hash_SHA256
Regular expression
Event example for checking regular expressions
category=KL_APT_Hash_SHA256.*sha256=(?<object>[^\s]*).*usrName=(?<login>[^\s]*)May 2 16:41:40 category=KL_APT_Hash_SHA256 matchedIndicator=2EE072EEA2EE615EC006E65A0CF0F70EA342E0615EC0F70ECA342470EE0CF082 url=- src=192.168.0.0 ip=- md5=- sha1=- sha256=2EE072EEA2EE615EC006E65A0CF0F70EA342E0615EC0F70ECA342470EE0CF082 usrName=VerifTestUserName MD5=7A2E65A0F70EE0615EC0CA34240CF082 SHA1=EA2EE06E65A0F70EE0615EC0CA342470EE0CF082 SHA256=2EE072EEA2EE615EC006E65A0CF0F70EA342E0615EC0F70ECA342470EE0CF082 detection_date=01.06.2018 00:00 publication_name=TestRecord - KL_APT_IP
Regular expression
Event example for checking regular expressions
category=KL_APT_IP.*matchedIndicator=(?<object>[^\s]*).*usrName=(?<login>[^\s]*)May 2 16:41:40 category=KL_APT_IP matchedIndicator=192.0.2.4 url=- src=192.168.0.0 ip=192.0.2.4 md5=- sha1=- sha256=- usrName=VerifTestUserName detection_date=01.06.2018 00:00 ip=192.0.2.4 publication_name=TestRecord - KL_APT_URL
Regular expression
Event example for checking regular expressions
category=KL_APT_URL.*matchedIndicator=(?<url>[^\s]*).*usrName=(?<login>[^\s]*)May 2 16:41:40 category=KL_APT_URL matchedIndicator=b046f5b25458638f6705d53539c79f62.com url=b046f5b25458638f6705d53539c79f62.com src=192.168.0.0 ip=- md5=- sha1=- sha256=- usrName=VerifTestUserName detection_date=01.06.2018 00:00 id=0 mask=b046f5b25458638f6705d53539c79f62.com publication_name=TestRecord type=1 - KL_BotnetCnC_Hash_MD5
Regular expression
Event example for checking regular expressions
category=KL_BotnetCnC_Hash_MD5.*md5=(?<object>[^\s]*).*usrName=(?<login>[^\s]*).*mask=(?<url>[^\s]*).*threat=(?<objectname>[^\s]*)May 2 16:41:40 category=KL_BotnetCnC_Hash_MD5 url=- md5=E013C01AB3E27BE6FBA4E23EE88B100F sha1=- sha256=- ip=- usrName=VerifTestUserName IP=118.142.224.213, 160.16.120.71, 61.19.201.7 files=[{MD5=E013C01AB3E27BE6FBA4E23EE88B100F SHA256=C00269AA2BCF375D0CF870C36F737C27EBB04F69F5B6912F860D8A1F5F1D9DF6}] first_seen=08.07.2015 23:39 geo=jp, hk, tw, au, th, cn, my, ph, vn, in id=9189405 last_seen=29.10.2015 15:59 mask=172.117.45.14/pid=1000/botnet_setup_3.exe popularity=5 threat=Trojan-Banker.AndroidOS.Wroba type=3 - KL_BotnetCnC_Hash_SHA1
Regular expression
Event example for checking regular expressions
category=KL_BotnetCnC_Hash_SHA1.*sha1=(?<object>[^\s]*).*usrName=(?<login>[^\s]*).*mask=(?<url>[^\s]*).*threat=(?<objectname>[^\s]*)May 2 16:41:40 category=KL_BotnetCnC_Hash_SHA1 url=- md5=- sha1=FE61DED0504013D9ED6691F6C5BB69DCD8C8DD60 sha256=- ip=- usrName=VerifTestUserName IP=78.47.151.188 files=[{SHA1=FE61DED0504013D9ED6691F6C5BB69DCD8C8DD60 SHA256=B6AEF9CBFA21B0A9E6D03364F5476B81C4A5D8EF212DFB35E3EF96003CADCB0B}] first_seen=21.07.2015 12:19 geo=it, es, de, fr, gb id=9320249 last_seen=14.01.2016 12:55 mask=botnet_domain_4.com/get.php?p=4&id=2 popularity=4 threat=Trojan-SMS.AndroidOS.Opfake type=4 - KL_BotnetCnC_Hash_SHA256
Regular expression
Event example for checking regular expressions
category=KL_BotnetCnC_Hash_SHA256.*sha256=(?<object>[^\s]*).*usrName=(?<login>[^\s]*).*mask=(?<url>[^\s]*).*threat=(?<objectname>[^\s]*)May 2 16:41:40 category=KL_BotnetCnC_Hash_SHA256 url=- md5=- sha1=- sha256=AFDD5508B48B8270C1DBAF32121A00951E450A56791275D8E7C413EF8380A809 ip=- usrName=VerifTestUserName IP=46.4.114.61, 95.213.186.51, 95.213.192.71, 176.9.82.215, 178.63.12.207, 109.206.186.164, 176.9.48.86, 213.163.70.170, 95.213.192.83, 173.45.161.113 files=[{MD5=55B8D137C80AE5E995EC355524594F3B SHA1=BEA6B860C719F1C886461C8A3FF4935471D2FA64 SHA256=AFDD5508B48B8270C1DBAF32121A00951E450A56791275D8E7C413EF8380A809}] first_seen=15.04.2015 13:18 geo=vn, in, tr, mx, ir, bd, id, dz, ph, th id=9230458 last_seen=14.01.2016 12:55 mask=*.subbotnet_domain_19.botnet_domain.com popularity=5 threat=Trojan.Win32.Agent type=19 - KL_BotnetCnC_URL
Regular expression
Event example for checking regular expressions
category=KL_BotnetCnC_URL.*url=(?<url>[^\s]*).*usrName=(?<login>[^\s]*)May 2 16:41:40 category=KL_BotnetCnC_URL url=http://d.subphishing_domain.phishing_domain_19.com md5=- sha1=- sha256=- ip=- usrName=VerifTestUserName IP=104.168.159.146, 138.201.0.229, 138.201.0.231, 138.201.0.230, 78.46.185.21, 78.46.185.23, 78.46.185.12, 78.46.185.3, 78.46.185.16, 78.46.185.28 first_seen=12.01.2016 12:50 geo=br, pt, us id=9508721 last_seen=14.01.2016 13:36 mask=*.subphishing_domain.phishing_domain_19.com popularity=5 type=19 - KL_ICS_Hash_MD5
Regular expression
Event example for checking regular expressions
category=KL_ICS_Hash_MD5.*md5=(?<object>[^\s]*).*usrName=(?<login>[^\s]*).*threat=(?<objectname>[^\s]*)May 2 16:41:40 category=KL_ICS_Hash_MD5 matchedIndicator=7A8F30B40C6564EFF95E678F7C43346C url=- src=- ip=- md5=7A8F30B40C6564EFF95E678F7C43346C sha1=- sha256=- usrName=VerifTestUserName MD5=7A8F30B40C6564EFF95E678F7C43346C SHA1=E51B1A1FDA2CAF10623A83A1476585AC6E10D569 SHA256=EF6CDD46DB5513F7247789E559A1520F6C1DCD17235C395EDCA3E5043988B54B file_size=1989 first_seen=10.07.2015 23:53 last_seen=12.10.2019 18:44 popularity=1 threat=HEUR:Trojan.Win32.Generic - KL_ICS_Hash_SHA1
Regular expression
Event example for checking regular expressions
category=KL_ICS_Hash_SHA1.*sha1=(?<object>[^\s]*).*usrName=(?<login>[^\s]*).*threat=(?<objectname>[^\s]*)May 2 16:41:40 category=KL_ICS_Hash_SHA1 matchedIndicator=E51B1A1FDA2CAF10623A83A1476585AC6E10D569 url=- src=- ip=- md5=- sha1=E51B1A1FDA2CAF10623A83A1476585AC6E10D569 sha256=- usrName=VerifTestUserName MD5=7A8F30B40C6564EFF95E678F7C43346C SHA1=E51B1A1FDA2CAF10623A83A1476585AC6E10D569 SHA256=EF6CDD46DB5513F7247789E559A1520F6C1DCD17235C395EDCA3E5043988B54B file_size=1989 first_seen=10.07.2015 23:53 last_seen=12.10.2019 18:44 popularity=1 threat=HEUR:Trojan.Win32.Generic - KL_ICS_Hash_SHA256
Regular expression
Event example for checking regular expressions
category=KL_ICS_Hash_SHA256.*sha256=(?<object>[^\s]*).*usrName=(?<login>[^\s]*).*threat=(?<objectname>[^\s]*)May 2 16:41:40 category=KL_ICS_Hash_SHA256 matchedIndicator=EF6CDD46DB5513F7247789E559A1520F6C1DCD17235C395EDCA3E5043988B54B url=- src=- ip=- md5=- sha1=- sha256=EF6CDD46DB5513F7247789E559A1520F6C1DCD17235C395EDCA3E5043988B54B usrName=VerifTestUserName MD5=7A8F30B40C6564EFF95E678F7C43346C SHA1=E51B1A1FDA2CAF10623A83A1476585AC6E10D569 SHA256=EF6CDD46DB5513F7247789E559A1520F6C1DCD17235C395EDCA3E5043988B54B file_size=1989 first_seen=10.07.2015 23:53 last_seen=12.10.2019 18:44 popularity=1 threat=HEUR:Trojan.Win32.Generic - KL_InternalTI_URL
Regular expression
Event example for checking regular expressions
category=KL_InternalTI_URL.*url=(?<object>[^\s]*).*usrName=(?<login>[^\s]*)May 2 16:41:40 category=KL_InternalTI_URL matchedIndicator=fakess123.nu url=fakess123.nu src=- ip=- md5=- sha1=- sha256=- usrName=VerifTestUser URL=fakess123.nu - KL_InternalTI_IP
Regular expression
Event example for checking regular expressions
category=KL_InternalTI_IP.*ip=(?<object>[^\s]*).*usrName=(?<login>[^\s]*)May 2 16:41:40 category=KL_InternalTI_IP matchedIndicator=192.0.2.0 url=- src=- ip=192.0.2.0 md5=- sha1=- sha256=- usrName=VerifTestUser IP=192.0.2.0 - KL_InternalTI_Hash_MD5
Regular expression
Event example for checking regular expressions
category=KL_InternalTI_MD5.*md5=(?<object>[^\s]*).*usrName=(?<login>[^\s]*)May 2 16:41:40 category=KL_InternalTI_MD5 matchedIndicator=44D88612FEA8A8F36DE82E1278ABB02F url=- src=- ip=- md5=44D88612FEA8A8F36DE82E1278ABB02F sha1=- sha256=- usrName=VerifTestUser MD5=44D88612FEA8A8F36DE82E1278ABB02F - KL_InternalTI_Hash_SHA1
Regular expression
Event example for checking regular expressions
category=KL_InternalTI_SHA1.*sha1=(?<object>[^\s]*).*usrName=(?<login>[^\s]*)May 2 16:41:40 category=KL_InternalTI_SHA1 matchedIndicator=3395856CE81F2B7382DEE72602F798B642F14140 url=- src=- ip=- md5=- sha1=3395856CE81F2B7382DEE72602F798B642F14140 sha256=- usrName=VerifTestUser SHA1=3395856CE81F2B7382DEE72602F798B642F14140 - KL_InternalTI_Hash_SHA256
Regular expression
Event example for checking regular expressions
category=KL_InternalTI_SHA256.*sha256=(?<object>[^\s]*).*usrName=(?<login>[^\s]*)May 2 16:41:40 category=KL_InternalTI_SHA256 matchedIndicator=762B2BE1D22B737A287D0D6D4FBAF983FD214BBA1497C0A3A2C58C7819303C0C url=- src=- ip=- md5=- sha1=- sha256=762B2BE1D22B737A287D0D6D4FBAF983FD214BBA1497C0A3A2C58C7819303C0C usrName=VerifTestUser SHA256=762B2BE1D22B737A287D0D6D4FBAF983FD214BBA1497C0A3A2C58C7819303C0C - KL_IP_Reputation
Regular expression
Event example for checking regular expressions
