Sending Kaspersky Industrial CyberSecurity for Networks events to SIEM systems
In Kaspersky Industrial CyberSecurity for Networks, you can use a connector to send data to a SIEM system server. After you add a connector, you need to configure forwarding of events through this connector.
The contents and order in which information is displayed about events forwarded to a SIEM system may differ from the data displayed in the Events section of the Kaspersky Industrial CyberSecurity for Networks Server web interface.
- Verifying event forwarding using an HP ArcSight system (as an example)
To verify event forwarding:
- Make sure that a channel is configured for receiving messages from Kaspersky Industrial CyberSecurity for Networks using the standard tools of the HP ArcSight system.
- Open your browser and enter the address of your HP ArcSight system.
- Log in to your user account and go to Analyze → Live Event Viewer (see the figure below).
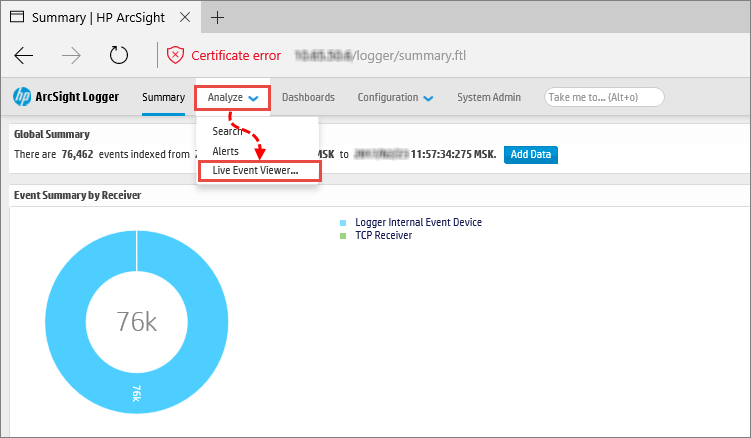
Opening the Live Event Viewer section in the HP ArcSight system
- Click the Start button (see the figure below).
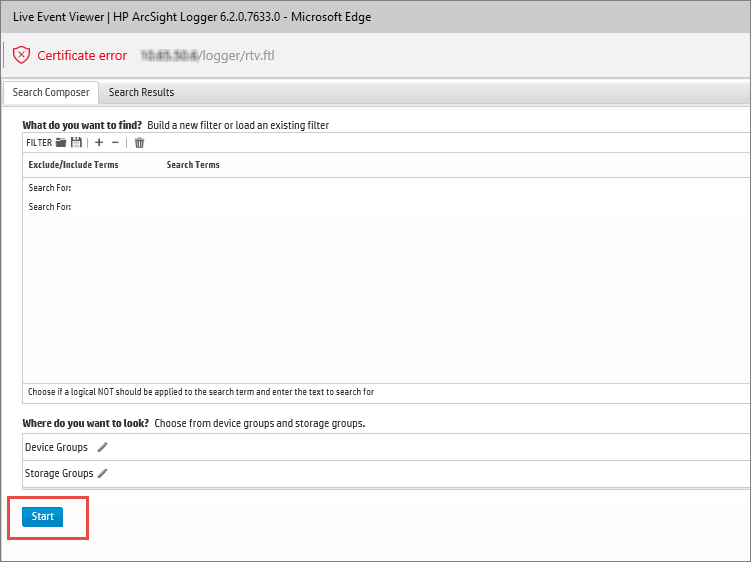
Starting Live Event Viewer in the HP ArcSight system
- Open the command line interface and enter the following command to connect to the server over the Telnet protocol:
telnet <ArcSight server address> <port> - Send a test message in CEF format:
CEF:0|KasperskyLab|TMS|1.0|KLAUD_EV_TESTEVENT|Critical Test event|1|src=10.0.0.1 dst=10.0.0.2 code=1234
If there is a connection with the HP ArcSight system, the Live Event Viewer section will show an event whose contents match the message that was sent (see the figure below).
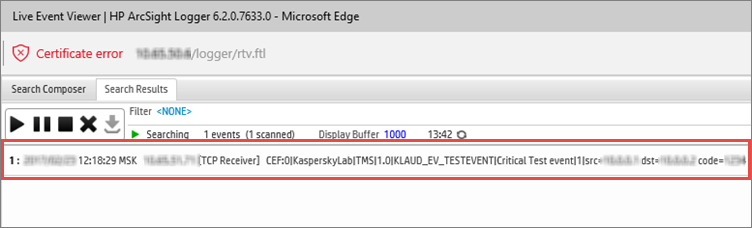
Verifying operation results
- Format of messages forwarded to a SIEM system
The application transmits data to a SIEM system in CEF 20 format. The internal
EventMessagestructure is used when transmitting data.Received messages are not converted to the system log protocol format.
