Enabling encrypted connections scan
To enable the scanning of encrypted connections:
- In the main application window, click the
 button.
button. - In the application settings window, select General settings → Network settings.
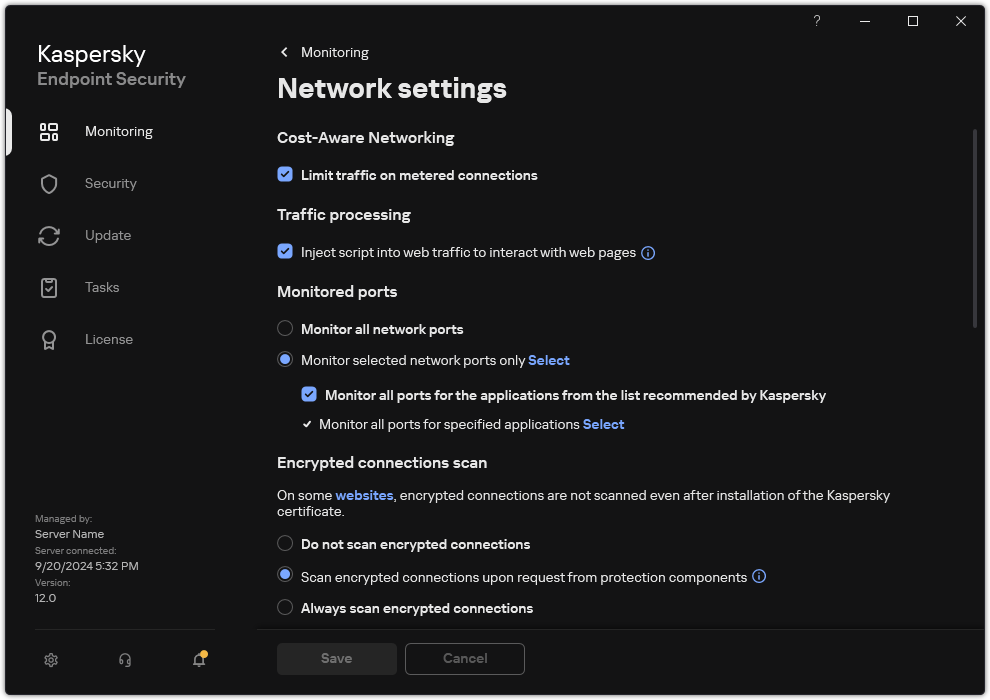
Encrypted connections scan settings
- In the Encrypted connections scan block, select the encrypted connection scanning mode:
- Do not scan encrypted connections. Kaspersky Endpoint Security will not have access to the contents of websites whose addresses begin with
https://. - Scan encrypted connections upon request from protection components. Kaspersky Endpoint Security will scan encrypted traffic only when requested by the Web Threat Protection, Mail Threat Protection, and Web Control components.
- Always scan encrypted connections. Kaspersky Endpoint Security will scan encrypted network traffic even if protection components are disabled.
Kaspersky Endpoint Security does not scan encrypted connections that were established by trusted applications for which traffic scanning is disabled. Kaspersky Endpoint Security does not scan encrypted connections from the predefined list of trusted websites. The predefined list of trusted websites is created by Kaspersky experts. This list is updated with the application's anti-virus databases. You can view the predefined list of trusted websites only in the Kaspersky Endpoint Security interface. You cannot view the list in the Kaspersky Security Center Console.
- Do not scan encrypted connections. Kaspersky Endpoint Security will not have access to the contents of websites whose addresses begin with
- If necessary, add scan exclusions: trusted addresses and applications.
- Configure the settings for scanning encrypted connections (see the table below).
