Scan from context menu
Kaspersky Endpoint Security lets you run a scan of individual files for viruses and other malware from the context menu (see the figure below).
When performing a scan from the context menu, Kaspersky Endpoint Security does not scan files whose contents are located in OneDrive cloud storage.
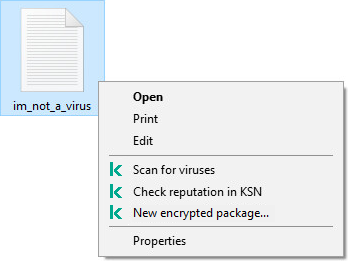
Scan from context menu
Scan from Context Menu task settings
Parameter |
Description |
|---|---|
Action on threat detection |
Disinfect; delete if disinfection fails. If this option is selected, Kaspersky Endpoint Security automatically attempts to disinfect all infected files that are detected. If disinfection fails, Kaspersky Endpoint Security deletes the files. Disinfect; block if disinfection fails. If this option is selected, Kaspersky Endpoint Security automatically attempts to disinfect all infected files that are detected. If disinfection is not possible, Kaspersky Endpoint Security adds the information about the infected files that are detected to the list of active threats. Inform. If this option is selected, Kaspersky Endpoint Security adds the information about infected files to the list of active threats on detection of these files. |
Scan only new and changed files |
Scans only new files and those files that have been modified since the last time they were scanned. This helps reduce the duration of a scan. This mode applies both to simple and to compound files. |
Skip files that are scanned for longer than N sec |
Limits the duration for scanning a single object. After the specified amount of time, Kaspersky Endpoint Security stops scanning a file. This helps reduce the duration of a scan. |
Scan archives |
Scans archives in the following formats: RAR, ARJ, ZIP, CAB, LHA, JAR, and ICE. |
Scan distribution packages |
The check box enables or disables scanning of distribution packages. |
Scan files in Microsoft Office formats |
Scans Microsoft Office files (DOC, DOCX, XLS, PPT and other Microsoft extensions). Microsoft Office files also include OLE objects. |
Do not unpack large compound files |
If this check box is selected, Kaspersky Endpoint Security does not scan compound files if their size exceeds the specified value. |
Machine learning and signature analysis |
The machine learning and signature analysis method uses the Kaspersky Endpoint Security databases that contain descriptions of known threats and ways to neutralize them. Protection that uses this method provides the minimum acceptable security level. Based on the recommendations of Kaspersky experts, machine learning and signature analysis is always enabled. |
Heuristic Analysis |
The technology was developed for detecting threats that cannot be detected by using the current version of Kaspersky application databases. It detects files that may be infected with an unknown virus or a new variety of a known virus. When scanning files for malicious code, the heuristic analyzer executes instructions in the executable files. The number of instructions that are executed by the heuristic analyzer depends on the level that is specified for the heuristic analyzer. The heuristic analysis level ensures a balance between the thoroughness of searching for new threats, the load on the resources of the operating system, and the duration of heuristic analysis. |
iSwift Technology |
This technology increases scanning speed by excluding certain files from scanning. Files are excluded from scanning by using a special algorithm that takes into account the release date of Kaspersky Endpoint Security databases, the date that the file was last scanned on, and any modifications to the scanning settings. The iSwift technology is an advancement of the iChecker technology for the NTFS file system. |
iChecker Technology |
This technology increases scanning speed by excluding certain files from scanning. Files are excluded from scans by using a special algorithm that takes into account the release date of Kaspersky Endpoint Security databases, the date when the file was last scanned, and any modifications to the scan settings. There are limitations to iChecker Technology: it does not work with large files and applies only to files with a structure that the application recognizes (for example, EXE, DLL, LNK, TTF, INF, SYS, COM, CHM, ZIP, and RAR). |