Obtaining access to a blocked device
When configuring Device Control, you can accidentally block access to a device that is necessary for work.
If Kaspersky Security Center is not deployed in your organization, you can provide access to a device in the settings of Kaspersky Endpoint Security. For example, you can add the device to the trusted list or temporarily disable Device Control.
If Kaspersky Security Center is deployed in your organization and a policy has been applied to computers, you can provide access to a device in the Administration Console.
Online mode for granting access
You can grant access to a blocked device in online mode only if Kaspersky Security Center is deployed in the organization and a policy has been applied to the computer. The computer must have the capability to establish a connection with the Administration Server.
Granting access in online mode consists of the following steps:
- The user sends the administrator a message containing an access request.
- The administrator adds the device to the trusted list.
You can add a trusted device in a policy for the administration group or in the local application settings for an individual computer.
- The administrator updates the settings of Kaspersky Endpoint Security on the user's computer.
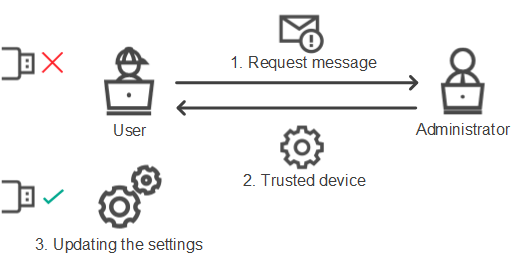
Schematic for granting access to a device in online mode
Offline mode for granting access
You can grant access to a blocked device in offline mode only if Kaspersky Security Center is deployed in the organization and a policy has been applied to the computer. In the policy settings, in the Device Control section, the Allow requests for temporary access check box must be selected.
If you need to grant temporary access to a blocked device but you cannot add the device to the trusted list, you can grant access to the device in offline mode. This way, you can grant access to a blocked device even if the computer does not have network access or if the computer is outside of the corporate network.
Granting access in offline mode consists of the following steps:
- The user creates a request access file and sends it to the administrator.
- The administrator creates an access key from the request access file and sends it to the user.
- The user activates the access key.
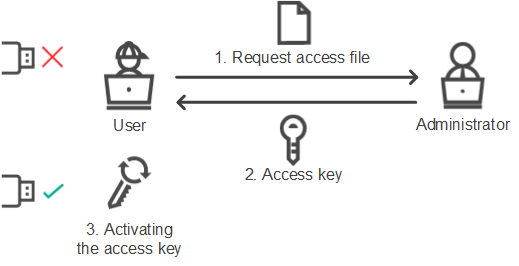
Schematic for granting access to a device in offline mode