Configuring security settings manually
By default Real-Time Computer Protection tasks use common security settings for the entire protection scope. These settings correspond to the Recommended predefined security level.
The default values of security settings can be modified by configuring them as common settings for the entire protection scope or as different settings for individual items in the device's file resource list or nodes in the tree.
When working with the protected device's file resource tree, security settings that are configured for the selected parent node are automatically applied to all child nodes. The security settings of the parent node are not applied to child nodes that are configured separately.
How to configure security settings manually in the Kaspersky Security Center Administration Console
- In the Kaspersky Security Center Administration Console tree, select the Policies folder.
- Select the necessary policy and double-click to open the policy properties.
- In the policy properties window, select Real-Time Computer Protection.
- In the Real-Time File Protection section, click Settings.
- In the Real-Time File Protection window, go to the Protection scope tab.
- Select the resource whose security settings you want to configure.
- Click Configure.
- In the window that opens, select the required security level and click Settings.
- On the General tab, specify the following settings:
- Objects that should be included in the protection scope:
- In the Optimization block, select or clear the Scan only new and modified files check box.
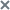
This check box enables / disables scanning and protection of files that have been recognized by Kaspersky Embedded Systems Security as new or modified since the last scan.
If the check box is selected, Kaspersky Embedded Systems Security scans and protects only the files that it has recognized as new or modified since the last scan.
If the check box is cleared, Kaspersky Embedded Systems Security scans and protects files regardless of their modification status.
- In the Scan of compound files section, specify the compound objects that you want to include in the scan scope:
- Scan archives
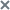
Scanning ZIP, GZIP, BZIP, RAR, TAR, ARJ, CAB, LHA, JAR, ICE, and other archives. The application scans archives not only by extension, but also by format. When checking archives, the application performs a recursive unpacking. This allows to detect threats inside multi-level archives (archive within an archive).
- Scan distribution packages
- Scan files in Microsoft Office formats
- Scan email format files
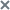
The check box enables or disables running scan tasks after the protected device switches to a UPS source.
If the check box is selected, Kaspersky Embedded Systems Security pauses running scan tasks after the protected device switches to a UPS source.
If the check box is cleared, Kaspersky Embedded Systems Security continues running scan tasks after the protected device switches to a UPS source.
By default, the check box is cleared.
- Scan archives
- On the Actions tab, specify the following settings:
- Select the action to be performed on infected and other detected objects:
- Inform
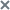
When this mode is selected, Kaspersky Embedded Systems Security does not block access to nor perform any actions on infected or other detected objects. The following event is recorded in the task log: Object not disinfected. Reason: no action was taken to neutralize detected object due to user-defined settings. The event specifies all available information about the detected object.
Inform mode should be separately configured for each protection or scan area. This mode is not used by default in any of the security levels. If you select this mode, Kaspersky Embedded Systems Security automatically changes the security level to Inform.
- Block
- Perform additional action
Select the action from the drop-down list:
- Disinfect
- Disinfect. Delete if disinfection fails
- Delete
- Recommended
- Inform
- Configure actions to be performed on objects depending on the type of object detected:
- Clear or select the Apply the action to the selected object types check box.
If the check box is selected, you can independently set primary and secondary actions for each type of detected objects by clicking the button next to the check box. However, Kaspersky Embedded Systems Security will not allow to open or execute an infected object regardless of your choice.
If the check box is cleared, Kaspersky Embedded Systems Security performs actions that are selected in the Action to perform on infected and other objects block.
By default, the check box is cleared.
- Click Settings and select the types of objects to be detected.
- Clear or select the Apply the action to the selected object types check box.
- Configure actions on compound files that are not available for modification: clear or select the Entirely remove the compound file that cannot be modified by the application in case of embedded object detection check box.
This check box enables or disables forced removal of the parent compound file when a malicious, probably infected or other detectable embedded child object is detected.
If the check box is selected and the task is configured to remove infected and probably infected objects, Kaspersky Embedded Systems Security forcibly removes the entire parent compound object when a malicious or other embedded object is detected. The parent file along with all of its contents are forcibly removed if the application cannot remove only the detected child object (for example, if the parent object cannot be modified).
If this check box is cleared and the task is configured to remove infected and probably infected objects, Kaspersky Embedded Systems Security does not perform the selected action if the parent object cannot be modified.
- Select the action to be performed on infected and other detected objects:
- On the Performance tab, specify the following settings:
- Unpack in the background compound files larger than (MB)
If the check box is selected, the application provides access to compound files that are larger than the specified value before these files are scanned. In this case, Kaspersky Embedded Systems Security unpacks and scans compound files in the background.
The application provides access to compound files that are smaller than this value only after unpacking and scanning these files.
If the check box is not selected, the application provides access to compound files only after unpacking and scanning files of any size.
- Stop scanning if it takes longer than (sec)
- Do not scan compound objects larger than (MB)
Excludes objects larger than the specified size from scanning.
If the check box is selected, Kaspersky Embedded Systems Security skips compound objects whose size exceeds the specified limit during a virus scan.