category=KL_IP_Reputation.*ip=(?<object>[^\s]*).*usrName=(?<login>[^\s]*).*category=(?<process>[^\s]*).*threat_score=(?<severity>[^\s]*)May 2 16:41:40 category=KL_IP_Reputation url=- md5=- sha1=- sha256=- ip=18.50.1.47 usrName=VerifiTestUserName category=spam first_seen=21.01.2015 00:00 ip=18.50.1.47 ip_geo=us last_seen=17.05.2016 03:16 popularity=1 threat_score=100 - KL_IP_Reputation_Hash_MD5
Regular expression
Event example for checking regular expressions
category=KL_IP_Reputation_Hash_MD5.*matchedIndicator=(?<object>[^\s]*).*usrName=(?<login>[^\s]*)May 2 16:41:40 category=KL_IP_Reputation_Hash_MD5 matchedIndicator=61200D253ADD14C91CD64F2CB1F221CB url=- src=- ip=- md5=61200D253ADD14C91CD64F2CB1F221CB sha1=- sha256=- usrName=- category=malware domains=k4d7ppv9.humanpchelp.pw, mwi49i2b.backbonecomputer.top, 9uq5mmw7.overseascomputer.pw, 9tqnii2s.motivationcomputer.pw, 4iaag9ng.luxurypchelp.pw, kxol25kx.pcserviceline.top, 7ifiye96.phoenixcomputerhelp.pw, tnv5yyvj.pcservicecatch.pw, y4ki19os.computercoral.top, pmayaidy.rankpcservice.top files=[{ MD5=61200D253ADD14C91CD64F2CB1F221CB SHA1=E23B0F6ECEFF56870908B2EC704F62ACB4E005AD SHA256=7FC582451A8D9EAF112A3CFC7EFF8EBC8A5FCB8480E42A8D2B5A4E0E3C12D793 threat=HEUR:Trojan.Script.Generic},{ MD5=06A2E41E9CDA9C19AF5FB29483687A56 SHA1=37ED2076FCC0365BA02210E18BBAB162D7338180 SHA256=9570F5C81FF906CD52EE42B5D24359B8A7CA4EC225C532A811699F1089847252 threat=HEUR:Trojan.Script.Generic},{ MD5=AA909F4A33A0D305C0ADF7FCD6DC95E5 SHA1=0A88A71A3C43F02075B7B3CB1A6ED1A603CC666E SHA256=96467635B09D64B29DEAF2A7923ADCD63C2E7F9308B80DDF46F251EBDB2E6A66 threat=HEUR:Trojan.Script.Generic},{ MD5=1D02D52FE17A040A2C7D7C4EE7020E6A SHA1=036D8147D00334824073A22C3D7016EE27643CBD SHA256=737117D867D8CC777AF09F635126C6867ADD08C47C74EDCF5636A84F3F14911B threat=HEUR:Trojan.Script.Generic},{ MD5=393F797A732D5FF35B6102B298349C65 SHA1=760C99F3FB4330BA7B9EB76780718E3023C345EE SHA256=5E86FE0A4DA6A1394DBC6BD2D0F7BD2791BCC1099F83B04282B0508005212FCB threat=HEUR:Trojan.Script.Generic},{ MD5=5A90DDAAEA8646E84927E5DD7BAAA3E2 SHA1=CA2EEF839CF649E42EB4F7E618BD491B40340462 SHA256=1A73D4EA89E89C22B3B03E1A841882A59FCC1ED18299D6914DF4BC2E5CF05A44 threat=HEUR:Trojan.Script.Generic}] first_seen=21.02.2019 23:57 ip=93.115.27.83 ip_geo=lt ip_whois={ asn=16125 country=LT created=01.12.2016 net_name=CHERRYSERVERS-LT-DEDICATED net_range=93.115.27.0 - 93.115.27.255 updated=01.12.2016} last_seen=22.05.2019 19:18 popularity=5 threat_score=94 users_geo=de, jp, fr, it, ch, at, be, pl, es, dz - KL_IP_Reputation_Hash_SHA1
Regular expression
Event example for checking regular expressions
category=KL_IP_Reputation_Hash_SHA1.*matchedIndicator=(?<object>[^\s]*).*usrName=(?<login>[^\s]*)May 2 16:41:40 category=KL_IP_Reputation_Hash_SHA1 matchedIndicator=E23B0F6ECEFF56870908B2EC704F62ACB4E005AD url=- src=- ip=- md5=- sha1=E23B0F6ECEFF56870908B2EC704F62ACB4E005AD sha256=- usrName=- category=malware domains=k4d7ppv9.humanpchelp.pw, mwi49i2b.backbonecomputer.top, 9uq5mmw7.overseascomputer.pw, 9tqnii2s.motivationcomputer.pw, 4iaag9ng.luxurypchelp.pw, kxol25kx.pcserviceline.top, 7ifiye96.phoenixcomputerhelp.pw, tnv5yyvj.pcservicecatch.pw, y4ki19os.computercoral.top, pmayaidy.rankpcservice.top files=[{ MD5=61200D253ADD14C91CD64F2CB1F221CB SHA1=E23B0F6ECEFF56870908B2EC704F62ACB4E005AD SHA256=7FC582451A8D9EAF112A3CFC7EFF8EBC8A5FCB8480E42A8D2B5A4E0E3C12D793 threat=HEUR:Trojan.Script.Generic},{ MD5=06A2E41E9CDA9C19AF5FB29483687A56 SHA1=37ED2076FCC0365BA02210E18BBAB162D7338180 SHA256=9570F5C81FF906CD52EE42B5D24359B8A7CA4EC225C532A811699F1089847252 threat=HEUR:Trojan.Script.Generic},{ MD5=AA909F4A33A0D305C0ADF7FCD6DC95E5 SHA1=0A88A71A3C43F02075B7B3CB1A6ED1A603CC666E SHA256=96467635B09D64B29DEAF2A7923ADCD63C2E7F9308B80DDF46F251EBDB2E6A66 threat=HEUR:Trojan.Script.Generic},{ MD5=1D02D52FE17A040A2C7D7C4EE7020E6A SHA1=036D8147D00334824073A22C3D7016EE27643CBD SHA256=737117D867D8CC777AF09F635126C6867ADD08C47C74EDCF5636A84F3F14911B threat=HEUR:Trojan.Script.Generic},{ MD5=393F797A732D5FF35B6102B298349C65 SHA1=760C99F3FB4330BA7B9EB76780718E3023C345EE SHA256=5E86FE0A4DA6A1394DBC6BD2D0F7BD2791BCC1099F83B04282B0508005212FCB threat=HEUR:Trojan.Script.Generic},{ MD5=5A90DDAAEA8646E84927E5DD7BAAA3E2 SHA1=CA2EEF839CF649E42EB4F7E618BD491B40340462 SHA256=1A73D4EA89E89C22B3B03E1A841882A59FCC1ED18299D6914DF4BC2E5CF05A44 threat=HEUR:Trojan.Script.Generic}] first_seen=21.02.2019 23:57 ip=93.115.27.83 ip_geo=lt ip_whois={ asn=16125 country=LT created=01.12.2016 net_name=CHERRYSERVERS-LT-DEDICATED net_range=93.115.27.0 - 93.115.27.255 updated=01.12.2016} last_seen=22.05.2019 19:18 popularity=5 threat_score=94 users_geo=de, jp, fr, it, ch, at, be, pl, es, dz - KL_IP_Reputation_Hash_SHA256
Regular expression
Event example for checking regular expressions
category=KL_IP_Reputation_Hash_SHA256.*matchedIndicator=(?<object>[^\s]*).*usrName=(?<login>[^\s]*)May 2 16:41:40 category=KL_IP_Reputation_Hash_SHA256 matchedIndicator=7FC582451A8D9EAF112A3CFC7EFF8EBC8A5FCB8480E42A8D2B5A4E0E3C12D793 url=- src=- ip=- md5=- sha1=- sha256=7FC582451A8D9EAF112A3CFC7EFF8EBC8A5FCB8480E42A8D2B5A4E0E3C12D793 usrName=- category=malware domains=k4d7ppv9.humanpchelp.pw, mwi49i2b.backbonecomputer.top, 9uq5mmw7.overseascomputer.pw, 9tqnii2s.motivationcomputer.pw, 4iaag9ng.luxurypchelp.pw, kxol25kx.pcserviceline.top, 7ifiye96.phoenixcomputerhelp.pw, tnv5yyvj.pcservicecatch.pw, y4ki19os.computercoral.top, pmayaidy.rankpcservice.top files=[{ MD5=61200D253ADD14C91CD64F2CB1F221CB SHA1=E23B0F6ECEFF56870908B2EC704F62ACB4E005AD SHA256=7FC582451A8D9EAF112A3CFC7EFF8EBC8A5FCB8480E42A8D2B5A4E0E3C12D793 threat=HEUR:Trojan.Script.Generic},{ MD5=06A2E41E9CDA9C19AF5FB29483687A56 SHA1=37ED2076FCC0365BA02210E18BBAB162D7338180 SHA256=9570F5C81FF906CD52EE42B5D24359B8A7CA4EC225C532A811699F1089847252 threat=HEUR:Trojan.Script.Generic},{ MD5=AA909F4A33A0D305C0ADF7FCD6DC95E5 SHA1=0A88A71A3C43F02075B7B3CB1A6ED1A603CC666E SHA256=96467635B09D64B29DEAF2A7923ADCD63C2E7F9308B80DDF46F251EBDB2E6A66 threat=HEUR:Trojan.Script.Generic},{ MD5=1D02D52FE17A040A2C7D7C4EE7020E6A SHA1=036D8147D00334824073A22C3D7016EE27643CBD SHA256=737117D867D8CC777AF09F635126C6867ADD08C47C74EDCF5636A84F3F14911B threat=HEUR:Trojan.Script.Generic},{ MD5=393F797A732D5FF35B6102B298349C65 SHA1=760C99F3FB4330BA7B9EB76780718E3023C345EE SHA256=5E86FE0A4DA6A1394DBC6BD2D0F7BD2791BCC1099F83B04282B0508005212FCB threat=HEUR:Trojan.Script.Generic},{ MD5=5A90DDAAEA8646E84927E5DD7BAAA3E2 SHA1=CA2EEF839CF649E42EB4F7E618BD491B40340462 SHA256=1A73D4EA89E89C22B3B03E1A841882A59FCC1ED18299D6914DF4BC2E5CF05A44 threat=HEUR:Trojan.Script.Generic}] first_seen=21.02.2019 23:57 ip=93.115.27.83 ip_geo=lt ip_whois={ asn=16125 country=LT created=01.12.2016 net_name=CHERRYSERVERS-LT-DEDICATED net_range=93.115.27.0 - 93.115.27.255 updated=01.12.2016} last_seen=22.05.2019 19:18 popularity=5 threat_score=94 users_geo=de, jp, fr, it, ch, at, be, pl, es, dz - KL_Malicious_Hash_MD5
Regular expression
Event example for checking regular expressions
category=KL_Malicious_Hash_MD5.*md5=(?<object>[^\s]*).*usrName=(?<login>[^\s]*).*file_size=(?<size>[^\s]*).*threat=(?<objectname>[^\s]*)May 2 16:41:40 category=KL_Malicious_Hash_MD5 url=- md5=0F1DCBB2A888B99FAE72144087CAE565 sha1=- sha256=- ip=- usrName=VerifTestUserName MD5=0F1DCBB2A888B99FAE72144087CAE565 file_size=105472 file_type=PE first_seen=26.11.2015 13:06 geo=ru, ro, ua, tj, us, cz, kz, gb last_seen=14.01.2016 12:29 popularity=5 threat=UDS:DangerousObject.Multi.Generic - KL_Malicious_Hash_SHA1
Regular expression
Event example for checking regular expressions
category=KL_Malicious_Hash_SHA1.*sha1=(?<object>[^\s]*).*usrName=(?<login>[^\s]*).*file_size=(?<size>[^\s]*).*threat=(?<objectname>[^\s]*)May 2 16:41:40 category=KL_Malicious_Hash_SHA1 url=- md5=- sha1=6665856CE81F2B7382DEE72602F798B642F14140 sha256=- ip=- usrName=VerifTestUserName MD5=55D88612FEA8A8F36DE82E1278ABB02F SHA1=6665856CE81F2B7382DEE72602F798B642F14140 SHA256=275A021BBFB6489E54D471899F7DB9D1663FC695EC2FE2A2C4777AABF651FD0F file_size=68 first_seen=02.04.2010 22:07 last_seen=14.01.2016 13:41 popularity=5 threat=EICAR-Test-File - KL_Malicious_Hash_SHA256
Regular expression
Event example for checking regular expressions
category=KL_Malicious_Hash_SHA256.*sha256=(?<object>[^\s]*).*usrName=(?<login>[^\s]*).*file_size=(?<size>[^\s]*).*threat=(?<objectname>[^\s]*)May 2 16:41:40 category=KL_Malicious_Hash_SHA256 url=- md5=- sha1=- sha256=EC1D5E24A9F866F21118914445AB0A00A60F791B51478F3D0DD375A6BD45897D ip=- usrName=VerifTestUserName SHA1=C365DC5128FF0A607D78BFBAB36E08263DC66B18 SHA256=EC1D5E24A9F866F21118914445AB0A00A60F791B51478F3D0DD375A6BD45897D file_size=1696256 file_type=PE first_seen=15.07.2015 11:50 geo=ru, ua, by, dz, ir, eg, kz, mx, in, tr last_seen=14.01.2016 12:29 popularity=5 threat=HackTool.Win32.KRT.bw - KL_Malicious_URL
