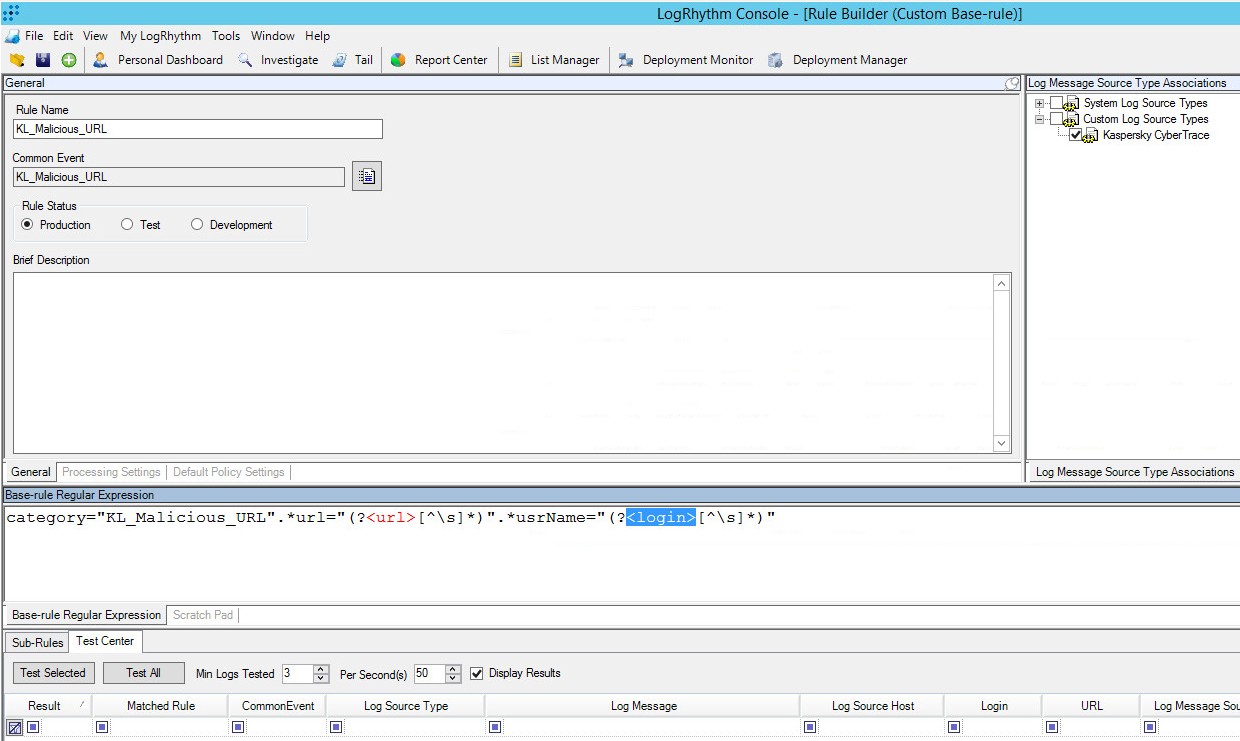
This section describes how you can add Kaspersky CyberTrace rules to LogRhythm manually.
The following table contains regular expressions for each event. If you want to use other regular expressions, use the example events from the third column of the table to check the regular expressions of your choice.
Event
|
Regular expression
|
Event example for checking regular expressions
|
AbuseCh_Feodo_Block_IP
|
category=AbuseCh_Feodo_Block_IP.*ip=(?<object>[^\s]*).*usrName=(?<login>[^\s]*)
|
May 2 16:41:40 category=AbuseCh_Feodo_Block_IP matchedIndicator=103.11.83.52 url=- src=- ip=103.11.83.52 md5=- sha1=- sha256=- usrName=VerifTestUserName ip=103.11.83.52 source=https://feodotracker.abuse.ch/downloads/ipblocklist.txt
|
AbuseCh_Feodo_Malware_Hash_MD5
|
category=AbuseCh_Feodo_Malware_Hash_MD5.*md5=(?<object>[^\s]*).*usrName=(?<login>[^\s]*)
|
May 2 16:41:40 category=AbuseCh_Feodo_Malware_Hash_MD5 matchedIndicator=86255ec982e822f6b57855d3866618ae url=- src=- ip=- md5=86255ec982e822f6b57855d3866618ae sha1=- sha256=- usrName=VerifTestUserName MD5=86255ec982e822f6b57855d3866618ae data_added=2015-09-22
|
AbuseCh_Ransomware_Block_URL
|
category=AbuseCh_Ransomware_Block_URL.*url=(?<url>[^\s]*).*usrName=(?<login>[^\s]*)
|
May 2 16:41:40 category=AbuseCh_Ransomware_Block_URL matchedIndicator=00005ik.rcomhost.com/7fg3g url=00005ik.rcomhost.com/7fg3g src=- ip=- md5=- sha1=- sha256=- usrName=- source=https://ransomwaretracker.abuse.ch/downloads/RW_URLBL.txt url=00005ik.rcomhost.com/7fg3g
|
AbuseCh_Ransomware_Block_Domain
|
category=AbuseCh_Ransomware_Block_Domain.*url=(?<url>[^\s]*).*usrName=(?<login>[^\s]*)
|
May 2 16:41:40 category=AbuseCh_Ransomware_Block_Domain matchedIndicator=pagaldaily.com url=pagaldaily.com src=- ip=- md5=- sha1=- sha256=- usrName=- domain=pagaldaily.com source=https://ransomwaretracker.abuse.ch/downloads/RW_DOMBL.txt
|
AbuseCh_Ransomware_Block_IP
|
category=AbuseCh_Ransomware_Block_IP.*ip=(?<object>[^\s]*).*usrName=(?<login>[^\s]*)
|
May 2 16:41:40 category=AbuseCh_Ransomware_Block_IP matchedIndicator=83.217.11.193 url=- src=- ip=83.217.11.193 md5=- sha1=- sha256=- usrName=VerifTestUserName ip=83.217.11.193 source=https://ransomwaretracker.abuse.ch/downloads/RW_IPBL.txt
|
AbuseCh_Ransomware_Common_URL
|
category=AbuseCh_Ransomware_Common_URL.*url=(?<url>[^\s]*).*usrName=(?<login>[^\s]*)
|
May 2 16:41:40 category=AbuseCh_Ransomware_Common_URL matchedIndicator=83.217.11.193/linuxsucks.php url=83.217.11.193/linuxsucks.php src=- ip=- md5=- sha1=- sha256=- usrName=- ASN=199669 IPList=[{ ip=83.217.11.193}] country=RU domain=83.217.11.193 first_seen=12.08.2018 00:46 malware=Locky registar= source=https://ransomwaretracker.abuse.ch/feeds/csv/ status=offline threat=C2 url=83.217.11.193/linuxsucks.php
|
AbuseCh_SSL_Certificate_Block_IP
|
category=AbuseCh_SSL_Certificate_Block_IP.*ip=(?<object>[^\s]*).*usrName=(?<login>[^\s]*)
|
May 2 16:41:40 category=AbuseCh_SSL_Certificate_Block_IP matchedIndicator=83.217.11.193 url=- src=- ip=83.217.11.193 md5=- sha1=- sha256=- usrName=VerifTestUserName ip=83.217.11.193 source=https://sslbl.abuse.ch/blacklist/sslblacklist.csv
|
AbuseCh_SSL_Certificate_Hash_SHA1
|
category=AbuseCh_SSL_Certificate_Hash_SHA1.*sha1=(?<object>[^\s]*).*usrName=(?<login>[^\s]*)
|
May 2 16:41:40 category= AbuseCh_SSL_Certificate_Hash_SHA1 matchedIndicator=3395856ce81f2b7382dee72602f798b642f14140 url=- src=- ip=- md5=- sha1=3395856ce81f2b7382dee72602f798b642f14140 sha256=- usrName=VerifTestUserName MD5=86255ec982e822f6b57855d3866618ae data_added=2015-09-22
|
BlocklistDe_Block_IP
|
category=BlocklistDe_Block_IP.*ip=(?<object>[^\s]*).*usrName=(?<login>[^\s]*)
|
May 2 16:41:40 category=BlocklistDe_Block_IP matchedIndicator=83.217.11.193 url=- src=- ip=83.217.11.193 md5=- sha1=- sha256=- usrName=VerifTestUserName ip=83.217.11.193
|
CyberCrime_Tracker_Block_Url
|
category= CyberCrime_Tracker_Block_Url.*url=(?<url>[^\s]*).*usrName=(?<login>[^\s]*)
|
May 2 16:41:40 category=CyberCrime_Tracker_Block_Url matchedIndicator=83.217.11.193/linuxsucks.php url=83.217.11.193/linuxsucks.php src=- ip=- md5=- sha1=- sha256=- usrName=- ASN=199669 IPList=[{ ip=83.217.11.193}] country=RU domain=83.217.11.193 first_seen=12.08.2018 00:46 malware=Locky status=offline threat=C2 url=83.217.11.193/linuxsucks.php
|
EmergingThreats_Block_IP
|
category=EmergingThreats_Block_IP.*ip=(?<object>[^\s]*).*usrName=(?<login>[^\s]*)
|
May 2 16:41:40 category=EmergingThreats_Block_IP matchedIndicator=101.200.81.187 url=- src=- ip=101.200.81.187 md5=- sha1=- sha256=- usrName=VerifTestUserName ip=101.200.81.187 source=https://rules.emergingthreats.net/fwrules/emerging-Block-IPs.txt
|
EmergingThreats_Compromised_IP
|
category=EmergingThreats_Compromised_IP.*ip=(?<object>[^\s]*).*usrName=(?<login>[^\s]*)
|
May 2 16:41:40 category=EmergingThreats_Compromised_IP matchedIndicator=100.24.121.249 url=- src=- ip=100.24.121.249 md5=- sha1=- sha256=- usrName=VerifTestUserName ip=100.24.121.249 source=https://rules.emergingthreats.net/blockrules/compromised-ips.txt
|
KL_ALERT_FeedBecameAvailable
|
alert=KL_ALERT_FeedBecameAvailable.*feed=(?<object>[^\s]*)
|
May 2 16:41:40 alert=KL_ALERT_FeedBecameAvailable feed=Botnet_CnC_URL_Data_Feed.json
|
KL_ALERT_FeedBecameUnavailable
|
alert=KL_ALERT_FeedBecameUnavailable.*feed=(?<object>[^\s]*)
|
May 2 16:41:40 alert=KL_ALERT_FeedBecameUnavailable feed=Botnet_CnC_URL_Data_Feed.json
|
KL_ALERT_OutdatedFeed
|
alert=KL_ALERT_OutdatedFeed.*feed=(?<object>[^\s]*)
|
May 2 16:41:40 alert=KL_ALERT_OutdatedFeed feed=Botnet_CnC_URL_Data_Feed.json
|
KL_ALERT_ServiceStarted
|
alert=KL_ALERT_ServiceStarted
|