If this check box is cleared, Kaspersky Embedded Systems Security scans compound objects of any size.
- Use iSwift technology
iSwift compares a file’s NTFS identifier stored in a database with its current identifier. Scanning is performed only for files whose identifiers have changed (new files and files modified since the last scan of NTFS system objects).
If the check box is selected, Kaspersky Embedded Systems Security scans only new files or those modified since the last scan of NTFS system objects.
If the check box is cleared, Kaspersky Embedded Systems Security scans NTFS file system objects regardless of the file creation date or file modification date, except for files from network folders.
The check box is selected by default.
- Use iChecker technology
iChecker calculates and remembers checksums of scanned files. If an object is modified, the checksum changes. The application compares all checksums and scans only files that are new and have been modified since the last scan.
If the check box is selected, Kaspersky Embedded Systems Security scans only new and modified files.
If the check box is cleared, Kaspersky Embedded Systems Security scans files regardless of the file creation date or file modification date.
The check box is selected by default.
- Unpack in the background compound files larger than (MB)
- Save the new security settings.
How to configure security settings manually in the Kaspersky Security Center Web Console
- In the main window of the Web Console, select Assets (Devices) → Policies & profiles.
- Click the name of the Kaspersky Embedded Systems Security policy.
The policy properties window opens.
- Select the Application settings tab.
- Go to Real-Time Computer Protection → Real-Time File Protection and click the Configure button.
- Select the Protection scope tab.
- Do one of the following:
- Click the Add button to add a new rule and specify security settings for it.
- Select an existing rule and click Edit button.
The Edit scope window opens.
- Set the toggle switch to Active.
- Select a security level and specify security settings as necessary.
- In the Objects protection mode section, select the type of the object that you want to include in the protection scope:
- In the Optimization section, select or clear the Protect only new and modified files check box.
- In the Compound objects protection section, specify the compound objects that you want to include in the scan scope:
- Select the action to be performed on infected and other detected objects:
- Inform
- Block
- Perform additional action
Select the action from the drop-down list:
- Disinfect
- Disinfect, delete if disinfection fails
- Delete
- Recommended
- Configure actions to be performed on objects depending on the type of object detected:
- Clear or select the Apply the action to the selected object types check box.
- If the check box is selected, click Settings and select the types of objects to be detected.
- Configure actions on compound files that are not available for modification: clear or select the Entirely remove the compound file that cannot be modified by the application in case of embedded object detection check box.
- In the Optimization section, configure the following settings:
- Save the new security settings.
How to configure security settings manually in the Application Console
- In the Kaspersky Embedded Systems Security Console tree, select Real-Time Computer Protection → Real-Time File Protection.
- In the results pane of the Real-Time File Protection node, click Configure protection scope.
The Properties: Real-Time File Protection window opens.
- Select the resource whose security settings you want to configure.
- Click Configure.
- In the window that opens, select the required security level and click Settings.
- On the General tab, specify the following settings:
- Objects that should be included in the protection scope:
- All objects. Kaspersky Embedded Systems Security scans all objects.
- Objects scanned by format. Kaspersky Embedded Systems Security scans only infectable objects based on file format. Kaspersky compiles the list of formats. It is included in the Kaspersky Embedded Systems Security databases.
- Objects scanned by the list of extensions specified in anti-virus databases. Kaspersky Embedded Systems Security scans only infectable objects based on file extension. Kaspersky compiles the list of extensions. It is included in the Kaspersky Embedded Systems Security databases.
- In the Optimization block, select or clear the Protect only new and modified files check box.
- In the Scan of compound files section, specify the compound objects that you want to include in the scan scope:
- Scan archives. Scanning ZIP, GZIP, BZIP, RAR, TAR, ARJ, CAB, LHA, JAR, ICE, and other archives. The application scans archives not only by extension, but also by format. When checking archives, the application performs a recursive unpacking. This allows to detect threats inside multi-level archives (archive within an archive).
- Scan distribution packages. This check box enables/disables scanning of third-party distribution packages.
- Scan files in Microsoft Office formats. Scans Microsoft Office files (DOC, DOCX, XLS, PPT and other Microsoft extensions). Office format files include OLE objects as well. Kaspersky Embedded Systems Security scans office format files that are smaller than 1 MB, regardless of whether the check box is selected or not.
- Scan email format files.
- Objects that should be included in the protection scope:
- On the Actions tab, specify the following settings:
- Select the action to be performed on infected and other detected objects:
- Inform.
- Block.
- Perform additional action.
Select the action from the drop-down list:
- Disinfect
- Disinfect. Delete if disinfection fails
- Delete.
- Recommended.
- Configure actions to be performed on objects depending on the type of object detected:
- Clear or select the Apply the action to the selected object types check box.
- Click Settings and select the types of objects to be detected.
- Configure actions on compound files that are not available for modification: clear or select the Entirely remove the compound file that cannot be modified by the application in case of embedded object detection check box.
- Select the action to be performed on infected and other detected objects:
- On the Performance tab, specify the following settings:
- Save the new security settings.