GetThreats. Obtaining data on detected threats
Receive a list of detected threats (Threats report). This report contains information about threats and virus activity during the last 30 days prior to creating the report.
Command syntax
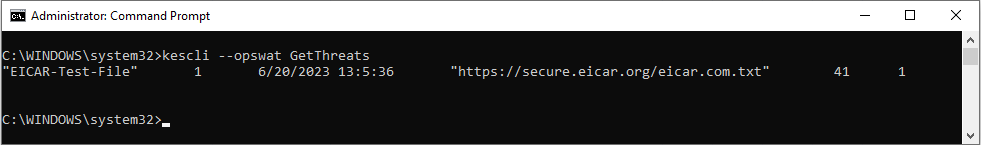
kescli --opswat GetThreats
When this command is executed, Kaspersky Endpoint Security will send a response in the following format:
<name of detected object> <type of object> <detection date and time> <path to file> <action on threat detection> <threat danger level>
Managing the application from the command line
Object type |
|
|
Not known ( |
|
Viruses ( |
|
Trojan programs ( |
|
Malicious programs ( |
|
Advertisement programs ( |
|
Auto-dialer programs ( |
|
Applications that could be used by a cybercriminal to harm the user's computer or data ( |
|
Packed objects whose packing method may be used to protect malicious code ( |
|
Unknown objects ( |
|
Known applications ( |
|
Concealed files ( |
|
Applications requiring attention ( |
|
Anomalous behavior ( |
|
Not determined ( |
|
Ad banners ( |
|
Network attack ( |
|
Registry access ( |
|
Suspicious activity ( |
|
Vulnerabilities ( |
|
|
|
Unwanted email attachment ( |
|
Malware detected by Kaspersky Security Network ( |
|
Unknown link ( |
|
Other malware ( |
Action on threat detection |
|
|
Not known ( |
|
Threat was remediated ( |
|
Object was infected and has not been disinfected ( |
|
Object is in an archive and has not been disinfected ( |
|
Object has been disinfected ( |
|
Object has not been disinfected ( |
|
Object was deleted ( |
|
A backup copy of the object was created ( |
|
Object was moved to Backup ( |
|
Object was deleted on computer restart ( |
|
Object was disinfected on computer restart ( |
|
Object was moved to Backup by a user ( |
|
Object was added to exclusions ( |
|
Object was moved to Backup on computer restart ( |
|
False positive ( |
|
Process was terminated ( |
|
Object was not detected ( |
|
Cannot resolve the threat ( |
|
Object was restored ( |
|
Object was created as a result of threat activity ( |
|
Object was restored on computer restart ( |
|
Object was not processed ( |
Threat danger level |
|
|
Unknown |
|
High |
|
Medium scan |
|
Low |
|
Info (less than Low) |