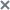Searching events in design mode
To define event search conditions in builder mode:
- Select the Threat Hunting section, Builder tab in the application web interface window.
This opens the event search form.
- In the drop-down list, select an event search criterion.
You can view a description of the event search criteria in the Event search criteria section.
- In the drop-down list, select an operator.
For a list of available operators, see the Operators section.
Each type of value of the field has its own relevant set of operators. For example, when the EventType field value type is selected, the = and != operators will be available.
- Depending on the selected type of field value, perform one of the following actions:
- In the field, specify one or several characters by which you want to perform an event search.
- In the drop-down list, select the field value option by which you want to perform an event search.
For example, to search for a full match based on a user name, enter the user name.
- If you want to add a new condition, use the AND or OR logical operator and repeat the necessary actions for adding a condition.
- If you want to add a group of conditions, click the Group button and repeat the actions necessary for adding conditions.
- If you want to delete a group of conditions, click the Remove group button.
- If you want to search events that occurred during a specific period, in the Any time drop-down list select one of the following event search periods:
- Any time if you want the table to display events found as far back as the records go.
- Last hour if you want the table to display events that were found during the last hour.
- Last day if you want the table to display events found during the last day.
- Custom range if you want the table to display events found during the period you specify.
- If you selected Custom range:
- In the calendar that opens, specify the start and end dates of the event display range.
- Click Apply.
The calendar closes.
- Click Search.
The table of events that satisfy the search criteria is displayed.
If you are using the distributed solution and multitenancy mode, found events are grouped in tiers: Server – Tenant names – Server names.
- Click the name of the server for which you want to view events.
The host table of the selected server is displayed. Event grouping levels are displayed above the table.