Step 5. Retrieving custom event properties
This section describes how to configure retrieval of custom event properties from Kaspersky CyberTrace outgoing events, in addition to standard fields. As a result of this setting, the MD5, SHA1, and SHA256 hashes will be extracted and the extraction rule of the Source IP field will be redefined.
To configure retrieval of custom event properties:
- Select the Log Activity tab, and then click Add Filter.
The Add Filter form opens.
- Fill in the form:
- In the Parameter drop-down list, select
Log Source [Indexed]. - In the Operator drop-down list, select
Equals. - In the Log Source list, select
KL_Threat_Feed_Service_v2.The selection
KL_Threat_Feed_Service_v2is the log source name that is set in theOutputSettings > EventFormatelement and theOutputSettings > AlertFormatelement of the Kaspersky CyberTrace Service configuration file (you can also set them by using Kaspersky CyberTrace Web).
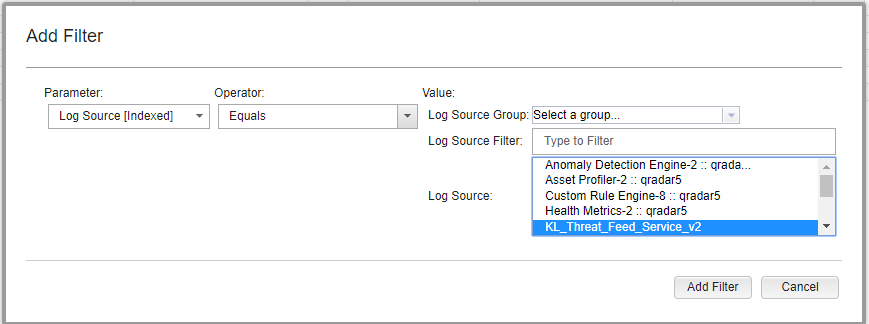
Adding a filter
- In the Parameter drop-down list, select
- Click Add Filter.
- Run the verification test, and then stop the events flow by clicking Pause (
 ) in the upper-right area of the window.
) in the upper-right area of the window. - Press Ctrl (or Shift) to select several records, and then select Actions → DSM editor.
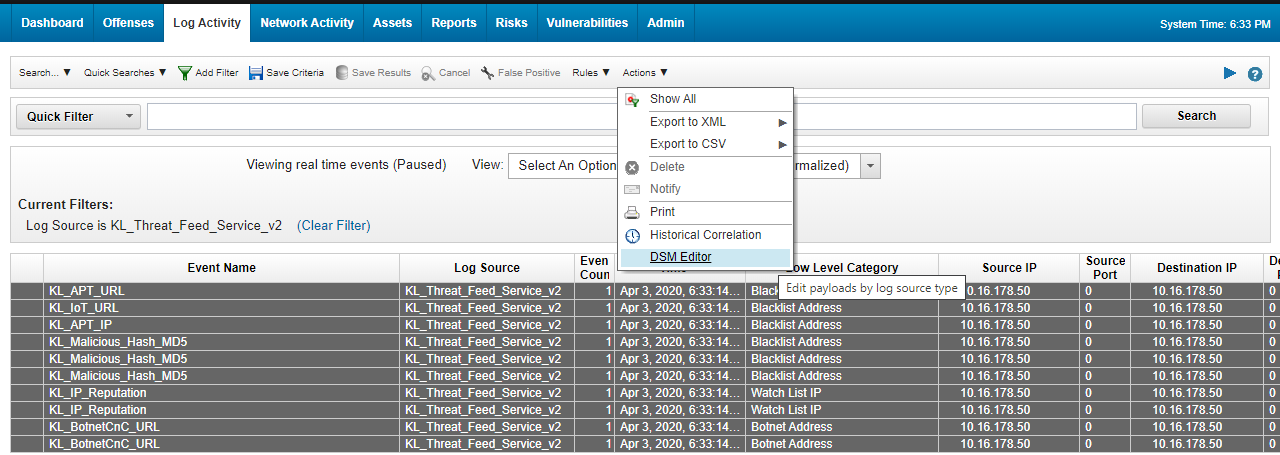
The Log Activity window
The DSM Editor window opens.