Regular expression
Event example for checking regular expressions
category=KL_Malicious_URL.*url=(?<url>[^\s]*).*usrName=(?<login>[^\s]*)May 2 16:41:40 category=KL_Malicious_URL url=http://sub1.submalicious_domain.malicious_domain_19.com md5=- sha1=- sha256=- ip=- usrName=VerifTestUserName IP=217.23.14.223 first_seen=14.01.2016 02:42 geo=ru, kz, ro, ua, by, cz id=9524476 last_seen=14.01.2016 13:36 mask=*.submalicious_domain.malicious_domain_19.com popularity=5 type=19 - KL_Malicious_URL_Hash_MD5
Regular expression
Event example for checking regular expressions
category=KL_Malicious_URL_Hash_MD5.*matchedIndicator=(?<object>[^\s]*).*usrName=(?<login>[^\s]*)May 2 16:41:40 category=KL_Malicious_URL_Hash_MD5 matchedIndicator=C735608E2DDE63857C3877AE438EBF78 url=- src=- ip=- md5=C735608E2DDE63857C3877AE438EBF78 sha1=- sha256=- usrName=- IP=104.27.160.251, 104.27.161.251, 145.239.252.74, 46.35.111.137, 207.244.89.108, 54.37.87.37, 207.244.89.90, 77.111.246.8, 131.173.16.52 category=Malware files=[{ MD5=C735608E2DDE63857C3877AE438EBF78 SHA1=9FB04AB8756742E9903A9A77566938DC9D83138C SHA256=127E83998D65FD80328D89B87B9C4CB5756C57FCC03189FAC5B7D77D4FB48FC5 threat=HEUR:Trojan.Script.Miner.gen}] first_seen=15.03.2019 14:27 geo=es, de, it, ru, ve, pl, pt, jp, kz, mx id=29703667 last_seen=23.05.2019 14:12 mask=tercabilis.info popularity=4 type=1 whois={ NS=art.ns.cloudflare.com, olga.ns.cloudflare.com NS_ips=173.245.58.137, 173.245.59.102 country=FR created=02.10.2018 domain=tercabilis.info expires=02.10.2019 org=NETIM registrar_name=NETIM SARL updated=01.12.2018} - KL_Malicious_URL_Hash_SHA1
Regular expression
Event example for checking regular expressions
category=KL_Malicious_URL_Hash_SHA1.*matchedIndicator=(?<object>[^\s]*).*usrName=(?<login>[^\s]*)May 2 16:41:40 category=KL_Malicious_URL_Hash_SHA1 matchedIndicator=9FB04AB8756742E9903A9A77566938DC9D83138C url=- src=- ip=- md5=- sha1=9FB04AB8756742E9903A9A77566938DC9D83138C sha256=- usrName=- IP=163.172.129.78, 212.47.250.90 category=Malware files=[{ MD5=9096549542B5A4E711BF04732416AA97 SHA1=4616FF9FBFF692535C6F0D9BD347CC0593A1F6B8 threat=HEUR:Trojan.Script.Miner.gen},{ MD5=6CBF2B0ADC72F64913EDE949A3F93B2D SHA1=5BB602A5A3AE5C685F0EB9CF2BFE9546DFC5832A SHA256=E804F6ADF2B7C99A8E0B158E880DF3172131CFAD7D796A75CBC2E46606371D2E threat=HEUR:Trojan.Script.Miner.gen},{ MD5=C735608E2DDE63857C3877AE438EBF78 SHA1=9FB04AB8756742E9903A9A77566938DC9D83138C SHA256=127E83998D65FD80328D89B87B9C4CB5756C57FCC03189FAC5B7D77D4FB48FC5 threat=HEUR:Trojan.Script.Miner.gen}] first_seen=29.05.2018 15:54 geo=ru, kz, by, ua id=23128232 last_seen=23.03.2019 12:07 mask=play.on.animeteatr.ru popularity=3 type=2 - KL_Malicious_URL_Hash_SHA256
Regular expression
Event example for checking regular expressions
category=KL_Malicious_URL_Hash_SHA256.*matchedIndicator=(?<object>[^\s]*).*usrName=(?<login>[^\s]*)May 2 16:41:40 category=KL_Malicious_URL_Hash_SHA256 matchedIndicator=127E83998D65FD80328D89B87B9C4CB5756C57FCC03189FAC5B7D77D4FB48FC5 url=- src=- ip=- md5=- sha1=- sha256=127E83998D65FD80328D89B87B9C4CB5756C57FCC03189FAC5B7D77D4FB48FC5 usrName=- IP=163.172.129.78, 212.47.250.90, 173.192.191.169, 167.99.216.96, 89.238.177.226 category=Malware files=[{ MD5=C735608E2DDE63857C3877AE438EBF78 SHA1=9FB04AB8756742E9903A9A77566938DC9D83138C SHA256=127E83998D65FD80328D89B87B9C4CB5756C57FCC03189FAC5B7D77D4FB48FC5 threat=HEUR:Trojan.Script.Miner.gen},{ MD5=978E8C1CB071387ABBB4A673FF918BB9 SHA1=AFAEEE65BB483994FAC36A6B97F10B2BAA51F832 SHA256=3CFAACB2E8EE3E7CC5685DEDDFED7E34BF7595015307FEE64DD3C196C1D4ED93 threat=HEUR:Trojan.Script.Miner.gen},{ MD5=9096549542B5A4E711BF04732416AA97 SHA1=4616FF9FBFF692535C6F0D9BD347CC0593A1F6B8 threat=HEUR:Trojan.Script.Miner.gen},{ MD5=3FF0CF473B1E8FEB3BC018AF999DF4F5 SHA1=6813E9BB538F4AE1290411DD6AC48D615B5A4F21 threat=HEUR:Trojan.Script.Miner.gen},{ MD5=6CBF2B0ADC72F64913EDE949A3F93B2D SHA1=5BB602A5A3AE5C685F0EB9CF2BFE9546DFC5832A SHA256=E804F6ADF2B7C99A8E0B158E880DF3172131CFAD7D796A75CBC2E46606371D2E threat=HEUR:Trojan.Script.Miner.gen},{ MD5=44A27780FD4ABF64BF4EBB5584857160 SHA1=C9552F0DBF8A213556F3CC0CBD98CBFD157362F9 SHA256=EB703A25657D70CD85059A1AFD4720DF5273C4775EE05C6A2B1D3FBFD84D767C threat=HEUR:Trojan.Script.Miner.gen}] first_seen=29.05.2018 15:54 geo=de, gr, it, gb, pl, dz, hu, at, br, ch id=23128262 last_seen=07.04.2019 20:16 mask=play.play1.videos.vidto.me popularity=4 type=2 whois={ MX=mail.vidto.me, mail2.vidto.me MX_ips=158.69.116.96 NS=pns1.cloudns.net, pns2.cloudns.net, pns3.cloudns.net, pns4.cloudns.net NS_ips=185.136.96.111, 185.136.97.111, 185.136.98.111, 185.136.99.111 country=SE created=21.06.2012 domain=vidto.me expires=21.06.2021 org=Shield Whois registrar_name=AB NameISP updated=23.11.2018} - KL_Mobile_BotnetCnC_Hash_MD5
Regular expression
Event example for checking regular expressions
category=KL_Mobile_BotnetCnC_Hash_MD5.*url=(?<url>[^\s]*).*usrName=(?<login>[^\s]*).*Mask=(?<object>[^\s{}]*).*verdict=(?<objectname>[^\s]*)May 2 16:41:40 category=KL_Mobile_BotnetCnC_Hash_MD5 url=- md5=12B8D137C80AE5E995EC355524594F3B sha1=- sha256=- ip=- usrName=VerifTestUserName Behaviour=Get Location, Collect phone info, Read SMS, Get Accounts, Read Contacts Details=[{Mask=*.subdbotnet_domain_19.dbotnet_domain.com}] MD5=12B8D137C80AE5E995EC355524594F3B verdict=Evaluation-CnC.AndroidOS - KL_Mobile_BotnetCnC_Hash_SHA1
Regular expression
Event example for checking regular expressions
category=KL_Mobile_BotnetCnC_Hash_SHA1.*sha1=(?<object>[^\s]*).*usrName=(?<login>[^\s]*).*verdict=(?<objectname>[^\s]*)May 2 16:41:40 category=KL_Mobile_BotnetCnC_Hash_SHA1 url=- md5=- sha1=AFAEEE65BB483994FAC36A6B97F10B2BAA51F832 sha256=- ip=- usrName=VerifTestUserName Behaviour=Get Location, Collect phone info, Read SMS, Get Accounts, Read Contacts - KL_Mobile_BotnetCnC_Hash_SHA256
Regular expression
Event example for checking regular expressions
category=KL_Mobile_BotnetCnC_Hash_SHA256.*sha256=(?<object>[^\s]*).*usrName=(?<login>[^\s]*).*verdict=(?<objectname>[^\s]*)May 2 16:41:40 category=KL_Mobile_BotnetCnC_Hash_SHA256 url=- md5=- sha1=- sha256=E804F6ADF2B7C99A8E0B158E880DF3172131CFAD7D796A75CBC2E46606371D2E ip=- usrName=VerifTestUserName Behaviour=Get Location, Collect phone info, Read SMS, Get Accounts, Read Contacts - KL_Mobile_BotnetCnC_URL
Regular expression
Event example for checking regular expressions
category=KL_Mobile_BotnetCnC_URL.*url=(?<url>[^\s]*).*usrName=(?<login>[^\s]*).*Mask=(?<object>[^\s{}]*).*verdict=(?<objectname>[^\s]*)May 2 16:41:40 category=KL_Mobile_BotnetCnC_URL url=baddomain.subdbotnet_domain_19.dbotnet_domain.com md5=- sha1=- sha256=- ip=- usrName=VerifTestUserName Behaviour=Get Location, Collect phone info, Read SMS, Get Accounts, Read Contacts Details=[{Mask=*.subdbotnet_domain_19.dbotnet_domain.com}] MD5=12B8D137C80AE5E995EC355524594F3B verdict=Evaluation-CnC.AndroidOS - KL_Mobile_Malicious_Hash_MD5
Regular expression
Event example for checking regular expressions
category=KL_Mobile_Malicious_Hash_MD5.*md5=(?<object>[^\s]*).*usrName=(?<login>[^\s]*).*file_size=(?<size>[^\s]*).*threat=(?<objectname>[^\s]*)May 2 16:41:40 category=KL_Mobile_Malicious_Hash_MD5 url=- md5=A0D02A618E0FB400EDC0E210DD975E21 sha1=- sha256=- ip=- usrName=VerifTestUserName MD5=A0D02A618E0FB400EDC0E210DD975E21 SHA1=AB04F1F9CFE33EADB7ECC75EDF7A79EE1E22AEE6 SHA256=5E658421AE871ED9EA85A352050B7F27525821649EA0A6863B62BA7BDED2C074 file_size=378980 first_seen=10.09.2015 06:47 geo=ru, in, id, ir, my, bd, ua, br, dz, ro last_seen=14.01.2016 13:18 popularity=5 threat=HEUR:Trojan.AndroidOS.Guerrilla.b - KL_Mobile_Malicious_Hash_SHA1
Regular expression
Event example for checking regular expressions
category=KL_Mobile_Malicious_Hash_SHA1.*sha1=(?<object>[^\s]*).*usrName=(?<login>[^\s]*).*file_size=(?<size>[^\s]*).*threat=(?<objectname>[^\s]*)May 2 16:41:40 category=KL_Mobile_Malicious_Hash_SHA1 url=- md5=- sha1=9DA11F40D00E37D27A7B41EE7C741F4CF0E52AE6 sha256=- ip=- usrName=VerifTestUserName MD5=F9E8AB7B3E0B23203B678772AFD4CDD1 SHA1=9DA11F40D00E37D27A7B41EE7C741F4CF0E52AE6 SHA256=111319613DA28D6D59282EBC2730E0448717CD55B36050B9142167936070F9EE file_size=236096 first_seen=15.12.2015 20:59 geo=ru, ua, in, tr, id, dz, mx, kz, by, ro last_seen=14.01.2016 13:23 popularity=5 threat=HEUR:Trojan.AndroidOS.Ztorg.a - KL_Mobile_Malicious_Hash_SHA256
