Intrusion detection tab
On the Intrusion detection tab (see the figure below), you can manage sets of Intrusion Detection rules and additional Intrusion Detection methods.
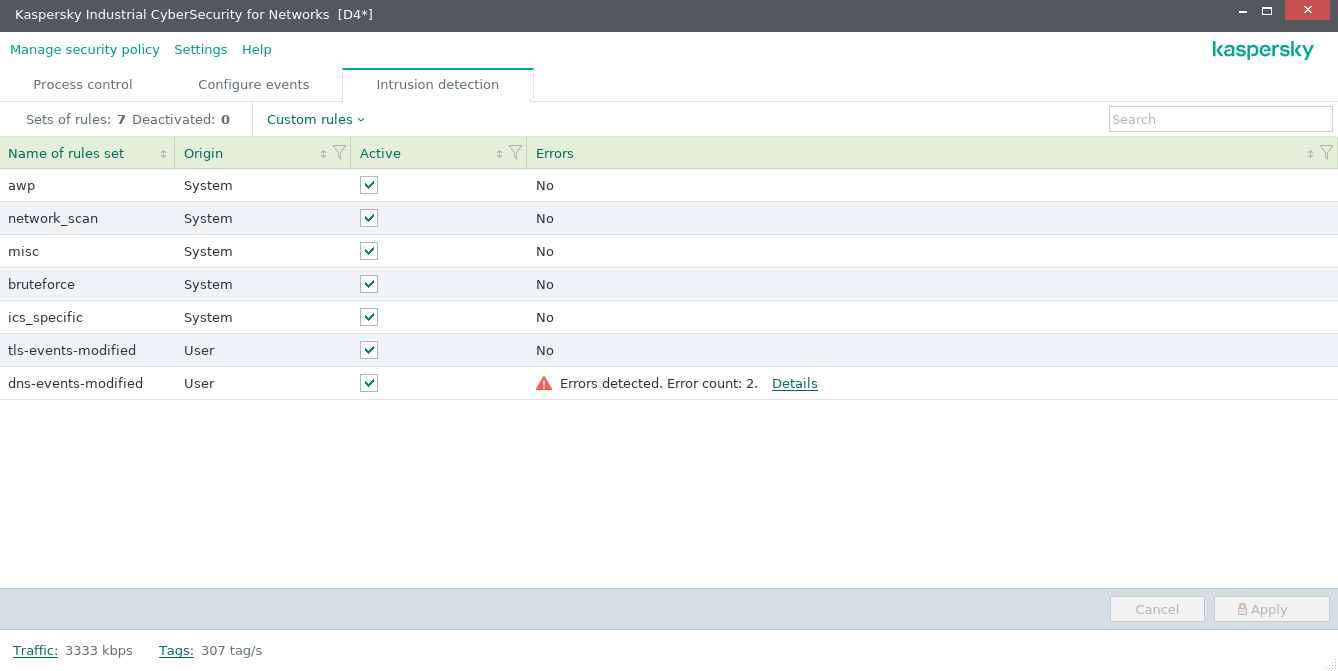
Intrusion detection tab
Above the table containing the sets of Intrusion Detection rules, a toolbar provides the following management elements and data fields:
- Sets of rules – total number of rule sets in the table. The sets of rules include Intrusion Detection rules grouped by certain attributes. System sets and custom sets of rules can be used in the application.
- Deactivated – number of inactive sets of rules in the table.
- Custom rules – menu for selecting actions to take on custom sets of rules. You can use the menu items to load custom sets of rules into the application or remove all custom sets of rules.
- Search field – lets you enter a query to search by values in the Name of rules set column.
The table containing the sets of Intrusion Detection rules is located in the main part of the tab. The table columns display the following information about sets of rules:
- Name of rules set – name of the set of Intrusion Detection rules. For custom rule sets, the name matches the name of the file from which the rule set was loaded (without the RULES extension).
- Origin – value determining the type of rule set. Two values are available: System (for the system set of rules) or User (for the custom set of rules).
- Active – field for enabling and disabling rules. If the check box is selected, the rule set is active (rules from the rule set are applied when intrusions are detected). If the check box is cleared, the rule set is inactive (rules from the rule set are not applied). The state of rule sets is modified after the changes are applied.
- Errors – information about the presence of errors in rules. If errors have not been detected, the No value is displayed. If there are errors, the number of detected errors is displayed. You can open a window containing additional information about errors by clicking the Details link (this link appears if there are errors).
The lower part of the Intrusion detection tab contains buttons for canceling and applying changes to the state of sets of rules (in the Active column).
Page top