Managing policies
A policy is a collection of application settings that are defined for an administration group. You can configure multiple policies with different values for one application. An application can run under different settings for different administration groups. Each administration group can have its own policy for an application.
Policy settings are sent to client computers by Network Agent during synchronization. By default, the Administration Server performs synchronization immediately after policy settings are changed. UDP port 15000 on the client computer is used for synchronization. The Administration Server performs synchronization every 15 minutes by default. If synchronization fails after policy settings were changed, the next synchronization attempt will be performed according to the configured schedule.
Active and inactive policy
A policy is intended for a group of managed computers and can be active or inactive. The settings of an active policy are saved on client computers during synchronization. You cannot simultaneously apply multiple policies to one computer, therefore only one policy may be active in each group.
You can create an unlimited number of inactive policies. An inactive policy does not affect application settings on computers in the network. Inactive policies are intended as preparations for emergency situations, such as a virus attack. If there is an attack via flash drives, you can activate a policy that blocks access to flash drives. In this case, the active policy automatically becomes inactive.
Out-of-office policy
An out-of-office policy is activated when a computer leaves the organization network perimeter.
Settings inheritance
Policies, like administration groups, are arranged in a hierarchy. By default, a child policy inherits settings from the parent policy. Child policy is a policy for nested hierarchy levels, that is a policy for nested administration groups and secondary Administration Servers. You can disable the inheritance of settings from the parent policy.
Each policy setting has the ![]() attribute, which indicates if the settings can be modified in the child policies or in the local application settings. The
attribute, which indicates if the settings can be modified in the child policies or in the local application settings. The ![]() attribute is applicable only if inheritance of parent policy settings is enabled for the child policy. Out-of-office policies do not affect other policies through the hierarchy of administration groups.
attribute is applicable only if inheritance of parent policy settings is enabled for the child policy. Out-of-office policies do not affect other policies through the hierarchy of administration groups.
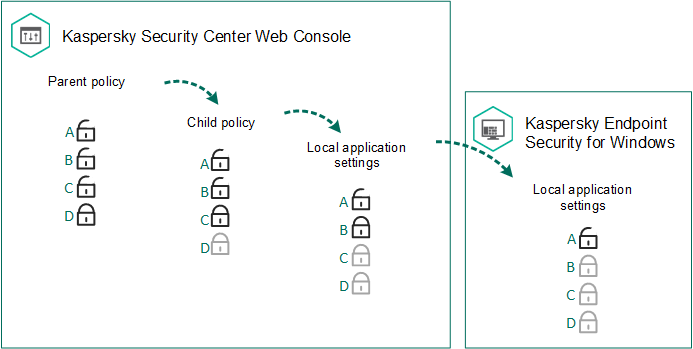
Settings inheritance
The rights to access policy settings (read, write, execute) are specified for each user who has access to the Kaspersky Security Center Administration Server and separately for each functional scope of Kaspersky Endpoint Security. To configure the rights to access policy settings, go to the Security section of the properties window of the Kaspersky Security Center Administration Server.
Creating a policy
How to create a policy in the Administration Console (MMC)
How to create a policy in the Web Console and Cloud Console
As a result, Kaspersky Endpoint Security settings will be configured on client computers during the next synchronization. You can view information about the policy that is being applied to the computer in the Kaspersky Endpoint Security interface by clicking the Support button on the main screen (for example, the policy name). To do so, in the settings of the Network Agent policy, you need to enable the receipt of extended policy data. For more details about a Network Agent policy, please refer to the Kaspersky Security Center Help Guide.
Security level indicator
The security level indicator is displayed in the top part of the Properties: <Policy name> window. The indicator can take one of the following values:
- High protection level. The indicator takes this value and turns green if all components from the following categories are enabled:
- Critical. This category includes the following components:
- File Threat Protection.
- Behavior Detection.
- Exploit Prevention.
- Remediation Engine.
- Important. This category includes the following components:
- Kaspersky Security Network.
- Web Threat Protection.
- Mail Threat Protection.
- Host Intrusion Prevention.
- Critical. This category includes the following components:
- Medium protection level. The indicator takes this value and turns yellow if one of the important components is disabled.
- Low protection level. The indicator takes this value and turns red in one of the following cases:
- One or multiple critical components are disabled.
- Two ore more important components are disabled.
If the indicator has the Medium protection level or Low protection level value, a link that opens the Recommended protection components window appears to the right of the indicator. In this window, you can enable any of the recommended protection components.
Page top