Regular expression
Event example for checking regular expressions
category=KL_Mobile_Malicious_Hash_SHA256.*sha256=(?<object>[^\s]*).*usrName=(?<login>[^\s]*).*file_size=(?<size>[^\s]*).*threat=(?<objectname>[^\s]*)May 2 16:41:40 category=KL_Mobile_Malicious_Hash_SHA256 url=- md5=- sha1=- sha256=3F52BBBA93A3C757D781ED4D8D526632995FD2F712788D24C528B2F5DB6E3C42 ip=- usrName=VerifTestUserName MD5=A8315A5D4C8ACB982372C16B83BAEAAA SHA1=ABBB5A760C3203CB460D60279269F5568D89F848 SHA256=3F52BBBA93A3C757D781ED4D8D526632995FD2F712788D24C528B2F5DB6E3C42 file_size=444408 first_seen=01.08.2015 00:08 geo=ru, ua, kz, ro, by, cn, tj, uz, az, md last_seen=14.01.2016 13:18 popularity=5 threat=HEUR:Trojan-SMS.AndroidOS.Podec.a - KL_Phishing_URL
Regular expression
Event example for checking regular expressions
category=KL_Phishing_URL.*url=(?<url>[^\s]*).*usrName=(?<login>[^\s]*)May 2 16:41:40 category=KL_Phishing_URL url=http://d.subphishing_domain.phishing_domain_19.com md5=- sha1=- sha256=- ip=- usrName=VerifTestUserName IP=104.168.159.146, 138.201.0.229, 138.201.0.231, 138.201.0.230, 78.46.185.21, 78.46.185.23, 78.46.185.12, 78.46.185.3, 78.46.185.16, 78.46.185.28 first_seen=12.01.2016 12:50 geo=br, pt, us id=9508721 last_seen=14.01.2016 13:36 mask=*.subphishing_domain.phishing_domain_19.com popularity=5 type=19 - KL_Ransomware_URL
Regular expression
Event example for checking regular expressions
category=KL_Ransomware_URL.*url=(?<url>[^\s]*).*usrName=(?<login>[^\s]*)May 2 16:41:40 category=KL_Ransomware_URL matchedIndicator=fakess123r.nu url=fakess123r.nu src=192.168.0.0 ip=- md5=- sha1=- sha256=- usrName=VerifTestUserName first_seen=10.08.2016 14:18 id=0 last_seen=22.12.2017 15:12 mask=fakess123r.nu popularity=1 type=1 - KL_Ransomware_URL_Hash_MD5
Regular expression
Event example for checking regular expressions
category=KL_Ransomware_URL_Hash_MD5.*md5=(?<object>[^\s]*).*usrName=(?<login>[^\s]*)May 2 16:41:40 category=KL_Ransomware_URL_Hash_MD5 matchedIndicator=DAFECEDABFE0F3AB372A7C83B84CEFF6 url=- src=- ip=- md5=DAFECEDABFE0F3AB372A7C83B84CEFF6 sha1=- sha256=- usrName=- IP=104.27.174.162, 104.27.175.162, 188.166.67.166, 193.176.84.67, 185.232.23.3, 5.182.27.20, 178.128.153.190, 78.24.218.108, 158.58.172.76, 2.59.214.27 files=[{ MD5=DAFECEDABFE0F3AB372A7C83B84CEFF6 SHA1=0D68EE713180A5BF73F7C74CE00F067D2BE5CF7C SHA256=7DD78D2CBFF85A80954558C5C01986FC5D9099C87ECE796A374626EB76BE037D threat=HEUR:Trojan.Win32.Generic}] first_seen=01.04.2019 18:17 geo=ru, kz, ua, by, de, lt, ro, pl, md, it id=30341045 last_seen=23.05.2019 14:19 mask=sama-berli.info popularity=5 type=1 whois={ NS=dora.ns.cloudflare.com, zod.ns.cloudflare.com NS_ips=173.245.58.108, 173.245.59.250 country=UA created=24.01.2019 domain=sama-berli.info expires=24.01.2020 org=ZAO Sigva registrar_email=abuse@reg.ru registrar_name=Limited Liability Company "Registrar of domain names REG.RU" updated=29.03.2019} - KL_Ransomware_URL_Hash_SHA1
Regular expression
Event example for checking regular expressions
category=KL_Ransomware_URL_Hash_SHA1.*matchedIndicator=(?<object>[^\s]*).*usrName=(?<login>[^\s]*)May 2 16:41:40 category=KL_Ransomware_URL_Hash_SHA1 matchedIndicator=0D68EE713180A5BF73F7C74CE00F067D2BE5CF7C url=- src=- ip=- md5=- sha1=0D68EE713180A5BF73F7C74CE00F067D2BE5CF7C sha256=- usrName=- IP=104.27.174.162, 104.27.175.162, 188.166.67.166, 193.176.84.67, 185.232.23.3, 5.182.27.20, 178.128.153.190, 78.24.218.108, 158.58.172.76, 2.59.214.27 files=[{ MD5=DAFECEDABFE0F3AB372A7C83B84CEFF6 SHA1=0D68EE713180A5BF73F7C74CE00F067D2BE5CF7C SHA256=7DD78D2CBFF85A80954558C5C01986FC5D9099C87ECE796A374626EB76BE037D threat=HEUR:Trojan.Win32.Generic}] first_seen=01.04.2019 18:17 geo=ru, kz, ua, by, de, lt, ro, pl, md, it id=30341045 last_seen=23.05.2019 14:19 mask=sama-berli.info popularity=5 type=1 whois={ NS=dora.ns.cloudflare.com, zod.ns.cloudflare.com NS_ips=173.245.58.108, 173.245.59.250 country=UA created=24.01.2019 domain=sama-berli.info expires=24.01.2020 org=ZAO Sigva registrar_email=abuse@reg.ru registrar_name=Limited Liability Company "Registrar of domain names REG.RU" updated=29.03.2019} - KL_Ransomware_URL_Hash_SHA256
Regular expression
Event example for checking regular expressions
category=KL_Ransomware_URL_Hash_SHA256.*matchedIndicator=(?<object>[^\s]*).*usrName=(?<login>[^\s]*)May 2 16:41:40 category=KL_Ransomware_URL_Hash_SHA256 matchedIndicator=7DD78D2CBFF85A80954558C5C01986FC5D9099C87ECE796A374626EB76BE037D url=- src=- ip=- md5=- sha1=- sha256=7DD78D2CBFF85A80954558C5C01986FC5D9099C87ECE796A374626EB76BE037D usrName=- IP=104.27.174.162, 104.27.175.162, 188.166.67.166, 193.176.84.67, 185.232.23.3, 5.182.27.20, 178.128.153.190, 78.24.218.108, 158.58.172.76, 2.59.214.27 files=[{ MD5=DAFECEDABFE0F3AB372A7C83B84CEFF6 SHA1=0D68EE713180A5BF73F7C74CE00F067D2BE5CF7C SHA256=7DD78D2CBFF85A80954558C5C01986FC5D9099C87ECE796A374626EB76BE037D threat=HEUR:Trojan.Win32.Generic}] first_seen=01.04.2019 18:17 geo=ru, kz, ua, by, de, lt, ro, pl, md, it id=30341045 last_seen=23.05.2019 14:19 mask=sama-berli.info popularity=5 type=1 whois={ NS=dora.ns.cloudflare.com, zod.ns.cloudflare.com NS_ips=173.245.58.108, 173.245.59.250 country=UA created=24.01.2019 domain=sama-berli.info expires=24.01.2020 org=ZAO Sigva registrar_email=abuse@reg.ru registrar_name=Limited Liability Company "Registrar of domain names REG.RU" updated=29.03.2019} - KL_Exploit_Hash_MD5
Regular expression
Event example for checking regular expressions
category=KL_Exploit_Hash_MD5.*md5=(?<object>[^\s]*).*usrName=(?<login>[^\s]*)May 2 16:41:40 category=KL_Exploit_Hash_MD5 matchedIndicator=DAFECEDABFE0F3AB372A7C83B84CEFF6 url=- src=- ip=- md5=DAFECEDABFE0F3AB372A7C83B84CEFF6 sha1=- sha256=- usrName=- IP=104.27.174.162, 104.27.175.162, 188.166.67.166, 193.176.84.67, 185.232.23.3, 5.182.27.20, 178.128.153.190, 78.24.218.108, 158.58.172.76, 2.59.214.27 files=[{ MD5=DAFECEDABFE0F3AB372A7C83B84CEFF6 SHA1=0D68EE713180A5BF73F7C74CE00F067D2BE5CF7C SHA256=7DD78D2CBFF85A80954558C5C01986FC5D9099C87ECE796A374626EB76BE037D threat=HEUR:Trojan.Win32.Generic}] first_seen=01.04.2019 18:17 geo=ru, kz, ua, by, de, lt, ro, pl, md, it id=30341045 last_seen=23.05.2019 14:19 mask=sama-berli.info popularity=5 type=1 whois={ NS=dora.ns.cloudflare.com, zod.ns.cloudflare.com NS_ips=173.245.58.108, 173.245.59.250 country=UA created=24.01.2019 domain=sama-berli.info expires=24.01.2020 org=ZAO Sigva registrar_email=abuse@reg.ru registrar_name=Limited Liability Company "Registrar of domain names REG.RU" updated=29.03.2019} - KL_Exploit_Hash_SHA1
Regular expression
Event example for checking regular expressions
category=KL_Exploit_Hash_SHA1.*sha1=(?<object>[^\s]*).*usrName=(?<login>[^\s]*)May 2 16:41:40 category=KL_Exploit_Hash_SHA1 matchedIndicator=0D68EE713180A5BF73F7C74CE00F067D2BE5CF7C url=- src=- ip=- md5=- sha1=0D68EE713180A5BF73F7C74CE00F067D2BE5CF7C sha256=- usrName=- IP=104.27.174.162, 104.27.175.162, 188.166.67.166, 193.176.84.67, 185.232.23.3, 5.182.27.20, 178.128.153.190, 78.24.218.108, 158.58.172.76, 2.59.214.27 files=[{ MD5=DAFECEDABFE0F3AB372A7C83B84CEFF6 SHA1=0D68EE713180A5BF73F7C74CE00F067D2BE5CF7C SHA256=7DD78D2CBFF85A80954558C5C01986FC5D9099C87ECE796A374626EB76BE037D threat=HEUR:Trojan.Win32.Generic}] first_seen=01.04.2019 18:17 geo=ru, kz, ua, by, de, lt, ro, pl, md, it id=30341045 last_seen=23.05.2019 14:19 mask=sama-berli.info popularity=5 type=1 whois={ NS=dora.ns.cloudflare.com, zod.ns.cloudflare.com NS_ips=173.245.58.108, 173.245.59.250 country=UA created=24.01.2019 domain=sama-berli.info expires=24.01.2020 org=ZAO Sigva registrar_email=abuse@reg.ru registrar_name=Limited Liability Company "Registrar of domain names REG.RU" updated=29.03.2019} - KL_Exploit_Hash_SHA256
Regular expression
Event example for checking regular expressions
category=KL_Exploit_Hash_SHA256.*sha256=(?<object>[^\s]*).*usrName=(?<login>[^\s]*)May 2 16:41:40 category=KL_Exploit_Hash_SHA256 matchedIndicator=7DD78D2CBFF85A80954558C5C01986FC5D9099C87ECE796A374626EB76BE037D url=- src=- ip=- md5=- sha1=- sha256=7DD78D2CBFF85A80954558C5C01986FC5D9099C87ECE796A374626EB76BE037D usrName=- IP=104.27.174.162, 104.27.175.162, 188.166.67.166, 193.176.84.67, 185.232.23.3, 5.182.27.20, 178.128.153.190, 78.24.218.108, 158.58.172.76, 2.59.214.27 files=[{ MD5=DAFECEDABFE0F3AB372A7C83B84CEFF6 SHA1=0D68EE713180A5BF73F7C74CE00F067D2BE5CF7C SHA256=7DD78D2CBFF85A80954558C5C01986FC5D9099C87ECE796A374626EB76BE037D threat=HEUR:Trojan.Win32.Generic}] first_seen=01.04.2019 18:17 geo=ru, kz, ua, by, de, lt, ro, pl, md, it id=30341045 last_seen=23.05.2019 14:19 mask=sama-berli.info popularity=5 type=1 whois={ NS=dora.ns.cloudflare.com, zod.ns.cloudflare.com NS_ips=173.245.58.108, 173.245.59.250 country=UA created=24.01.2019 domain=sama-berli.info expires=24.01.2020 org=ZAO Sigva registrar_email=abuse@reg.ru registrar_name=Limited Liability Company "Registrar of domain names REG.RU" updated=29.03.2019} - KL_IoT_Hash_MD5
