Starting file execution
Before executing a file in Kaspersky Research Sandbox, you must upload it and select execution options.
To execute a file in Kaspersky Research Sandbox:
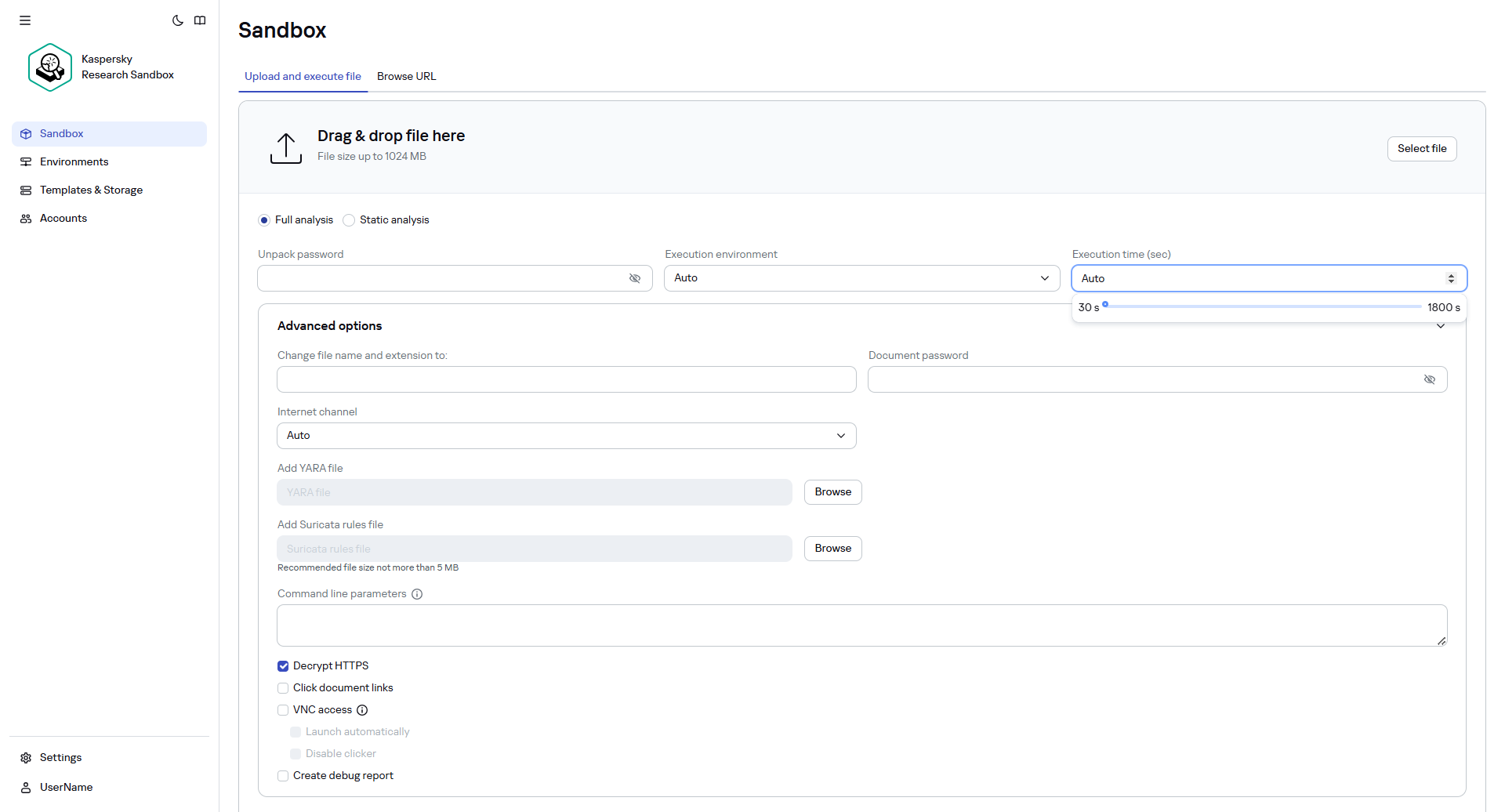
- On the Sandbox page of Kaspersky Research Sandbox, on the Upload and execute file tab, select an object that you want to execute in one of the following ways:
- Click the Select file button and select the required object in the window that opens.