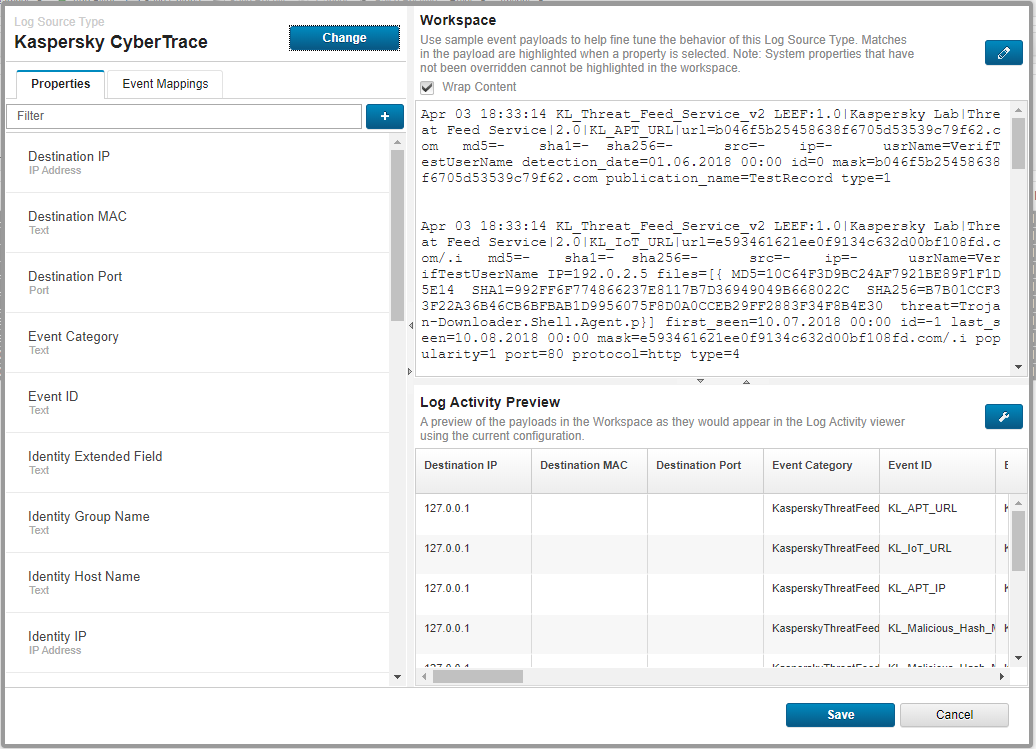
The DSM Editor window
- In the DSM Editor window, click the + button near the Filters text box.
The Choose a Custom Property Definition to Express form opens.
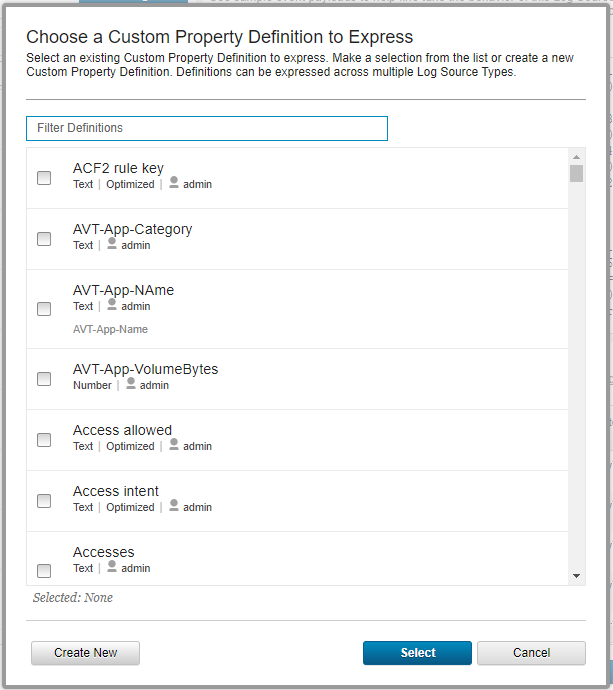
Choosing a custom property
- Click Create new.