Regular expression
Event example for checking regular expressions
category=KL_IoT_Hash_MD5.*md5=(?<object>[^\s]*).*usrName=(?<login>[^\s]*)May 2 16:41:40 category=KL_IoT_Hash_MD5 matchedIndicator=DAFECEDABFE0F3AB372A7C83B84CEFF6 url=- src=- ip=- md5=DAFECEDABFE0F3AB372A7C83B84CEFF6 sha1=- sha256=- usrName=- IP=104.27.174.162, 104.27.175.162, 188.166.67.166, 193.176.84.67, 185.232.23.3, 5.182.27.20, 178.128.153.190, 78.24.218.108, 158.58.172.76, 2.59.214.27 files=[{ MD5=DAFECEDABFE0F3AB372A7C83B84CEFF6 SHA1=0D68EE713180A5BF73F7C74CE00F067D2BE5CF7C SHA256=7DD78D2CBFF85A80954558C5C01986FC5D9099C87ECE796A374626EB76BE037D threat=HEUR:Trojan.Win32.Generic}] first_seen=01.04.2019 18:17 geo=ru, kz, ua, by, de, lt, ro, pl, md, it id=30341045 last_seen=23.05.2019 14:19 mask=sama-berli.info popularity=5 type=1 whois={ NS=dora.ns.cloudflare.com, zod.ns.cloudflare.com NS_ips=173.245.58.108, 173.245.59.250 country=UA created=24.01.2019 domain=sama-berli.info expires=24.01.2020 org=ZAO Sigva registrar_email=abuse@reg.ru registrar_name=Limited Liability Company "Registrar of domain names REG.RU" updated=29.03.2019} - KL_IoT_Hash_SHA1
Regular expression
Event example for checking regular expressions
category=KL_IoT_Hash_SHA1.*sha1=(?<object>[^\s]*).*usrName=(?<login>[^\s]*)May 2 16:41:40 category=KL_IoT_Hash_MD5 matchedIndicator=0D68EE713180A5BF73F7C74CE00F067D2BE5CF7C url=- src=- ip=- md5=- sha1=0D68EE713180A5BF73F7C74CE00F067D2BE5CF7C sha256=- usrName=- IP=104.27.174.162, 104.27.175.162, 188.166.67.166, 193.176.84.67, 185.232.23.3, 5.182.27.20, 178.128.153.190, 78.24.218.108, 158.58.172.76, 2.59.214.27 files=[{ MD5=DAFECEDABFE0F3AB372A7C83B84CEFF6 SHA1=0D68EE713180A5BF73F7C74CE00F067D2BE5CF7C SHA256=7DD78D2CBFF85A80954558C5C01986FC5D9099C87ECE796A374626EB76BE037D threat=HEUR:Trojan.Win32.Generic}] first_seen=01.04.2019 18:17 geo=ru, kz, ua, by, de, lt, ro, pl, md, it id=30341045 last_seen=23.05.2019 14:19 mask=sama-berli.info popularity=5 type=1 whois={ NS=dora.ns.cloudflare.com, zod.ns.cloudflare.com NS_ips=173.245.58.108, 173.245.59.250 country=UA created=24.01.2019 domain=sama-berli.info expires=24.01.2020 org=ZAO Sigva registrar_email=abuse@reg.ru registrar_name=Limited Liability Company "Registrar of domain names REG.RU" updated=29.03.2019} - KL_IoT_Hash_SHA256
Regular expression
Event example for checking regular expressions
category=KL_IoT_URL.*url=(?<url>[^\s]*).*usrName=(?<login>[^\s]*)May 2 16:41:40 category=KL_IoT_Hash_SHA256 matchedIndicator=7DD78D2CBFF85A80954558C5C01986FC5D9099C87ECE796A374626EB76BE037D url=- src=- ip=- md5=- sha1=- sha256=7DD78D2CBFF85A80954558C5C01986FC5D9099C87ECE796A374626EB76BE037D usrName=- IP=104.27.174.162, 104.27.175.162, 188.166.67.166, 193.176.84.67, 185.232.23.3, 5.182.27.20, 178.128.153.190, 78.24.218.108, 158.58.172.76, 2.59.214.27 files=[{ MD5=DAFECEDABFE0F3AB372A7C83B84CEFF6 SHA1=0D68EE713180A5BF73F7C74CE00F067D2BE5CF7C SHA256=7DD78D2CBFF85A80954558C5C01986FC5D9099C87ECE796A374626EB76BE037D threat=HEUR:Trojan.Win32.Generic}] first_seen=01.04.2019 18:17 geo=ru, kz, ua, by, de, lt, ro, pl, md, it id=30341045 last_seen=23.05.2019 14:19 mask=sama-berli.info popularity=5 type=1 whois={ NS=dora.ns.cloudflare.com, zod.ns.cloudflare.com NS_ips=173.245.58.108, 173.245.59.250 country=UA created=24.01.2019 domain=sama-berli.info expires=24.01.2020 org=ZAO Sigva registrar_email=abuse@reg.ru registrar_name=Limited Liability Company "Registrar of domain names REG.RU" updated=29.03.2019} - KL_IoT_URL
Regular expression
Event example for checking regular expressions
category=KL_IoT_Hash_SHA256.*sha256=(?<object>[^\s]*).*usrName=(?<login>[^\s]*)May 2 16:41:40 category=KL_IoT_URL matchedIndicator=fakess123r.nu url=fakess123r.nu src=192.168.0.0 ip=- md5=- sha1=- sha256=- usrName=VerifTestUserName first_seen=10.08.2016 14:18 id=0 last_seen=22.12.2017 15:12 mask=fakess123r.nu popularity=1 type=1 - KL_Vulnerable_File_Hash_MD5
Regular expression
Event example for checking regular expressions
category=KL_Vulnerable_File_Hash_MD5.*md5=(?<object>[^\s]*).*usrName=(?<login>[^\s]*)May 2 16:41:40 category=KL_Vulnerable_File_Hash_MD5 matchedIndicator=DAFECEDABFE0F3AB372A7C83B84CEFF6 url=- src=- ip=- md5=DAFECEDABFE0F3AB372A7C83B84CEFF6 sha1=- sha256=- usrName=- IP=104.27.174.162, 104.27.175.162, 188.166.67.166, 193.176.84.67, 185.232.23.3, 5.182.27.20, 178.128.153.190, 78.24.218.108, 158.58.172.76, 2.59.214.27 files=[{ MD5=DAFECEDABFE0F3AB372A7C83B84CEFF6 SHA1=0D68EE713180A5BF73F7C74CE00F067D2BE5CF7C SHA256=7DD78D2CBFF85A80954558C5C01986FC5D9099C87ECE796A374626EB76BE037D threat=HEUR:Trojan.Win32.Generic}] first_seen=01.04.2019 18:17 geo=ru, kz, ua, by, de, lt, ro, pl, md, it id=30341045 last_seen=23.05.2019 14:19 mask=sama-berli.info popularity=5 type=1 whois={ NS=dora.ns.cloudflare.com, zod.ns.cloudflare.com NS_ips=173.245.58.108, 173.245.59.250 country=UA created=24.01.2019 domain=sama-berli.info expires=24.01.2020 org=ZAO Sigva registrar_email=abuse@reg.ru registrar_name=Limited Liability Company "Registrar of domain names REG.RU" updated=29.03.2019} - KL_Vulnerable_File_Hash_SHA1
Regular expression
Event example for checking regular expressions
category=KL_Vulnerable_File_Hash_SHA1.*sha1=(?<object>[^\s]*).*usrName=(?<login>[^\s]*)May 2 16:41:40 category=KL_Vulnerable_File_Hash_SHA1 matchedIndicator=0D68EE713180A5BF73F7C74CE00F067D2BE5CF7C url=- src=- ip=- md5=- sha1=0D68EE713180A5BF73F7C74CE00F067D2BE5CF7C sha256=- usrName=- IP=104.27.174.162, 104.27.175.162, 188.166.67.166, 193.176.84.67, 185.232.23.3, 5.182.27.20, 178.128.153.190, 78.24.218.108, 158.58.172.76, 2.59.214.27 files=[{ MD5=DAFECEDABFE0F3AB372A7C83B84CEFF6 SHA1=0D68EE713180A5BF73F7C74CE00F067D2BE5CF7C SHA256=7DD78D2CBFF85A80954558C5C01986FC5D9099C87ECE796A374626EB76BE037D threat=HEUR:Trojan.Win32.Generic}] first_seen=01.04.2019 18:17 geo=ru, kz, ua, by, de, lt, ro, pl, md, it id=30341045 last_seen=23.05.2019 14:19 mask=sama-berli.info popularity=5 type=1 whois={ NS=dora.ns.cloudflare.com, zod.ns.cloudflare.com NS_ips=173.245.58.108, 173.245.59.250 country=UA created=24.01.2019 domain=sama-berli.info expires=24.01.2020 org=ZAO Sigva registrar_email=abuse@reg.ru registrar_name=Limited Liability Company "Registrar of domain names REG.RU" updated=29.03.2019} - KL_Vulnerable_File_Hash_SHA256
Regular expression
Event example for checking regular expressions
category=KL_Vulnerable_File_Hash_SHA256.*sha256=(?<object>[^\s]*).*usrName=(?<login>[^\s]*)May 2 16:41:40 category= KL_Vulnerable_File_Hash_SHA256 matchedIndicator=7DD78D2CBFF85A80954558C5C01986FC5D9099C87ECE796A374626EB76BE037D url=- src=- ip=- md5=- sha1=- sha256=7DD78D2CBFF85A80954558C5C01986FC5D9099C87ECE796A374626EB76BE037D usrName=- IP=104.27.174.162, 104.27.175.162, 188.166.67.166, 193.176.84.67, 185.232.23.3, 5.182.27.20, 178.128.153.190, 78.24.218.108, 158.58.172.76, 2.59.214.27 files=[{ MD5=DAFECEDABFE0F3AB372A7C83B84CEFF6 SHA1=0D68EE713180A5BF73F7C74CE00F067D2BE5CF7C SHA256=7DD78D2CBFF85A80954558C5C01986FC5D9099C87ECE796A374626EB76BE037D threat=HEUR:Trojan.Win32.Generic}] first_seen=01.04.2019 18:17 geo=ru, kz, ua, by, de, lt, ro, pl, md, it id=30341045 last_seen=23.05.2019 14:19 mask=sama-berli.info popularity=5 type=1 whois={ NS=dora.ns.cloudflare.com, zod.ns.cloudflare.com NS_ips=173.245.58.108, 173.245.59.250 country=UA created=24.01.2019 domain=sama-berli.info expires=24.01.2020 org=ZAO Sigva registrar_email=abuse@reg.ru registrar_name=Limited Liability Company "Registrar of domain names REG.RU" updated=29.03.2019}
Step 5. Adding Kaspersky CyberTrace policy
This section describes how you can add a Kaspersky CyberTrace policy to LogRhythm.
To add a Kaspersky CyberTrace policy to LogRhythm:
- Run LogRhythm Console.
- Select Deployment Manager > Log Processing Policies.
- Click the New button (
 ).
).The Log Source Type Selector window opens.
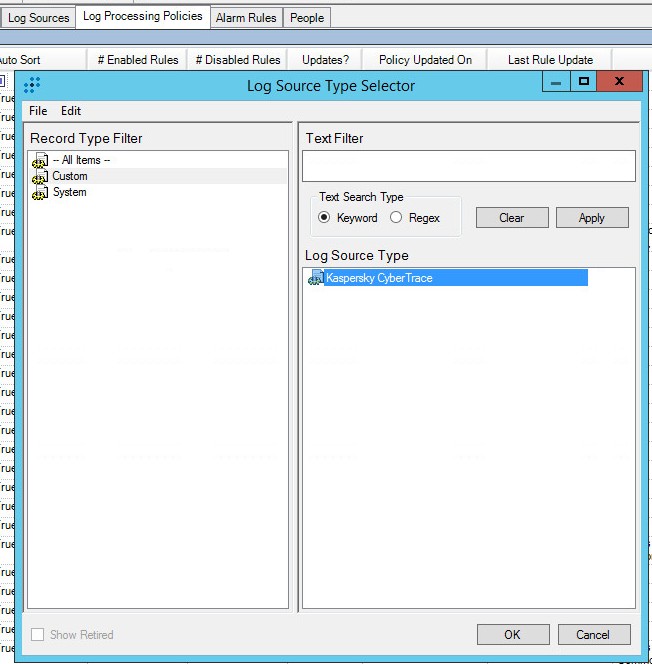
Log Source Type Selector window
- In the Log Source Type list, select Kaspersky CyberTrace.
- Click OK.
