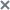Viewing the table of objects that were placed in Storage
The table of objects placed in Storage is in the Storage section, Files subsection of the application web interface window.
The table of objects placed in Storage contains the following information:
- Type is the method by which the object was placed in Storage.
The following methods are possible:
 — The object was placed in Storage in one of the following ways:
— The object was placed in Storage in one of the following ways:- The Get file task was run.
- A copy was received of an object that was quarantined on hosts with the Endpoint Agent component (in the Storage section, Quarantine subsection, Get file from quarantine action was selected in the menu for the link with the directory of the object).
 — The object was placed in Storage in one of the following ways:
— The object was placed in Storage in one of the following ways:- The Get forensics task was run.
- The Get process memory dump task was run.
- The Get registry key task was run.
- The Get NTFS metafiles task was run.
 — The object was manually downloaded by the user in the Storage section, Files subsection.
— The object was manually downloaded by the user in the Storage section, Files subsection.
- Object—Information about the object. For example, the file name or file path.
- Scan results—Object scan result.
The scan result is displayed as one of the following values:
- Not detected—As a result of a scan, the application did not detect signs of a targeted attack, probably infected objects, or suspicious activity.
- Error—Object scan ended with an error.
- In process—Object scan has not yet completed.
- Not scanned—Object was not sent to be scanned.
- Detected—As a result of a scan, the application detected signs of a targeted attack, a probably infected object, or suspicious activity.
- Servers is the name of the server with the PCN or SCN role. The host from which the object was received is connected to this server.
This column is displayed if you are using the distributed solution and multitenancy mode.
- Source—IP address or name of the host from which the object was received, or the name of the user account that uploaded the object.
- Time stored—Date and time when the object was placed in Storage.
- Actions—Actions that can be performed with the object. The following actions are available:
 — delete an object from Storage.
— delete an object from Storage. — send the object in Storage for scanning by the Anti-Malware Engine, YARA, and Sandbox technologies.
— send the object in Storage for scanning by the Anti-Malware Engine, YARA, and Sandbox technologies. — download the object from Storage to your computer.
— download the object from Storage to your computer.
Clicking the link with the file name or file path opens a list in which you can select one of the following actions:
- Filter by this value.
- Exclude from filter.
- Download.
- Send file for scanning.
- Find events:
- File path.
- MD5.
- SHA256.
- Find alerts:
- File path.
- MD5.
- SHA256.
- Copy value to clipboard.
Clicking the link with the host name opens a list in which you can select one of the following actions:
- Filter by this value.
- Exclude from filter.
- Find events.
- Find alerts.
- Copy value to clipboard.