Format of the EventMessage structure
The table below provides data in the following columns:
- EventMessage — field name in a message.
- Event — corresponding field of the event in Kaspersky Industrial CyberSecurity for Networks or a specific value.
- Description — field description.
EventMessage
Event
Description
dateTime
Start
Date and time (with precision down to the millisecond) when the event-triggering network packet was captured.
hostname
Kaspersky Industrial CyberSecurity for Networks Server address
Address of the Kaspersky Industrial CyberSecurity for Networks Server.
cefVersion
0
CEF version number.
deviceVendor
Kaspersky Lab
Vendor.
deviceProduct
Kaspersky Industrial CyberSecurity for Networks
Product name.
deviceVersion
Example: 3.0.0.472.
Version of Kaspersky Industrial CyberSecurity for Networks.
signatureId
Event type
Event type ID.
name
Title
Event description.
severity
Event severity level:
- 10 – Critical
- 5 – Warning
- 0 – Informational
Event severity level.
Values from 0 to 10, where 10 is the most severe event.extension
Indicated in the Extension Fields table
Determined individually for each type of message.
Date and time is sent in the following format:
YYYY-MM-DDThh:mm:ss.msZ. Example: 2021-04-01T22:14:15.030Z — time of the event, which occurred on April 01, 2021 at 22 hours, 14 minutes, 15 seconds, and 030 milliseconds.Contents of Extension Fields
The table below provides data in the following columns:
- Extension — field name in a message.
- Related events — events in which the specific field is sent.
- Description — field description.
Extension
Related events
Description
cnt
Common fields of events
Counter of the number of times an event is repeated after the event is registered.
dmac
Common fields of events
Destination MAC address.
dpt
Common fields of events
Destination port.
dst
Common fields of events
Destination IP address.
end
Common fields of events
Event end time.
smac
Common fields of events
Source MAC address.
spt
Common fields of events
Source port.
src
Common fields of events
Source IP address.
start
Common fields of events
Event registration time.
technology
Common fields of events
Technology that was used to register the event.
triggeredRule
Common fields of events
Triggered rule.
protocol
Common fields of events
Protocol.
vlanId
Common fields of events
VLAN ID.
monitoringPoint
Common fields of events
Monitoring point whose traffic invoked registration of the event.
sourceIndustrialAddress
Common fields of events
Application-level address for the source.
destinationIndustrialAddress
Common fields of events
Application-level address for the destination.
eventIdentifier
Common fields of events
Event ID.
noTrafficDuration
No traffic at monitoring point
Period of no traffic.
tagId
Invalid tag type
Tag ID.
expectedTagType
Invalid tag type
Expected data type of tag.
actualTagType
Invalid tag type
Actual data type of tag.
ruleName
- Process Control rule violation
- Intrusion Detection rule from the system set of rules was triggered
Rule name.
tags
Process Control rule violation
Tags.
msg
Intrusion Detection rule from the system set of rules was triggered
Message.
substitutedIpAddress
- Signs of ARP spoofing detected in ARP replies
- Signs of ARP spoofing detected in ARP requests
IP address of the source of network packets.
targetIpAddress
- Signs of ARP spoofing detected in ARP replies
- Signs of ARP spoofing detected in ARP requests
IP address of the destination of network packets.
attackStartTimestamp
- Signs of ARP spoofing detected in ARP replies
- Signs of ARP spoofing detected in ARP requests
Start time of the activity showing signs of an attack.
ownerMac
- IP address conflict detected
- New IP address detected
- New device detected
- New information received
- Traffic detected from MAC address
- MAC address added to device
- IP address added to device
MAC address of owner.
ownerIp
- New device detected
- MAC address added to device
- IP address added to device
- IP address conflict detected
- New MAC address detected
IP address of owner.
challengerMac
IP address conflict detected
MAC address of challenger.
newIpAddress
New IP address detected
New IP address.
newMacAddress
New MAC address detected
New MAC address.
oldIpAddress
New IP address detected
Old IP address.
assetName
New device detected
Device name.
Device settings
The table below provides data on the settings of devices.
If one or two devices were identified for a detected interaction, Kaspersky Industrial CyberSecurity for Networks also sends known information about one or two devices to the SIEM system.
If multiple devices were identified for a detected interaction, the message is duplicated with different address information and different device settings (if the devices are different).
Extension
Device setting
srcAssetName
Name of the source device.
srcVendor
Vendor of the source device.
srcOS
Operating system of the source device.
srcNetworkName
Network name of the source device.
srcModel
Model of the source device.
dstAssetName
Name of the destination device.
dstVendor
Vendor of the destination device.
dstOS
Operating system of the destination device.
dstNetworkName
Network name of the destination device.
dstModel
Model of the destination device.