Configuring Kaspersky CyberTrace for integration with McAfee Enterprise Security Manager
This section describes how to configure Kaspersky CyberTrace for integration with McAfee ESM.
To configure Kaspersky CyberTrace for integration with McAfee ESM:
- Download Kaspersky CyberTrace from https://support.kaspersky.com/datafeeds/download/15920.
- Install Kaspersky CyberTrace.
- In Linux, Kaspersky CyberTrace is installed to the
/opt/kaspersky/ktfsdirectory. - For the Windows installation, the installation directory is hereinafter referred to as
%CyberTrace_installDir%.
- In Linux, Kaspersky CyberTrace is installed to the
- When you sign in to Kaspersky CyberTrace Web UI for the first time, the Initial Setup Wizard opens. Follow the onscreen instructions. In particular, define the following settings:
- At the Proxy settings step of the wizard, If necessary, specify the proxy server connection parameters.
- At the Data management settings step of the wizard, specify the following:
- Under SIEM system, select Other.
- Under Incoming events, specify IP address and port on which Kaspersky CyberTrace will listen for incoming events.
- Under Detection alerts, specify IP address and port of McAfee ESM to which Kaspersky CyberTrace will send detection alerts and service alerts.
For McAfee ESM, the port is 514.
- On the Settings → Event sources page, click the
(Edit) button next to the Default event source, select the Regular expressions tab, and then specify the following regular expressions:
Regular expressions for integration with McAfee ESM
Indicator type
Rule name
Regular expression
Additional options
CONTEXT
Device
deviceExternalId\=(.*?)\s
CONTEXT
DeviceAction
act\=(.*?)\s
CONTEXT
DeviceIp
deviceTranslatedAddress\=(.*?)\s
HASH
RE_HASH
([\da-fA-F]{32,64})
Extract all: True
IP
RE_IP
dst\=(.*?)\s
URL
RE_URL
(?:\:\/\/)((?:\S+(?::\S*)?+@)?(?:(?:(?:[a-z\x{00a1}-\x{ffff}0-9]+-*)*[a-z\x{00a1}-\x{ffff}0-9]*)(?:\.(?:[a-z\x{00a1}-\x{ffff}0-9]+-)*+[a-z\x{00a1}-\x{ffff}0-9]++)*(?:\.(?:[a-z\x{00a1}-\x{ffff}\-0-9]{2,}+)))(?:\.*:\d{2,5})?+(?:\.*\/[^\s\"\<\>]*+)?+)
Extract all: True
IP
SRC_IP
src\=(.*?)\s
CONTEXT
UserName
duser\=(.*?)\s
- On the Normalization rules tab, enable the Apply normalization rules toggle switch, and then specify the following replacement rule:
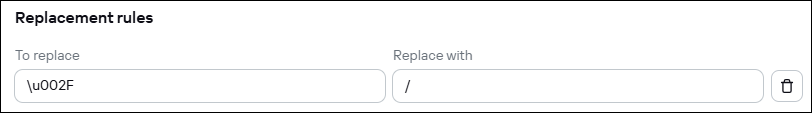
Replacement rule for integration with McAfee ESM
- Save the changes.
- Select Settings → Service alerts, and then specify the following formats:
Service alerts format for integration with McAfee ESM
Field
Value
Format of service alerts
Kaspersky CyberTrace Service Event| date=%Date% alert=%Alert% msg:%RecordContext%Format of records context
%ParamName%=%ParamValue%Note the space before
%ParamName%.Save the changes.
- Select Settings → Detection alerts, and then specify the following formats:
Detection alerts format for integration with McAfee ESM
Field
Value
Format → Alert format
Kaspersky CyberTrace Detection Event| date=%Date% reason=%Category% detected=%MatchedIndicator% act=%DeviceAction% dst=%RE_IP% src=%SRC_IP% hash=%RE_HASH% request=%RE_URL% dvc=%DeviceIp% sourceServiceName=%Device% suser=%UserName% msg:%RecordContext%Context → Actionable fields
%ParamName%:%ParamValue%Note the space before
%ParamName%.Save the changes.