May 2 16:41:40 alert=KL_ALERT_ServiceStarted
|
KL_ALERT_ServiceStopped
|
alert=KL_ALERT_ServiceStopped
|
May 2 16:41:40 alert=KL_ALERT_ServiceStopped
|
KL_ALERT_ServiceUnavailable
|
alert=KL_ALERT_ServiceUnavailable
|
May 2 16:41:40 alert=KL_ALERT_ServiceUnavailable
|
KL_ALERT_UpdatedFeed
|
alert=KL_ALERT_UpdatedFeed.*feed=(?<object>[^\s]*).*records=(?<quantity>[^\s]*)
|
May 2 16:41:40 alert=KL_ALERT_UpdatedFeed feed=Botnet_CnC_URL_Data_Feed.json records=23
|
KL_ALERT_FailedToUpdateFeed
|
alert=KL_ALERT_FailedToUpdateFeed.*feed=(?<object>[^\s]*)
|
May 2 16:41:40 alert=KL_ALERT_FailedToUpdateFeed feed=Botnet_CnC_URL_Data_Feed.json
|
KL_ALERT_LicenseExpires
|
alert=KL_ALERT_LicenseExpires.*license_name=(?<object>[^\s]*)
|
May 2 16:41:40 alert=KL_ALERT_LicenseExpires expiration_date=23.02.2020 license_name=kl_license
|
KL_ALERT_LicenseExpired
|
alert=KL_ALERT_LicenseExpired.*license_name=(?<object>[^\s]*)
|
May 2 16:41:40 alert=KL_ALERT_LicenseExpired expiration_date=23.02.2020 license_name=kl_license
|
KL_ALERT_EPSLimitExceeded
|
alert=KL_ALERT_EPSLimitExceeded.*current_eps=(?<quantity>[^\s]*)
|
May 2 16:41:40 alert=KL_ALERT_EPSLimitExceeded current_eps=6500 license_limit_eps=5000
|
KL_ALERT_EPSHardLimit
|
alert=KL_ALERT_EPSHardLimit.*license_limit_eps=(?<quantity>[^\s]*)
|
May 2 16:41:40 alert=KL_ALERT_EPSHardLimit license_limit_eps=5000
|
KL_ALERT_FeedLoadedPartially
|
alert=KL_ALERT_FeedLoadedPartially.*feed=(?<object>[^\s]*).*loaded_records=(?<quantity>[^\s]*)
|
May 2 16:41:40 alert=KL_ALERT_FeedLoadedPartially feed=Botnet_CnC_URL_Data_Feed.json loaded_records=23
|
KL_ALERT_LicenseChanged
|
alert=KL_ALERT_LicenseChanged.*license_name=(?<object>[^\s]*)
|
May 2 16:41:40 alert=KL_ALERT_LicenseChanged expiration_date=23.02.2020 license_name=kl_license license_level=EnterpriseTIP
|
KL_ALERT_ConfigurationUpdated
|
alert=KL_ALERT_ConfigurationUpdated
|
May 2 16:41:40 alert=KL_ALERT_ConfigurationUpdated
|
KL_APT_Hash_MD5
|
category=KL_APT_Hash_MD5.*matchedIndicator=(?<object>[^\s]*).*usrName=(?<login>[^\s]*)
|
May 2 16:41:40 category=KL_APT_Hash_MD5 matchedIndicator=7A2E65A0F70EE0615EC0CA34240CF082 url=- src=192.168.0.0 ip=- md5=7A2E65A0F70EE0615EC0CA34240CF082 sha1=- sha256=- usrName=VerifTestUserName MD5=7A2E65A0F70EE0615EC0CA34240CF082 detection_date=01.06.2018 00:00 publication_name=TestRecord
|
KL_APT_IP
|
category=KL_APT_IP.*matchedIndicator=(?<object>[^\s]*).*usrName=(?<login>[^\s]*)
|
May 2 16:41:40 category=KL_APT_IP matchedIndicator=192.0.2.4 url=- src=192.168.0.0 ip=192.0.2.4 md5=- sha1=- sha256=- usrName=VerifTestUserName detection_date=01.06.2018 00:00 ip=192.0.2.4 publication_name=TestRecord
|
KL_APT_URL
|
category=KL_APT_URL.*matchedIndicator=(?<url>[^\s]*).*usrName=(?<login>[^\s]*)
|
May 2 16:41:40 category=KL_APT_URL matchedIndicator=b046f5b25458638f6705d53539c79f62.com url=b046f5b25458638f6705d53539c79f62.com src=192.168.0.0 ip=- md5=- sha1=- sha256=- usrName=VerifTestUserName detection_date=01.06.2018 00:00 id=0 mask=b046f5b25458638f6705d53539c79f62.com publication_name=TestRecord type=1
|
KL_BlackList_Hash_MD5
|
category=KL_BlackList_Hash_MD5.*matchedIndicator=(?<object>[^\s]*).*usrName=(?<login>[^\s]*)
|
May 2 16:41:40 category=KL_BlackList_Hash_MD5 matchedIndicator=44D88612FEA8A8F36DE82E1278ABB02F url=- src=- ip=- md5=44D88612FEA8A8F36DE82E1278ABB02F sha1=- sha256=- usrName=- MD5=44D88612FEA8A8F36DE82E1278ABB02F
|
KL_BlackList_Hash_SHA1
|
category=KL_BlackList_Hash_SHA1.*matchedIndicator=(?<object>[^\s]*).*usrName=(?<login>[^\s]*)
|
May 2 16:41:40 category=KL_BlackList_Hash_SHA1 matchedIndicator=3395856ce81f2b7382dee72602f798b642f14140 url=- src=- ip=- md5=- sha1=3395856ce81f2b7382dee72602f798b642f14140 sha256=- usrName=- SHA1=3395856ce81f2b7382dee72602f798b642f14140
|
KL_BlackList_Hash_SHA256
|
category=KL_BlackList_Hash_SHA256.*matchedIndicator=(?<object>[^\s]*).*usrName=(?<login>[^\s]*)
|
May 2 16:41:40 category=KL_Malicious_Hash_SHA256 matchedIndicator=275a021bbfb6489e54d471899f7db9d1663fc695ec2fe2a2c4538aabf651fd0f url=- src=- ip=- md5=- sha1=- sha256=275a021bbfb6489e54d471899f7db9d1663fc695ec2fe2a2c4538aabf651fd0f usrName=- MD5=44D88612FEA8A8F36DE82E1278ABB02F SHA1=3395856CE81F2B7382DEE72602F798B642F14140 SHA256=275A021BBFB6489E54D471899F7DB9D1663FC695EC2FE2A2C4538AABF651FD0F file_size=68 first_seen=02.04.2010 22:07 last_seen=17.03.2017 13:33 popularity=5 threat=EICAR-Test-File
|
KL_BlackList_IP
|
category=KL_BlackList_IP.*matchedIndicator=(?<object>[^\s]*).*usrName=(?<login>[^\s]*)
|
May 2 16:41:40 category=KL_BlackList_IP matchedIndicator=192.0.2.0 url=- src=- ip=192.0.2.0 md5=- sha1=- sha256=- usrName=- ip=192.0.2.0
|
KL_BlackList_URL
|
category=KL_BlackList_URL.*matchedIndicator=(?<url>[^\s]*).*usrName=(?<login>[^\s]*)
|
May 2 16:41:40 category=KL_BlackList_URL matchedIndicator=fakess123.nu url=fakess123.nu src=- ip=- md5=- sha1=- sha256=- usrName=- mask=fakess123.nu
|
KL_BotnetCnC_Hash_MD5
|
category=KL_BotnetCnC_Hash_MD5.*md5=(?<object>[^\s]*).*usrName=(?<login>[^\s]*).*mask=(?<url>[^\s]*).*threat=(?<objectname>[^\s]*)
|
May 2 16:41:40 category=KL_BotnetCnC_Hash_MD5 url=- md5=E013C01AB3E27BE6FBA4E23EE88B100F sha1=- sha256=- ip=- usrName=VerifTestUserName IP=118.142.224.213, 160.16.120.71, 61.19.201.7 files=[{MD5=E013C01AB3E27BE6FBA4E23EE88B100F SHA256=C00269AA2BCF375D0CF870C36F737C27EBB04F69F5B6912F860D8A1F5F1D9DF6}] first_seen=08.07.2015 23:39 geo=jp, hk, tw, au, th, cn, my, ph, vn, in id=9189405 last_seen=29.10.2015 15:59 mask=172.117.45.14/pid=1000/botnet_setup_3.exe popularity=5 threat=Trojan-Banker.AndroidOS.Wroba type=3
|
KL_BotnetCnC_Hash_SHA1
|
category=KL_BotnetCnC_Hash_SHA1.*sha1=(?<object>[^\s]*).*usrName=(?<login>[^\s]*).*mask=(?<url>[^\s]*).*threat=(?<objectname>[^\s]*)
