Using Kaspersky Threat Intelligence Portal for Splunk Phantom in playbooks
You can use Kaspersky Threat Intelligence Portal for Splunk Phantom actions in Splunk Phantom playbooks. This section contains an example of how to create a playbook that requests full information about an IP address.
To create a playbook that requests full information about an IP address:
- In Splunk Phantom, click the Home split button and in the drop-down list select Playbooks.
The Playbooks section
- In the list, select the item you want and then click the + Playbook (
 ) button.
) button.The Phantom Playbook Editor opens.
- In the Playbook name text box, specify the playbook name that you want.
- Click the green semicircle of the START element.
A panel with elements that can be created appears to the left of the playbook scheme.
- In the left panel, click the Filter element and create a filter element that checks whether an event contains a value in the
dstfield. - Click the right green semicircle of the filter element just created and create an action element that calls the
ip reputationaction of Kaspersky Threat Intelligence Portal for Splunk Phantom.This action retrieves the reputation of the IP address contained in the
dstfield of the event being checked. - Create a decision element linked to the filter element just created.
Specify the following condition in the decision element: the value of the
threat_scorefield of the event being checked is equal to or greater than75. - Link the Else branch to the END element.
- For the if branch of the decision element, create an action element that calls the
get detailed infoaction of Kaspersky Threat Intelligence Portal for Splunk Phantom. - Link this action element to the END element.
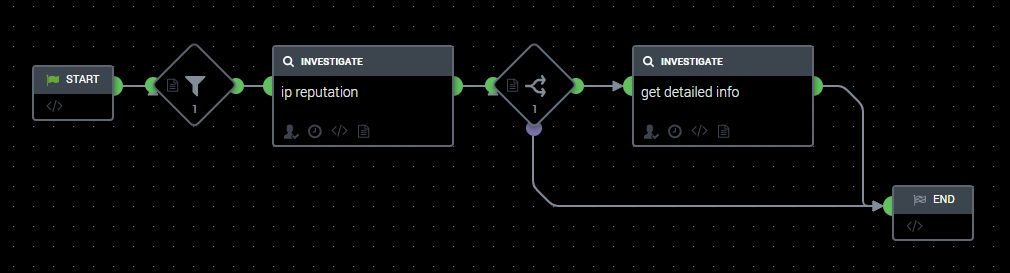
A playbook sample