Creating notifications about incoming service events
You can create notifications about incoming Kaspersky CyberTrace service events by configuring alert rules.
To create notifications about service events from Kaspersky CyberTrace in RSA NetWitness:
- On the RSA NetWitness menu, select the Monitor > Reports and then select Manage > Rules.
Manage > Rules form
- In the Groups section, select CyberTrace_Rules.
CyberTrace rules
- In the Rules section, click the Add split button (
 ). In the drop-down list, select NetWitness Platform DB.
). In the drop-down list, select NetWitness Platform DB.The Build Rule window opens.
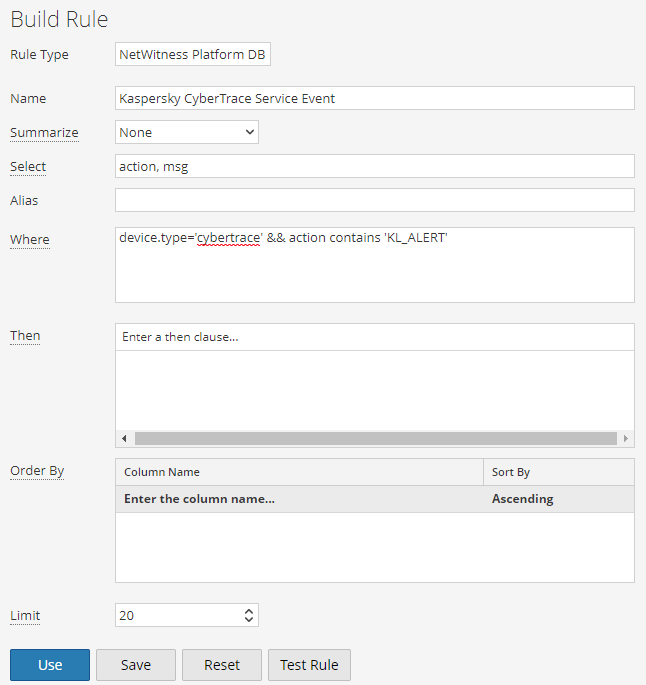
- In the Build Rule window, specify the following settings:
- In the Name field, specify the name of the rule.
You can specify any name.
- In the Summarize field, specify the value different from
None, if you want to agregate events. - In the Select field, specify the fields that contain values are used in notifications.
In service events, Kaspersky CyberTrace uses the msg and action fields.
- In the Where field, specify the notification conditions. For example:
device.type='cybertrace' && action contains 'KL_ALERT'This condition contains all Kaspersky CyberTrace service events.
- If necessary, fill in the rest fields as you choose.
The Build Rule window
- In the Name field, specify the name of the rule.
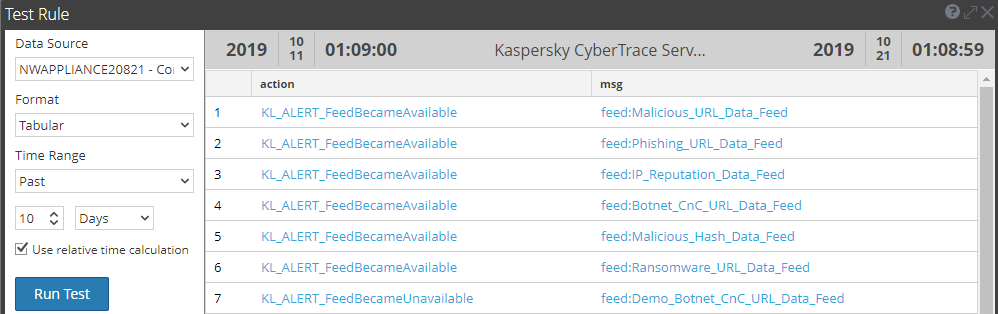
- Click the Test Rule button to make sure that checking the specified rules is performed correctly.
The Test Rule window
- Click Save to save the rule.
- Click Use, and in the window that opens select Alert and then Select.
The Use Rule window
The Create/Modify Alert window opens.
- In the Create/Modify Alert window, specify the following settings:
- In the Data Source field, select an event source with Kaspersky CyberTrace events.
- In the Description field, specify the alert description.
You can specify any description.
- In the Severity field, specify the severity of the alert.
- In the Notification field, specify the following settings:
- The way that RSA NetWitness will send notify you about alerts.
- The body of the alert.
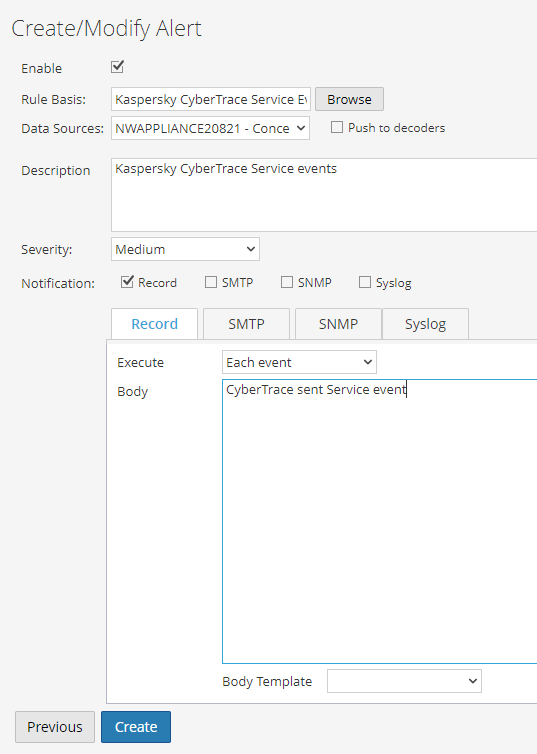
The Create/Modify Alert window
- Click Create to save the rule.
The rule will now be added to the Alert list of the Manage > Alerts tab.
- To browse all alerts that comply with the created rule, click the View Alerts button (
 ).
).