|
May 2 16:41:40 category=KL_BotnetCnC_Hash_SHA1 url=- md5=- sha1=FE61DED0504013D9ED6691F6C5BB69DCD8C8DD60 sha256=- ip=- usrName=VerifTestUserName IP=78.47.151.188 files=[{SHA1=FE61DED0504013D9ED6691F6C5BB69DCD8C8DD60 SHA256=B6AEF9CBFA21B0A9E6D03364F5476B81C4A5D8EF212DFB35E3EF96003CADCB0B}] first_seen=21.07.2015 12:19 geo=it, es, de, fr, gb id=9320249 last_seen=14.01.2016 12:55 mask=botnet_domain_4.com/get.php?p=4&id=2 popularity=4 threat=Trojan-SMS.AndroidOS.Opfake type=4
|
KL_BotnetCnC_Hash_SHA256
|
category=KL_BotnetCnC_Hash_SHA256.*sha256=(?<object>[^\s]*).*usrName=(?<login>[^\s]*).*mask=(?<url>[^\s]*).*threat=(?<objectname>[^\s]*)
|
May 2 16:41:40 category=KL_BotnetCnC_Hash_SHA256 url=- md5=- sha1=- sha256=AFDD5508B48B8270C1DBAF32121A00951E450A56791275D8E7C413EF8380A809 ip=- usrName=VerifTestUserName IP=46.4.114.61, 95.213.186.51, 95.213.192.71, 176.9.82.215, 178.63.12.207, 109.206.186.164, 176.9.48.86, 213.163.70.170, 95.213.192.83, 173.45.161.113 files=[{MD5=55B8D137C80AE5E995EC355524594F3B SHA1=BEA6B860C719F1C886461C8A3FF4935471D2FA64 SHA256=AFDD5508B48B8270C1DBAF32121A00951E450A56791275D8E7C413EF8380A809}] first_seen=15.04.2015 13:18 geo=vn, in, tr, mx, ir, bd, id, dz, ph, th id=9230458 last_seen=14.01.2016 12:55 mask=*.subbotnet_domain_19.botnet_domain.com popularity=5 threat=Trojan.Win32.Agent type=19
|
KL_BotnetCnC_URL
|
category=KL_BotnetCnC_URL.*url=(?<url>[^\s]*).*usrName=(?<login>[^\s]*)
|
May 2 16:41:40 category=KL_BotnetCnC_URL url=http://d.subphishing_domain.phishing_domain_19.com md5=- sha1=- sha256=- ip=- usrName=VerifTestUserName IP=104.168.159.146, 138.201.0.229, 138.201.0.231, 138.201.0.230, 78.46.185.21, 78.46.185.23, 78.46.185.12, 78.46.185.3, 78.46.185.16, 78.46.185.28 first_seen=12.01.2016 12:50 geo=br, pt, us id=9508721 last_seen=14.01.2016 13:36 mask=*.subphishing_domain.phishing_domain_19.com popularity=5 type=19
|
KL_IP_Reputation
|
category=KL_IP_Reputation.*ip=(?<object>[^\s]*).*usrName=(?<login>[^\s]*).*category=(?<process>[^\s]*).*threat_score=(?<severity>[^\s]*)
|
May 2 16:41:40 category=KL_IP_Reputation url=- md5=- sha1=- sha256=- ip=18.50.1.47 usrName=VerifiTestUserName category=spam first_seen=21.01.2015 00:00 ip=18.50.1.47 ip_geo=us last_seen=17.05.2016 03:16 popularity=1 threat_score=100
|
KL_IP_Reputation_Hash_MD5
|
category=KL_IP_Reputation_Hash_MD5.*matchedIndicator=(?<object>[^\s]*).*usrName=(?<login>[^\s]*)
|
May 2 16:41:40 category=KL_IP_Reputation_Hash_MD5 matchedIndicator=61200D253ADD14C91CD64F2CB1F221CB url=- src=- ip=- md5=61200D253ADD14C91CD64F2CB1F221CB sha1=- sha256=- usrName=- category=malware domains=k4d7ppv9.humanpchelp.pw, mwi49i2b.backbonecomputer.top, 9uq5mmw7.overseascomputer.pw, 9tqnii2s.motivationcomputer.pw, 4iaag9ng.luxurypchelp.pw, kxol25kx.pcserviceline.top, 7ifiye96.phoenixcomputerhelp.pw, tnv5yyvj.pcservicecatch.pw, y4ki19os.computercoral.top, pmayaidy.rankpcservice.top files=[{ MD5=61200D253ADD14C91CD64F2CB1F221CB SHA1=E23B0F6ECEFF56870908B2EC704F62ACB4E005AD SHA256=7FC582451A8D9EAF112A3CFC7EFF8EBC8A5FCB8480E42A8D2B5A4E0E3C12D793 threat=HEUR:Trojan.Script.Generic},{ MD5=06A2E41E9CDA9C19AF5FB29483687A56 SHA1=37ED2076FCC0365BA02210E18BBAB162D7338180 SHA256=9570F5C81FF906CD52EE42B5D24359B8A7CA4EC225C532A811699F1089847252 threat=HEUR:Trojan.Script.Generic},{ MD5=AA909F4A33A0D305C0ADF7FCD6DC95E5 SHA1=0A88A71A3C43F02075B7B3CB1A6ED1A603CC666E SHA256=96467635B09D64B29DEAF2A7923ADCD63C2E7F9308B80DDF46F251EBDB2E6A66 threat=HEUR:Trojan.Script.Generic},{ MD5=1D02D52FE17A040A2C7D7C4EE7020E6A SHA1=036D8147D00334824073A22C3D7016EE27643CBD SHA256=737117D867D8CC777AF09F635126C6867ADD08C47C74EDCF5636A84F3F14911B threat=HEUR:Trojan.Script.Generic},{ MD5=393F797A732D5FF35B6102B298349C65 SHA1=760C99F3FB4330BA7B9EB76780718E3023C345EE SHA256=5E86FE0A4DA6A1394DBC6BD2D0F7BD2791BCC1099F83B04282B0508005212FCB threat=HEUR:Trojan.Script.Generic},{ MD5=5A90DDAAEA8646E84927E5DD7BAAA3E2 SHA1=CA2EEF839CF649E42EB4F7E618BD491B40340462 SHA256=1A73D4EA89E89C22B3B03E1A841882A59FCC1ED18299D6914DF4BC2E5CF05A44 threat=HEUR:Trojan.Script.Generic}] first_seen=21.02.2019 23:57 ip=93.115.27.83 ip_geo=lt ip_whois={ asn=16125 country=LT created=01.12.2016 net_name=CHERRYSERVERS-LT-DEDICATED net_range=93.115.27.0 - 93.115.27.255 updated=01.12.2016} last_seen=22.05.2019 19:18 popularity=5 threat_score=94 users_geo=de, jp, fr, it, ch, at, be, pl, es, dz
|
KL_IP_Reputation_Hash_SHA1
|
category=KL_IP_Reputation_Hash_SHA1.*matchedIndicator=(?<object>[^\s]*).*usrName=(?<login>[^\s]*)
|
May 2 16:41:40 category=KL_IP_Reputation_Hash_SHA1 matchedIndicator=E23B0F6ECEFF56870908B2EC704F62ACB4E005AD url=- src=- ip=- md5=- sha1=E23B0F6ECEFF56870908B2EC704F62ACB4E005AD sha256=- usrName=- category=malware domains=k4d7ppv9.humanpchelp.pw, mwi49i2b.backbonecomputer.top, 9uq5mmw7.overseascomputer.pw, 9tqnii2s.motivationcomputer.pw, 4iaag9ng.luxurypchelp.pw, kxol25kx.pcserviceline.top, 7ifiye96.phoenixcomputerhelp.pw, tnv5yyvj.pcservicecatch.pw, y4ki19os.computercoral.top, pmayaidy.rankpcservice.top files=[{ MD5=61200D253ADD14C91CD64F2CB1F221CB SHA1=E23B0F6ECEFF56870908B2EC704F62ACB4E005AD SHA256=7FC582451A8D9EAF112A3CFC7EFF8EBC8A5FCB8480E42A8D2B5A4E0E3C12D793 threat=HEUR:Trojan.Script.Generic},{ MD5=06A2E41E9CDA9C19AF5FB29483687A56 SHA1=37ED2076FCC0365BA02210E18BBAB162D7338180 SHA256=9570F5C81FF906CD52EE42B5D24359B8A7CA4EC225C532A811699F1089847252 threat=HEUR:Trojan.Script.Generic},{ MD5=AA909F4A33A0D305C0ADF7FCD6DC95E5 SHA1=0A88A71A3C43F02075B7B3CB1A6ED1A603CC666E SHA256=96467635B09D64B29DEAF2A7923ADCD63C2E7F9308B80DDF46F251EBDB2E6A66 threat=HEUR:Trojan.Script.Generic},{ MD5=1D02D52FE17A040A2C7D7C4EE7020E6A SHA1=036D8147D00334824073A22C3D7016EE27643CBD SHA256=737117D867D8CC777AF09F635126C6867ADD08C47C74EDCF5636A84F3F14911B threat=HEUR:Trojan.Script.Generic},{ MD5=393F797A732D5FF35B6102B298349C65 SHA1=760C99F3FB4330BA7B9EB76780718E3023C345EE SHA256=5E86FE0A4DA6A1394DBC6BD2D0F7BD2791BCC1099F83B04282B0508005212FCB threat=HEUR:Trojan.Script.Generic},{ MD5=5A90DDAAEA8646E84927E5DD7BAAA3E2 SHA1=CA2EEF839CF649E42EB4F7E618BD491B40340462 SHA256=1A73D4EA89E89C22B3B03E1A841882A59FCC1ED18299D6914DF4BC2E5CF05A44 threat=HEUR:Trojan.Script.Generic}] first_seen=21.02.2019 23:57 ip=93.115.27.83 ip_geo=lt ip_whois={ asn=16125 country=LT created=01.12.2016 net_name=CHERRYSERVERS-LT-DEDICATED net_range=93.115.27.0 - 93.115.27.255 updated=01.12.2016} last_seen=22.05.2019 19:18 popularity=5 threat_score=94 users_geo=de, jp, fr, it, ch, at, be, pl, es, dz
