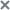Viewing information about an IOC file
To view IOC file details:
- In the window of the application web interface, select the Custom rules section, IOC subsection.
This opens the table of IOC files.
- Select the IOC file for which you want to view information.
This opens a window containing information about the IOC file.
The window contains the following information:
- Clicking the Find alerts link opens the Alerts section with the filter condition populated with the name of your selected IOC file.
- Clicking the Find events link opens the Threat Hunting section with the search condition populated with indicators of compromise of your selected IOC file.
- Clicking the Download link opens the IOC file download window.
- Autoscan—The IOC file is used when automatically scanning hosts with the Endpoint Agent component.
- Name—Name of the IOC file.
- Importance—Importance level that must be assigned to an alert generated using this IOC file.
The importance level can have one of the following values:
 – Low importance.
– Low importance. – Medium importance.
– Medium importance. – High importance.
– High importance.
- Apply to—Displays the name of the tenant and the names of servers associated with events scanned based on this IOC file (in distributed solution and multitenancy mode).
- XML—Displays the IOC file contents in XML format.