Migrating the KSWS trusted zone
A trusted zone is a system administrator-configured list of objects and applications that Kaspersky Endpoint Security does not monitor when active. You can migrate trusted zone objects from KSWS to KES using the Policies and Tasks Batch Conversion Wizard or the wizard for creating a new KES policy based on the KSWS policy. KSWS and KES have different sets of components and features, so after migration you must verify that exclusions satisfy your corporate security requirements. The methods of adding exclusions to the trusted zone are also different for KES and KSWS. The Migration Wizard does not have tools to migrate all KSWS exclusions. This means that after the migration, you must manually add some of the KSWS exclusions.
To make sure Kaspersky Endpoint Security works correctly on servers, it is recommended to add files important for the server's functioning to the trusted zone. For SQL servers, you must add MDF and LDF database files. For Microsoft Exchange servers, you must add CHK, EDB, JRS, LOG, and JSL files. You may use masks, for example, C:\Program Files (x86)\Microsoft SQL Server\*.mdf.
Starting with Kaspersky Endpoint Security 12.6 for Windows, scan exclusions and trusted applications are added to the trusted zone. Predefined scan exclusions and trusted applications help quickly configure Kaspersky Endpoint Security on SQL servers, Microsoft Exchange servers, and System Center Configuration Manager. This means you do not need to manually set up a trusted zone for the application on servers.
KES and KSWS trusted zone creation methods.
KSWS |
|
KES |
|---|---|---|
Object to scan |
|
|
|
(does not migrate) |
|
|
→ |
File or folder |
|
→ |
File or folder |
|
(does not migrate) |
|
Detected object |
→ |
Object name |
Trusted processes |
→ |
Trusted applications |
Migration of scanned objects
KSWS exclusions that have the Object to scan method selected in their properties are migrated to KES exclusions that have the File or folder method selected in their properties, with some limitations. The migration of an exclusion depends on the object selection method:
- Predefined scope – does not migrate.
After migration, you must add such exclusions manually. Exclusions as predefined areas must be configured in the Malware Scan task settings.
- Disk, folder or network location – migrate to KES exclusions that have the "File or folder" method selected in properties.
- File – migrate to KES exclusions that have the "File or folder" method selected in properties.
- Script file or web address – does not migrate.
After migration, you must add such exclusions manually. Exclusions as script web addresses must be added to trusted web addresses for Web Threat Protection.
If the Apply also to subfolders check box is selected for the scanned object, this setting is migrated to KES exclusions (the Include subfolders check box).
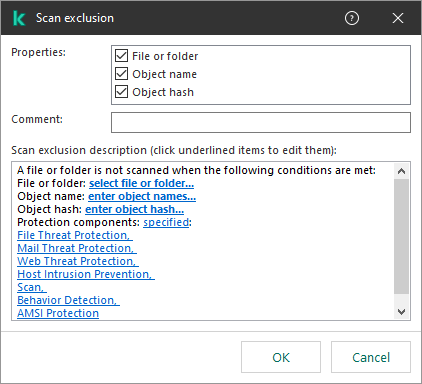
KES exclusion settings
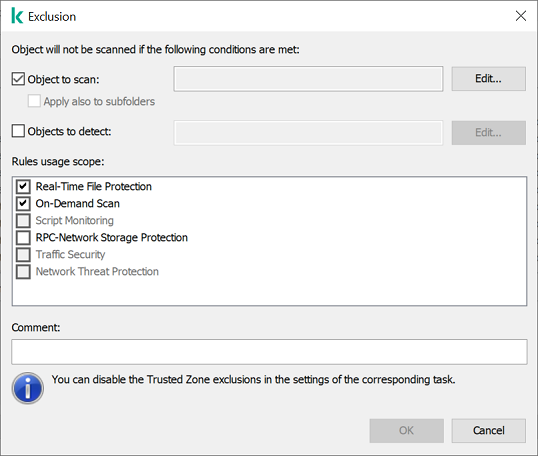
KSWS exclusion settings
Migration of detected objects
KSWS exclusions that have the Detected object method selected in their properties are migrated to KES exclusions that have the Object name method selected in their properties. The name of the detected object corresponds to the classification of the Kaspersky Encyclopedia (for example, Email-Worm, Rootkit, or RemoteAdmin). Kaspersky Endpoint Security supports masks with the question mark ? (matches any single character) and the asterisk * (matches any sequence of characters).