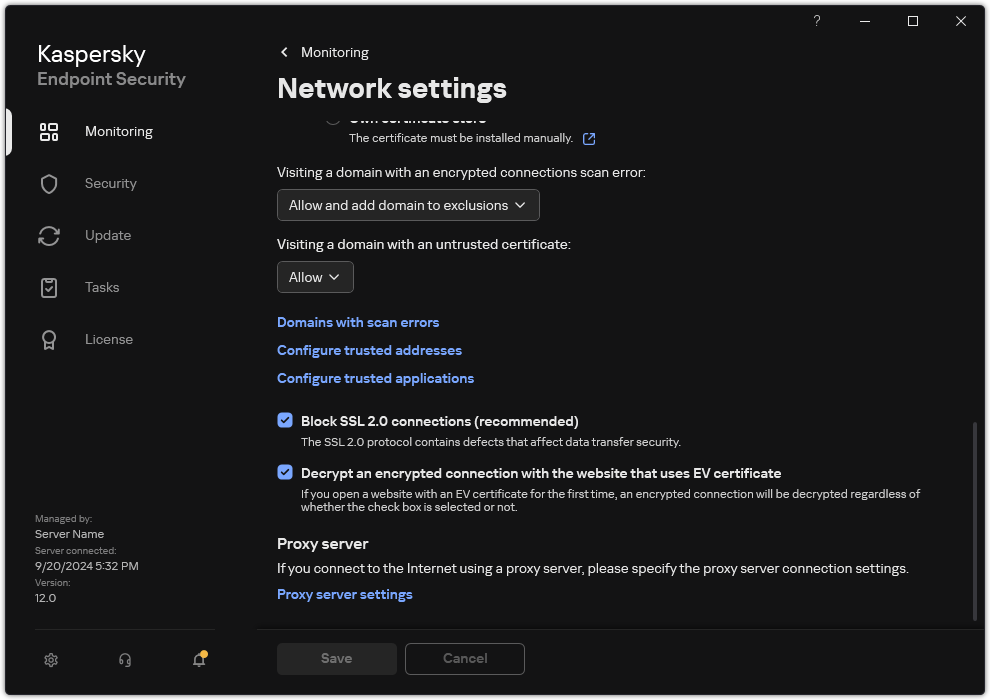
Additional settings for scanning encrypted connections
- Save your changes.
Encrypted connections scan settings
Parameter
Description
Trusted root certificates
List of trusted root certificates. Kaspersky Endpoint Security lets you install trusted root certificates on user computers if, for example, you need to deploy a new certification center. The application lets you add a certificate to a special Kaspersky Endpoint Security certificate store. In this case, the certificate is considered trusted only for the Kaspersky Endpoint Security application. In other words, the user can gain access to a website with the new certificate in the browser. If another application tries to gain access to the website, you can get a connection error because of a certificate issue. To add to the system certificate store, you can use Active Directory group policies.
Visiting a domain with an untrusted certificate
- Allow. When visiting a domain with an untrusted certificate, Kaspersky Endpoint Security allows the network connection.
When opening a domain with an untrusted certificate in a browser, Kaspersky Endpoint Security displays an HTML page showing a warning and the reason why visiting that domain is not recommended. A user can click the link from the HTML warning page to obtain access to the requested web resource.
If a third-party application or service establishes a connection with a domain with an untrusted certificate, Kaspersky Endpoint Security creates its own certificate to scan traffic. The new certificate has the Untrusted status. This is necessary to warn the third-party application about the untrusted connection because the HTML page cannot be shown in this case and the connection can be established in background mode.
- Block. When visiting a domain with an untrusted certificate, Kaspersky Endpoint Security blocks the network connection. When opening a domain with an untrusted certificate in a browser, Kaspersky Endpoint Security displays an HTML page showing the reason why that domain is blocked.
Visiting a domain with an encrypted connections scan error
- Block. If this item is selected, when an encrypted connection scan error occurs, Kaspersky Endpoint Security blocks the network connection.
- Allow and add domain to exclusions. If this item is selected, when an encrypted connection scan error occurs, Kaspersky Endpoint Security adds the domain that resulted in the error to the list of domains with scan errors and does not monitor encrypted network traffic when this domain is visited. You can view a list of domains with encrypted connections scan errors only in the local interface of the application. To clear the list contents, you need to select Block. Kaspersky Endpoint Security also generates an event for the encrypted connection scan error.
Block SSL 2.0 connections (recommended)
If the check box is selected, the application blocks network connections established over the SSL 2.0 protocol.
If the check box is cleared, the application does not block network connections established over the SSL 2.0 protocol and does not monitor network traffic transmitted over these connections.
Decrypt an encrypted connection with the website that uses EV certificate
EV certificates (Extended Validation Certificate) confirm the authenticity of websites and enhance the security of the connection. Browsers use a lock icon in their address bar to indicate that a website has an EV certificate. Browsers may also fully or partially color the address bar in green.
If the check box is selected, the application decrypts and monitors encrypted connections with websites that use an EV certificate.
If the check box is cleared, the application does not have access to the contents of HTTPS traffic. For this reason, the application monitors HTTPS traffic only based on the website address, for example,
https://bing.com.If you are opening a website with an EV certificate for the first time, the encrypted connection will be decrypted regardless of whether or not the check box is selected.
- Allow. When visiting a domain with an untrusted certificate, Kaspersky Endpoint Security allows the network connection.