- In the MPE Policy Editor window that opens, in the Name field, type the policy name (
CyberTrace Policy).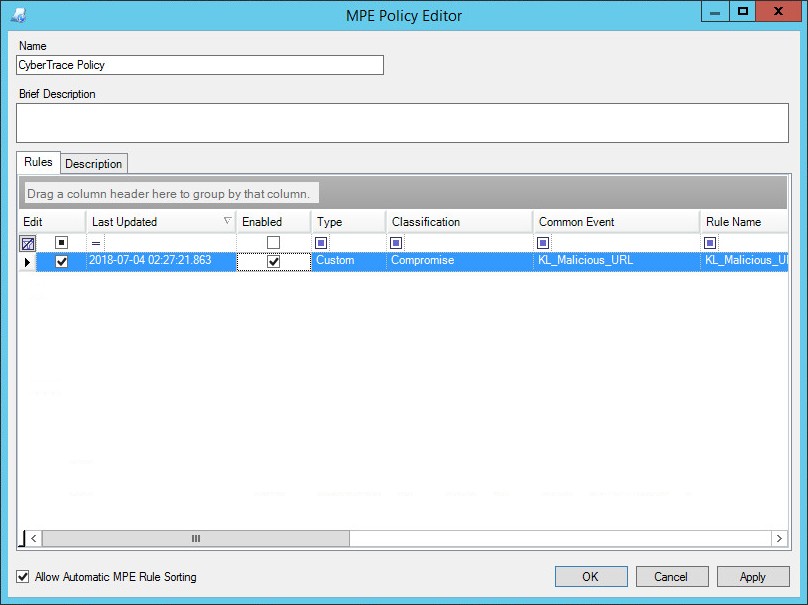
MPE Policy Editor window
- On the Rules tab, edit the properties of the Kaspersky CyberTrace events:
- Select all the check boxes for every event.
- Right-click in the table and select Properties.
The MPE Policy Rule Editor window opens.
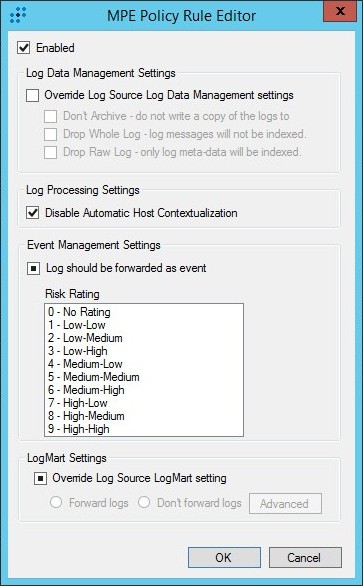
MPE Policy Rule Editor window
- In the MPE Policy Rule Editor window, select the Enabled check box but make no changes to the other check boxes.
- Click OK.
Step 6. Adding a log source to System Monitor Agent
This section describes the actions to perform so that a new log source pertaining to Kaspersky CyberTrace will appear in LogRhythm. If LogRhythm is already configured properly, you do not need to take action, as the new log source will appear in LogRhythm and you only have to check that everything is as you specified.
To create conditions for a log source pertaining to Kaspersky CyberTrace to be added to LogRhythm:
- Run LogRhythm Console.
- Select Deployment Manager > System Monitors > Agent > Properties.
The System Monitor Agent Properties window opens.
- Select the Syslog and Flow Settings tab.
- Select the Enable Syslog Server checkbox.
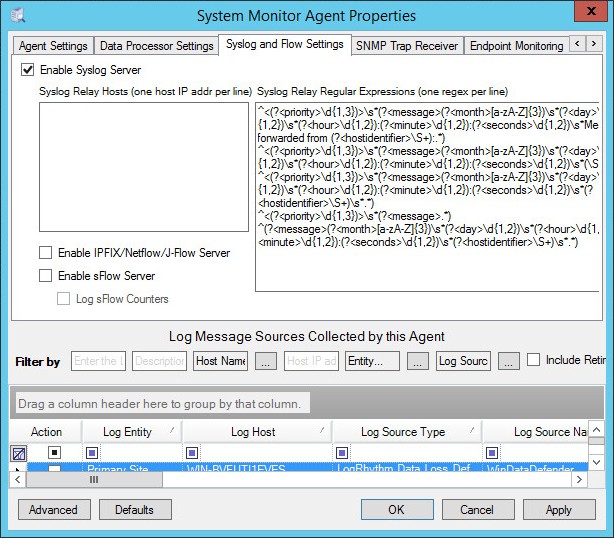
System Monitor Agent Properties window
- Click OK.
- Turn off Windows Firewall or add exclusions to it so that incoming SYSLOG events can arrive.
- Select Deployment Manager > Data Processors > Properties > Advanced.
The Data Processor Advanced Properties window opens.
- In the table, select the following items. Property names are in the Name column and the Value column contains the checkboxes to be selected:
- AutomaticLogSourceConfigurationNetFlow
- AutomaticLogSourceConfigurationsFlow
- AutomaticLogSourceConfigurationSNMPTrap
- AutomaticLogSourceConfigurationSyslog
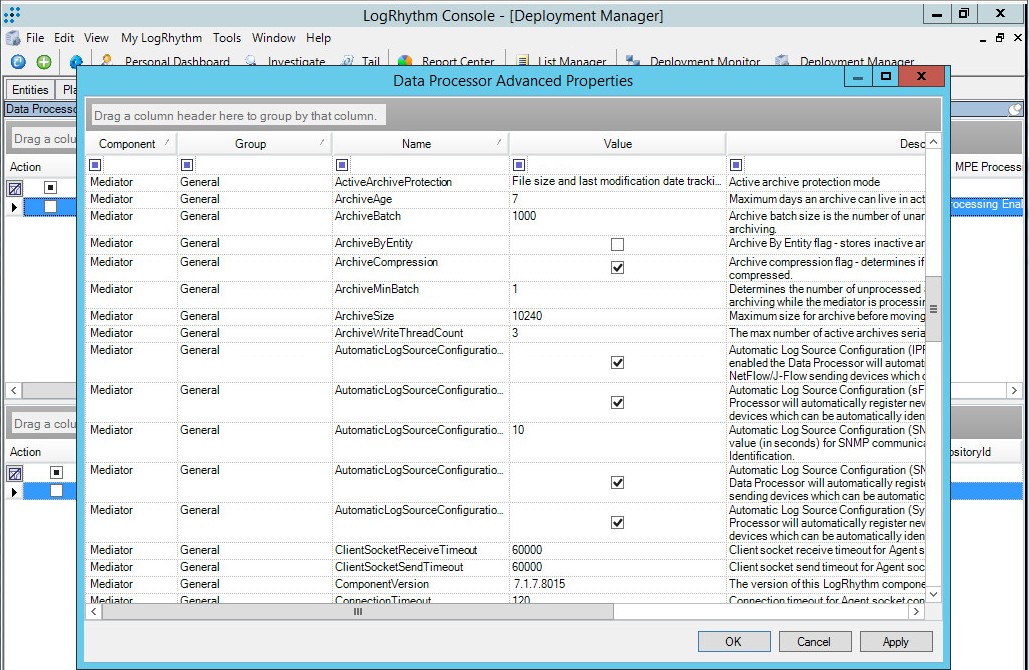
Data Processor Advanced Properties window
- Click OK.
- Restart LogRhythm if necessary.
LogRhythm will inform you whether a restart is required.
After Kaspersky CyberTrace sends an event, a new item appears on the Log Sources tab.
To accept the new log source:
- Right-click the new item, and then select Actions > Resolve Log Source Hosts.
- Double-click the new item.
The Log Source Acceptance Properties window opens.
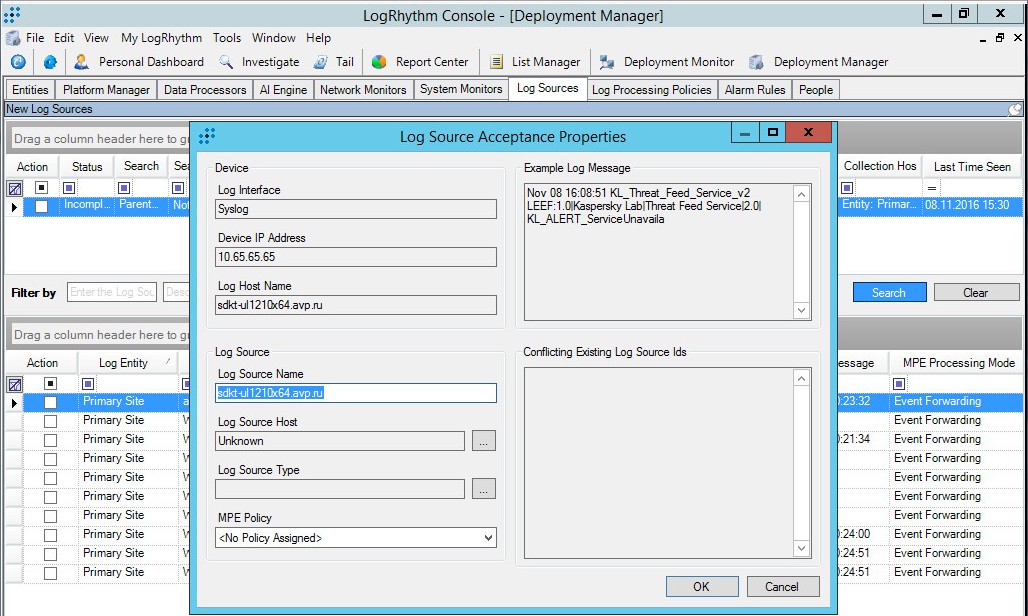
Log Source Acceptance Properties window
- Edit the properties:
- Specify the log source host.
- Specify
Kaspersky CyberTraceas the log source type. - Specify the MPE policy that you added in step 4.
- Click OK.
- If an error message appears saying that you cannot use an unknown log source host, add a new entity as follows:
- In LogRhythm Console, select the Entities tab.
- Click the New Child Entity toolbar button.
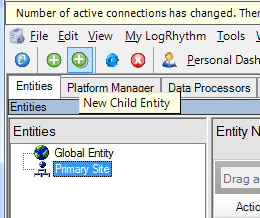
- In the Entity Properties window that opens, specify the entity properties.
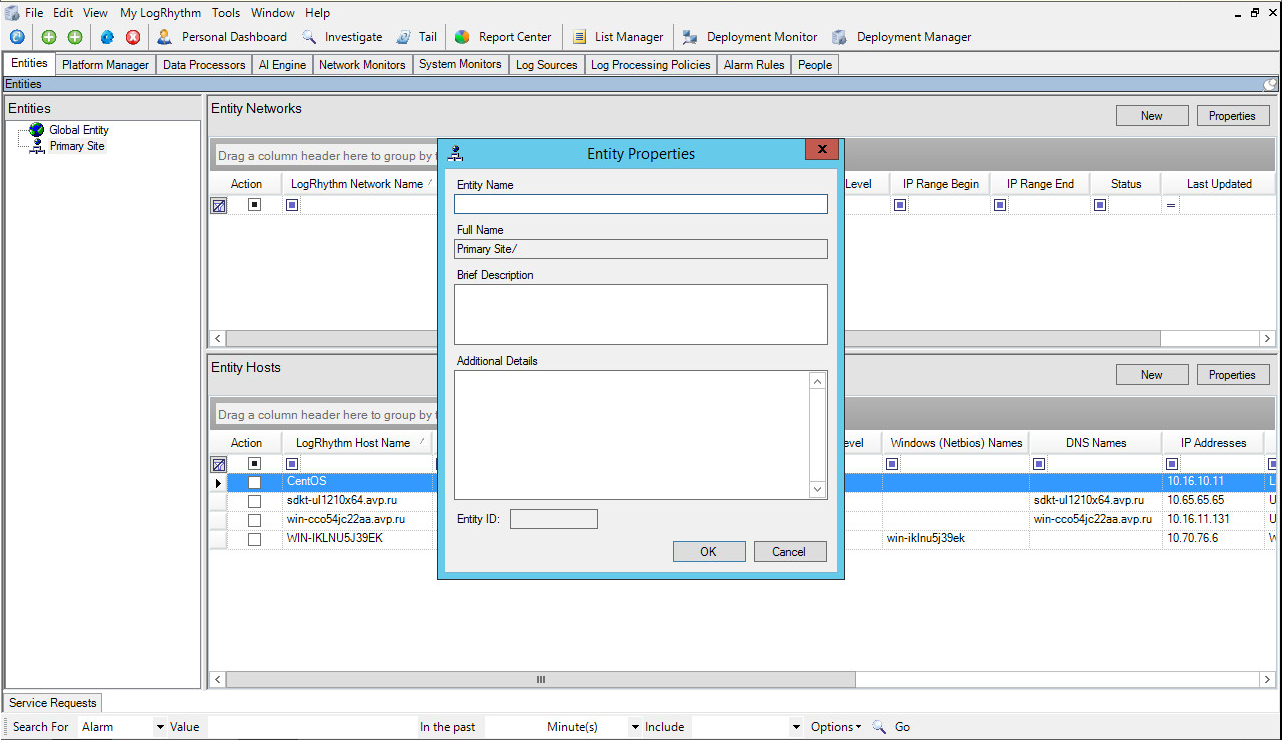
The entity name must be unique and non-empty. Other entity properties can be arbitrary.
