Application functionality depending on the distribution kit
Operation of Kaspersky Web Traffic Security (Standalone)
When Kaspersky Web Traffic Security (Standalone) is installed from an RPM or DEB package, an external proxy server is used. It can be installed on the same physical server as the application or on a separate physical server. Administration and configuration of an external proxy server is carried out by using the resources of the operating system.
The operating principle of Kaspersky Web Traffic Security (Standalone) is presented in the figure below.
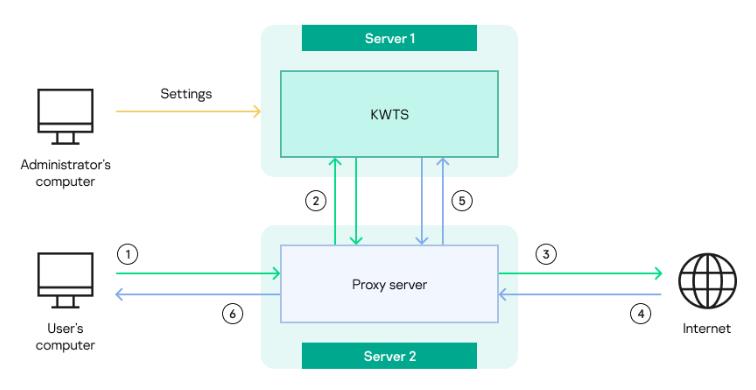
Operating principle of Kaspersky Web Traffic Security (Standalone)
The numbering in the figure corresponds to the following steps of traffic processing:
- A user requests access to a web resource. This request is relayed to the proxy server.
- The proxy server relays the request to the cluster node that processes traffic. The application scans the request according to the traffic processing rules received from the Control node. The result is then relayed to the proxy server.
- If access to a web resource is allowed, the proxy server sends the request to a web server for access to the requested web resource.
- The web server hosting the requested web resource sends a response to the proxy server.
- The response is also sent to the cluster node so that it can be scanned according to the traffic processing rules.
- After the scan, the proxy server sends the response to the user's computer. Depending on the actions configured in the application, the following pages may be displayed:
- If access to the web resource is allowed, the requested web page is displayed.
- If access to the web resource is prohibited, the block page is displayed.
- If the Redirect action was applied, the user sees the web page to which the redirect was configured.
It is recommended to also configure processing of HTTPS traffic on an external proxy server.
Operation of Kaspersky Web Traffic Security (Appliance)
When the application is deployed from an ISO image, a built-in proxy server is installed on each cluster node. The built-in proxy server and Kaspersky Web Traffic Security (ICAP server of the application) communicate over the ICAP protocol locally within the server where the application is installed.
The operating principle of Kaspersky Web Traffic Security (Appliance) is presented in the figure below.
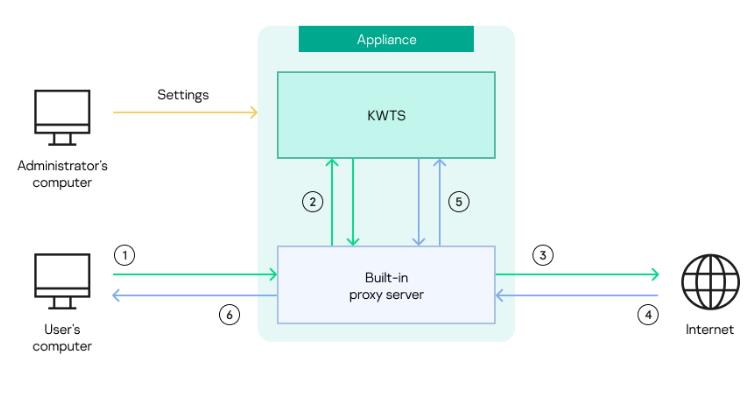
Operating principle of Kaspersky Web Traffic Security (Appliance)
The numbering in the figure corresponds to the following steps of traffic processing:
- A user requests access to a web resource. This request is relayed to the server where the application is installed.
- The built-in proxy server accepts the request and relays it to the application's ICAP server to be scanned in accordance with the traffic processing rules.
- If access to the web resource is allowed according to the scan results, the built-in proxy server sends the request to this web server on the Internet.
- The web server hosting the requested web resource sends a response to the built-in proxy server.
- The built-in proxy server sends the response of the web server to the application's ICAP server to be scanned in accordance with the traffic processing rules. The scan result is returned to the built-in proxy server.
- The built-in proxy server sends the response to the user's computer. Depending on the actions configured in the application, the following pages may be displayed:
- If access to the web resource is allowed, the requested web page is displayed.
- If access to the web resource is prohibited, the block page is displayed.
- If the Redirect action was applied, the user sees the web page to which the redirect was configured.