Step 3 (optional). Adding Kaspersky CyberTrace events
This section describes how you can add Kaspersky CyberTrace events to LogRhythm manually.
Skip this step, if the importing of Kaspersky CyberTrace rules and events succeeds.
To add Kaspersky CyberTrace events to LogRhythm:
- Run LogRhythm Console.
- Select Deployment Manager > Tools > Knowledge > Common Event Manager.
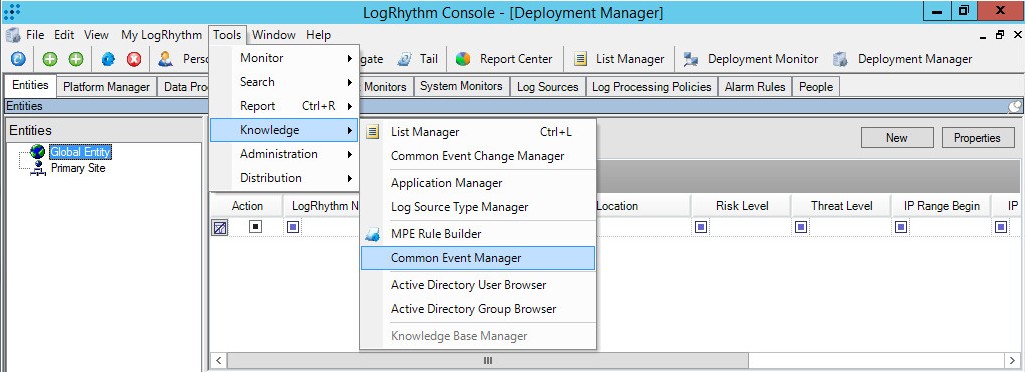
Common Event Manager menu item
The Common Event Manager window opens.
- Add the events provided in the tables below. If you do not use all commercial and OSINT feeds, some of the events might not be necessary.
- Events of the
"Security : Compromise"classification
Event
Description
KL_APT_Hash_MD5
Hash of a malicious file used in an APT campaign is detected by Kaspersky CyberTrace.
KL_APT_Hash_SHA1
Hash of a malicious file used in an APT campaign is detected by Kaspersky CyberTrace.
KL_APT_Hash_SHA256
Hash of a malicious file used in an APT campaign is detected by Kaspersky CyberTrace.
KL_APT_IP
IP address used in an APT campaign is detected by Kaspersky CyberTrace.
KL_APT_URL
URL used in an APT campaign is detected by Kaspersky CyberTrace.
KL_BotnetCnC_Hash_MD5
Botnet hash is detected by Kaspersky CyberTrace.
KL_BotnetCnC_Hash_SHA1
Botnet hash is detected by Kaspersky CyberTrace.
KL_BotnetCnC_Hash_SHA256
Botnet hash is detected by Kaspersky CyberTrace.
KL_BotnetCnC_URL
Botnet C&C URL is detected by Kaspersky CyberTrace.
KL_Exploit_Hash_MD5
Hash of exploit is detected by Kaspersky CyberTrace.
KL_Exploit_Hash_SHA1
Hash of exploit is detected by Kaspersky CyberTrace.
KL_Exploit_Hash_SHA256
Hash of exploit is detected by Kaspersky CyberTrace.
KL_ICS_Hash_MD5
ICS hash is detected by Kaspersky CyberTrace.
KL_ICS_Hash_SHA1
ICS hash is detected by Kaspersky CyberTrace.
KL_ICS_Hash_SHA256
ICS hash is detected by Kaspersky CyberTrace.
KL_InternalTI_URL
URL of the InternalTI list of Kaspersky CyberTrace.
KL_InternalTI_IP
IP of the InternalTI list of Kaspersky CyberTrace.
KL_InternalTI_Hash_MD5
Hash of the InternalTI list of Kaspersky CyberTrace.
KL_InternalTI_Hash_SHA1
Hash of the InternalTI list of Kaspersky CyberTrace.
KL_InternalTI_Hash_SHA256
Hash of the InternalTI list of Kaspersky CyberTrace.
KL_IoT_Hash_MD5
Hash of IoT is detected by Kaspersky CyberTrace.
KL_IoT_Hash_SHA1
Hash of IoT is detected by Kaspersky CyberTrace.
KL_IoT_Hash_SHA256
Hash of IoT is detected by Kaspersky CyberTrace.
KL_IoT_URL
URL that infects Internet of Things-enabled (IoT) devices is detected by Kaspersky CyberTrace.
KL_IP_Reputation
Malicious or suspicious IP address is detected by Kaspersky CyberTrace.
KL_IP_Reputation_Hash_MD5
Hash of a file hosted on a malicious or suspicious IP address is detected by Kaspersky CyberTrace.
KL_IP_Reputation_Hash_SHA1
Hash of a file hosted on a malicious or suspicious IP address is detected by Kaspersky CyberTrace.
KL_IP_Reputation_Hash_SHA256
Hash of a file hosted on a malicious or suspicious IP address is detected by Kaspersky CyberTrace.
KL_Malicious_URL
Malicious URL is detected by Kaspersky CyberTrace.