The Create a new Custom Property Definition form opens.
- Fill in the form:
- In the Name field, enter
MD5. - In the Field Type drop-down list, select
Text. - In the Description field, enter a description of the property.
- Select the Enable this Property for Use in Rules and Search Indexing check box.
- Click Save.
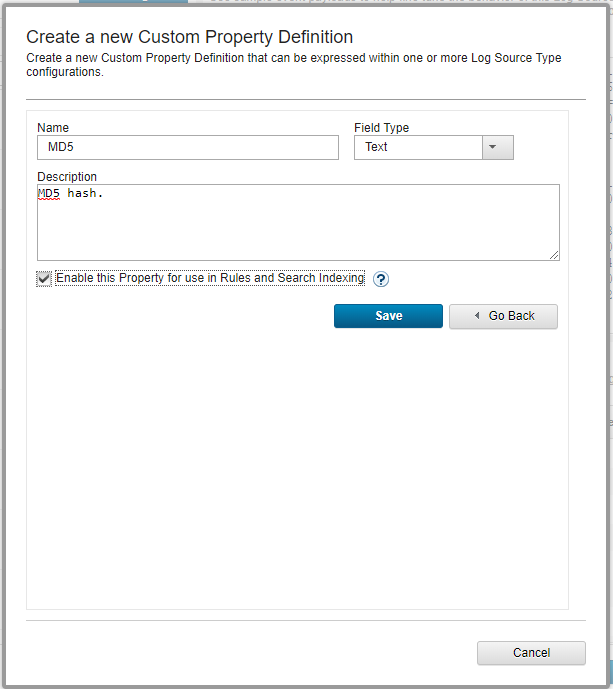
Creating a new custom property definition
- In the Name field, enter
- Add the
SHA1andSHA256properties similarly. - In the Choose a Custom Property Definition to Express window, select the created properties, add URL and Source IP, and then click Select.
- In the Log Activity Preview section, click Configure and then select the following properties:
Event NameIP (custom)MD5 (custom)SHA1 (custom)SHA256 (custom)Source IPURL (custom)Username
Click Update.
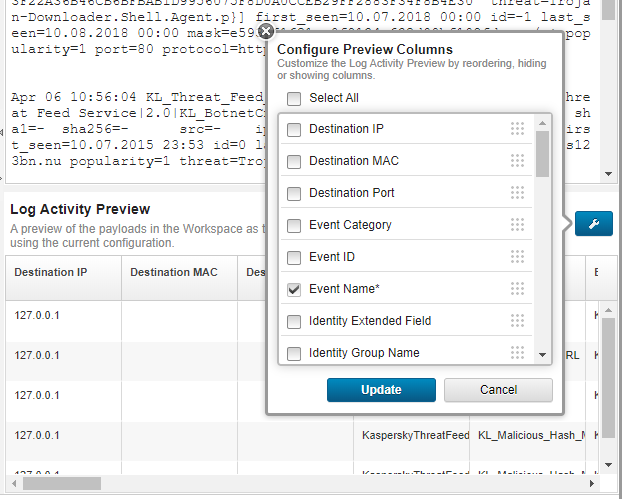
Configuring preview columns
- On the Properties tab, configure regular expressions as described in the table below:
Custom property
Regular expression
MD5
md5=([\da-fA-F]{32})SHA1
sha1=([\da-fA-F]{40})SHA256
sha256=([\da-fA-F]{64})URL
url=([-a-zA-Z0-9()@:%_\+.~#?&\/\/=]{2,})Source IP
src=(\d{1,3}\.\d{1,3}\.\d{1,3}\.\d{1,3})If necessary, type
1in the Capture Group field. - For the Source IP property, select the Override system behavior check box.