Migration of exclusion usage scope
The usage scope of an exclusion is a set of components to which the exclusion applies. KES and KSWS have different sets of components so the Migration Wizard cannot migrate the exclusion usage scope. Therefore, if at least one component is selected in the KSWS usage scope, KES applies the exclusion to all application components.
You can configure the KSWS usage scope in trusted zone settings and also in the settings of KSWS protection components. To do so, you can select or clear the Apply Trusted Zone check box in the corresponding section of the policy. The settings of KES protection components do not include such a check box. This means the trusted zone status in individual component settings is lost upon migration. After completing the migration, select components to which the exclusion applies in trusted zone settings in the KES policy.
Migrating comments
Comments from the KSWS trusted zone are migrated to KES exclusion comments without modification.
Migrating trusted processes
KSWS trusted processes are migrated to KES trusted processes with some limitations. Migrating trusted processes depends on the object selection method:
- Path to the file on the protected device – migrates to KES trusted applications.
- File hash – does not migrate.
If KSWS has trusted processes configured as a file hash, such trusted processes are not migrated. After migration, you must add such trusted processes manually.
If the Do not check file backup operations check box is selected in trusted process settings, this setting is migrated to KES trusted applications (the Do not monitor application activity check box).
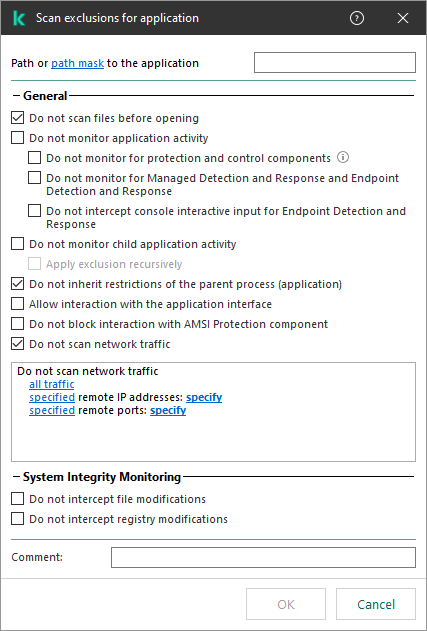
KES trusted application settings
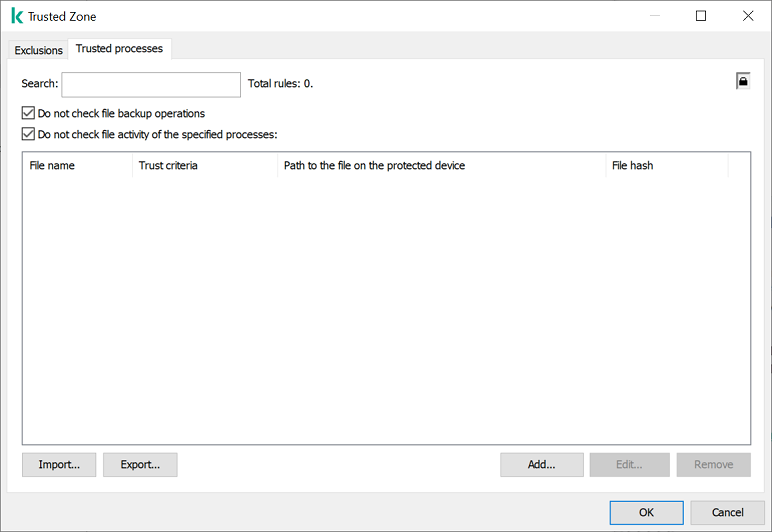
KSWS trusted process settings
Page top