Privilege Separation pattern
Description
The Privilege Separation pattern involves the use of non-privileged isolated system modules for interaction with clients (other modules or users) that do not have any privileges. The purpose of the Privilege Separation pattern is to reduce the amount of code that is executed with special privileges without impacting or restricting application functionality.
The Privilege Separation pattern is a special case of the Distrustful Decomposition pattern.
Example
An unauthenticated user connects to a system that has functions requiring elevated privileges.
Context
The system has components with a large attack surface due to their high number of connections with unsafe sources and/or a complicated, potentially error-prone implementation.
Problem
When a client with unknown privileges interacts with a privileged component of the system, there are risks that the data and functionality accessible to that component could be compromised.
Solution
Interactions with unsafe clients must be conducted only through specially allocated components that have no privileges. The Privilege Separation pattern does not modify system functionality. Instead, it merely separates functionality into components with different privileges.
Operation
Pattern operations can be divided into two phases:
- Pre-Authentication. The client is not yet authenticated. It sends a request to a privileged master process. The master process creates a child process with no privileges (and no access to the file system). This child process performs client authentication.
- Post-Authentication. The client is authenticated and authorized. The privileged master process creates a new child process that has privileges corresponding to the permissions of the client. This process is responsible for all subsequent interaction with the client.
Recommendations on implementation in KasperskyOS
At the Pre-Authentication phase, the master process can save the state of each non-privileged process in the form of a finite-state machine and change the state of the finite-state machine during authentication.
Requests from child processes to the master process are performed using standard IPC mechanisms. However, interaction control is conducted using the Kaspersky Security Module.
Impacts
If attackers gain control of a non-privileged process, they will not gain access to any privileged functions or data. If attackers gain control of an authorized process, they will obtain only the privileges of this process.
In addition, code that is organized in this manner is easier to check and test. You just have to pay special attention to the functionality that operates with elevated privileges.
Implementation examples
Example of a Privilege Separation pattern implementation: Device Access example.
Sources of information
The Privilege Separation pattern is described in detail in the following resources:
- Chad Dougherty, Kirk Sayre, Robert C. Seacord, David Svoboda, Kazuya Togashi (JPCERT/CC), "Secure Design Patterns" (March-October 2009). Software Engineering Institute. https://resources.sei.cmu.edu/asset_files/TechnicalReport/2009_005_001_15110.pdf
- Dangler, Jeremiah Y., "Categorization of Security Design Patterns" (2013). Electronic Theses and Dissertations. Paper 1119. https://dc.etsu.edu/etd/1119
Device Access example
The Device Access example demonstrates use of the Privilege Separation pattern.
Example architecture
The example contains the following three programs: Device, LoginManager and Storage.
In this example, the Device program queries the Storage program to receive information and queries the LoginManager program for authorization.
The Device program obtains access to the Storage program after successful authorization.
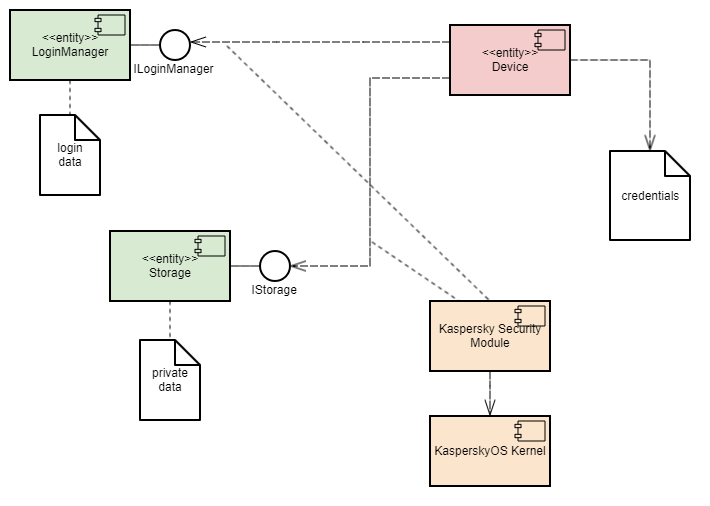
This example demonstrates the capability to separate the authorization logic and the data access logic into independent components. This separation guarantees that data access can be opened only after successful authorization. The security module monitors whether authorization was successfully completed. This architecture also enables independent development and testing of the authorization logic and the data access provision logic.
A security policy in the Device Access example has the following characteristics:
- The
Deviceprogram has the capability to query theLoginManagerprogram for authorization. - Calls of the
GetInfo()method of theStorageprogram are managed by methods of the Flow security model:- The finite-state machine described in the
sessionobject configuration has two states:unauthenticatedandauthenticated. - The initial state is
unauthenticated. - Only transitions from
unauthenticatedtoauthenticatedand vice versa are allowed. - The
sessionobject is created when theDeviceprogram is started. - When the
Deviceprogram successfully calls theLogin()method of theLoginManagerprogram, the state of thesessionobject changes toauthenticated. - When the
Deviceprogram successfully calls theLogout()method of theLoginManagerprogram, the state of thesessionobject changes tounauthenticated. - When the
Deviceprogram calls theGetInfo()method of theStorageprogram, the current state of thesessionobject is verified. The call is allowed only if the current state of the object isauthenticated.
- The finite-state machine described in the
Example files
The code of the example and build scripts are available at the following path:
/opt/KasperskyOS-Community-Edition-<version>/examples/device_access
Building and running example
See Building and running examples section.
Page top