Step 4. Performing the verification test (QRadar)
This section explains how to check the capabilities of Kaspersky CyberTrace by performing the verification test.
Please make sure you perform the verification test before editing any filtering rules in the Feed Utility configuration file.
What is the verification test
The verification test is a procedure that is used to check the capabilities of Kaspersky CyberTrace and to confirm the accuracy of the integration.
During this test you will check whether events from QRadar are received by Feed Service, whether events from Feed Service are received by QRadar, and whether events are correctly parsed by Feed Service using the regular expressions.
About the verification test file
The verification test file is a file that contains a collection of events with URLs, IP addresses, and hashes. This file is located in the ./verification directory in the distribution kit. The name of this file is kl_verification_test.txt.
Verification procedure
To verify the installation:
- Start Feed Service (see section "Using Feed Service").
- Make sure that the
"KL_Verification_Tool"log source is added to QRadar and routing rules are set in such a way that events from"KL_Verification_Tool"are sent to Feed Service. - Open QRadar Console and select the Log Activity tab.
- Add a filter:
- Click the Add Filter button.
- In the Parameter drop-down list, select
Log Source. - In the Operator drop-down list, select
Equals. - In the Value group, in the Log Source drop-down list select the required service name.
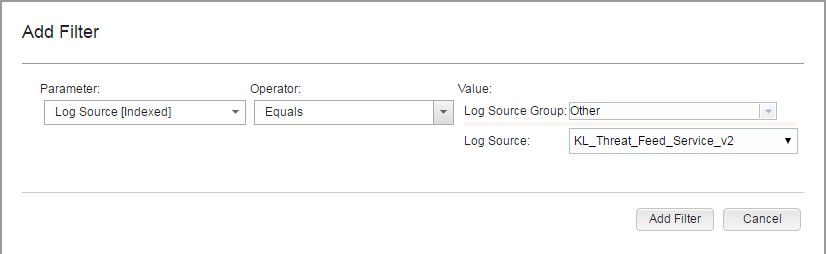
Adding a filter for browsing events
- Click the Add Filter button.
The
Log Source is KL_Threat_Feed_Service_v2string will be displayed under Current Filters. - In the View drop-down list, select
Real Timeto clear the event area.You now can browse information about the service events.
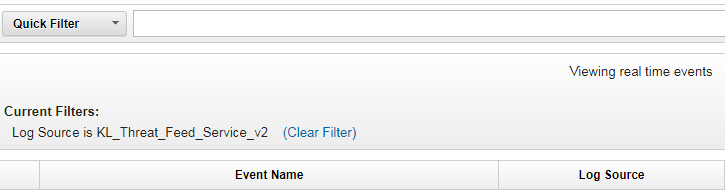
Browsing filtered information
- Run Log Scanner to send the
kl_verification_test.txtfile to QRadar, as described in section "Step 3. Sending a set of events to QRadar". That is, run the following command:For Linux:
./log_scanner -p ../verification/kl_verification_test.txtFor Windows:
log_scanner.exe -p ../verification/kl_verification_test.txtIf you specify the
-rflag in this command, the test result is written to the Log Scanner report file. If you do not specify the-rflag, the test results are sent to the SIEM solution by using theOutputSettings > ConnectionStringsettings specified in the Feed Service configuration file.The expected results to be displayed by QRadar depend on the feeds you use. The verification test results are listed in the following table.
