Retrospective scan settings
Kaspersky CyberTrace allows you to save events potentially containing undetected indicators, perform a retrospective scan of these events according to the indicators from the updated feeds, and then view retrospective scan results. This section explains how to configure Kaspersky CyberTrace for using the retrospective scan.
The events are not saved in full, only the selected fields are saved for use in the retrospective scan.
The Retrospective scan tab allows you to do the following:
- Enable or disable the retrospective scan.
- View the current size of saved events.
- Remove saved events.
Saved events cannot be removed when the retrospective scan is in progress. If you want to disable the retrospective scan and removed the saved events, you must wait until the current retroscan task is finished.
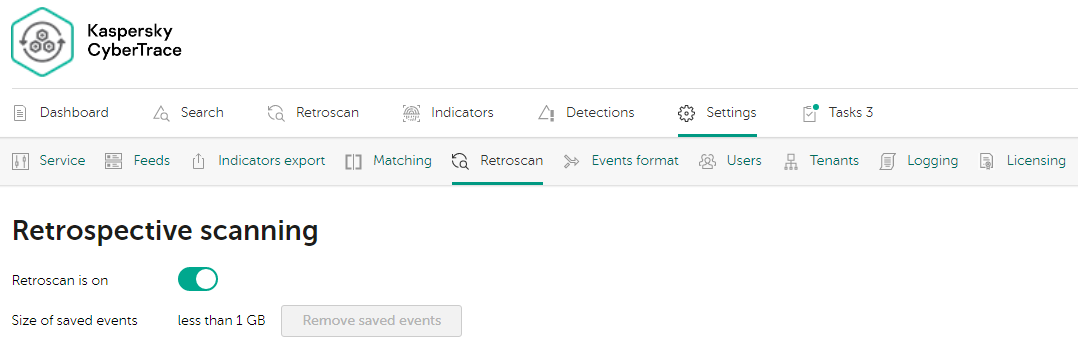
Retrospective scan tab
- On the General settings tab, manage the following settings:
- Set the frequency of the scheduled retrospective scan task or disable the scan on schedule. If Every month is selected, retrospective scan starts every 30 days.
- Enable or disable the size limit for events that must be saved for the retrospective scan.
- Set the maximum size of events (in gigabytes) that must be saved for the retrospective scan.
- Set how long (in days) the events used for the retrospective scan must be stored.
- Set how long (in days) the results of the retrospective scan must be stored.
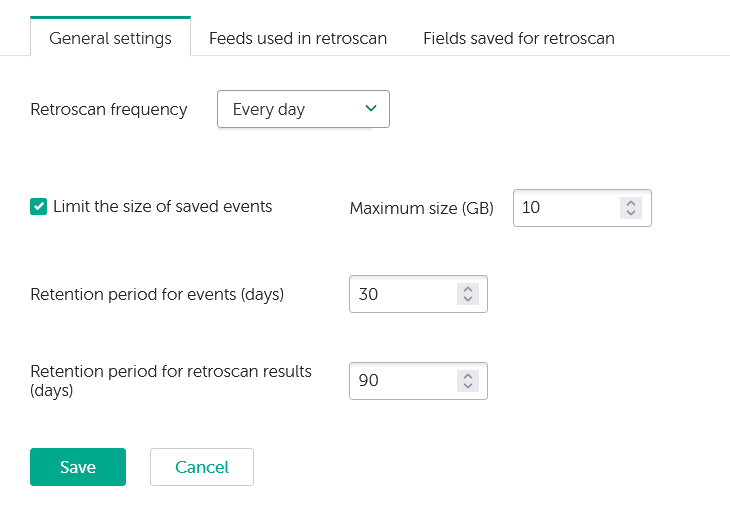
General settings tab
- On the Feeds used in retroscan tab, enable or disable feeds that must be used in the retrospective scan.

Feeds used in retroscan tab
- On the Fields saved for retroscan tab, configure the following settings:
- Enable or disable saving events related to a specific tenant for use in the retrospective scan.
If you exclude a tenant from the retrospective scan, the regular expressions contained in this tenant become unavailable for selection.
- Select regular expressions contained in a tenant for use in the retrospective scan.
You must select at least one regular expression.
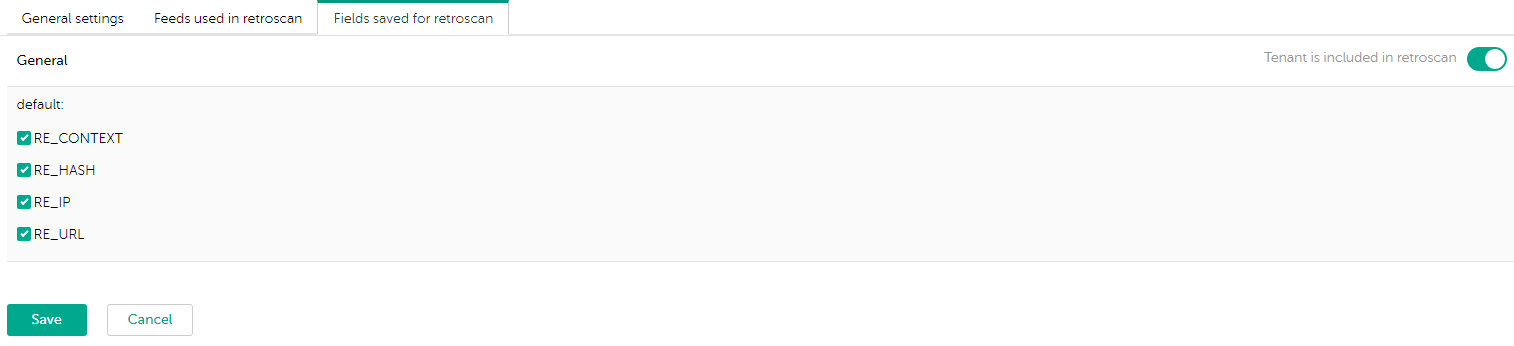
Fields saved for retroscan tab
- Enable or disable saving events related to a specific tenant for use in the retrospective scan.
Recommendations on retrospective scan settings
Retrospective scan is a resource-consuming functionality that may take a long time when checking huge amounts of data. For more efficient use of retrospective scan without looking up indicators for all incoming events, we recommend to single out the events that will be retrospectively scanned to the separate event source.
To add a source for retrospective scan:
- On the Settings>Matching tab, click Add new event source.
- Add a regular expression to single out an event (for example, for Syslog message format it could be
^\<d+\>.*$). - Click Next.
The window with properties of the newly added source appears.
- On the Regular expressions tab, add indicator types that may come from this source.
- Set the rule name typical for this source and indicator type (for example,
RE_IP_NEW_SIEM).For regular expressions for various event sources, see the "Regular expressions for popular event sources" section.
- Click OK to make sure that the new source is successfully added.
- Go to Settings>Retroscan, and then select the Fields saved for retroscan tab.
- Enable only those sources and their regular expressions that are necessary for retrospective scan.
- Save changes.
>Service alerts related to retrospective scan
Kaspersky CyberTrace generates the following service alerts to inform you about the retrospective scan process:
KL_ALERT_RetroScanCompletedKL_ALERT_RetroScanErrorKL_ALERT_RetroScanStorageExceeded
For details about the above alerts, see the "Alert events sent by Kaspersky CyberTrace" section.
Page top