Enabling encrypted connections scan
By default, Kaspersky Endpoint Security does not always scan encrypted connections, but only when requested by protection components.
How to enable encrypted connections scan in the Administration Console (MMC)
How to enable encrypted connections scan in the Web Console and Cloud Console
How to enable encrypted connections scan in the application interface
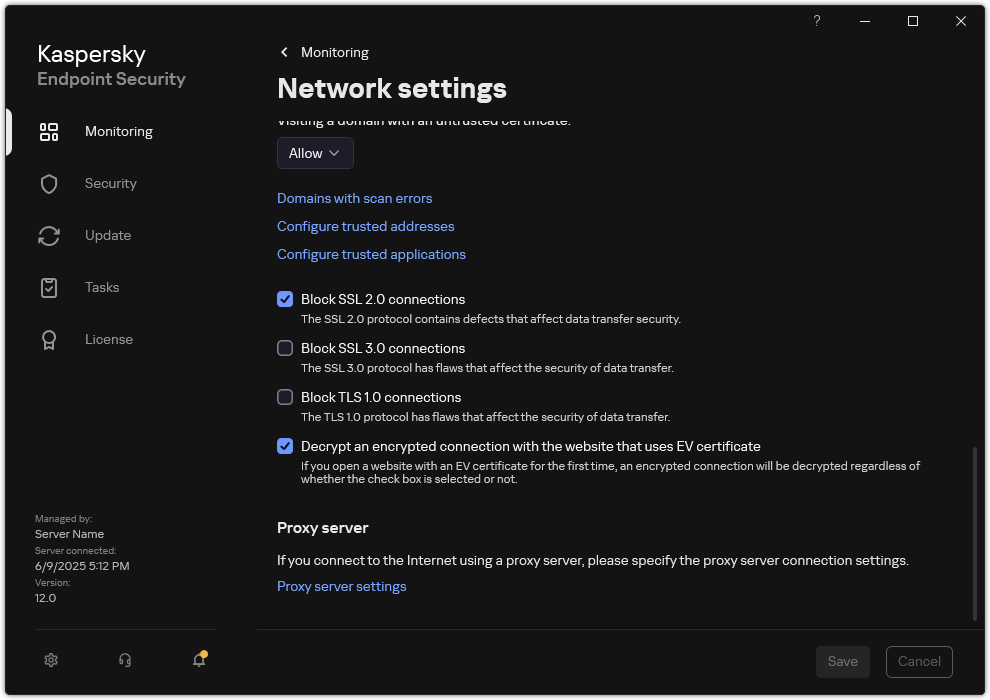
Encrypted connections scan settings
Parameter |
Description |
|---|---|
Trusted root certificates |
List of trusted root certificates. Kaspersky Endpoint Security lets you install trusted root certificates on user computers if, for example, you need to deploy a new certification center. The application lets you add a certificate to a special Kaspersky Endpoint Security certificate store. In this case, the certificate is considered trusted only for the Kaspersky Endpoint Security application. In other words, the user can gain access to a website with the new certificate in the browser. If another application tries to gain access to the website, you can get a connection error because of a certificate issue. To add to the system certificate store, you can use Active Directory group policies. |
Visiting a domain with an untrusted certificate |
|
Visiting a domain with an encrypted connections scan error |
|
Block SSL 2.0 connections |
If the check box is selected, the application monitors and blocks network connections established over the SSL 2.0 protocol. If the check box is cleared, the application does not block network connections established over the SSL 2.0 protocol. However, the application does not monitor network traffic over this protocol. |
Block SSL 3.0 connections |
If the check box is selected, the application blocks network connections established over the SSL 3.0 protocol. If the check box is selected, the application blocks network connections established over the SSL 3.0 protocol. The application monitors network traffic over this protocol. All components of the application work without restrictions. |
Block TLS 1.0 connections |
If the check box is selected, the application blocks network connections established over the TLS 1.0 protocol. If the check box is selected, the application blocks network connections established over the TLS 1.0 protocol. The application monitors network traffic over this protocol. All components of the application work without restrictions. |
Decrypt an encrypted connection with the website that uses EV certificate |
EV certificates (Extended Validation Certificate) confirm the authenticity of websites and enhance the security of the connection. Browsers use a lock icon in their address bar to indicate that a website has an EV certificate. Browsers may also fully or partially color the address bar in green. If the check box is selected, the application decrypts and monitors encrypted connections with websites that use an EV certificate. If the check box is cleared, the application does not have access to the contents of HTTPS traffic. For this reason, the application monitors HTTPS traffic only based on the website address, for example, If you are opening a website with an EV certificate for the first time, the encrypted connection will be decrypted regardless of whether or not the check box is selected. |
 .
.