- Click OK.
- Repeat the action in step 3 by using the created entity as the log source host.
- Select the Action checkbox.
- Right-click the log source, and then select Actions > Accept > Defaults.
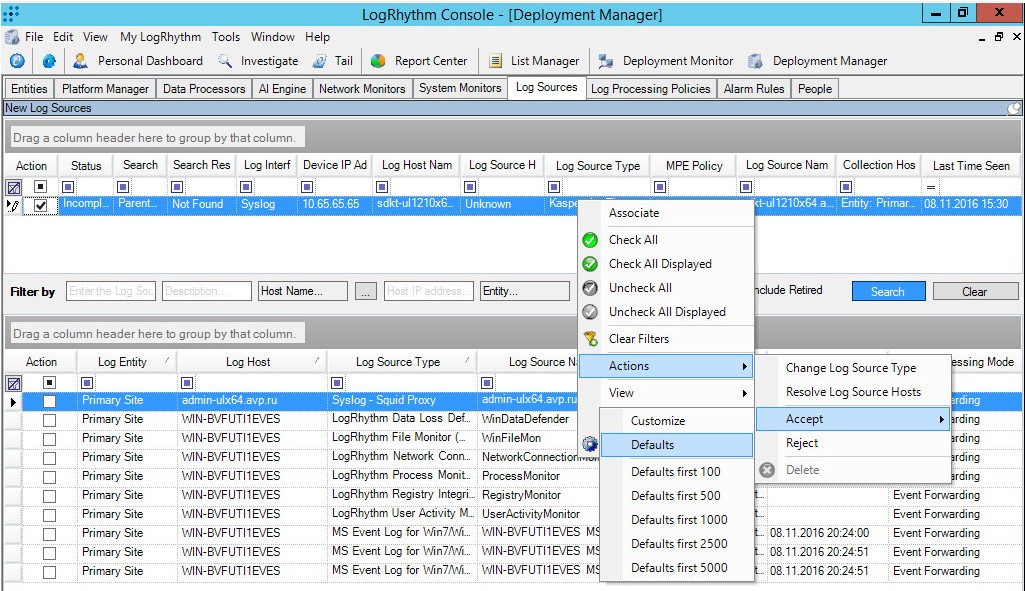
Log source context menu
The new log source now appears in the lower table in LogRhythm Console.
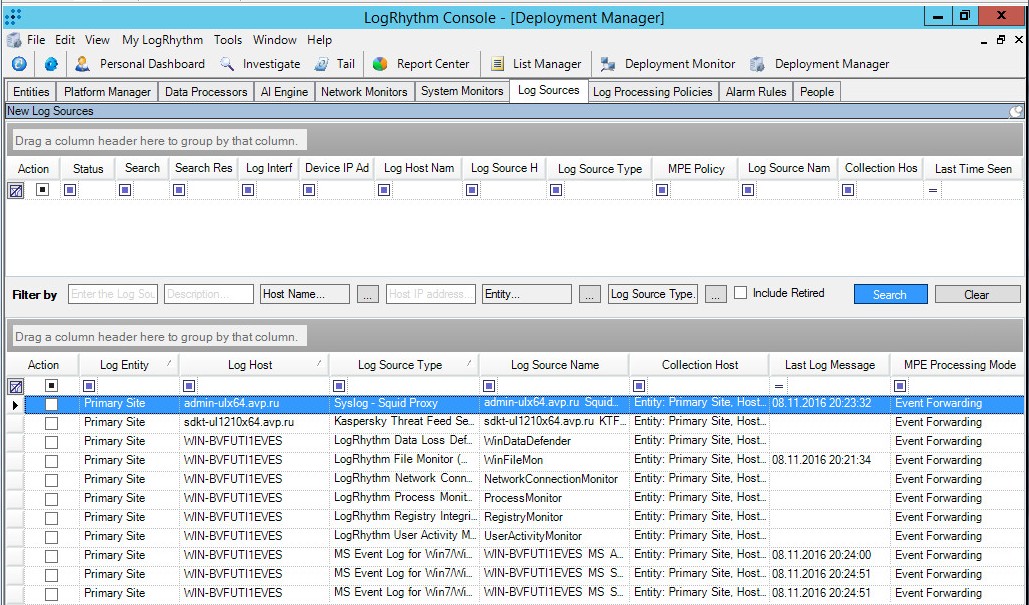
New log source
Disabling log forwarding for the events received from Kaspersky CyberTrace
You may need to disable log forwarding for the events received from Kaspersky CyberTrace, to avoid the looping of events, which is forwarding the received events back to Kaspersky CyberTrace.
To disable log forwarding for the events received from Kaspersky CyberTrace:
- On the Log Sources tab, select the checkbox of the log source associated with Kaspersky CyberTrace.
- Right-click the log source, and then select Actions > Edit properties.
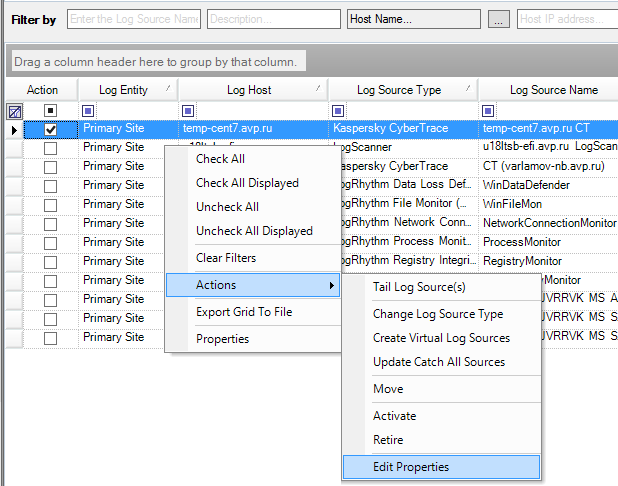
Editing the properties of the Kaspersky CyberTrace log source
- The Log Message Source Properties window opens. In the Log Message Processing Mode drop-down list, select MPE Processing Enabled, Event Forwarding Disabled, and then click OK.
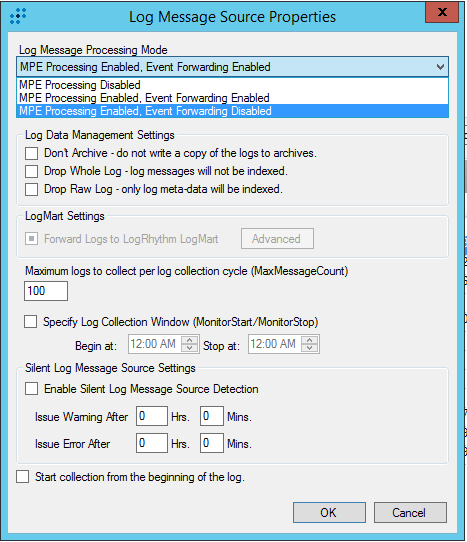
Specifying the log message processing mode
In the MPE Processing Mode column, No Event Forwarding will be displayed for the selected log source.
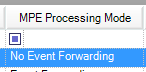
The MPE Processing Mode column
Page topStep 7. Configuring log forwarding to Kaspersky CyberTrace
This section explains how to configure LogRhythm to forward logs to Kaspersky CyberTrace. Configuring LogRhythm includes adding a log receiver and adding a log distribution pollicy.
Adding a log receiver
In LogRhythm, create a new log receiver. This log receiver will represent Kaspersky CyberTrace.
To add a log receiver to LogRhythm:
- Run LogRhythm Console.
- Select Deployment Manager > Tools > Distribution > Log Distribution Services > Receiver Manager.
The Log Distribution Receiver Manager window opens.
- Select File > New.
- Fill in the fields of the Syslog Receiver Properties window that opens:
- Specify the IP address of the remote host on which Kaspersky CyberTrace is installed (the IP address specified in the
InputSettings > ConnectionStringelement of the Feed Service configuration file). - Specify the remote port that Kaspersky CyberTrace listens on for events (the port specified in the
InputSettings > ConnectionStringelement of the Feed Service configuration file). - Change Network Protocol to TCP.
- Specify the IP address of the remote host on which Kaspersky CyberTrace is installed (the IP address specified in the
- Click OK.
- After a new row appears in the table, right-click the row and select Enabled.
Adding a log distribution policy
After the log receiver is added, set the conditions by adding a log distribution policy for events to be forwarded to Kaspersky CyberTrace.
To add a log distribution policy:
- Select Deployment Manager > Tools > Distribution > Log Distribution Services > Policy Manager.
- In the Log Distribution Policy Manager window that opens, select File > New.
The Log Distribution Policy Wizard starts.
- Follow the instructions of the Wizard.
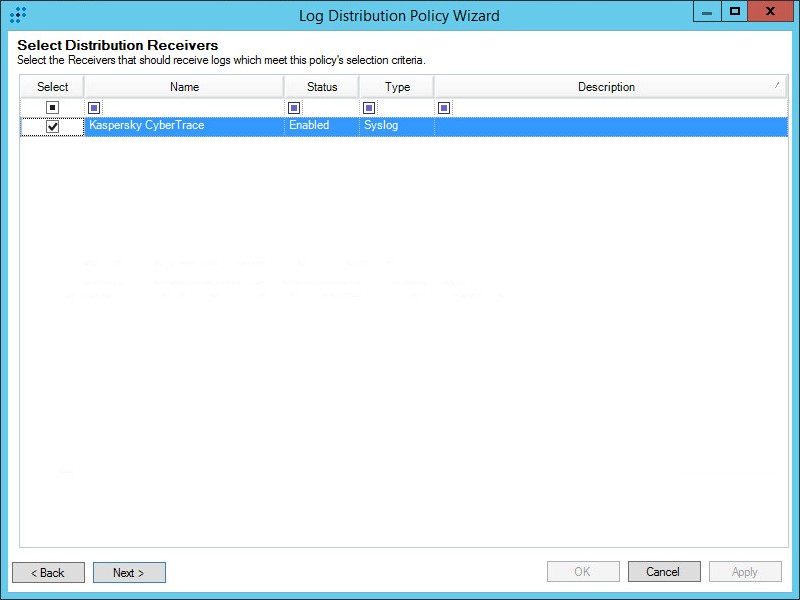
Log Distribution Policy Wizard
- In the Select Distribution Receivers table, select the
Kaspersky CyberTraceitem that was created previously. - Select the log sources that can send URLs, hashes, and IP addresses.
After the Log Distribution Policy Wizard finishes, the new row appears in the table.
- In the Select Distribution Receivers table, select the
- Right-click the new row in the table and select Enabled.
The computer on which Kaspersky CyberTrace is installed will now receive logs. You can check this by using the netcat utility.
Displaying detection events in LogRhythm
As a result of the above actions, LogRhythm will receive and display detection events. Also, the events will appear in the web console, which is available at https://<logrhythmIP>:8443 or at https://<logrhythmIP>:80.
Step 8 (optional). Performing the verification test
This section explains how to verify that Kaspersky CyberTrace has been integrated with LogRhythm correctly by performing the verification test.
To create the conditions for performing the verification test:
- Create a custom log source type, as described in section "Step 1. Adding a Custom Log Source type", with the following parameters:
Field
Data
Name
Kaspersky LogScanner
Full Name
Kaspersky LogScanner
Abbreviation
LogScanner
Log Format
Syslog
Brief Description
Kaspersky LogScanner is a command-line application that allows you to send data to Feed Service for checking against feeds.
- Add a new common event, as described in section "Step 3 (optional). Adding Kaspersky CyberTrace events", with the following parameters:
Field
Data
Name
LogScanner_event
Classification
Audit : Other Audit
Brief Description
LogScanner event for verification purposes
Risk Rating
Low-Low
Common Event Properties window
- Add an MPE rule for Log Scanner, as described in section "Step 4 (optional). Adding Kaspersky CyberTrace rules", using the following parameters:
- In the Log Message Source Type Associations tree pane, select Kaspersky LogScanner.
- Specify
LogScanner_eventas the Rule Name. - In the Common Event drop-down list, select LogScanner_event.
- In Rule Status, select Production.
- In Base-Rule Regular Expression, type '
.*'.