KL_Malicious_URL_Hash_MD5
Hash of a file hosted on a malicious URL is detected by Kaspersky CyberTrace.
KL_Malicious_URL_Hash_SHA1
Hash of a file hosted on a malicious URL is detected by Kaspersky CyberTrace.
KL_Malicious_URL_Hash_SHA256
Hash of a file hosted on a malicious URL is detected by Kaspersky CyberTrace.
KL_Malicious_Hash_MD5
Malicious hash is detected by Kaspersky CyberTrace.
KL_Malicious_Hash_SHA1
Malicious hash is detected by Kaspersky CyberTrace.
KL_Malicious_Hash_SHA256
Malicious hash is detected by Kaspersky CyberTrace.
KL_Mobile_Malicious_Hash_MD5
Mobile malicious hash is detected by Kaspersky CyberTrace.
KL_Mobile_Malicious_Hash_SHA1
Mobile malicious hash is detected by Kaspersky CyberTrace.
KL_Mobile_Malicious_Hash_SHA256
Mobile malicious hash is detected by Kaspersky CyberTrace.
KL_Mobile_BotnetCnC_Hash_MD5
Mobile botnet C&C hash is detected by Kaspersky CyberTrace.
KL_Mobile_BotnetCnC_Hash_SHA1
Mobile botnet C&C hash is detected by Kaspersky CyberTrace.
KL_Mobile_BotnetCnC_Hash_SHA256
Mobile botnet C&C hash is detected by Kaspersky CyberTrace.
KL_Mobile_BotnetCnC_URL
Mobile botnet C&C URL is detected by Kaspersky CyberTrace.
KL_Phishing_URL
Phishing URL is detected by Kaspersky CyberTrace.
KL_Ransomware_URL
URL that hosts ransomware is detected by Kaspersky CyberTrace.
KL_Ransomware_URL_Hash_MD5
Hash of ransomware is detected by Kaspersky CyberTrace.
KL_Ransomware_URL_Hash_SHA1
Hash of ransomware is detected by Kaspersky CyberTrace.
KL_Ransomware_URL_Hash_SHA256
Hash of ransomware is detected by Kaspersky CyberTrace.
KL_Vulnerable_File_Hash_MD5
Hash of vulnerable software and related exploits is detected by Kaspersky CyberTrace.
KL_Vulnerable_File_Hash_SHA1
Hash of vulnerable software and related exploits is detected by Kaspersky CyberTrace.
KL_Vulnerable_File_Hash_SHA256
Hash of vulnerable software and related exploits is detected by Kaspersky CyberTrace.
AbuseCh_Feodo_Block_IP
IP address from the Abuse.Ch_Feodo_Block_IP feed is detected by Kaspersky CyberTrace.
AbuseCh_Ransomware_Block_URL
URL from the Abuse.Ch_Ransomware_Block_URL feed is detected by Kaspersky CyberTrace.
AbuseCh_Ransomware_Block_Domain
Domain from the Abuse.Ch_Ransomware_Block_Domain feed is detected by Kaspersky CyberTrace.
AbuseCh_Ransomware_Block_IP
IP address from the Abuse.Ch_Ransomware_Block_IP feed is detected by Kaspersky CyberTrace.
AbuseCh_Ransomware_Common_URL
URL from the Abuse.Ch_Ransomware_Common_URL feed is detected by Kaspersky CyberTrace.
AbuseCh_SSL_Certificate_Block_IP
IP address from the AbuseCh_SSL_Certificate_Block_IP feed is detected by Kaspersky CyberTrace.
AbuseCh_SSL_Certificate_Hash_SHA1
Hash from the AbuseCh_SSL_Certificate_Hash_SHA1 feed is detected by Kaspersky CyberTrace.
BlocklistDe_Block_IP
IP from the BlocklistDe_Block_IP feed is detected by Kaspersky CyberTrace.
CyberCrime_Tracker_Block_Url
URL from the CyberCrime_Tracker_Block_Url feed is detected by Kaspersky CyberTrace.
EmergingThreats_Block_IP
IP address from the EmergingThreats_Block_IP feed is detected by Kaspersky CyberTrace.
EmergingThreats_Compromised_IP
IP address from the EmergingThreats_Compromised_IP feed is detected by Kaspersky CyberTrace.
- Alert events:
Event
Description
Classification
KL_ALERT_ConfigurationUpdated
This event is generated if Feed Service has reloaded the configuration file.
Audit : Configuration
KL_ALERT_FeedBecameAvailable
This event is generated if a feed that can be used with the current certificate has become available.
Audit : Other Audit Success
KL_ALERT_FeedBecameUnavailable
This event is generated if a feed that is being used with the current certificate has become unavailable.
Audit : Other Audit Failure
KL_ALERT_OutdatedFeed
This event is generated if a feed has not been updated during the specified period.
Audit : Other Audit Failure
KL_ALERT_ServiceUnavailable
This event is generated when the watchdog module has detected that Feed Service has crashed or frozen.
Audit : Other Audit Failure
KL_ALERT_ServiceStopped
This event is generated when Feed Service is stopped successfully.
