About imported indicators and their context fields
This section describes the UI display of indicators imported to ThreatConnect.
Each indicator imported to ThreatConnect by Kaspersky Threat Feed App for ThreatConnect contains the following information:
- Indicator value
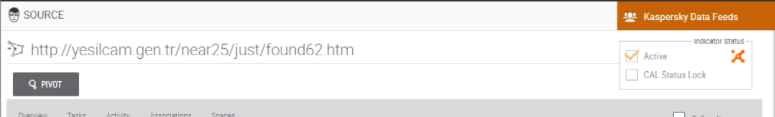
Example of indicator value
- Dates of indicator importing and updating in ThreatConnect
- Overall Threat Rating
The Overall Threat Rating is calculated as follows:
- For Demo Feeds, Exact Feeds, ICS Hash Feeds, and IoT URL Feeds, the rating is defined according to the Popularity field of the feed entry:
Popularity
Overall Threat Rating
1
5
2
4
3
3
4
2
5
1
The less popularity the indicator has, the more dangerous the indicator is.
- For all APT Feeds, the Overall Threat Rating is equal to 5.
- For Vulnerability Feeds and ICS Vulnerability Feeds, the rating is defined according to the Severity field:
Severity
Overall Threat Rating
Low
1
Medium
2
Warning
3
High
4
Critical
5
See the example below:
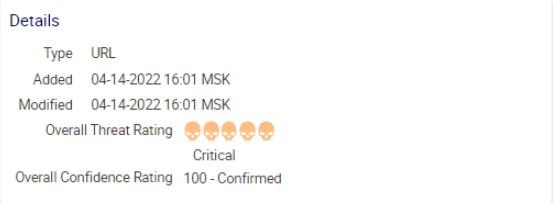
Example of an indicator Overall Threat Rating
- Tags
The tags assigned to indicators are intended for classifying the indicators by the type of feed and threat. The tags are listed in the table of data feeds, indicator types, and tags.
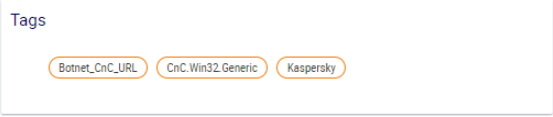
Example of tags
- Context fields
The context fields for each feed type are presented in the table below:
Feed
|
Context field
|
Attribute name TC |
Attribute description |
IP Reputation Data Feed Demo IP Reputation Data Feed |
ip_whois |
IP WhoIs |
Available IP information |
files |
Files |
Array with elements of information about the file downloaded from this IP |
|
APT IP Data Feed
|
detection_date |
Detection date |
The date of detection of the attack to which the file belongs |
publication_name |
Publication name |
The name of the attack to which the file belongs |
|
api_publication_id |
Publication id |
ID of the publication to download the report from KL TIP |
|
actors |
Actors |
Names of criminal groups associated with the use of indicators |
|
industries |
Industries |
List of industries targeted by the attack |
|
Botnet C&C URL Data Feed Demo Botnet C&C URL Data Feed
|
urls |
Urls |
Array with top10 bot URLs |
IP |
IP |
Top 10 IP addresses into which the domain of this Botnet C&C has resolved |
|
whois |
Whois |
Available whois information |
|
files |
Files |
Array with elements of information about the file downloaded from this IP |
|
Botnet C&C URL Exact Data Feed
|
IP |
IP |
Top 10 IP addresses into which the domain of this Botnet C&C has resolved |
whois |
WhoIs |
Available whois information |
|
files |
Files |
Array with elements of information about the file downloaded from this IP |
|
bot_urls |
Bot urls |
Array with top10 URLs |
|
APT URL Data Feed
|
port |
Port |
The port through which the attack took place |
detection_date |
Detection date |
The date of detection of the attack to which the file belongs |
|
publication_name |
Publication name |
The name of the attack to which the file belongs |
|
api_publication_id |
Publication id |
ID of the publication to download the report from KL TIP |
|
actors |
Actors |
Names of criminal groups associated with the use of indicators |
|
industries |
Industries |
List of industries targeted by the attack |
|
Malicious URL Data Feed Malicious URL Exact Data Feed
|
IP |
IP |
Top 10 IP addresses into which the domain has resolved |
whois |
WhoIs |
Available whois information |
|
files |
Files |
Array with elements of information about the file downloaded from this IP |
|
Mobile Botnet C&C URL Data Feed
|
urls |
URL |
Array with top10 bot URLs |
IP |
IP |
Top 10 IP addresses into which the domain of this Botnet C&C has resolved |
|
whois |
WhoIs |
Available whois information |
|
files |
Files |
Array with elements of information about the file downloaded from this IP |
|
IOT URL Data Feed
|
protocol |
Protocol |
Top 100 protocols that attackers used to access the resource and download malware |
port |
Ports |
Top 100 ports through which attackers downloaded malware from this resource |
