Password protection
Multiple users with different levels of computer literacy can share a computer. If users have unrestricted access to Kaspersky Endpoint Security and its settings, the overall level of computer protection may be reduced. Password protection lets you restrict users' access to Kaspersky Endpoint Security according to the permissions granted to them (for example, permission to exit the application).
If the user that started the Windows session (session user) has the permission to perform the action, Kaspersky Endpoint Security does not request the user name and password or a temporary password. The user receives access to Kaspersky Endpoint Security in accordance with the granted permissions.
If a session user does not have the permission to perform an action, the user can obtain access to the application in the following ways:
- Enter a user name and password.
This method is suitable for day-to-day operations. To perform a password-protected action, you must enter the domain account credentials of the user with the required permission. In this case, the computer must be in that domain. If the computer is not in the domain, you can use the KLAdmin account.
- Enter a temporary password.
This method is suitable for granting temporary permissions to perform blocked actions (for example, exiting the application) to users outside the corporate network. When a temporary password expires or a session ends, Kaspersky Endpoint Security reverts its settings to their previous state.
When a user attempts to perform a password-protected action, Kaspersky Endpoint Security prompts the user for the user name and password or temporary password (see the figure below).
In the password entry window, you can switch languages only by pressing ALT+SHIFT. Using other shortcuts, even if they are configured in the operating system, do not work for switching languages.
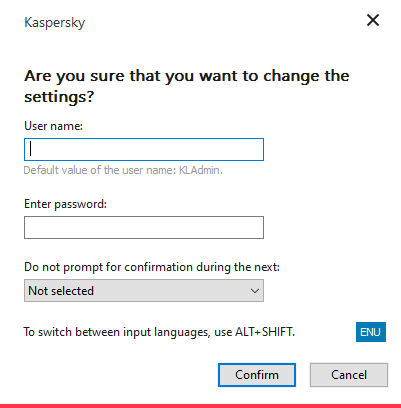
Kaspersky Endpoint Security access password prompt
User name and password
To access Kaspersky Endpoint Security, you must enter your domain account credentials. Password protection supports the following accounts:
- KLAdmin. An Administrator account with unrestricted access to Kaspersky Endpoint Security. The KLAdmin account has the right to perform any action that is password-protected. The permissions for the KLAdmin account cannot be revoked. When you enable password protection, Kaspersky Endpoint Security prompts you to set a password for the KLAdmin account.
- The Everyone group. A built-in Windows group that includes all users within the corporate network. Users in the Everyone group can access the application according to the permissions that are granted to them.
- Individual users or groups. User accounts for which you can configure individual permissions. For example, if an action is blocked for the Everyone group, you can allow this action for an individual user or a group.
- Session user. Account of the user who started the Windows session. You can switch to another session user when prompted for a password (the Save password for current session check box). In this case, Kaspersky Endpoint Security regards the user whose account credentials were entered as the session user instead of the user who started the Windows session.
Temporary password
A temporary password can be used to grant temporary access to Kaspersky Endpoint Security for an individual computer outside of the corporate network. The Administrator generates a temporary password for an individual computer in the computer properties in Kaspersky Security Center. The Administrator selects the actions that will be protected with the temporary password, and specifies the temporary password's validity period.
Password protection operating algorithm
Kaspersky Endpoint Security decides whether to allow or block a password-protected action based on the following algorithm (see the figure below).
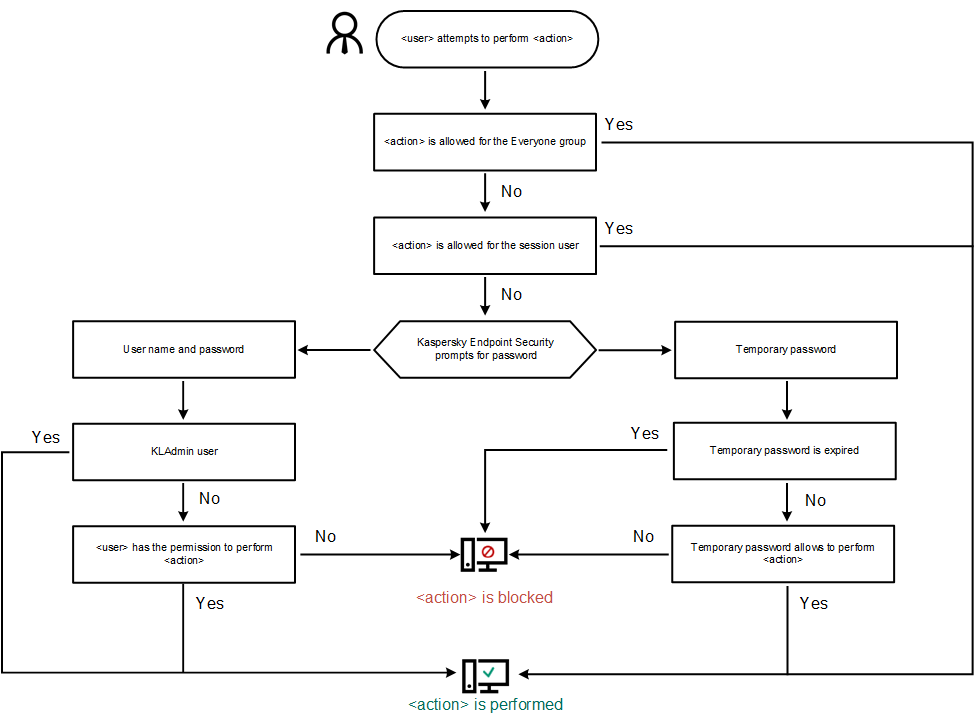
Password protection operating algorithm