Audit : Startup and Shutdown
KL_ALERT_ServiceStarted
This event is generated when Feed Service is started successfully.
Audit : Startup and Shutdown
KL_ALERT_UpdatedFeed
This event is generated when a feed is updated and loaded by Feed Service.
Audit : Other Audit Success
KL_ALERT_FailedToUpdateFeed
This event is generated when Feed Service fails to load a new feed (for example, due to the limitation on the number of indicators that is imposed by the license key) and continues using an old feed.
Audit : Other Audit Failure
KL_ALERT_LicenseExpires
This event is generated to inform you that the license key that is being used will expire in less than 30 days.
Audit : Policy
KL_ALERT_LicenseExpired
This event is generated when your license key has expired.
Audit : Policy
KL_ALERT_EPSLimitExceeded
This event is generated when the limit on the number of processed events per second (EPS) imposed by the licensed key or licensing level has been exceeded.
Audit : Policy
KL_ALERT_EPSHardLimit
This event is generated when Feed Service limits the number of events processed per second (EPS) to the maximum number of events for the current license key or licensing level. The limit applies regardless of the number of incoming events.
Audit : Policy
KL_ALERT_LicenseChanged
This event is generated when Kaspersky CyberTrace starts to use another license key or licensing level.
Audit : Configuration
KL_ALERT_RetroScanError
This event is generated when the retrospective scan task failed.
Audit : Other Audit Failure
KL_ALERT_RetroScanCompleted
This event is generated when the retrospective scan task succeeded.
Audit : Other Audit Success
KL_ALERT_RetroScanStorageExceeded
This event is generated when the limit on the size of the saved events has been exceeded.
Audit : Policy
KL_ALERT_IndicatorsStoreLimitExceeded
This event is generated when the limit on the size of the saved indicators has been exceeded.
Audit : Policy
KL_ALERT_IndicatorsStoreHardLimit
This event is generated when Kaspersky CyberTrace limits adding and updating of indicators.
Audit : Policy
KL_ALERT_FreeSpaceEnds
This event is generated when the available disk space becomes low.
Audit : Policy
Alert events may contain context fields, as described in the section about the alert events of Kaspersky CyberTrace.
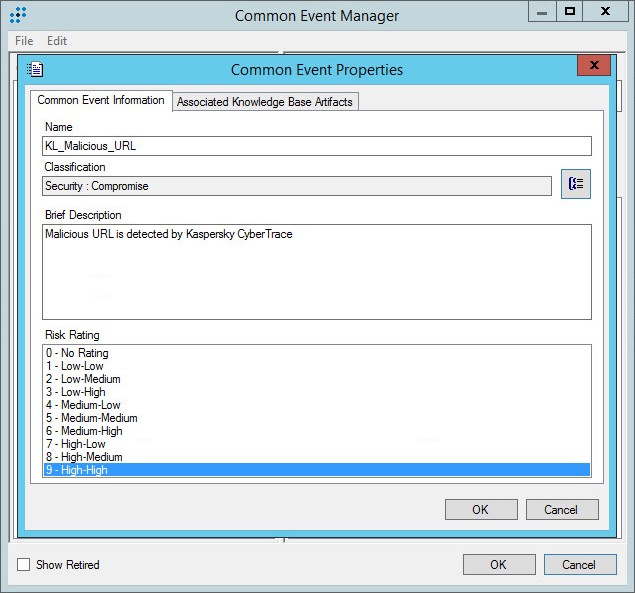
Common Event Properties window
- Events of the
After the events are added, the Common Event Manager window must contain the events as shown in the figure below.
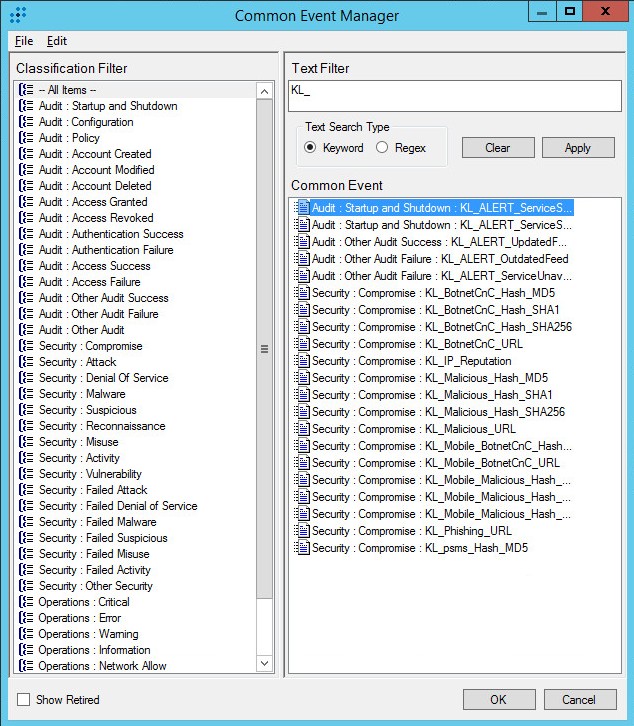
Added events
Page top