Verification test result
Feed used
Detected objects
Malicious URL Data Feed
http://fakess123.nu
http://badb86360457963b90faac9ae17578ed.com
and many others, such as kaspersky.com/test/wmuf
Phishing URL Data Feed
http://fakess123ap.nu
http://e77716a952f640b42e4371759a661663.com
Botnet CnC URL Data Feed
http://fakess123bn.nu
http://a7396d61caffe18a4cffbb3b428c9b60.com
IP Reputation Data Feed
192.0.2.0
192.0.2.3
Malicious Hash Data Feed
FEAF2058298C1E174C2B79AFFC7CF4DF
44D88612FEA8A8F36DE82E1278ABB02F (stands for EICAR Standard Anti-Virus Test File)
C912705B4BBB14EC7E78FA8B370532C9
Mobile Malicious Hash Data Feed
60300A92E1D0A55C7FDD360EE40A9DC1
Mobile Botnet CnC URL Data Feed
001F6251169E6916C455495050A3FB8D (MD5 hash)
http://sdfed7233dsfg93acvbhl.su/steallallsms.php (URL mask)
P-SMS Trojan Data Feed
FFAD85C453F0F29404491D8DAF0C646E (MD5 hash)
Ransomware URL Data Feed
http://fakess123r.nu
http://fa7830b4811fbef1b187913665e6733c.com
Vulnerability Data Feed
D8C1F5B4AD32296649FF46027177C594
APT URL Data Feed
http://b046f5b25458638f6705d53539c79f62.com
APT Hash Data Feed
7A2E65A0F70EE0615EC0CA34240CF082
APT IP Data Feed
192.0.2.4
IoT URL Data Feed
http://e593461621ee0f9134c632d00bf108fd.com/.i
Demo Botnet CnC URL Data Feed
http://5a015004f9fc05290d87e86d69c4b237.com
http://fakess123bn.nu
Demo IP Reputation Data Feed
192.0.2.1
192.0.2.3
Demo Malicious Hash Data Feed
776735A8CA96DB15B422879DA599F474
FEAF2058298C1E174C2B79AFFC7CF4DF
44D88612FEA8A8F36DE82E1278ABB02F
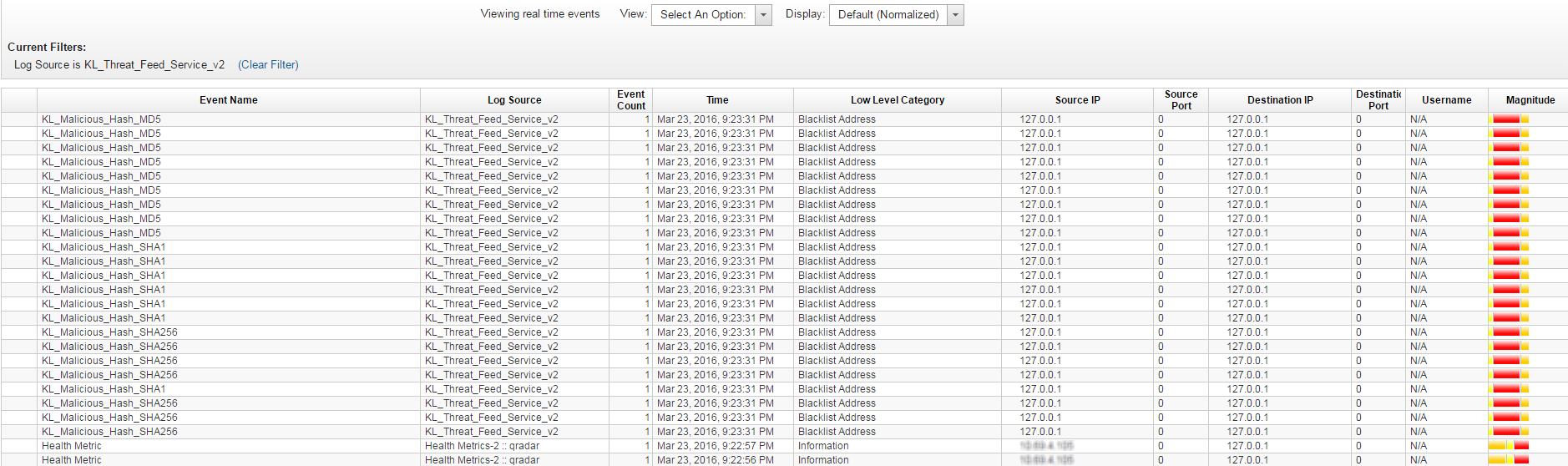
Browsing events from Feed Service
If the actual results of the test are the same as those expected, the integration of Feed Service with QRadar is correct.
Page top