|
IP |
IP |
Top 10 IP addresses into which the domain has resolved |
|
files |
Files |
Array with elements of information about the file downloaded from this IP |
|
Phishing URL Data Feed Phishing URL Exact Data Feed
|
industries |
Industries |
List of industries targeted by the attack |
IP |
IP |
Top 10 IP addresses into which the domain has resolved |
|
whois |
WhoIs |
Domain Information |
|
stolen_data_type |
Stolen data type |
Types of data that want to steal |
|
targeted_organization |
Targeted organization |
Organizations targeted by the attack |
|
phishing_kit |
Phishing kit |
Used fishing kit |
|
attack_type |
Attack type |
A list of the types of attacks that this URL is associated with |
|
Ransomware URL Data Feed
|
IP |
IP |
Top 10 IP addresses into which the domain of this Botnet C&C has resolved |
whois |
WhoIs |
Available whois information |
|
files |
Files |
Array with elements of information about the file downloaded from this IP |
|
Malicious Hash Data Feed Demo Malicious Hash Data Feed
|
file_size |
File size |
File size in bytes |
file_type |
File type |
File type |
|
file_names |
File names |
File names |
|
IP |
IP |
Top 10 IP addresses from which the file was swung |
|
mitre |
Mitre |
A list of techniques, sub-techniques and tactics that are used by the file |
|
urls |
URL |
Top 10 URLs from which the file was downloaded |
|
APT Hash Data Feed
|
detection_date |
Detection date |
The date of detection of the attack to which the file belongs |
publication_name |
Publication name |
The name of the attack to which the file belongs |
|
api_publication_id |
Publication id |
ID of the publication to download the report from KL TIP |
|
actors |
Actors |
Names of criminal groups associated with the use of indicators |
|
industries |
Industries |
List of industries targeted by the attack |
|
mitre |
Mitre |
A list of techniques, sub-techniques and tactics that are used by the file |
|
ICS Hash Data Feed
|
file_size |
File size |
File size in bytes |
file_names |
File names |
File names |
|
IP |
IP |
Top 10 URLs from which the file was downloaded |
|
urls |
URL |
Top 10 URLs from which the file was downloaded |
|
Mobile Malicious Hash Data Feed |
file_size |
File size |
File size in bytes |
ICS Vulnerability Data Feed
|
publication_date |
Publication date |
Date of vulnerability detection |
description |
Description |
A general description. There may be several descriptions from various sources. Check the Default checkbox above to make this description the default |
|
vendor |
Vendor |
Vendor whose products the vulnerability was found in |
|
affected_products |
Affected products |
Vulnerable versions of the product |
|
mitigations |
Mitigations |
Recommendations for fixing vulnerabilities |
|
advisory_urls |
Advisory urls |
Links to blogs/advisory/vendor statements that mention the vulnerability |
|
cve |
CVE |
Array of CVE threats |
|
patches |
Patches |
List of patches released by vulnerable products that close the vulnerability |
|
Vulnerability Data Feed
|
detection_date |
Detection date |
Date of vulnerability detection |
description |
Description |
A general description. There may be several descriptions from various sources. Check the Default checkbox above to make this description the default |
|
vendors |
Vendors |
Vendors in whose products the vulnerability was found |
|
affected_products |
Affected products |
Vulnerable versions of the product |
|
solution_description |
Solution description |
Description of the solution to the vulnerability problem |
|
solution_urls |
Solution urls |
Links to download updated versions of software with closed vulnerabilities |
|
advisory_urls |
Advisory urls |
Links to blogs/advisory/vendor statements that mention the vulnerability |
|
impacts |
Impacts |
Abbreviations describing the impact on the system when exploiting a vulnerability |
|
cve |
CVE |
Array of CVE threats |
|
patches |
Patches |
List of patches released by vulnerable products that close the vulnerability |
Feeds and context fields
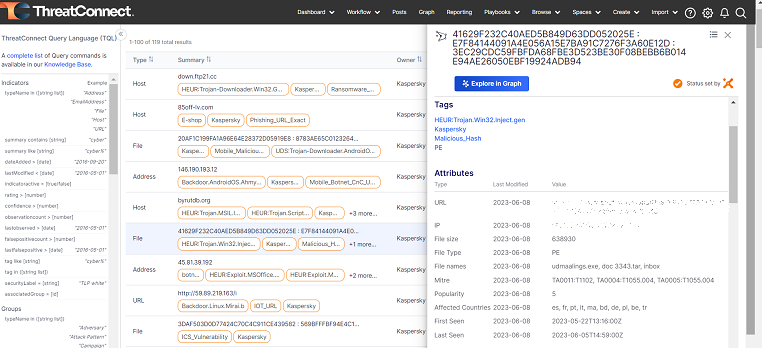
Example of context fields
Page top