Web Threat Protection
The Web Threat Protection component prevents downloads of malicious files from the Internet, and also blocks malicious and phishing websites. The component provides computer protection with the help of anti-virus databases, the Kaspersky Security Network cloud service, and heuristic analysis.
Kaspersky Endpoint Security scans HTTP-, HTTPS- and FTP-traffic. Kaspersky Endpoint Security scans URLs and IP addresses. You can specify the ports that Kaspersky Endpoint Security will monitor, or select all ports.
For HTTPS traffic monitoring, you need to enable encrypted connections scan.
When a user tries to open a malicious or phishing website, Kaspersky Endpoint Security will block access and show a warning (see the figure below).
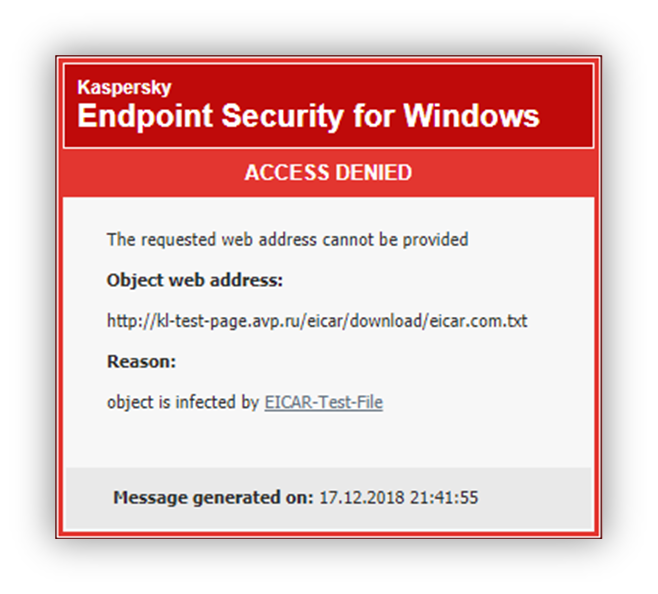
Website access denied message
Web Threat Protection component settings
Parameter |
Description |
|---|---|
Action on threat detection |
|
Do not scan web traffic from trusted web addresses |
If the check box is selected, the Web Threat Protection component does not scan the content of web pages or websites whose addresses are included in the list of trusted web addresses. |
Trusted web addresses |
The Web Threat Protection component does not scan the content of web pages or websites whose addresses are included in the list of trusted web addresses. You can add both the specific address and the address mask of a web page/website to the list of trusted web addresses. |