|
KL_IP_Reputation_Hash_SHA256
|
category=KL_IP_Reputation_Hash_SHA256.*matchedIndicator=(?<object>[^\s]*).*usrName=(?<login>[^\s]*)
|
May 2 16:41:40 category=KL_IP_Reputation_Hash_SHA256 matchedIndicator=7FC582451A8D9EAF112A3CFC7EFF8EBC8A5FCB8480E42A8D2B5A4E0E3C12D793 url=- src=- ip=- md5=- sha1=- sha256=7FC582451A8D9EAF112A3CFC7EFF8EBC8A5FCB8480E42A8D2B5A4E0E3C12D793 usrName=- category=malware domains=k4d7ppv9.humanpchelp.pw, mwi49i2b.backbonecomputer.top, 9uq5mmw7.overseascomputer.pw, 9tqnii2s.motivationcomputer.pw, 4iaag9ng.luxurypchelp.pw, kxol25kx.pcserviceline.top, 7ifiye96.phoenixcomputerhelp.pw, tnv5yyvj.pcservicecatch.pw, y4ki19os.computercoral.top, pmayaidy.rankpcservice.top files=[{ MD5=61200D253ADD14C91CD64F2CB1F221CB SHA1=E23B0F6ECEFF56870908B2EC704F62ACB4E005AD SHA256=7FC582451A8D9EAF112A3CFC7EFF8EBC8A5FCB8480E42A8D2B5A4E0E3C12D793 threat=HEUR:Trojan.Script.Generic},{ MD5=06A2E41E9CDA9C19AF5FB29483687A56 SHA1=37ED2076FCC0365BA02210E18BBAB162D7338180 SHA256=9570F5C81FF906CD52EE42B5D24359B8A7CA4EC225C532A811699F1089847252 threat=HEUR:Trojan.Script.Generic},{ MD5=AA909F4A33A0D305C0ADF7FCD6DC95E5 SHA1=0A88A71A3C43F02075B7B3CB1A6ED1A603CC666E SHA256=96467635B09D64B29DEAF2A7923ADCD63C2E7F9308B80DDF46F251EBDB2E6A66 threat=HEUR:Trojan.Script.Generic},{ MD5=1D02D52FE17A040A2C7D7C4EE7020E6A SHA1=036D8147D00334824073A22C3D7016EE27643CBD SHA256=737117D867D8CC777AF09F635126C6867ADD08C47C74EDCF5636A84F3F14911B threat=HEUR:Trojan.Script.Generic},{ MD5=393F797A732D5FF35B6102B298349C65 SHA1=760C99F3FB4330BA7B9EB76780718E3023C345EE SHA256=5E86FE0A4DA6A1394DBC6BD2D0F7BD2791BCC1099F83B04282B0508005212FCB threat=HEUR:Trojan.Script.Generic},{ MD5=5A90DDAAEA8646E84927E5DD7BAAA3E2 SHA1=CA2EEF839CF649E42EB4F7E618BD491B40340462 SHA256=1A73D4EA89E89C22B3B03E1A841882A59FCC1ED18299D6914DF4BC2E5CF05A44 threat=HEUR:Trojan.Script.Generic}] first_seen=21.02.2019 23:57 ip=93.115.27.83 ip_geo=lt ip_whois={ asn=16125 country=LT created=01.12.2016 net_name=CHERRYSERVERS-LT-DEDICATED net_range=93.115.27.0 - 93.115.27.255 updated=01.12.2016} last_seen=22.05.2019 19:18 popularity=5 threat_score=94 users_geo=de, jp, fr, it, ch, at, be, pl, es, dz
|
KL_Malicious_Hash_MD5
|
category=KL_Malicious_Hash_MD5.*md5=(?<object>[^\s]*).*usrName=(?<login>[^\s]*).*file_size=(?<size>[^\s]*).*threat=(?<objectname>[^\s]*)
|
May 2 16:41:40 category=KL_Malicious_Hash_MD5 url=- md5=0F1DCBB2A888B99FAE72144087CAE565 sha1=- sha256=- ip=- usrName=VerifTestUserName MD5=0F1DCBB2A888B99FAE72144087CAE565 file_size=105472 file_type=PE first_seen=26.11.2015 13:06 geo=ru, ro, ua, tj, us, cz, kz, gb last_seen=14.01.2016 12:29 popularity=5 threat=UDS:DangerousObject.Multi.Generic
|
KL_Malicious_Hash_SHA1
|
category=KL_Malicious_Hash_SHA1.*sha1=(?<object>[^\s]*).*usrName=(?<login>[^\s]*).*file_size=(?<size>[^\s]*).*threat=(?<objectname>[^\s]*)
|
May 2 16:41:40 category=KL_Malicious_Hash_SHA1 url=- md5=- sha1=6665856CE81F2B7382DEE72602F798B642F14140 sha256=- ip=- usrName=VerifTestUserName MD5=55D88612FEA8A8F36DE82E1278ABB02F SHA1=6665856CE81F2B7382DEE72602F798B642F14140 SHA256=275A021BBFB6489E54D471899F7DB9D1663FC695EC2FE2A2C4777AABF651FD0F file_size=68 first_seen=02.04.2010 22:07 last_seen=14.01.2016 13:41 popularity=5 threat=EICAR-Test-File
|
KL_Malicious_Hash_SHA256
|
category=KL_Malicious_Hash_SHA256.*sha256=(?<object>[^\s]*).*usrName=(?<login>[^\s]*).*file_size=(?<size>[^\s]*).*threat=(?<objectname>[^\s]*)
|
May 2 16:41:40 category=KL_Malicious_Hash_SHA256 url=- md5=- sha1=- sha256=EC1D5E24A9F866F21118914445AB0A00A60F791B51478F3D0DD375A6BD45897D ip=- usrName=VerifTestUserName SHA1=C365DC5128FF0A607D78BFBAB36E08263DC66B18 SHA256=EC1D5E24A9F866F21118914445AB0A00A60F791B51478F3D0DD375A6BD45897D file_size=1696256 file_type=PE first_seen=15.07.2015 11:50 geo=ru, ua, by, dz, ir, eg, kz, mx, in, tr last_seen=14.01.2016 12:29 popularity=5 threat=HackTool.Win32.KRT.bw
|
KL_Malicious_URL
|
category=KL_Malicious_URL.*url=(?<url>[^\s]*).*usrName=(?<login>[^\s]*)
|
May 2 16:41:40 category=KL_Malicious_URL url=http://sub1.submalicious_domain.malicious_domain_19.com md5=- sha1=- sha256=- ip=- usrName=VerifTestUserName IP=217.23.14.223 first_seen=14.01.2016 02:42 geo=ru, kz, ro, ua, by, cz id=9524476 last_seen=14.01.2016 13:36 mask=*.submalicious_domain.malicious_domain_19.com popularity=5 type=19
|
KL_Malicious_URL_Hash_MD5
|
category=KL_Malicious_URL_Hash_MD5.*matchedIndicator=(?<object>[^\s]*).*usrName=(?<login>[^\s]*)
|
