About the single-instance integration scheme
By default, Feed Service and Kaspersky CyberTrace App are configured to use the following integration scheme. This scheme is called the single-instance integration scheme.
About the apps and services used in the single instance integration scheme
In the single instance integration scheme, Kaspersky CyberTrace is divided into one app and one service:
- Feed Service
This service matches Splunk events against Kaspersky Threat Data Feeds.
Feed Service sends the resulting events to Splunk. Splunk stores the events from Feed Service in the
mainindex. - Kaspersky CyberTrace App
This app contains Kaspersky CyberTrace App dashboards, alert templates, and the lookup script. The app also contains rules for parsing events received from Feed Service, and rules for forwarding events from Splunk to Feed Service.
Single-instance integration scheme
In the single-instance integration scheme, Splunk Apps and Feed Service by default are configured to work on the same computer (IP address is 127.0.0.1). Kaspersky CyberTrace App takes input on port 3000 and forwards it to Feed Service on port 9999. Feed Service then returns matches to Kaspersky CyberTrace App on port 9998.
If you want to install Feed Service on a separate computer, you must specify the required addresses and ports used by Feed Service and Kaspersky CyberTrace App when installing Kaspersky CyberTrace.
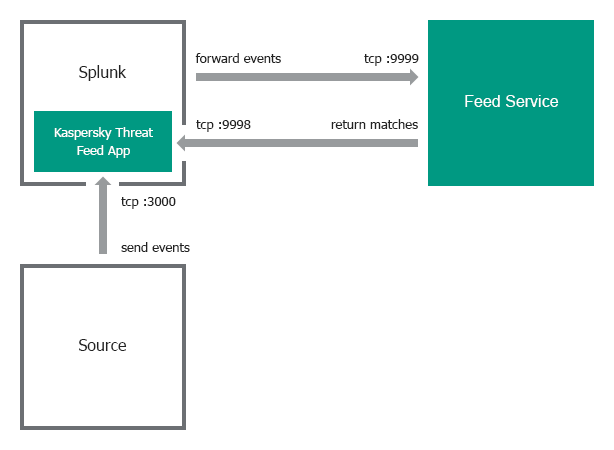
Single-instance integration scheme
Event format
By default, Kaspersky CyberTrace App and Feed Service are configured to receive events in a certain format:
- Feed Service parses events displayed in Kaspersky CyberTrace Web. These regular expressions are created for a specific format of inbound data. For example, the default regular expression for URLs will match a URL containing the protocol (for example, HTTP or HTTPS). If the URLs in the events generated by your devices do not contain the protocol, change the regular expression accordingly.
- The lookup script that comes with Kaspersky CyberTrace App sends events to Feed Service in a format that matches the regular expressions used by Feed Service.
When you change the regular expressions by using Kaspersky CyberTrace Web, edit the lookup script accordingly.
Page top