Step 3. Configuring Kaspersky CyberTrace for interaction with ArcSight
This section describes how to configure Kaspersky CyberTrace for interaction with ArcSight during normal work.
To configure Kaspersky CyberTrace for interaction with ArcSight:
- Open Kaspersky CyberTrace Web.
- Go to the Settings → General page.
- In the Incoming events section, select the IP address and port that Kaspersky CyberTrace Service listens on for incoming events. The IP address and port are set when ArcSight Forwarding Connector is installed (its default value is
127.0.0.1:9999). - Go to the Settings → Event sources page.
- Click the
(Edit) button next to the Default event source.
The Edit event source "{{sourceId}}" window opens.
- On the Normalization rules tab:
- In the To replace field, enter the character sequence
\= - In the Replace with field, enter the character
=
After you make the changes, the Normalization rules tab must look like the following:
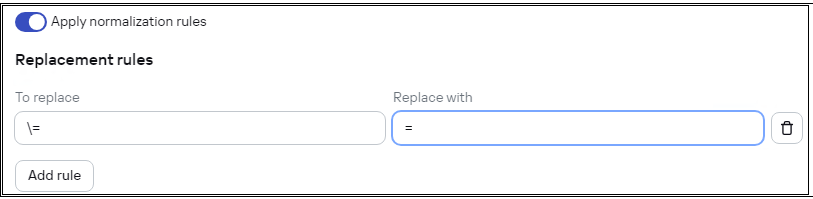
Normalization rules tab
- In the To replace field, enter the character sequence
- Select the Regular expressions tab. This tab contains universal regular expressions that match URLs (with protocol), hashes, IP addresses (src and dst), device name, vendor name, device IP address, user name, and event ID. Change these regular expressions to match the events.
- Close the Edit event source "{{sourceId}}" window.
- On the Settings → Service alerts page, in the Format of service alerts field, enter the following string:
CEF:0|Kaspersky|Kaspersky CyberTrace for ArcSight|2.0|1|CyberTrace Service Event|4| reason=%Alert% msg=%RecordContext% - On the Settings → Detection alerts page, in the Alert format field, specify the following string:
CEF:0|Kaspersky|Kaspersky CyberTrace for ArcSight|2.0|2|CyberTrace Detection Event|8| reason=%Category% dst=%DST_IP% src=%DeviceIp% fileHash=%RE_HASH% request=%RE_URL% sourceServiceName=%Device% sproc=%Product% suser=%UserName% msg=CyberTrace detected %Category% externalId=%Id% %ActionableFields% cs5Label=MatchedIndicator cs5=%MatchedIndicator% cn3Label=Confidence cn3=%Confidence% cs6Label=Context cs6=%RecordContext%
ArcSight and actionable fields
The following actionable fields are used in Kaspersky Data Feeds. You can review the actionable fields on the Settings → Feeds page.
- For Demo Botnet C&C URL Data Feed and Botnet C&C URL Data Feed:
Field name
Output
CEF field
mask
cs1
deviceCustomString1
first_seen
flexString1
flexString1
last_seen
flexString2
flexString2
popularity
cn2
deviceCustomNumber2
threat
cs3
deviceCustomString3
urls/url
cs4
deviceCustomString4
whois/domain
cs2
deviceCustomString2
- For Demo Malicious Hash Data Feed and Malicious Hash Data Feed:
Field name
Output
CEF field
first_seen
flexString1
flexString1
last_seen
flexString2
flexString2
popularity
cn2
deviceCustomNumber2
threat
cs3
deviceCustomString3
urls/url
cs4
deviceCustomString4
file_size
fsize
file_size
- For Demo IP Reputation Feed and IP Reputation Data Feed:
Field name
Output
CEF field
first_seen
flexString1
flexString1
last_seen
flexString2
flexString2
popularity
cn2
deviceCustomNumber2
threat_score
cn1
deviceCustomNumber1
domains
cs2
deviceCustomString2
urls/url
cs4
deviceCustomString4
files/threat
cs3
deviceCustomString3
- For Malicious URL Data Feed:
Field name
Output
CEF field
mask
cs1
deviceCustomString1
first_seen
flexString1
flexString1
last_seen
flexString2
flexString2
popularity
cn2
deviceCustomNumber2
files/threat
cs3
deviceCustomString3
category
cs4
deviceCustomString4
whois/domain
cs2
deviceCustomString2
- For Mobile Malicious Hash Data Feed:
Field name
Output
CEF field
first_seen
flexString1
flexString1
last_seen
flexString2
flexString2
popularity
cn2
deviceCustomNumber2
threat
cs3
deviceCustomString3
file_size
fsize
file_size
- For Phishing URL Data Feed:
Field name
Output
CEF field
mask
cs1
deviceCustomString1
first_seen
flexString1
flexString1
last_seen
flexString2
flexString2
popularity
cn2
deviceCustomNumber2
industry
deviceFacility
deviceFacility
whois/domain
cs2
deviceCustomString2
- For Mobile Botnet Data Feed:
Field name
Output
CEF field
threat
cs3
deviceCustomString3
- For APT URL Data Feed:
Field name
Output
CEF field
detection_date
flexString1
flexString1
publication_name
cs3
deviceCustomString3
- For APT IP Data Feed:
Field name
Output
CEF field
detection_date
flexString1
flexString1
publication_name
cs3
deviceCustomString3
- For APT Hash Data Feed:
Field name
Output
CEF field
detection_date
flexString1
flexString1
publication_name
cs3
deviceCustomString3
- For IoT URL Data Feed:
Field name
Output
CEF field
mask
cs1
deviceCustomString1
first_seen
flexString1
flexString1
last_seen
flexString2
flexString2
popularity
cn2
deviceCustomNumber2
files/threat
cs3
deviceCustomString3
Clearing ArcSight fields occupied by information from Kaspersky Data Feeds
If you want to use a CEF field for data other than information from Kaspersky Data Feeds, you must clear this field.
To clear a CEF field:
- Select the Settings tab of Kaspersky CyberTrace Web.
- Go to the Feeds page.
- Make sure the Kaspersky tab is selected, and then click the Kaspersky Threat Data Feed that contains the field that you want to clear.
- In the Actionable fields section, find the Output field name containing the name of the CEF field that you want to clear.
- Click the delete icon (
 ) next to the Output field name that you found in the previous step.
) next to the Output field name that you found in the previous step.