Device Control
This component is available if Kaspersky Endpoint Security is installed on a computer that runs on Windows for workstations. This component is unavailable if Kaspersky Endpoint Security is installed on a computer that runs on Windows for servers.
Device Control manages user access to devices that are installed on or connected to the computer (for example, hard drives, cameras, or Wi-Fi modules). This lets you protect the computer from infection when such devices are connected, and prevent loss or leaks of data.
Device access levels
Device Control controls access at the following levels:
- Device type. For example, printers, removable drives, and CD/DVD drives.
You can configure device access as follows:
- Allow –
 .
. - Block –
 .
. - Depends on connection bus (except for Wi-Fi) –
 .
. - Block with exceptions (Wi-Fi only) –
 .
.
- Allow –
- Connection bus. A connection bus is an interface used for connecting devices to the computer (for example, USB or FireWire). Therefore, you can restrict the connection of all devices, for example, over USB.
You can configure device access as follows:
- Allow –
 .
. - Block –
 .
.
- Allow –
- Trusted devices. Trusted devices are devices to which users that are specified in the trusted device settings have full access at all times.
You can add trusted devices based on the following data:
- Devices by ID. Each device has a unique identifier (Hardware ID, or HWID). You can view the ID in the device properties by using operating system tools. Example device ID:
SCSI\CDROM&VEN_NECVMWAR&PROD_VMWARE_SATA_CD00\5&354AE4D7&0&000000. Adding devices by ID is convenient if you want to add several specific devices. - Devices by model. Each device has a vendor ID (VID) and a product ID (PID). You can view the IDs in the device properties by using operating system tools. Template for entering the VID and PID:
VID_1234&PID_5678. Adding devices by model is convenient if you use devices of a certain model in your organization. This way, you can add all devices of this model. - Devices by ID mask. If you are using multiple devices with similar IDs, you can add devices to the trusted list by using masks. The
*character replaces any set of characters. Kaspersky Endpoint Security does not support the?character when entering a mask. For example,WDC_C*. - Devices by model mask. If you are using multiple devices with similar VIDs or PIDs (for example, devices from the same manufacturer), you can add devices to the trusted list by using masks. The
*character replaces any set of characters. Kaspersky Endpoint Security does not support the?character when entering a mask. For example,VID_05AC & PID_ *.
- Devices by ID. Each device has a unique identifier (Hardware ID, or HWID). You can view the ID in the device properties by using operating system tools. Example device ID:
Device Control regulates user access to devices by using access rules. Device Control also lets you save device connection/disconnection events. To save events, you need to configure the registration of events in a policy.
If access to a device depends on the connection bus (the ![]() status), Kaspersky Endpoint Security does not save device connection/disconnection events. To enable Kaspersky Endpoint Security to save device connection/disconnection events, allow access to the corresponding type of device (the
status), Kaspersky Endpoint Security does not save device connection/disconnection events. To enable Kaspersky Endpoint Security to save device connection/disconnection events, allow access to the corresponding type of device (the ![]() status) or add the device to the trusted list.
status) or add the device to the trusted list.
When a device that is blocked by Device Control is connected to the computer, Kaspersky Endpoint Security will block access and show a notification (see the figure below).
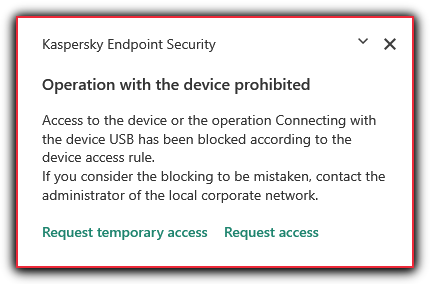
Device Control notification
Device Control operating algorithm
Kaspersky Endpoint Security makes a decision on whether to allow access to a device after the user connects the device to the computer (see the figure below).
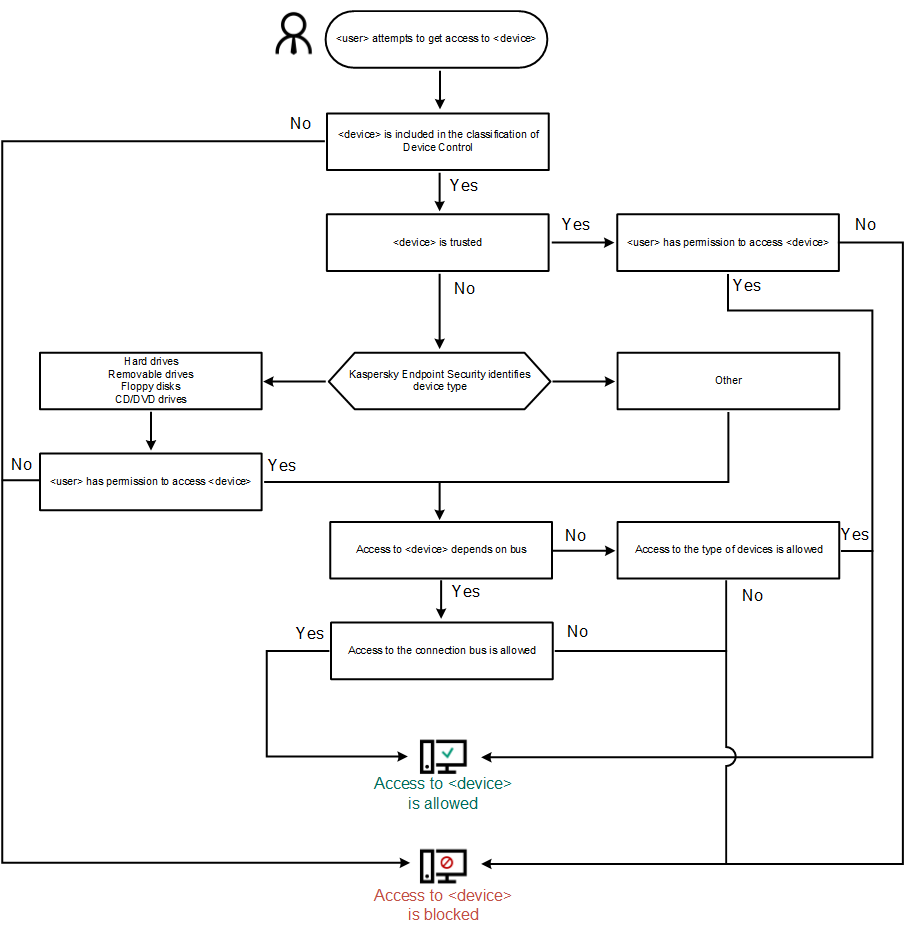
Device Control operating algorithm
If a device is connected and access is allowed, you can edit the access rule and block access. In this case, the next time someone attempts to access the device (such as to view the folder tree, or perform read or write operations), Kaspersky Endpoint Security blocks access. A device without a file system is blocked only the next time that the device is connected.
If a user of the computer with Kaspersky Endpoint Security installed must request access to a device that the user believes was blocked by mistake, send the user the request access instructions.