Getting detailed information about indicators
This section describes how to get detailed information about an indicator by using Kaspersky Threat Intelligence Portal for Splunk Phantom.
To get detailed information about an indicator from Kaspersky Threat Intelligence Portal:
- In Splunk Phantom, click the Home split button and in the drop-down list select Indicators.
- Select the Events tab.
- In the list, click the event that contains the indicator whose information you want to look up in Kaspersky Threat Intelligence Portal.
- Select the Artifacts tab.
- In the ARTIFACTS list, click the row that is related to the indicator whose information you want to look up in Kaspersky Threat Intelligence Portal.
The row expands and the event information is displayed. The indicator itself is in the Details section.
- Click the indicator you want to look up in Kaspersky Threat Intelligence Portal.
A form related to the indicator appears.
- Select the Run Action tab.
- Expand the Investigate action group and select the get detailed info action.
The Run Action form opens.
- Specify the following input data:
indicator—Indicator (an IP address, hash, URL, or domain) whose detailed information you want to retrieve. By default, it is the indicator you selected.This parameter is mandatory.
sections—List of sections that Kaspersky Threat Intelligence Portal returns.The sections in the list must be delimited by commas. For more information about sections, refer to the Kaspersky Threat Intelligence Portal documentation.
This parameter is optional. If you do not specify this parameter, information from all sections will be retrieved.
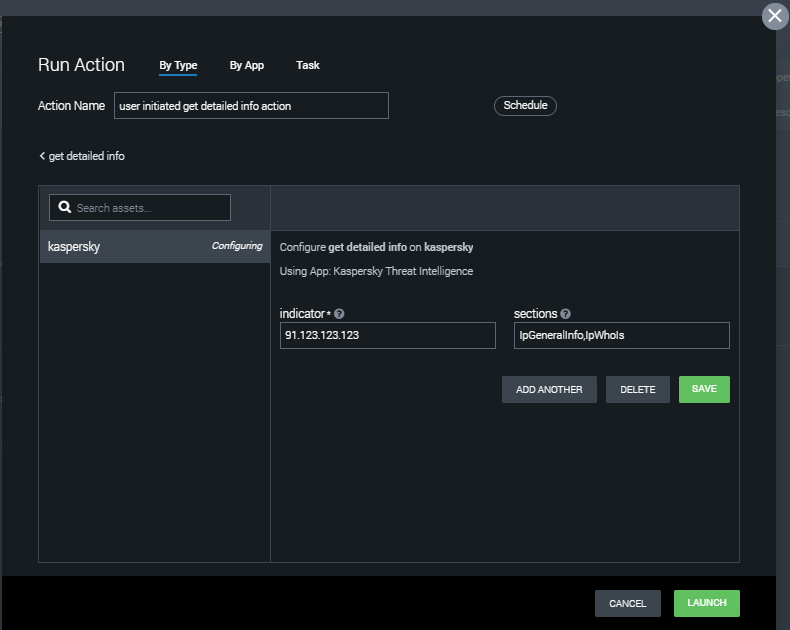
Run Action form
- Click LAUNCH.
The information about the indicator is now displayed in Splunk Phantom. The information displayed depends on the indicator type (IP address, URL, domain, or file hash). For example, the table below describes information about an IP address that Splunk Phantom displays.
IP address intelligence
KL TIP response field |
Splunk Phantom field |
Description |
- |
Indicator |
Requested indicator |
- |
KL TIP URL |
Web address of the indicator's page on Kaspersky Threat Intelligence Portal |
HitsCount |
Hits count |
Number of detections |
name |
APT report name |
Name of the APT report that contains the requested indicator |
You can browse the full response from Kaspersky Threat Intelligence Portal by expanding the tree nodes in the response form.
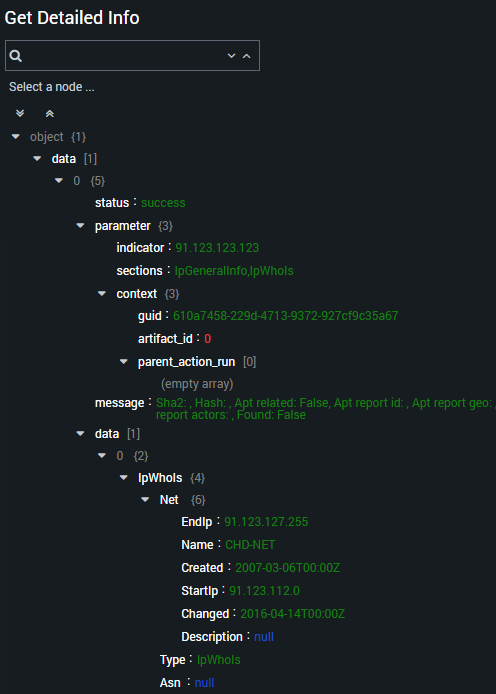
Comments on the request result
Page top