May 2 16:41:40 category=KL_Malicious_URL_Hash_MD5 matchedIndicator=C735608E2DDE63857C3877AE438EBF78 url=- src=- ip=- md5=C735608E2DDE63857C3877AE438EBF78 sha1=- sha256=- usrName=- IP=104.27.160.251, 104.27.161.251, 145.239.252.74, 46.35.111.137, 207.244.89.108, 54.37.87.37, 207.244.89.90, 77.111.246.8, 131.173.16.52 category=Malware files=[{ MD5=C735608E2DDE63857C3877AE438EBF78 SHA1=9FB04AB8756742E9903A9A77566938DC9D83138C SHA256=127E83998D65FD80328D89B87B9C4CB5756C57FCC03189FAC5B7D77D4FB48FC5 threat=HEUR:Trojan.Script.Miner.gen}] first_seen=15.03.2019 14:27 geo=es, de, it, ru, ve, pl, pt, jp, kz, mx id=29703667 last_seen=23.05.2019 14:12 mask=tercabilis.info popularity=4 type=1 whois={ NS=art.ns.cloudflare.com, olga.ns.cloudflare.com NS_ips=173.245.58.137, 173.245.59.102 country=FR created=02.10.2018 domain=tercabilis.info expires=02.10.2019 org=NETIM registrar_name=NETIM SARL updated=01.12.2018}
|
KL_Malicious_URL_Hash_SHA1
|
category=KL_Malicious_URL_Hash_SHA1.*matchedIndicator=(?<object>[^\s]*).*usrName=(?<login>[^\s]*)
|
May 2 16:41:40 category=KL_Malicious_URL_Hash_SHA1 matchedIndicator=9FB04AB8756742E9903A9A77566938DC9D83138C url=- src=- ip=- md5=- sha1=9FB04AB8756742E9903A9A77566938DC9D83138C sha256=- usrName=- IP=163.172.129.78, 212.47.250.90 category=Malware files=[{ MD5=9096549542B5A4E711BF04732416AA97 SHA1=4616FF9FBFF692535C6F0D9BD347CC0593A1F6B8 threat=HEUR:Trojan.Script.Miner.gen},{ MD5=6CBF2B0ADC72F64913EDE949A3F93B2D SHA1=5BB602A5A3AE5C685F0EB9CF2BFE9546DFC5832A SHA256=E804F6ADF2B7C99A8E0B158E880DF3172131CFAD7D796A75CBC2E46606371D2E threat=HEUR:Trojan.Script.Miner.gen},{ MD5=C735608E2DDE63857C3877AE438EBF78 SHA1=9FB04AB8756742E9903A9A77566938DC9D83138C SHA256=127E83998D65FD80328D89B87B9C4CB5756C57FCC03189FAC5B7D77D4FB48FC5 threat=HEUR:Trojan.Script.Miner.gen}] first_seen=29.05.2018 15:54 geo=ru, kz, by, ua id=23128232 last_seen=23.03.2019 12:07 mask=play.on.animeteatr.ru popularity=3 type=2
|
KL_Malicious_URL_Hash_SHA256
|
category=KL_Malicious_URL_Hash_SHA256.*matchedIndicator=(?<object>[^\s]*).*usrName=(?<login>[^\s]*)
|
May 2 16:41:40 category=KL_Malicious_URL_Hash_SHA256 matchedIndicator=127E83998D65FD80328D89B87B9C4CB5756C57FCC03189FAC5B7D77D4FB48FC5 url=- src=- ip=- md5=- sha1=- sha256=127E83998D65FD80328D89B87B9C4CB5756C57FCC03189FAC5B7D77D4FB48FC5 usrName=- IP=163.172.129.78, 212.47.250.90, 173.192.191.169, 167.99.216.96, 89.238.177.226 category=Malware files=[{ MD5=C735608E2DDE63857C3877AE438EBF78 SHA1=9FB04AB8756742E9903A9A77566938DC9D83138C SHA256=127E83998D65FD80328D89B87B9C4CB5756C57FCC03189FAC5B7D77D4FB48FC5 threat=HEUR:Trojan.Script.Miner.gen},{ MD5=978E8C1CB071387ABBB4A673FF918BB9 SHA1=AFAEEE65BB483994FAC36A6B97F10B2BAA51F832 SHA256=3CFAACB2E8EE3E7CC5685DEDDFED7E34BF7595015307FEE64DD3C196C1D4ED93 threat=HEUR:Trojan.Script.Miner.gen},{ MD5=9096549542B5A4E711BF04732416AA97 SHA1=4616FF9FBFF692535C6F0D9BD347CC0593A1F6B8 threat=HEUR:Trojan.Script.Miner.gen},{ MD5=3FF0CF473B1E8FEB3BC018AF999DF4F5 SHA1=6813E9BB538F4AE1290411DD6AC48D615B5A4F21 threat=HEUR:Trojan.Script.Miner.gen},{ MD5=6CBF2B0ADC72F64913EDE949A3F93B2D SHA1=5BB602A5A3AE5C685F0EB9CF2BFE9546DFC5832A SHA256=E804F6ADF2B7C99A8E0B158E880DF3172131CFAD7D796A75CBC2E46606371D2E threat=HEUR:Trojan.Script.Miner.gen},{ MD5=44A27780FD4ABF64BF4EBB5584857160 SHA1=C9552F0DBF8A213556F3CC0CBD98CBFD157362F9 SHA256=EB703A25657D70CD85059A1AFD4720DF5273C4775EE05C6A2B1D3FBFD84D767C threat=HEUR:Trojan.Script.Miner.gen}] first_seen=29.05.2018 15:54 geo=de, gr, it, gb, pl, dz, hu, at, br, ch id=23128262 last_seen=07.04.2019 20:16 mask=play.play1.videos.vidto.me popularity=4 type=2 whois={ MX=mail.vidto.me, mail2.vidto.me MX_ips=158.69.116.96 NS=pns1.cloudns.net, pns2.cloudns.net, pns3.cloudns.net, pns4.cloudns.net NS_ips=185.136.96.111, 185.136.97.111, 185.136.98.111, 185.136.99.111 country=SE created=21.06.2012 domain=vidto.me expires=21.06.2021 org=Shield Whois registrar_name=AB NameISP updated=23.11.2018}
|
KL_Mobile_BotnetCnC_Hash_MD5
|
category=KL_Mobile_BotnetCnC_Hash_MD5.*url=(?<url>[^\s]*).*usrName=(?<login>[^\s]*).*Mask=(?<object>[^\s{}]*).*verdict=(?<objectname>[^\s]*)
|
May 2 16:41:40 category=KL_Mobile_BotnetCnC_Hash_MD5 url=- md5=12B8D137C80AE5E995EC355524594F3B sha1=- sha256=- ip=- usrName=VerifTestUserName Behaviour=Get Location, Collect phone info, Read SMS, Get Accounts, Read Contacts Details=[{Mask=*.subdbotnet_domain_19.dbotnet_domain.com}] MD5=12B8D137C80AE5E995EC355524594F3B verdict=Evaluation-CnC.AndroidOS
|
KL_Mobile_BotnetCnC_Hash_SHA1
|
category=KL_Mobile_BotnetCnC_Hash_SHA1.*sha1=(?<object>[^\s]*).*usrName=(?<login>[^\s]*).*verdict=(?<objectname>[^\s]*)
|
May 2 16:41:40 category=KL_Mobile_BotnetCnC_Hash_SHA1 url=- md5=- sha1=AFAEEE65BB483994FAC36A6B97F10B2BAA51F832 sha256=- ip=- usrName=VerifTestUserName Behaviour=Get Location, Collect phone info, Read SMS, Get Accounts, Read Contacts
|
KL_Mobile_BotnetCnC_Hash_SHA256
|
category=KL_Mobile_BotnetCnC_Hash_SHA256.*sha256=(?<object>[^\s]*).*usrName=(?<login>[^\s]*).*verdict=(?<objectname>[^\s]*)
|
May 2 16:41:40 category=KL_Mobile_BotnetCnC_Hash_SHA256 url=- md5=- sha1=- sha256=E804F6ADF2B7C99A8E0B158E880DF3172131CFAD7D796A75CBC2E46606371D2E ip=- usrName=VerifTestUserName Behaviour=Get Location, Collect phone info, Read SMS, Get Accounts, Read Contacts
|
KL_Mobile_BotnetCnC_URL
|
category=KL_Mobile_BotnetCnC_URL.*url=(?<url>[^\s]*).*usrName=(?<login>[^\s]*).*Mask=(?<object>[^\s{}]*).*verdict=(?<objectname>[^\s]*)
|
May 2 16:41:40 category=KL_Mobile_BotnetCnC_URL url=baddomain.subdbotnet_domain_19.dbotnet_domain.com md5=- sha1=- sha256=- ip=- usrName=VerifTestUserName Behaviour=Get Location, Collect phone info, Read SMS, Get Accounts, Read Contacts Details=[{Mask=*.subdbotnet_domain_19.dbotnet_domain.com}] MD5=12B8D137C80AE5E995EC355524594F3B verdict=Evaluation-CnC.AndroidOS
|
KL_Mobile_Malicious_Hash_MD5
|
category=KL_Mobile_Malicious_Hash_MD5.*md5=(?<object>[^\s]*).*usrName=(?<login>[^\s]*).*file_size=(?<size>[^\s]*).*threat=(?<objectname>[^\s]*)
|
