Starting BitLocker Drive Encryption
Prior to starting full disk encryption, you are advised to make sure that the computer is not infected. To do so, start the Full Scan or Critical Areas Scan task. Performing full disk encryption on a computer that is infected by a rootkit may cause the computer to become inoperable.
To use BitLocker Drive Encryption on computers running Windows operating systems for servers, installing the BitLocker Drive Encryption component may be required. Install the component using the operating system tools (Add Roles and Components Wizard). For more information about installing BitLocker Drive Encryption, refer to the Microsoft documentation.
How to run BitLocker Drive Encryption through the Administration Console (MMC)
How to run BitLocker Drive Encryption through the Web Console and Cloud Console
You can use the Encryption Monitor tool to control the disk encryption or decryption process on a user's computer. You can run the Encryption Monitor tool from the main application window.
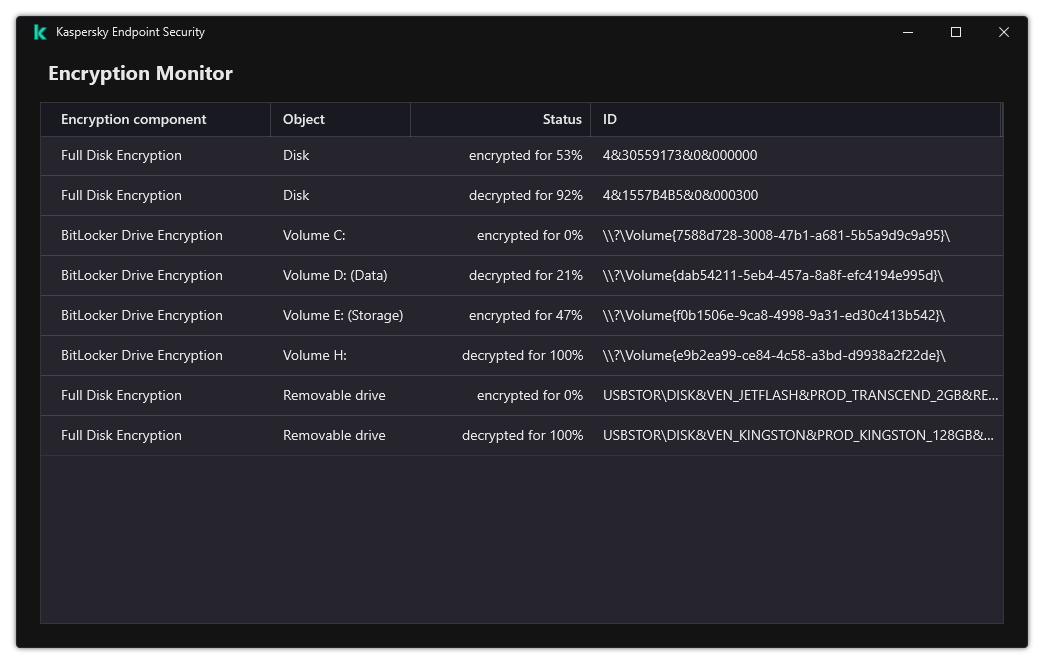
Encryption Monitor
After the policy is applied, the application will display the following queries, depending on the authentication settings:
- TPM only. No user input required. The disk will be encrypted when the computer restarts.
- TPM + PIN / Password. If a TPM module is available, a PIN code prompt window appears. If a TPM module is not available, you will see a password prompt window for preboot authentication.
- Password only. You will see a password prompt window for preboot authentication.
If the Federal Information Processing standard compatibility mode is enabled for computer operating system, then in Windows 8 and earlier versions of operating system, a request for connecting a storage device is displayed to save the recovery key file. You can save multiple recovery key files on a single storage device.
After setting a password or a PIN, BitLocker will ask you to restart your computer to complete the encryption. Next, the user needs to go through the BitLocker authentication procedure. After the authentication procedure, the user must log on to the system. After the operating system has loaded, BitLocker will complete the encryption.
If there is no access to encryption keys, the user may request the local network administrator to provide a recovery key (if the recovery key was not saved earlier on the storage device or was lost).
BitLocker Drive Encryption component settings
Parameter |
Description |
|---|---|
Enable use of BitLocker authentication requiring pre-boot keyboard input on tablets |
This check box enables / disables the use of authentication requiring data input in a preboot environment, even if the platform does not have the capability for preboot input (for example, with touchscreen keyboards on tablets). The touchscreen of tablet computers is not available in the preboot environment. To complete BitLocker authentication on tablet computers, the user must connect a USB keyboard, for example. If the check box is selected, use of authentication requiring preboot input is allowed. It is recommended to use this setting only for devices that have alternative data input tools in a preboot environment, such as a USB keyboard in addition to touchscreen keyboards. If the check box is cleared, BitLocker Drive Encryption is not possible on tablets. |
Use hardware encryption (Windows 8 and later versions) |
If the check box is selected, the application applies hardware encryption. This lets you increase the speed of encryption and use less computer resources. |
Encrypt used disk space only (reduces encryption time) |
This check box enables / disables the option that limits the encryption area to only occupied hard drive sectors. This limit lets you reduce encryption time. Enabling or disabling the Encrypt used disk space only (reduces encryption time) feature after starting encryption does not modify this setting until the hard drives are decrypted. You must select or clear the check box before starting encryption. If the check box is selected, only portions of the hard drive that are occupied by files are encrypted. Kaspersky Endpoint Security automatically encrypts new data as it is added. If the check box is cleared, the entire hard drive is encrypted, including residual fragments of previously deleted and modified files. This option is recommended for new hard drives whose data has not been modified or deleted. If you are applying encryption on a hard drive that is already in use, it is recommended to encrypt the entire hard drive. This ensures protection of all data, even deleted data that is potentially recoverable. This check box is cleared by default. |
Authentication method |
Only password (Windows 8 and later versions) If this option is selected, Kaspersky Endpoint Security prompts the user for a password when the user attempts to access an encrypted drive. This option can be selected when a Trusted Platform Module (TPM) is not being used. Trusted platform module (TPM) If this option is selected, BitLocker uses a Trusted Platform Module (TPM). A Trusted Platform Module (TPM) is a microchip developed to provide basic functions related to security (for example, to store encryption keys). A Trusted Platform Module is usually installed on the computer motherboard and interacts with all other system components via the hardware bus. For computers running Windows 7 or Windows Server 2008 R2, only encryption using a TPM module is available. If a TPM module is not installed, BitLocker encryption is not possible. Use of a password on these computers is not supported. A device equipped with a Trusted Platform Module can create encryption keys that can be decrypted only with the device. A Trusted Platform Module encrypts encryption keys with its own root storage key. The root storage key is stored within the Trusted Platform Module. This provides an additional level of protection against attempts to hack encryption keys. This action is selected by default. You can set an additional layer of protection for access to the encryption key, and encrypt the key with a password or a PIN:
|