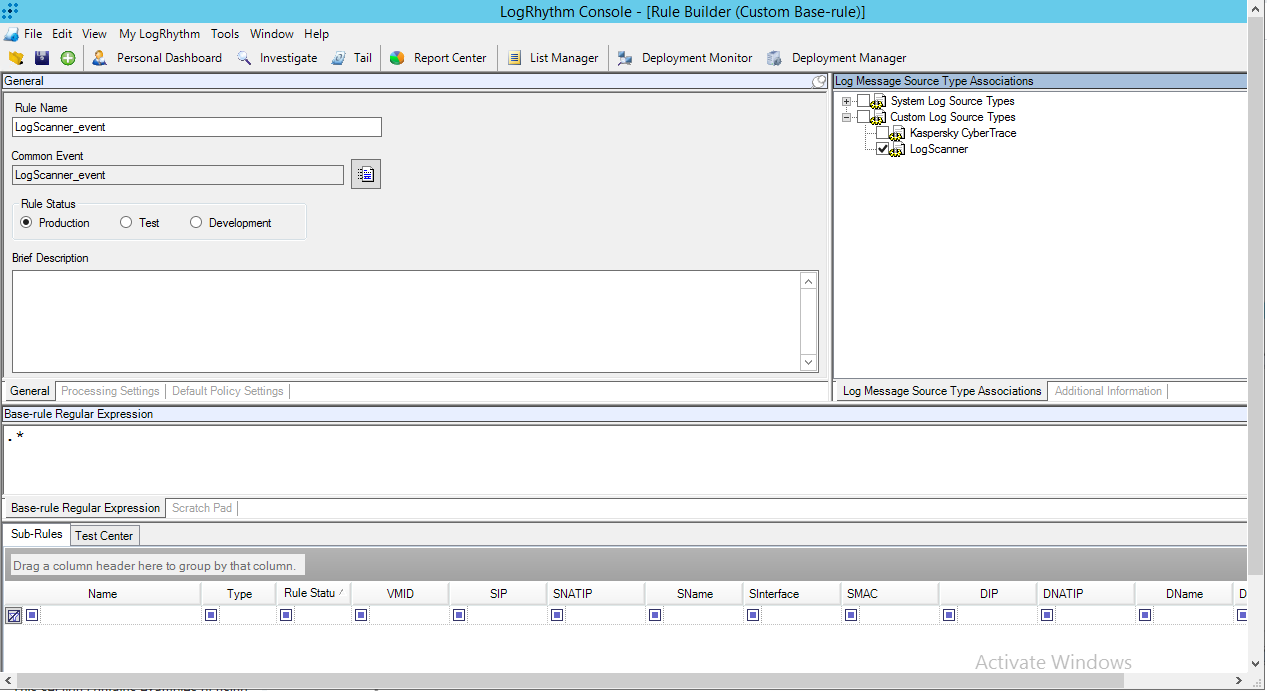
Rule builder form
- Create a new policy for Kaspersky Log Scanner, as described in section "Step 5. Adding Kaspersky CyberTrace policy".
In the Log Source Type list, select Kaspersky LogScanner. Specify all other parameters, as described in section "Step 5. Adding Kaspersky CyberTrace policy".
- Add a log source to System Monitor Agent:
- In the Log Scanner configuration file, specify the IP address of the computer on which LogRhythm runs and port
514. - Send the
%service_dir%/verification/kl_verification_test_cef.txtfile to LogRhythm.- For this purpose, run the following command (in Linux):
./log_scanner -p ../verification/kl_verification_test_cef.txt - For this purpose, run the following command (in Windows):
log_scanner.exe -p ..\verification\kl_verification_test_cef.txt
- For this purpose, run the following command (in Linux):
- In the Log Scanner configuration file, specify the IP address of the computer on which LogRhythm runs and port
After Kaspersky Log Scanner sends an event, a new item will appear on the Log Sources tab.
To accept the new log source:
- Right-click the new item, and then select Actions > Resolve Log Source Hosts.
- Double-click the new item.
The Log Source Acceptance Properties window opens.

Log Source Acceptance Properties window
- Edit the properties:
- Specify the log source host.
- Specify
Kaspersky LogScanneras the log source type. - Select the MPE policy that you previously created for Kaspersky Log Scanner.
- Click OK.
- If an error message appears saying that you cannot use an unknown log source host, add a new entity as follows:
- In LogRhythm Console, select the Entities tab.
- Click the New Child Entity toolbar button.

- In the Entity Properties window that opens, specify the entity properties.

The entity name must be unique and non-empty. Other entity properties can be arbitrary.
- Click OK.
- Repeat the action in step 3 by using the created entity as the log source host.
- Select the Action check box.
- Right-click the log source, and then select Actions > Accept > Defaults.

Log source context menu
The new log source now appears in the lower table in LogRhythm Console.

New log source
- Reload LogRhythm.
If you have previously configured log forwarding, as described in section "Step 7. Configuring log forwarding to Kaspersky CyberTrace", make sure that you have Kaspersky LogScanner selected as a Log source (see subsection "Adding a log distribution policy").
To perform the verification test:
Resend the %service_dir%/verification/kl_verification_test_cef.txt file to LogRhythm.
- For this purpose, run the following command (in Linux):
./log_scanner -p ../verification/kl_verification_test_cef.txt - For this purpose, run the following command (in Windows):
log_scanner.exe -p ..\verification\kl_verification_test_cef.txt
If the integration of Kaspersky CyberTrace with LogRhythm has been configured properly, test events from Log Scanner will be forwarded to Kaspersky CyberTrace automatically. Then, the alert events from Kaspersky CyberTrace will be sent to LogRhythm. The number of detections may vary depending on enabled Kaspersky Threat Data Feeds. The alert events can be displayed in the LogRhythm web console, as described in section "Step 10 (optional). Displaying alert events in LogRhythm".
Page topStep 9 (optional). Creating alerts about incoming Kaspersky CyberTrace service events
You can create notifications about incoming Kaspersky CyberTrace service events by configuring alert rules.
To create notifications about service events from Kaspersky CyberTrace in LogRhythm:
- Run LogRhythm Console.
- Select Deployment Manager > Alarm Rules and click New.
- In the Create Global Rule confirmation window, click Yes if you want to give access to manage this rule for all users with the Global Admin role. Click No, if you want to manage this rule only by yourself.
- Perform the following actions for each tab at the bottom of the page:
- On the Primary Criteria tab, do the following:
- Click New, and select the Common Event value in the Add New Field Filter drop-down list.
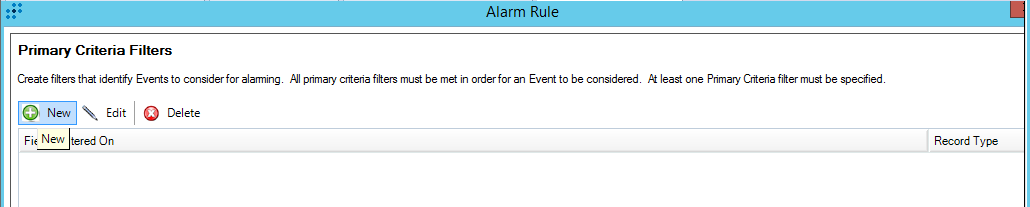
- Click Edit values.
The Field Filter Values window opens.
- In the Field Filter Values window, click Add Item.
- Select the name of the Kaspersky CyberTrace service event from the list. If such events are absent, add them as described in the "Adding Kaspersky CyberTrace events" section.
- Click OK.
- Click New, and select the Common Event value in the Add New Field Filter drop-down list.
- Leave the Include Filters, Exclude Filters and Day and Time Criteria tabs unchanged.
- On the Log Source Criteria tab, check Include the Selected Log Sources and then click Add.
The Alarm Rule window
- Select a source that corresponds to Kaspersky CyberTrace and click OK. For information on how to add Kaspersky CyberTrace event source, see section "Adding a log source to System Monitor Agent".
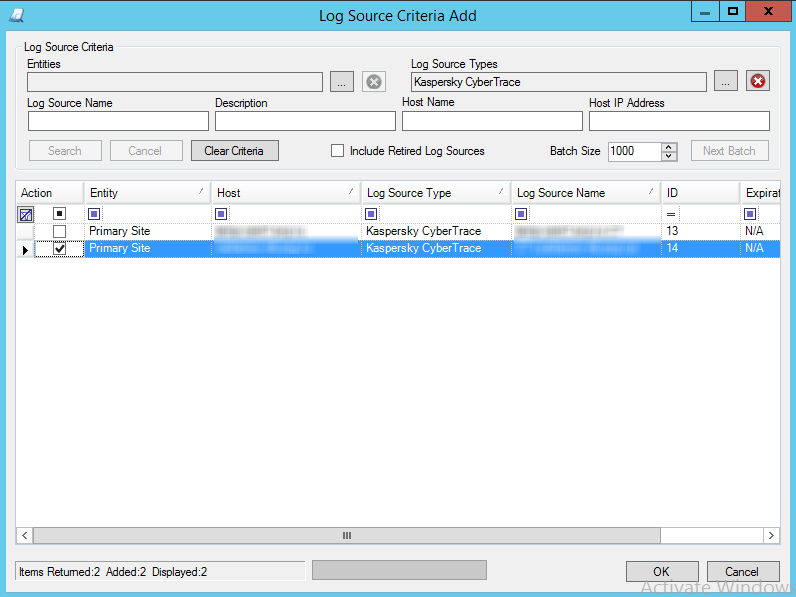
The Log Source Criteria Add window
- Leave the Aggregation tab unchanged.
- In the Settings tab, specify a period of time during which identical alerts that are associated with the occurrence of any new service events from Kaspersky CyberTrace have to be suppressed.
Alert suppression settings
- On the Notify tab, select a role or user you want to address notifications.
Choosing the roles to notificate
- Leave the Actions tab unchanged.
- On the Information tab, specify the name of the rule and its description.
Alarm Rule Name/Brief Description
- On the Primary Criteria tab, do the following:
- Click OK.
- On the Alarm Rules tab, right-click the new rule and select Actions > Enable.
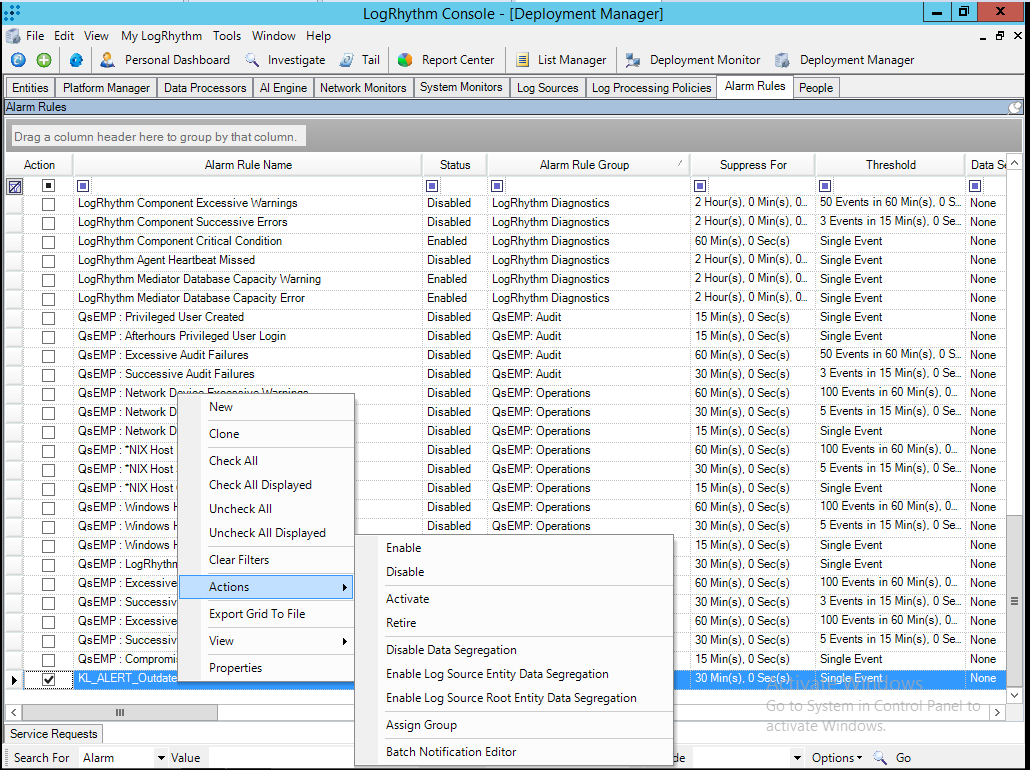
Enabling a rule
- Configure display of the alerts in the LogRhythm web console as described in section "Step 10 (optional). Displaying alert events in LogRhythm".
Step 10 (optional). Displaying alert events in LogRhythm
You can configure the LogRhythm web console so that it will display alert events together with detection events.
To configure the web console for displaying alert events:
- In the web console, click Search.
- Click Log Source Filter.
Search form
- Type
CyberTraceas the search string. - Move the search filter that is found to the right column by clicking the arrow (+).
- Click OK.
- After a new search has finished, open the result window.
The LogRhythm web console will display detection events together with alert events in the search result window.
Page top