May 2 16:41:40 category=KL_Mobile_Malicious_Hash_MD5 url=- md5=A0D02A618E0FB400EDC0E210DD975E21 sha1=- sha256=- ip=- usrName=VerifTestUserName MD5=A0D02A618E0FB400EDC0E210DD975E21 SHA1=AB04F1F9CFE33EADB7ECC75EDF7A79EE1E22AEE6 SHA256=5E658421AE871ED9EA85A352050B7F27525821649EA0A6863B62BA7BDED2C074 file_size=378980 first_seen=10.09.2015 06:47 geo=ru, in, id, ir, my, bd, ua, br, dz, ro last_seen=14.01.2016 13:18 popularity=5 threat=HEUR:Trojan.AndroidOS.Guerrilla.b
|
KL_Mobile_Malicious_Hash_SHA1
|
category=KL_Mobile_Malicious_Hash_SHA1.*sha1=(?<object>[^\s]*).*usrName=(?<login>[^\s]*).*file_size=(?<size>[^\s]*).*threat=(?<objectname>[^\s]*)
|
May 2 16:41:40 category=KL_Mobile_Malicious_Hash_SHA1 url=- md5=- sha1=9DA11F40D00E37D27A7B41EE7C741F4CF0E52AE6 sha256=- ip=- usrName=VerifTestUserName MD5=F9E8AB7B3E0B23203B678772AFD4CDD1 SHA1=9DA11F40D00E37D27A7B41EE7C741F4CF0E52AE6 SHA256=111319613DA28D6D59282EBC2730E0448717CD55B36050B9142167936070F9EE file_size=236096 first_seen=15.12.2015 20:59 geo=ru, ua, in, tr, id, dz, mx, kz, by, ro last_seen=14.01.2016 13:23 popularity=5 threat=HEUR:Trojan.AndroidOS.Ztorg.a
|
KL_Mobile_Malicious_Hash_SHA256
|
category=KL_Mobile_Malicious_Hash_SHA256.*sha256=(?<object>[^\s]*).*usrName=(?<login>[^\s]*).*file_size=(?<size>[^\s]*).*threat=(?<objectname>[^\s]*)
|
May 2 16:41:40 category=KL_Mobile_Malicious_Hash_SHA256 url=- md5=- sha1=- sha256=3F52BBBA93A3C757D781ED4D8D526632995FD2F712788D24C528B2F5DB6E3C42 ip=- usrName=VerifTestUserName MD5=A8315A5D4C8ACB982372C16B83BAEAAA SHA1=ABBB5A760C3203CB460D60279269F5568D89F848 SHA256=3F52BBBA93A3C757D781ED4D8D526632995FD2F712788D24C528B2F5DB6E3C42 file_size=444408 first_seen=01.08.2015 00:08 geo=ru, ua, kz, ro, by, cn, tj, uz, az, md last_seen=14.01.2016 13:18 popularity=5 threat=HEUR:Trojan-SMS.AndroidOS.Podec.a
|
KL_Phishing_URL
|
category=KL_Phishing_URL.*url=(?<url>[^\s]*).*usrName=(?<login>[^\s]*)
|
May 2 16:41:40 category=KL_Phishing_URL url=http://d.subphishing_domain.phishing_domain_19.com md5=- sha1=- sha256=- ip=- usrName=VerifTestUserName IP=104.168.159.146, 138.201.0.229, 138.201.0.231, 138.201.0.230, 78.46.185.21, 78.46.185.23, 78.46.185.12, 78.46.185.3, 78.46.185.16, 78.46.185.28 first_seen=12.01.2016 12:50 geo=br, pt, us id=9508721 last_seen=14.01.2016 13:36 mask=*.subphishing_domain.phishing_domain_19.com popularity=5 type=19
|
KL_psms_Hash_MD5
|
category=KL_psms_Hash_MD5.*md5=(?<object>[^\s]*).*usrName=(?<login>[^\s]*).*AV Verdict=(?<objectname>[^\s]*)
|
May 2 16:41:40 category=KL_psms_Hash_MD5 url=- md5=AA5516BDDAE3F060193A9E6551BC19EB sha1=- sha256=- ip=- usrName=VerifTestUserName AV Verdict=Trojan-SMS.AndroidOS.FakeInst.fy Country=ru Date=5/3/2014 11:15:29 PM MD5=AA5516BDDAE3F060193A9E6551BC19EB SMS Number=8612 SMS text=4098745 8281558 mcc=250
|
KL_Ransomware_URL
|
category=KL_Ransomware_URL.*url=(?<url>[^\s]*).*usrName=(?<login>[^\s]*)
|
May 2 16:41:40 category=KL_Ransomware_URL matchedIndicator=fakess123r.nu url=fakess123r.nu src=192.168.0.0 ip=- md5=- sha1=- sha256=- usrName=VerifTestUserName first_seen=10.08.2016 14:18 id=0 last_seen=22.12.2017 15:12 mask=fakess123r.nu popularity=1 type=1
|
KL_Ransomware_URL_Hash_MD5
|
category=KL_Ransomware_URL_Hash_MD5.*md5=(?<object>[^\s]*).*usrName=(?<login>[^\s]*)
|
May 2 16:41:40 category=KL_Ransomware_URL_Hash_MD5 matchedIndicator=DAFECEDABFE0F3AB372A7C83B84CEFF6 url=- src=- ip=- md5=DAFECEDABFE0F3AB372A7C83B84CEFF6 sha1=- sha256=- usrName=- IP=104.27.174.162, 104.27.175.162, 188.166.67.166, 193.176.84.67, 185.232.23.3, 5.182.27.20, 178.128.153.190, 78.24.218.108, 158.58.172.76, 2.59.214.27 files=[{ MD5=DAFECEDABFE0F3AB372A7C83B84CEFF6 SHA1=0D68EE713180A5BF73F7C74CE00F067D2BE5CF7C SHA256=7DD78D2CBFF85A80954558C5C01986FC5D9099C87ECE796A374626EB76BE037D threat=HEUR:Trojan.Win32.Generic}] first_seen=01.04.2019 18:17 geo=ru, kz, ua, by, de, lt, ro, pl, md, it id=30341045 last_seen=23.05.2019 14:19 mask=sama-berli.info popularity=5 type=1 whois={ NS=dora.ns.cloudflare.com, zod.ns.cloudflare.com NS_ips=173.245.58.108, 173.245.59.250 country=UA created=24.01.2019 domain=sama-berli.info expires=24.01.2020 org=ZAO Sigva registrar_email=abuse@reg.ru registrar_name=Limited Liability Company "Registrar of domain names REG.RU" updated=29.03.2019}
|
KL_Ransomware_URL_Hash_SHA1
|
category=KL_Ransomware_URL_Hash_SHA1.*matchedIndicator=(?<object>[^\s]*).*usrName=(?<login>[^\s]*)
|
May 2 16:41:40 category=KL_Ransomware_URL_Hash_SHA1 matchedIndicator=0D68EE713180A5BF73F7C74CE00F067D2BE5CF7C url=- src=- ip=- md5=- sha1=0D68EE713180A5BF73F7C74CE00F067D2BE5CF7C sha256=- usrName=- IP=104.27.174.162, 104.27.175.162, 188.166.67.166, 193.176.84.67, 185.232.23.3, 5.182.27.20, 178.128.153.190, 78.24.218.108, 158.58.172.76, 2.59.214.27 files=[{ MD5=DAFECEDABFE0F3AB372A7C83B84CEFF6 SHA1=0D68EE713180A5BF73F7C74CE00F067D2BE5CF7C SHA256=7DD78D2CBFF85A80954558C5C01986FC5D9099C87ECE796A374626EB76BE037D threat=HEUR:Trojan.Win32.Generic}] first_seen=01.04.2019 18:17 geo=ru, kz, ua, by, de, lt, ro, pl, md, it id=30341045 last_seen=23.05.2019 14:19 mask=sama-berli.info popularity=5 type=1 whois={ NS=dora.ns.cloudflare.com, zod.ns.cloudflare.com NS_ips=173.245.58.108, 173.245.59.250 country=UA created=24.01.2019 domain=sama-berli.info expires=24.01.2020 org=ZAO Sigva registrar_email=abuse@reg.ru registrar_name=Limited Liability Company "Registrar of domain names REG.RU" updated=29.03.2019}
|
KL_Ransomware_URL_Hash_SHA256
|
category=KL_Ransomware_URL_Hash_SHA256.*matchedIndicator=(?<object>[^\s]*).*usrName=(?<login>[^\s]*)
|
