Data traffic scheme for Corporate App Catalog in DMZ
The figure below shows data traffic when Corporate App Catalog is in the demilitarized zone (DMZ) and the managed devices, including mobile devices, are on the internet.
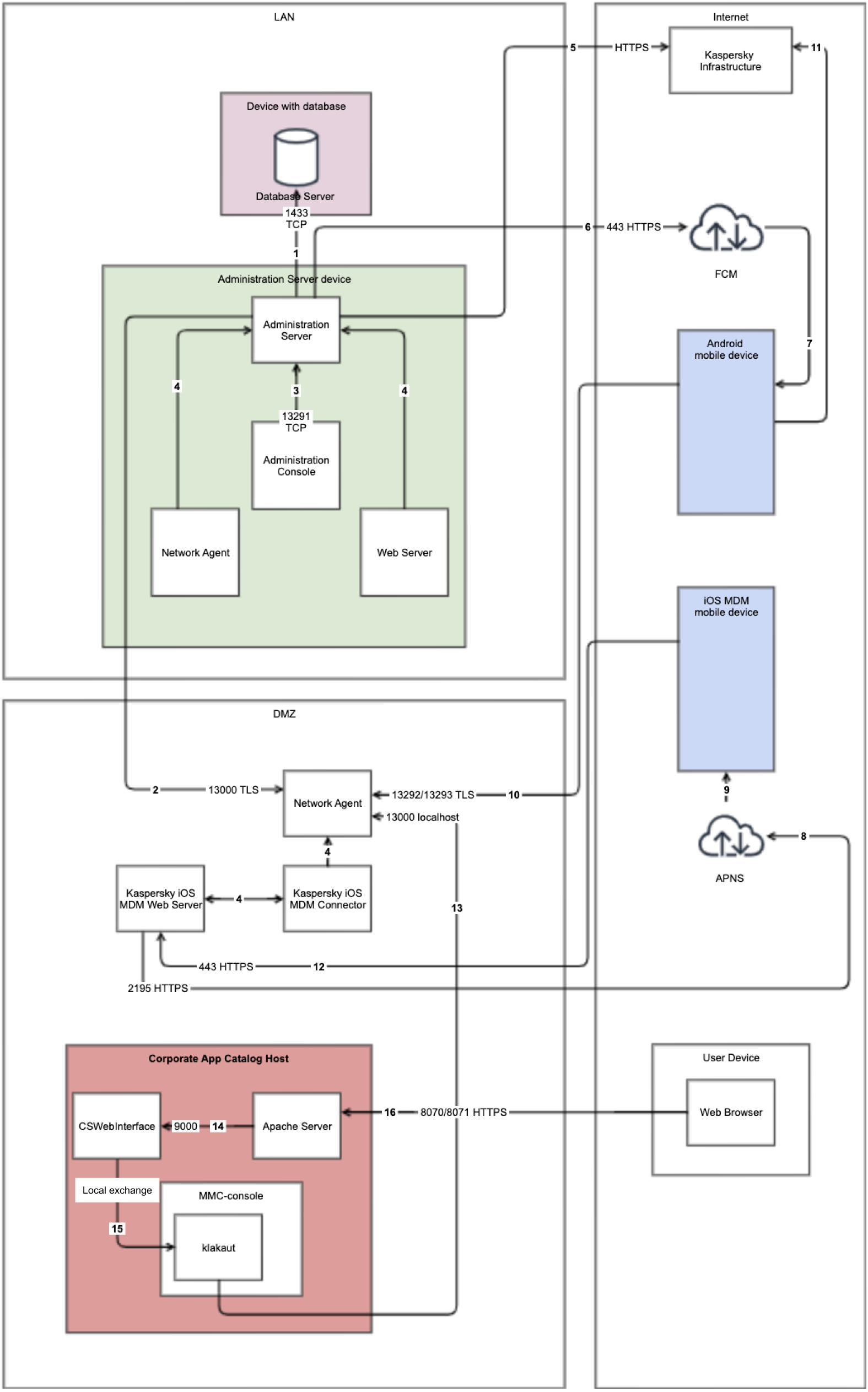
Managed devices connected to Administration Server through Corporate App Catalog and a connection gateway
In this figure, the managed devices are connected to the Administration Server though Corporate App Catalog and a connection gateway that are located in the DMZ.
