Configuring filtering rules for detection alerts
The Filtration tab of the Settings → Detection alerts page allows you to specify the filtering rules for detection alerts sent to a SIEM system from Kaspersky CyberTrace.
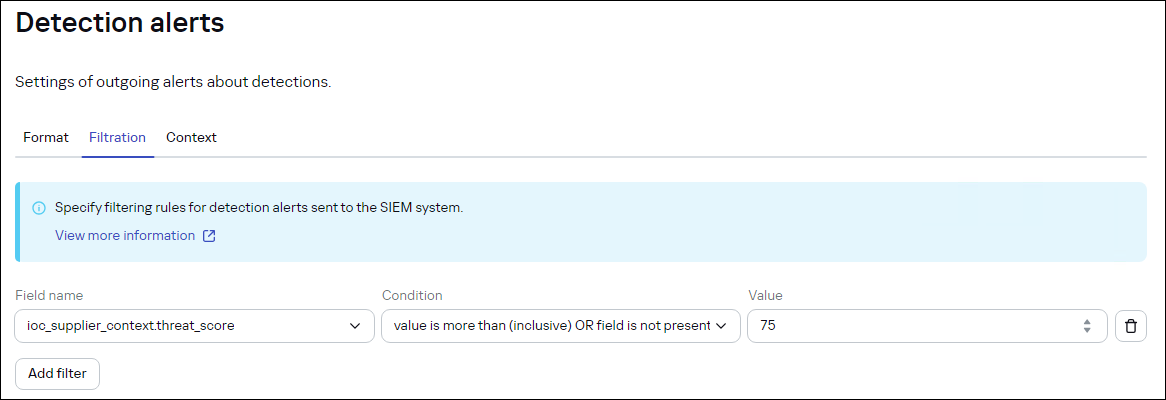
The Filtration tab of the Settings → Detection alerts page
Kaspersky CyberTrace will send detection alerts only if the flag for sending detection alerts to the SIEM system (the ioc_supplier_send_match event attribute from the indicator database) is set to true and all fields of a feed record that matched the indicator meet the filtering criteria. Note that if the detected indicator does not have the attribute specified in the filtering rule, this indicator is considered to meet the filter. However, all detection alerts will be included in statistics and displayed on the Dashboard and Detections pages.
To specify filters for detection alerts:
- In the Field name drop-down list, select the value that corresponds to the indicator attribute name from the indicator database to which filtering rules are applied. In the Condition drop-down list, select a filtering condition.
- In the Value text box, specify a filtering value.
To separate values in this text box, do not use a semicolon ('
;'). Instead, select value is one of (separated by a new line) OR field is not present in the Condition drop-down list, and either use a newline character ('\n') or press Enter. Otherwise, the filter will not be applied correctly. - Click the Add filter button if you want to add another alert filter.
If necessary, you can edit or delete any filtering rules.
Page top