May 2 16:41:40 category=KL_Ransomware_URL_Hash_SHA256 matchedIndicator=7DD78D2CBFF85A80954558C5C01986FC5D9099C87ECE796A374626EB76BE037D url=- src=- ip=- md5=- sha1=- sha256=7DD78D2CBFF85A80954558C5C01986FC5D9099C87ECE796A374626EB76BE037D usrName=- IP=104.27.174.162, 104.27.175.162, 188.166.67.166, 193.176.84.67, 185.232.23.3, 5.182.27.20, 178.128.153.190, 78.24.218.108, 158.58.172.76, 2.59.214.27 files=[{ MD5=DAFECEDABFE0F3AB372A7C83B84CEFF6 SHA1=0D68EE713180A5BF73F7C74CE00F067D2BE5CF7C SHA256=7DD78D2CBFF85A80954558C5C01986FC5D9099C87ECE796A374626EB76BE037D threat=HEUR:Trojan.Win32.Generic}] first_seen=01.04.2019 18:17 geo=ru, kz, ua, by, de, lt, ro, pl, md, it id=30341045 last_seen=23.05.2019 14:19 mask=sama-berli.info popularity=5 type=1 whois={ NS=dora.ns.cloudflare.com, zod.ns.cloudflare.com NS_ips=173.245.58.108, 173.245.59.250 country=UA created=24.01.2019 domain=sama-berli.info expires=24.01.2020 org=ZAO Sigva registrar_email=abuse@reg.ru registrar_name=Limited Liability Company "Registrar of domain names REG.RU" updated=29.03.2019}
|
KL_Exploit_Hash_MD5
|
category=KL_Exploit_Hash_MD5.*md5=(?<object>[^\s]*).*usrName=(?<login>[^\s]*)
|
May 2 16:41:40 category=KL_Exploit_Hash_MD5 matchedIndicator=DAFECEDABFE0F3AB372A7C83B84CEFF6 url=- src=- ip=- md5=DAFECEDABFE0F3AB372A7C83B84CEFF6 sha1=- sha256=- usrName=- IP=104.27.174.162, 104.27.175.162, 188.166.67.166, 193.176.84.67, 185.232.23.3, 5.182.27.20, 178.128.153.190, 78.24.218.108, 158.58.172.76, 2.59.214.27 files=[{ MD5=DAFECEDABFE0F3AB372A7C83B84CEFF6 SHA1=0D68EE713180A5BF73F7C74CE00F067D2BE5CF7C SHA256=7DD78D2CBFF85A80954558C5C01986FC5D9099C87ECE796A374626EB76BE037D threat=HEUR:Trojan.Win32.Generic}] first_seen=01.04.2019 18:17 geo=ru, kz, ua, by, de, lt, ro, pl, md, it id=30341045 last_seen=23.05.2019 14:19 mask=sama-berli.info popularity=5 type=1 whois={ NS=dora.ns.cloudflare.com, zod.ns.cloudflare.com NS_ips=173.245.58.108, 173.245.59.250 country=UA created=24.01.2019 domain=sama-berli.info expires=24.01.2020 org=ZAO Sigva registrar_email=abuse@reg.ru registrar_name=Limited Liability Company "Registrar of domain names REG.RU" updated=29.03.2019}
|
KL_Exploit_Hash_SHA1
|
category=KL_Exploit_Hash_SHA1.*sha1=(?<object>[^\s]*).*usrName=(?<login>[^\s]*)
|
May 2 16:41:40 category=KL_Exploit_Hash_SHA1 matchedIndicator=0D68EE713180A5BF73F7C74CE00F067D2BE5CF7C url=- src=- ip=- md5=- sha1=0D68EE713180A5BF73F7C74CE00F067D2BE5CF7C sha256=- usrName=- IP=104.27.174.162, 104.27.175.162, 188.166.67.166, 193.176.84.67, 185.232.23.3, 5.182.27.20, 178.128.153.190, 78.24.218.108, 158.58.172.76, 2.59.214.27 files=[{ MD5=DAFECEDABFE0F3AB372A7C83B84CEFF6 SHA1=0D68EE713180A5BF73F7C74CE00F067D2BE5CF7C SHA256=7DD78D2CBFF85A80954558C5C01986FC5D9099C87ECE796A374626EB76BE037D threat=HEUR:Trojan.Win32.Generic}] first_seen=01.04.2019 18:17 geo=ru, kz, ua, by, de, lt, ro, pl, md, it id=30341045 last_seen=23.05.2019 14:19 mask=sama-berli.info popularity=5 type=1 whois={ NS=dora.ns.cloudflare.com, zod.ns.cloudflare.com NS_ips=173.245.58.108, 173.245.59.250 country=UA created=24.01.2019 domain=sama-berli.info expires=24.01.2020 org=ZAO Sigva registrar_email=abuse@reg.ru registrar_name=Limited Liability Company "Registrar of domain names REG.RU" updated=29.03.2019}
|
KL_Exploit_Hash_SHA256
|
category=KL_Exploit_Hash_SHA256.*sha256=(?<object>[^\s]*).*usrName=(?<login>[^\s]*)
|
May 2 16:41:40 category=KL_Exploit_Hash_SHA256 matchedIndicator=7DD78D2CBFF85A80954558C5C01986FC5D9099C87ECE796A374626EB76BE037D url=- src=- ip=- md5=- sha1=- sha256=7DD78D2CBFF85A80954558C5C01986FC5D9099C87ECE796A374626EB76BE037D usrName=- IP=104.27.174.162, 104.27.175.162, 188.166.67.166, 193.176.84.67, 185.232.23.3, 5.182.27.20, 178.128.153.190, 78.24.218.108, 158.58.172.76, 2.59.214.27 files=[{ MD5=DAFECEDABFE0F3AB372A7C83B84CEFF6 SHA1=0D68EE713180A5BF73F7C74CE00F067D2BE5CF7C SHA256=7DD78D2CBFF85A80954558C5C01986FC5D9099C87ECE796A374626EB76BE037D threat=HEUR:Trojan.Win32.Generic}] first_seen=01.04.2019 18:17 geo=ru, kz, ua, by, de, lt, ro, pl, md, it id=30341045 last_seen=23.05.2019 14:19 mask=sama-berli.info popularity=5 type=1 whois={ NS=dora.ns.cloudflare.com, zod.ns.cloudflare.com NS_ips=173.245.58.108, 173.245.59.250 country=UA created=24.01.2019 domain=sama-berli.info expires=24.01.2020 org=ZAO Sigva registrar_email=abuse@reg.ru registrar_name=Limited Liability Company "Registrar of domain names REG.RU" updated=29.03.2019}
|
KL_IoT_Hash_MD5
|
category=KL_IoT_Hash_MD5.*md5=(?<object>[^\s]*).*usrName=(?<login>[^\s]*)
|
May 2 16:41:40 category=KL_IoT_Hash_MD5 matchedIndicator=DAFECEDABFE0F3AB372A7C83B84CEFF6 url=- src=- ip=- md5=DAFECEDABFE0F3AB372A7C83B84CEFF6 sha1=- sha256=- usrName=- IP=104.27.174.162, 104.27.175.162, 188.166.67.166, 193.176.84.67, 185.232.23.3, 5.182.27.20, 178.128.153.190, 78.24.218.108, 158.58.172.76, 2.59.214.27 files=[{ MD5=DAFECEDABFE0F3AB372A7C83B84CEFF6 SHA1=0D68EE713180A5BF73F7C74CE00F067D2BE5CF7C SHA256=7DD78D2CBFF85A80954558C5C01986FC5D9099C87ECE796A374626EB76BE037D threat=HEUR:Trojan.Win32.Generic}] first_seen=01.04.2019 18:17 geo=ru, kz, ua, by, de, lt, ro, pl, md, it id=30341045 last_seen=23.05.2019 14:19 mask=sama-berli.info popularity=5 type=1 whois={ NS=dora.ns.cloudflare.com, zod.ns.cloudflare.com NS_ips=173.245.58.108, 173.245.59.250 country=UA created=24.01.2019 domain=sama-berli.info expires=24.01.2020 org=ZAO Sigva registrar_email=abuse@reg.ru registrar_name=Limited Liability Company "Registrar of domain names REG.RU" updated=29.03.2019}
|
KL_IoT_Hash_SHA1
|
category=KL_IoT_Hash_SHA1.*sha1=(?<object>[^\s]*).*usrName=(?<login>[^\s]*)
|
