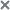Creating and configuring a file operations monitoring rule
To create and configure a file operations monitoring rule using the Application Console:
- In the Application Console tree, expand the System Inspection node.
- Select the File Integrity Monitor child node.
- Click the File Integrity Monitor link in the results pane of the File operations monitoring rules node.
The File operations monitoring rules window appears.
- Specify the path for the file operations monitoring scope in one of the following ways:
- If you want to select a folder or drive through the standard Microsoft Windows dialog:
- On the left side of the window, click the Browse button.
The standard Microsoft Windows Browse for folder window appears.
- Select the folder whose file operations you want to monitor.
- Click the OK button.
- On the left side of the window, click the Browse button.
- If you want to specify a monitoring scope manually, add a path using a supported mask:
- <*.ext> — all files with the extension <ext>, regardless of their location
- <*\name.ext> — all files with name <name> and extension <ext>, regardless of their location
- <\dir\*> — all files in folder <\dir>
- <\dir\*\name.ext> — all files with the name <name> and extension <ext> in folder <\dir> and all of its child folders
When specifying a monitoring scope manually, be sure that the path is in the following format: <volume letter>:\<mask>. If the volume letter is missing, Kaspersky Embedded Systems Security for Windows will not add the specified monitoring scope.
- If you want to select a folder or drive through the standard Microsoft Windows dialog:
- Click the Add button.
The monitoring scope will be displayed in the list on the left of the File operations monitoring rules window.
- If necessary, specify trusted users:
- On the Trusted users tab, click the Add button.
The standard Microsoft Windows Select users or groups window opens.
- Select users or user groups that will be allowed to perform operations on files in the selected monitoring scope.
- Click the OK button.
By default, Kaspersky Embedded Systems Security for Windows treats all users not on the trusted user list as untrusted, and generates Critical events for them. For trusted users, statistics are compiled.
- On the Trusted users tab, click the Add button.
- On the Set file operations markers tab, if necessary, specify the file operation markers that you want to monitor:
- Select the Detect file operations based on the following markers option.
- In the list of available file operations select the check boxes next to the operations you want to monitor.
By default, Kaspersky Embedded Systems Security for Windows detects all file operation markers. The Detect file operations based on all recognizable markers option is selected.
- If you want the application to block all file operations for the selected monitoring scope, select the Detect and block all file operations in the selected area check box.
- If you want the application to calculate the checksum of a file after it has been modified:
- Under Checksum calculation, select Calculate checksum for a file final version, after the file was changed, if possible. The checksum will be available for viewing in the task log.
- In the Calculate the checksum using the algorithm drop down list select one of the options:
- MD5 hash
- SHA256 hash.
- If necessary, add folders or drives to exclude file operations from monitoring:
- On the Set exclusions tab, select the Consider excluded monitoring scope check box.
- Click the Browse button.
The standard Microsoft Windows Browse for folder window appears.
- Select a folder or drive.
- Click the OK button.
- Click the Add button.
The specified folder or drive will be displayed in the list of exclusions.
You can also add file operations monitoring scope exclusions manually using the same masks that are used to specify file operations monitoring scopes.
- Click the Save button.