- Drag and drop the required object to the drop zone. The drop zone is displayed when you start dragging an object.
When the object is selected, its file name and size (in megabytes) are displayed.
The maximum size of an object that can be uploaded is 1024 MB.
If you upload a packed object, make sure it contains less than 1000 files. Kaspersky Research Sandbox scans all files in the object, but only 1000 files are available for downloading. It is recommended to execute objects that contain less than 1000 files.
If necessary, click the
 button to remove the selected file.
button to remove the selected file. - Select the analysis type:
- Full analysis—to perform both static and dynamic analysis. This option is selected by default.
- Static analysis—to perform only static analysis. If you select this option, only the Unpack password parameter and adding YARA rules file are available (see below in this procedure).
- If you want to execute an archive, make sure its format is supported.
Kaspersky Research Sandbox supports multi-layer decompression for archives. To perform dynamic analysis in automatic mode (without using VNC), an archive must contain only one file that needs to be executed in the virtual environment. If necessary, you can place a sample in nested archives (up to 10 layers).
To execute a password-protected archive, enter a password for the archive in the Unpack password field. If you do not enter a password for a password-protected archive, Kaspersky Research Sandbox tries to unpack an archive using default passwords.
Click the eye icon to show or hide the password.
- In the Execution environment drop-down list, select the operating system that you want to use as an execution environment.
The recommended execution environment (Kaspersky Research Sandbox automatically determines the optimal operating system according to type of uploaded file) is selected by default (Auto).
If you have successfully deployed custom execution environments, they are also displayed in the list of available environments in the Custom environments section.
You can use Microsoft Windows 10 x64 with disabled AMSI if Windows 10 image is installed.
To install Microsoft Windows 10 image, please contact your administrator.
- In the Execution time (sec) field, specify the object execution time (in seconds) by using the slider or entering the required number.
By default, the Auto value is selected—Kaspersky Research Sandbox automatically determines the optimal execution time according to the type of uploaded file.
You can specify an execution time from 30 to 1800 seconds (30 minutes). If necessary, click the Reset to auto button to specify the default value Auto.
An uploaded object will only be executed in the selected environment during the specified execution time. The specified time does not include the time required for analysis and displaying results.
- If necessary, click Advanced options and specify the following settings:
- In the Change file name and extension to field, you can specify another name and extension for the uploaded file. In this case, Kaspersky Research Sandbox attempts to execute the file according to the specified extension. Also, Kaspersky Research Sandbox determines the type of file after uploading to Sandbox, and processes the file accordingly. On the report page, the extension determined by Kaspersky Research Sandbox is displayed.
Most characters can be used to specify a file extension, with the exception of reserved characters (<, >, :, ", /, \, |, ?, *).
You can enter up to 254 characters to specify a file name and extension.
If the file extension is not specified, Kaspersky Research Sandbox attempts to define it automatically, and the file will be executed with the extension defined by Kaspersky Research Sandbox.
For more details about file types, refer to section Automatically detected file types.
- You can use Kaspersky Research Sandbox to open password-protected documents during execution in the Sandbox. To do this, enter the password in the Document password field. This field is empty by default.
The Document password field is available only for Windows-based execution environments.
Click the eye icon to show or hide the password.
- To specify a name of a network channel that the object will use to access the internet, select one of the following options in the Internet channel drop-down list:
- Auto—Select this option to define a network channel automatically.
- Tarpit—Select this option to emulate network availability during file execution, without real access to the internet. When you select this option, a connection from the virtual machine to any host is emulated. The Tarpit channel simplifies emulation of the following protocols: raw TCP/UDP, HTTP(S), ICMP, DNS.
- Other options in the list are set during Kaspersky Research Sandbox installation. For more details about available options, contact your administrator.
You cannot edit this option if a network channel was specified during template deployment.