May 2 16:41:40 category=KL_IoT_Hash_MD5 matchedIndicator=0D68EE713180A5BF73F7C74CE00F067D2BE5CF7C url=- src=- ip=- md5=- sha1=0D68EE713180A5BF73F7C74CE00F067D2BE5CF7C sha256=- usrName=- IP=104.27.174.162, 104.27.175.162, 188.166.67.166, 193.176.84.67, 185.232.23.3, 5.182.27.20, 178.128.153.190, 78.24.218.108, 158.58.172.76, 2.59.214.27 files=[{ MD5=DAFECEDABFE0F3AB372A7C83B84CEFF6 SHA1=0D68EE713180A5BF73F7C74CE00F067D2BE5CF7C SHA256=7DD78D2CBFF85A80954558C5C01986FC5D9099C87ECE796A374626EB76BE037D threat=HEUR:Trojan.Win32.Generic}] first_seen=01.04.2019 18:17 geo=ru, kz, ua, by, de, lt, ro, pl, md, it id=30341045 last_seen=23.05.2019 14:19 mask=sama-berli.info popularity=5 type=1 whois={ NS=dora.ns.cloudflare.com, zod.ns.cloudflare.com NS_ips=173.245.58.108, 173.245.59.250 country=UA created=24.01.2019 domain=sama-berli.info expires=24.01.2020 org=ZAO Sigva registrar_email=abuse@reg.ru registrar_name=Limited Liability Company "Registrar of domain names REG.RU" updated=29.03.2019}
|
KL_IoT_Hash_SHA256
|
category=KL_IoT_Hash_SHA256.*sha256=(?<object>[^\s]*).*usrName=(?<login>[^\s]*)
|
May 2 16:41:40 category=KL_IoT_Hash_SHA256 matchedIndicator=7DD78D2CBFF85A80954558C5C01986FC5D9099C87ECE796A374626EB76BE037D url=- src=- ip=- md5=- sha1=- sha256=7DD78D2CBFF85A80954558C5C01986FC5D9099C87ECE796A374626EB76BE037D usrName=- IP=104.27.174.162, 104.27.175.162, 188.166.67.166, 193.176.84.67, 185.232.23.3, 5.182.27.20, 178.128.153.190, 78.24.218.108, 158.58.172.76, 2.59.214.27 files=[{ MD5=DAFECEDABFE0F3AB372A7C83B84CEFF6 SHA1=0D68EE713180A5BF73F7C74CE00F067D2BE5CF7C SHA256=7DD78D2CBFF85A80954558C5C01986FC5D9099C87ECE796A374626EB76BE037D threat=HEUR:Trojan.Win32.Generic}] first_seen=01.04.2019 18:17 geo=ru, kz, ua, by, de, lt, ro, pl, md, it id=30341045 last_seen=23.05.2019 14:19 mask=sama-berli.info popularity=5 type=1 whois={ NS=dora.ns.cloudflare.com, zod.ns.cloudflare.com NS_ips=173.245.58.108, 173.245.59.250 country=UA created=24.01.2019 domain=sama-berli.info expires=24.01.2020 org=ZAO Sigva registrar_email=abuse@reg.ru registrar_name=Limited Liability Company "Registrar of domain names REG.RU" updated=29.03.2019}
|
KL_IoT_URL
|
category=KL_IoT_URL.*url=(?<url>[^\s]*).*usrName=(?<login>[^\s]*)
|
May 2 16:41:40 category=KL_IoT_URL matchedIndicator=fakess123r.nu url=fakess123r.nu src=192.168.0.0 ip=- md5=- sha1=- sha256=- usrName=VerifTestUserName first_seen=10.08.2016 14:18 id=0 last_seen=22.12.2017 15:12 mask=fakess123r.nu popularity=1 type=1
|
KL_Vulnerable_File_Hash_MD5
|
category=KL_Vulnerable_File_Hash_MD5.*md5=(?<object>[^\s]*).*usrName=(?<login>[^\s]*)
|
May 2 16:41:40 category=KL_Vulnerable_File_Hash_MD5 matchedIndicator=DAFECEDABFE0F3AB372A7C83B84CEFF6 url=- src=- ip=- md5=DAFECEDABFE0F3AB372A7C83B84CEFF6 sha1=- sha256=- usrName=- IP=104.27.174.162, 104.27.175.162, 188.166.67.166, 193.176.84.67, 185.232.23.3, 5.182.27.20, 178.128.153.190, 78.24.218.108, 158.58.172.76, 2.59.214.27 files=[{ MD5=DAFECEDABFE0F3AB372A7C83B84CEFF6 SHA1=0D68EE713180A5BF73F7C74CE00F067D2BE5CF7C SHA256=7DD78D2CBFF85A80954558C5C01986FC5D9099C87ECE796A374626EB76BE037D threat=HEUR:Trojan.Win32.Generic}] first_seen=01.04.2019 18:17 geo=ru, kz, ua, by, de, lt, ro, pl, md, it id=30341045 last_seen=23.05.2019 14:19 mask=sama-berli.info popularity=5 type=1 whois={ NS=dora.ns.cloudflare.com, zod.ns.cloudflare.com NS_ips=173.245.58.108, 173.245.59.250 country=UA created=24.01.2019 domain=sama-berli.info expires=24.01.2020 org=ZAO Sigva registrar_email=abuse@reg.ru registrar_name=Limited Liability Company "Registrar of domain names REG.RU" updated=29.03.2019}
|
KL_Vulnerable_File_Hash_SHA1
|
category=KL_Vulnerable_File_Hash_SHA1.*sha1=(?<object>[^\s]*).*usrName=(?<login>[^\s]*)
|
May 2 16:41:40 category=KL_Vulnerable_File_Hash_SHA1 matchedIndicator=0D68EE713180A5BF73F7C74CE00F067D2BE5CF7C url=- src=- ip=- md5=- sha1=0D68EE713180A5BF73F7C74CE00F067D2BE5CF7C sha256=- usrName=- IP=104.27.174.162, 104.27.175.162, 188.166.67.166, 193.176.84.67, 185.232.23.3, 5.182.27.20, 178.128.153.190, 78.24.218.108, 158.58.172.76, 2.59.214.27 files=[{ MD5=DAFECEDABFE0F3AB372A7C83B84CEFF6 SHA1=0D68EE713180A5BF73F7C74CE00F067D2BE5CF7C SHA256=7DD78D2CBFF85A80954558C5C01986FC5D9099C87ECE796A374626EB76BE037D threat=HEUR:Trojan.Win32.Generic}] first_seen=01.04.2019 18:17 geo=ru, kz, ua, by, de, lt, ro, pl, md, it id=30341045 last_seen=23.05.2019 14:19 mask=sama-berli.info popularity=5 type=1 whois={ NS=dora.ns.cloudflare.com, zod.ns.cloudflare.com NS_ips=173.245.58.108, 173.245.59.250 country=UA created=24.01.2019 domain=sama-berli.info expires=24.01.2020 org=ZAO Sigva registrar_email=abuse@reg.ru registrar_name=Limited Liability Company "Registrar of domain names REG.RU" updated=29.03.2019}
|
KL_Vulnerable_File_Hash_SHA256
|
category=KL_Vulnerable_File_Hash_SHA256.*sha256=(?<object>[^\s]*).*usrName=(?<login>[^\s]*)
|
May 2 16:41:40 category= KL_Vulnerable_File_Hash_SHA256 matchedIndicator=7DD78D2CBFF85A80954558C5C01986FC5D9099C87ECE796A374626EB76BE037D url=- src=- ip=- md5=- sha1=- sha256=7DD78D2CBFF85A80954558C5C01986FC5D9099C87ECE796A374626EB76BE037D usrName=- IP=104.27.174.162, 104.27.175.162, 188.166.67.166, 193.176.84.67, 185.232.23.3, 5.182.27.20, 178.128.153.190, 78.24.218.108, 158.58.172.76, 2.59.214.27 files=[{ MD5=DAFECEDABFE0F3AB372A7C83B84CEFF6 SHA1=0D68EE713180A5BF73F7C74CE00F067D2BE5CF7C SHA256=7DD78D2CBFF85A80954558C5C01986FC5D9099C87ECE796A374626EB76BE037D threat=HEUR:Trojan.Win32.Generic}] first_seen=01.04.2019 18:17 geo=ru, kz, ua, by, de, lt, ro, pl, md, it id=30341045 last_seen=23.05.2019 14:19 mask=sama-berli.info popularity=5 type=1 whois={ NS=dora.ns.cloudflare.com, zod.ns.cloudflare.com NS_ips=173.245.58.108, 173.245.59.250 country=UA created=24.01.2019 domain=sama-berli.info expires=24.01.2020 org=ZAO Sigva registrar_email=abuse@reg.ru registrar_name=Limited Liability Company "Registrar of domain names REG.RU" updated=29.03.2019}
|
 ).
).