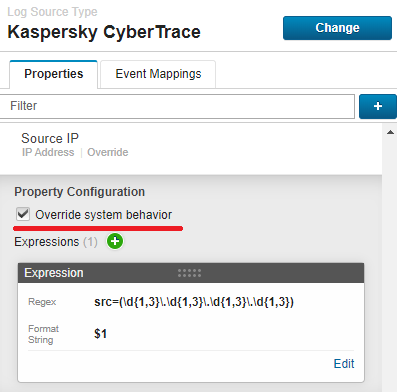
Source IP configuration
When changing the format for outgoing detection events in Kaspersky CyberTrace, the regular expressions that are specified above may require corresponding changes.
If all of the settings above are specified correctly, you will find the configured Custom properties in the Log Activity Preview section.
- Click Save and close the window.
- On the Log Activity tab, perform the new verification test.
After that, if you open the event received from
KL_Threat_Feed_Service_v2, the configured custom properties will be displayed.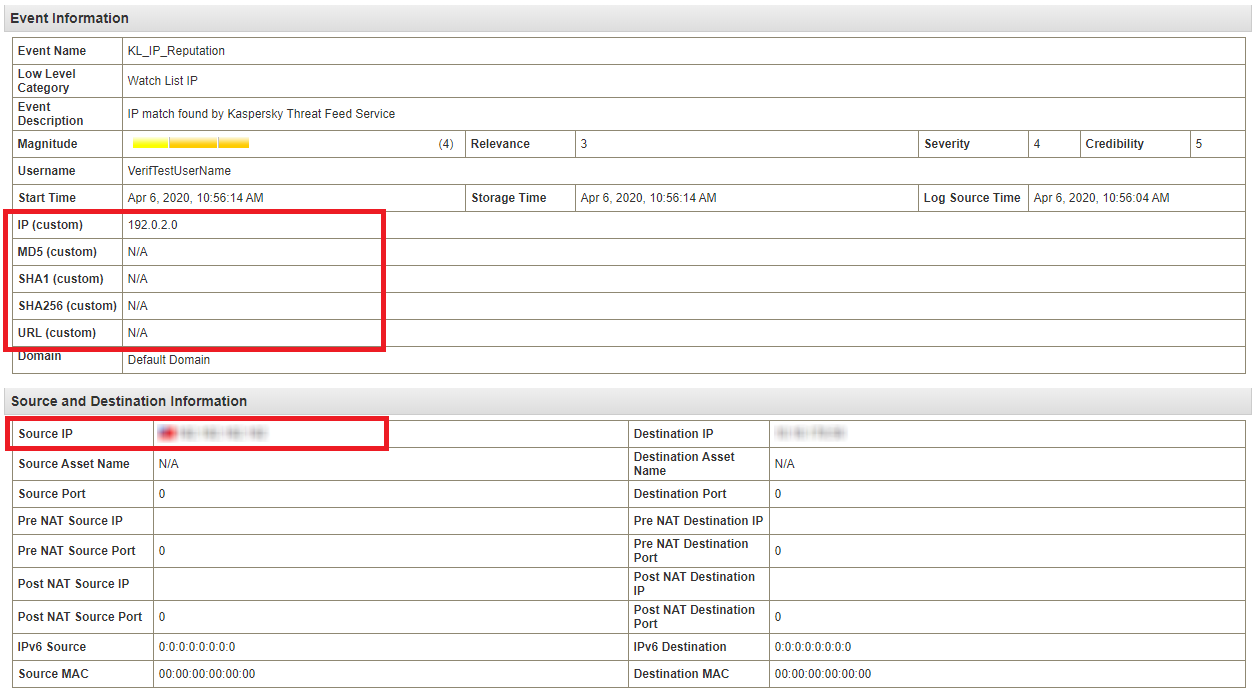
Event information