Step 2. Sending events from Feed Service to RSA NetWitness
This section describes the actions to take so that Feed Service will send events to RSA NetWitness.
Note that Feed Service sends events to a Log Decoder service.
To send events from Feed Service to RSA NetWitness:
- In the Feed Service configuration file, in the
OutputSettings > ConnectionStringelement specify the following value:[IP]:514Here
[IP]is the IP address of the Log Decoder service to which Feed Service will send events.As an alternative, you can perform this step by using Kaspersky CyberTrace Web.
If there are several Log Decoder services, perform the integration with only one of the Log Decoders.
- In directory
/etc/netwitness/ng/envision/etc/devicesof the computer on which Log Decoder runs, create a subdirectorycybertraceand copy to the subdirectory the following files from the%service_dir%/integration/cybertracedirectory:- cybertrace.ini
This is a configuration file that contains declaration of Feed Service for RSA NetWitness.
- v20_cybertracemsg.xml
This is a configuration file that contains parsing rules for events that are sent from Feed Service to RSA NetWitness. See below in this section for a description of the contents.
You can find these files in the
integration/cybertracedirectory of the distribution kit. - cybertrace.ini
- Restart Log Decoder.
For this purpose, in the Services view, for the selected Log Decoder click the Settings split button (
 ) and from the drop-down list select Restart.
) and from the drop-down list select Restart. - Make sure that the
cybertraceservice parser is turned on in RSA NetWitness.You can do this as follows:
- In the RSA NetWitness menu, select Administration > Services.
- In the Services grid, select the Log Decoder, and from the Actions menu, choose View > Config.
- In the Service Parsers Configuration panel, search for cybertrace, and ensure that the Config Value field in this row is selected.
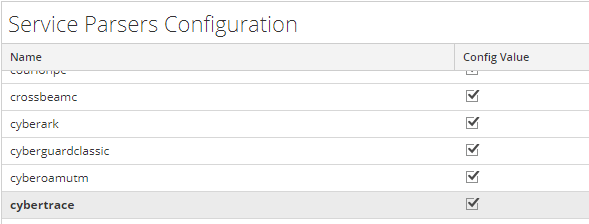
Service Parsers Configuration grid
- Restart Feed Service.
You can restart Feed Service by running the kl_feed_service script as follows:
%service_dir%/etc/init.d/kl_feed_service restartYou can do this by using Kaspersky CyberTrace Web too.
Integration files' contents
The v20_cybertracemsg.xml file contains the following rule for parsing service events from Feed Service:
alert=<action>,context=<msg> |
The v20_cybertracemsg.xml file contains several rules for parsing detection events from Feed Service:
- MATCH_EVENT:01—For parsing detection events when Botnet CnC URL Data Feed is involved in the detection process.
- MATCH_EVENT:02—For parsing detection events when Malicious URL Data Feed is involved in the detection process.
- MATCH_EVENT:03—For parsing detection events when Mobile Botnet CnC URL Data Feed is involved in the detection process.
- MATCH_EVENT:04—For parsing detection events when Malicious Hash Data Feed is involved in the detection process.
- MATCH_EVENT:05—For parsing detection events when Phishing URL Data Feed is involved in the detection process.
- MATCH_EVENT:06—For parsing detection events when Ransomware URL Data Feed or IoT URL Data Feed are involved in the detection process.
- MATCH_EVENT:07—For parsing detection events when IP Reputation Data Feed is involved in the detection process.
- MATCH_EVENT:08—For parsing detection events when P-SMS Trojan Data Feed or Vulnerability Data Feed are involved in the detection process.
- MATCH_EVENT:09—For parsing detection events when Mobile Malicious Hash Data Feed is involved in the detection process.
- MATCH_EVENT:10—For parsing detection events when APT feeds are involved in the detection process.
- MATCH_EVENT—For parsing detection events when other feeds are involved in the detection process.
The fields of the cybertrace.ini file and the v20_cybertracemsg.xml file correspond to the following format of service events and detection events from Feed Service:
<AlertFormat><![CDATA[<232>%CyberTrace:ALERT_EVENT alert=%Alert%,context=%RecordContext%]]></AlertFormat> <EventFormat><![CDATA[<232>%CyberTrace:MATCH_EVENT category=%Category%,detected=%MatchedIndicator%,url=%RE_URL%,hash=%RE_HASH%,dst=%DST_IP%,src=%SRC_IP%,dvc=%DeviceIp%,dev_name=%Device%,dev_action=%DeviceAction%,user=%UserName%,actF:%ActionableFields%,context=%RecordContext%]]></EventFormat> |
In the v20_cybertracemsg.xml file, the format of events from Feed Service is provided in the HEADER/content element and in the MESSAGE/content element. Make sure that the following fields are present in the index files of Log Decoder and Concentrator: virusname, url, checksum, and ip.src, ip.dst. As for the fields other than virusname, url, checksum, and ip.src, ip.dst in the MESSAGE/content element, you may or may not use them in the index files of Log Decoder and Concentrator. Also, make sure that the value of the flags attribute is None for each of these fields in the table-map-custom.xml file. If any of these conditions are not met, refer to section "RSA NetWitness troubleshooting".
