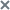Configuring exclusions from Network Threat Protection
In a policy, you can configure network threat protection exclusion rules that Kaspersky Security will use to exclude traffic of specific IP addresses from scans or apply special actions when processing such traffic. You can define exclusion rules for traffic from specific IP addresses or for traffic from all IP addresses in an IP subnet. When generating the scope of rules, the application takes into account whether or not the traffic is from a virtual LAN (VLAN).
If a group of virtual switch ports is running in Virtual Switch Tagging (VST) mode and exclusion rules are applied to traffic of virtual machines associated with this group of ports, the application does not take into account whether or not the traffic belongs to a virtual local area network (VLAN).
To configure a network threat protection exclusion rule:
- In the Kaspersky Security Center Administration Console, open the properties of the policy whose scope includes the relevant virtual machines:
- In the console tree, select the folder or administration group in which the policy was created.
- In the workspace, select the Policies tab.
- Select a policy in the list of policies and double-click the policy to open the Properties: <Policy name> window.
- In the policy properties window, in the Network threat protection section, select the Exclusions from protection subsection.
- Click Add or press INSERT and specify the scope of the exclusion rule in the Scope column.
- Select an exclusion rule in the Rule column.
- If necessary, use the arrows above the list to change the position of the created exclusion rule in the list. The rule priority is determined by its position in the list. If you set multiple rules for the same scope, the rule positioned higher in the list is applied first.
- In the Properties: <Policy name> window, click OK.