For more detailed scheme, please refer to Kaspersky Security Center Help.
The arrows indicate the initiation of traffic: each arrow points from a device that initiates the connection to the device that "answers" the call. The number of the port and the name of the protocol used for data transfer are provided. Each arrow has a number label, and details about the corresponding data traffic are as follows:
- Administration Server sends data to the database. If you install the Administration Server and the database on different devices, you must make available the necessary ports on the device where the database is located (for example, port 3306 for MySQL Server and MariaDB Server, or port 1433 for Microsoft SQL Server). Please refer to the DBMS documentation for the relevant information.
- The Administration Server receives connection from Network Agents and from secondary Administration Servers through SSL port 13000.
If you used an earlier version of Kaspersky Security Center, the Administration Server on your network can receive connection from Network Agents through non-SSL port 14000. Kaspersky Security Center also supports connection of Network Agents through port 14000, although using SSL port 13000 is recommended.
The distribution point was called "Update agent" in earlier versions of Kaspersky Security Center.
- Data from MMC-based Administration Console is transferred to the Administration Server through port 13291. The Administration Console can be installed on the same or on a different device.
- Applications on a single device exchange local traffic (either on the Administration Server or on a managed device). No external ports have to be opened.
- Data from the Administration Server to the Kaspersky servers (such as KSN data or information about licenses) and data from the Kaspersky servers to the Administration Server (such as application updates and anti-malware database updates) are transferred using the HTTPS protocol.
If you do not want your Administration Server to have access to the internet, you must manage this data manually.
- For Android mobile devices only: data from the Administration Server is transferred to Google servers. This connection is used to notify Android mobile devices that they are required to connect to the Administration Server. Then push notifications are sent to the mobile devices.
- For Android mobile devices only: push notifications from Google servers are sent to the mobile device. This connection is used to notify mobile devices that they are required to connect to the Administration Server.
- For iOS mobile devices only: data from the iOS MDM Server is transferred to Apple Push Notification servers. Then push notifications are sent to the mobile devices.
- For iOS mobile devices only: push notifications are sent from Apple servers to the mobile device. This connection is used to notify iOS mobile devices that they are required to connect to the Administration Server.
- For mobile devices only: data from the managed application is transferred to the Administration Server (or to the connection gateway) through TLS port 13292 / 13293—directly or through a Microsoft Forefront Threat Management Gateway (TMG).
- For mobile devices only: data from the mobile device is transferred to the Kaspersky infrastructure.
If a mobile device does not have internet access, the data is transferred to Administration Server through port 17100, and the Administration Server sends it to the Kaspersky infrastructure; however, this scenario applies very rarely.
- For iOS mobile devices only: data from the mobile device is transferred through TLS port 443 to the iOS MDM Server, which is on the same device as the Administration Server or on the connection gateway.
- For Corporate App Catalog usage only: the klakaut utility connects to the Administration Server through the connection gateway installed in DMZ.
- For Corporate App Catalog usage only: the Corporate App Catalog service receives connections from the Apache server.
- For Corporate App Catalog usage only: Corporate App Catalog connects to the klakaut utility that is included in MMC-based Administration Console distribution kit.
- Corporate App Catalog and Corporate App Catalog Management Console is opened in a browser. The data from the browser installed on the administrator or user device is transferred to the Apache web server through TLS port 8070 / 8071.
Port 8070 is used for connecting company employees and administrators to Corporate App Catalog via the browser. Port 8071 is used for connecting company administrators to Corporate App Catalog Management Console via the browser.