Step 3. Forwarding events from QRadar to Feed Service
To check events that arrive in QRadar by way of Feed Service, you must configure QRadar to forward the events to Feed Service.
To forward events from QRadar to Feed Service:
- Select Admin > Forwarding Destinations > Add.
- In the Forwarding Destination Properties window, type the identifier of the destination (for example,
"KL_Threat_Feed_Service_v2"). - Type the destination address (the host where Feed Service runs).
- Select
Payloadas the events format andTCPas the protocol.The
Payloadformat can contain less information thanJSONformat. For example, if event source names are used, QRadar may remove them from the event. You can specify theJSONformat instead, but make sure to configure events in this format properly. For instructions on configuring events inJSONformat to forward to Kaspersky CyberTrace, see section "Recommendations on configuring events in JSON format" below. - Set the port according to the Service settings of Kaspersky CyberTrace for inbound events.
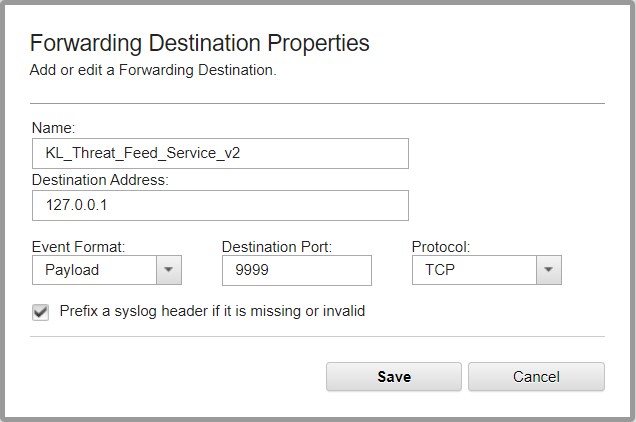
Adding a forwarding destination
- Click Save.
- Select Admin > Routing rules > Add.
- In the Routing Rule window, type the rule name (for example,
KL_Threat_Feed_Service_v2_Rule). - Select
Onlineas the mode. - Leave the default value in the Forwarding Event Collector drop-down list.
- Select
Eventsas the data source. - In the Event Filters group, set the event filter.
Choose the log sources together with
KL_Verification_Tool, and use theEquals any ofoperator in the filter.Clear the Match all incoming events check box or leave it cleared so that the detection events received from Feed Service will not be sent back to Feed Service.
- Select the Forward check box. In the table, next to the Name column, select the check box next to the item added in step 1 (in this case, it is
KL_Threat_Feed_Service_v2).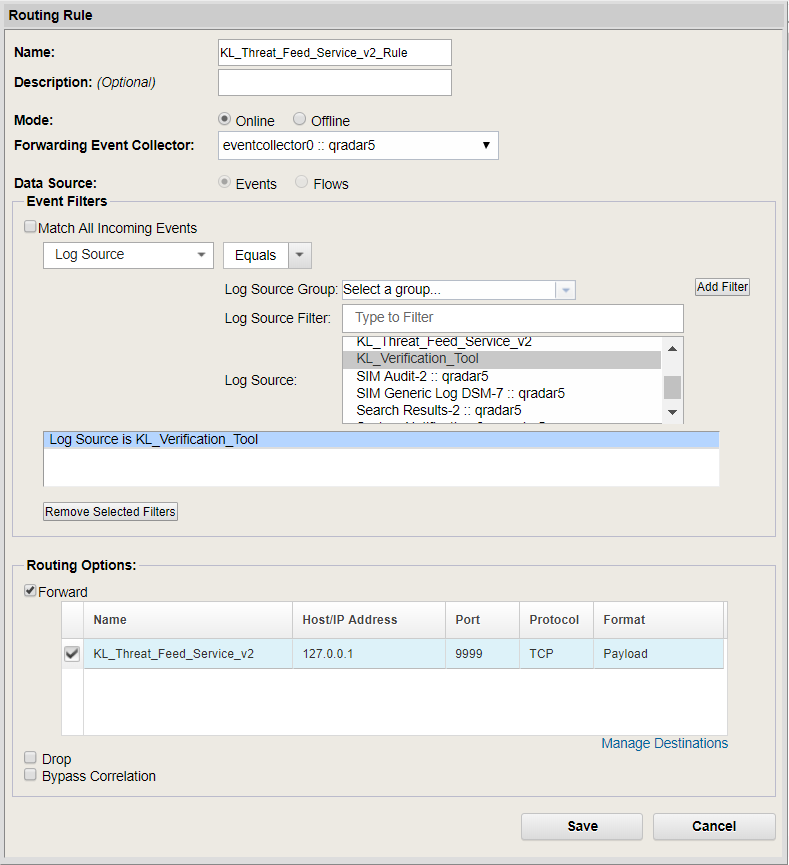
Adding a routing rule
- Click Save.
Recommendations on configuring events in JSON format
A number of QRadar versions (for example, 7.3.2 Patch 6 and 7.4.0) may drop some forwarded events in JSON format, which may lead to incorrect results.
To prevent this, we recommend that you exclude some fields from the JSON-formatted event (for an exact list of such fields contact the IBM's QRadar Support team or try to determine this list manually). You must specify additional normalizing rules in Kaspersky CyberTrace Web (see below).
Therefore, use the JSON format instead of the Payload format if the event in the Payload format does not contain the necessary fields. In this case, make sure that the following conditions are met:
- In the Forwarding Destination Properties window, only fields that you need are selected, and QRadar does not delete forwarded events. To decrease the amount of transmitted data and increase performance, we recommend that you create a separate profile (set of fields) to be forwarded to CyberTrace. In this profile, specify the appropriate fields that contain observables (such as URLs, hashes (MD5, SHA1, SHA256), and IP addresses) and the related context that allows the ability to find the original event (time stamps, user name, etc.).
To create a new profile that contain the fields to be forwarded within an event, click Create New Profile in the list to the right of the Profile field.
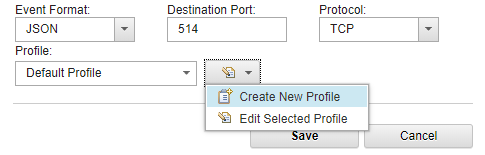
Configuring events in JSON format
- In CyberTrace, specify parsing rules for the fields. For example, for the user name (the
usrNamefield in terms of LEEF format) in JSON format, the regular expression may look like this:usrName\=(.*?)(?:$|\s|\"). We recommend that you specify similar regular expressions for each chosen field and check if these regular expressions are correctly applied to real detection events that are sent to QRadar, by using the RegExps Editor section of the Setting > Matching tab of Kaspersky CyberTrace Web. - On the Settings > Matching tab of Kaspersky CyberTrace Web, specify the following normalizing rules:
\\tin the Regexp to replace field and\tin the Replace with field\\nin the Regexp to replace field and an empty value in the Replace with field
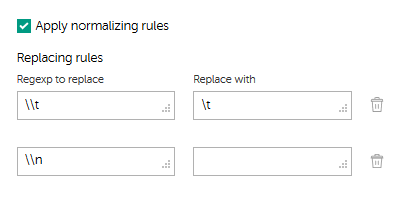
Configuring additional normalizing rules