- If necessary, click Browse near the Add YARA file entry field to select the file that contains YARA rules.
Kaspersky Research Sandbox only supports YARA rule modules that are involved in static analysis of a file and its contents. It does not support behavioral characteristics. Specifically, the cuckoo and console modules are not supported.
- If necessary, click Browse near the Add Suricata rules file entry field to select the file that contains Suricata rules used to scan a PCAP file.
The recommended file size is 5 MB. If the Suricata rule file size exceeds 16 MB, we recommend that you split it into several files (up to 5 MB in size) and upload them to the task sequentially.
- Kaspersky Research Sandbox can start object execution with specific parameters. To do this, enter the required parameters in the Command line parameters field.
You can use Windows environment variables by placing the % sign in front of and after the variable name (for example,
%SYSTEMROOT%). By default, environment variables are expanded on the user's host, before transferring and executing the object in the Sandbox. To transfer environment variables to the Sandbox as is, without expansion, use the%sign (for example,%SYSTEMROOT%).The command line may contain a variable
$samplethat will be replaced in the Sandbox with the actual path to the object in the operating system (for example,<notepad path> /A $sample).The command line length must not exceed 1024 characters, otherwise it will be shortened by Kaspersky Research Sandbox. Depending on the technical constraints of the operating system execution environment in the Sandbox, command line length may be further shortened.
This field is optional and available only when a Microsoft Windows or Linux execution environment is selected. Command line usage examples are described in the Appendices.
- To decrypt HTTPS traffic generated by the object during execution, select the Decrypt HTTPS check box.
If you chose a custom environment that has the Microsoft Windows XP SP3 x86 operating system installed, you can select the Decrypt HTTPS check box in the web interface. However, HTTPS traffic will not be decrypted during file execution.
HTTPS traffic decryption may decrease malware detection probability.
By default, the check box is selected.
- You can use Kaspersky Research Sandbox to browse the links in the documents that are opened in the Sandbox. To do this, select the Click document links check box.
The Click document links check box is available only if a Microsoft Windows based execution environment is selected. If you selected a custom execution environment based on Android or Linux, then the value of the Click document links parameter will be ignored during file execution.
Selecting this option can increase the detection level of malicious objects and their behavior.
This check box is cleared by default.
- If necessary, select the VNC access check box. VNC mode allows you to interact with the execution environment and samples during the detonation process.
If you select the VNC access check box, the following options become available:
- Launch automatically—Starts the sample automatically. This check box is selected by default.
- Disable clicker—Disables the utility that emulates a user. This check box is selected by default.
- You can generate a debug report for an executed file, which can be used for incident investigation by Kaspersky specialists. To do this, select the Create debug report check box. Diagnostic information about application performance is obtained separately.
Enabling this parameter requires additional free disk space to store object execution results.
This check box is cleared by default.
- In the Change file name and extension to field, you can specify another name and extension for the uploaded file. In this case, Kaspersky Research Sandbox attempts to execute the file according to the specified extension. Also, Kaspersky Research Sandbox determines the type of file after uploading to Sandbox, and processes the file accordingly. On the report page, the extension determined by Kaspersky Research Sandbox is displayed.
- If necessary, click the Reset button to reset options to default values.
Please note that added YARA file and Suricata rules file will not be removed. Use the
 button to remove the required rule file.
button to remove the required rule file. - Click the Start file execution button to start the file execution process.
Kaspersky Research Sandbox will display object execution results.
If an error occurs while uploading the object, you can try to upload the object again, or select another object.
If you terminate the uploading process for some reason, you can try to upload the same object again later or you can select another object.
An entry describing execution results appears in the History table. You can start to analyze results when the process completes and the Status field displays Completed.
- If necessary, click the rescan button
 to execute the previously uploaded and executed object, and repeat steps 2–5 of this procedure.
to execute the previously uploaded and executed object, and repeat steps 2–5 of this procedure.If the file is executed again later, results may differ from those in the History table for the same file. This is because Kaspersky expert systems update information about objects in real time. Execution results depend on the threat landscape.
Starting file execution
Page top