The following tables describe the fields used in the v20_cybertracemsg.xml and kl_feed_service.conf files, and describe how fields in one file correspond to fields in the other. If you want to constantly use some new field in detection events, contant your technical account manager (TAM).
- Fields of service events
Field in kl_feed_service.conf
Field in v20_cybertracemsg.xml
Description
<232>
-
Service string for RSA NetWitness.
%CyberTrace:
%CyberTrace:
Informs RSA NetWitness that an event is sent from Feed Service.
ALERT_EVENT
<messageid>
The event type.
-
<!payload>
Notifies RSA NetWitness that the event has additional information, the format of which is provided in the
MESSAGE/contentelement.%Alert%
<action>
The service event (for example, KL_ALERT_ServiceStarted).
%RecordContext%
<msg>
Context information about the service event.
- Fields of detection events
Field in kl_feed_service.conf
Field in v20_cybertracemsg.xml
Description
<232>
-
Service string for RSA NetWitness.
%CyberTrace:
%CyberTrace:
Informs RSA NetWitness that an event is sent from Feed Service.
MATCH_EVENT
<messageid>
The event type.
-
<!payload>
Notifies RSA NetWitness that the event has additional information, the format of which is provided in the
MESSAGE/contentelement.%Category%
<virusname>
Category of the detected object.
%MatchedIndicator%
<kl_detected_indicator%gt;
The detected indicator.
%RE_URL%
<url>
The URL specified in the event from RSA NetWitness.
%RE_HASH%
<checksum>
The hash specified in the event from RSA NetWitness.
%DST_IP%
<daddr>
The IP address to which the request is sent.
%SRC_IP%
<saddr>
The IP address from which the request is sent.
%DeviceIp%
<hostip>
The IP address from which the event is sent.
%Device%
<event_source>
The name of the device that has sent the event.
%DeviceAction%
<action>
The action that the device has performed.
%UserName%
<c_username>
The name of the user on whose account the action described in the event is performed.
%ActionableFields%
The fields' names are discussed below in this section.
Fields of the feed record involved in the detection process that are displayed apart from the context..
%RecordContext%
<fld1>
Context of the feed record that was involved in the detection process.
To view the contents of this field, open the event in RSA NetWitness and select the View Log tab.
The following tables describe the actionable fields used in the feeds and in the v20_cybertracemsg.xml file, and describe how fields in a feed correspond to fields in the file:
- Botnet CnC URL Data Feed and Demo Botnet CnC URL Data Feed
Field in the feed
Field in v20_cybertracemsg.xml
mask
kl_mask
first_seen
kl_first_seen
last_seen
kl_last_seen
popularity
kl_popularity
threat
kl_threat
- Malicious Hash Data Feed and Demo Malicious Hash Data Feed
Field in the feed
Field in v20_cybertracemsg.xml
MD5
kl_md5
SHA1
kl_sha1
SHA256
kl_sha256
first_seen
kl_first_seen
last_seen
kl_last_seen
popularity
kl_popularity
file_type
kl_file_type
file_size
kl_file_size
threat
kl_threat
- IP Reputation Data Feed and Demo IP Reputation Data Feed
Field in the feed
Field in v20_cybertracemsg.xml
ip
kl_ip
first_seen
kl_first_seen
last_seen
kl_last_seen
popularity
kl_popularity
threat_score
kl_threat_score
category
kl_category
threat
kl_threat
- Malicious URL Data Feed
Field in the feed
Field in v20_cybertracemsg.xml
mask
kl_mask
first_seen
kl_first_seen
last_seen
kl_last_seen
popularity
kl_popularity
files/threat
kl_threat
category
kl_category
- Mobile Malicious Hash Data Feed
Field in the feed
Field in v20_cybertracemsg.xml
MD5
kl_md5
SHA1
kl_sha1
SHA256
kl_sha256
first_seen
kl_first_seen
last_seen
kl_last_seen
popularity
kl_popularity
threat
kl_threat
file_size
kl_file_size
- Phishing URL Data Feed
Field in the feed
Field in v20_cybertracemsg.xml
mask
kl_mask
first_seen
kl_first_seen
last_seen
kl_last_seen
popularity
kl_popularity
industry
kl_industry
- P-SMS Trojan Data Feed and Vulnerability Data Feed
Field in the feed
Field in v20_cybertracemsg.xml
Date
kl_first_seen
AV Verdict
kl_verdict
When Vulnerability Data Feed is involved in a detection process, the
AV Verdictfield contains one of the following values:warninghighcritical
- Mobile Botnet CnC URL Data Feed
Field in the feed
Field in v20_cybertracemsg.xml
threat
kl_threat
- Ransomware URL Data Feed or IoT URL Data Feed
Field in the feed
Field in v20_cybertracemsg.xml
mask
kl_mask
first_seen
kl_first_seen
last_seen
kl_last_seen
popularity
kl_popularity
- APT feeds
Field in the feed
Field in v20_cybertracemsg.xml
detection_date
kl_detect_date
publication_name
kl_pub_name