Key features of Kaspersky Next
Kaspersky Next benefits are divided into three main sections.
Ease of use
Simple, intuitive, cloud-based console
Kaspersky Next is managed from a simple cloud-based console. It's available anytime, from any location, and does not require an administrator's device to be located in the same network as the managed devices. When the administrator logs in to the console, a dedicated Getting started page provides straightforward steps for protecting company devices. This page also indicates whether the security setup has reached the Required level, which is adequate most of the time, and how to reach the Recommended level.
After a workspace is opened three times, the Information panel → Monitoring page is displayed when the console starts, instead of the Information panel → Getting started page.
Default preconfigured security profile
To save time setting up security, every Kaspersky Next workspace contains a default security profile (see the figure below). A workspace is configured to provide efficient protection for a typical environment. The default security profile is automatically applied on every device after it is connected to the Management Console component of Kaspersky Next. This design lets you save time on security configuration and provides out-of-the-box protection, even without the involvement of an administrator.
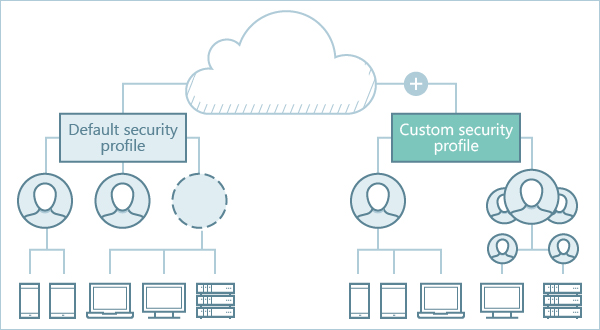
Default and custom security profiles
One security profile for all devices
Every security profile contains security settings for devices running Microsoft Windows, Apple macOS, Linux, Google Android, and Apple iOS and iPadOS. This arrangement allows you to set up and maintain a single security profile instead of five, assign the profile to users or user groups, and keep the security settings consistent for users.
Simple deployment
Because Kaspersky Next is managed through a browser, the only deployment required is that of security applications on corporate devices. This process consists of four easy steps:
- Enter the email addresses of employees, in Kaspersky Next.
- Send the employees an email message with instructions for installing security applications on their devices. The message contains links for downloading the applications.
- Make sure that employees install the applications on their devices.
- Match devices, which appear in the Devices section of Kaspersky Next Management Console, with users.
The email message that is generated and sent to employees by Kaspersky Next contains just one installation link. When an employee opens this link on a device, Kaspersky Next identifies the operating system and starts to download the correct installation package. This minimizes potential errors on the staff side.
Advanced security features
Some of the features mentioned in this section are available only if you activated Kaspersky Next under a Kaspersky Next EDR Optimum or XDR Expert license (please refer to the comparison of features for details).
Full set of endpoint protection features
The Kaspersky Endpoint Security components File Threat Protection, Mail Threat Protection, Network Threat Protection, and Web Threat Protection include technologies that shield users from malware, phishing, and other types of threats.
The Firewall component manages network activity and allows you to block potentially dangerous connections, such as remote desktop connections.
Protection against ransomware
Kaspersky Endpoint Security for Windows provides protection from ransomware for workstations running Windows operating systems and (starting from version 11) also protection from ransomware for file servers running Windows operating systems. The Kaspersky Endpoint Security components Behavior Detection, Exploit Prevention, and Remediation Engine monitor activity of applications on devices and block malicious actions.
Protection of mobile devices
In the corporate environment, mobile devices are becoming as important as wired computers: employees read corporate email, communicate with customers, and handle other crucial information. Kaspersky Next provides all core functionality for the protection and management of mobile devices, which includes the following:
- Password protection—Guards mobile devices against unauthorized access.
- Anti-theft protection for Android, iOS, and iPadOS devices—Protects a device from unauthorized access. If the device is lost or stolen, it can be locked remotely or all data can be wiped from it.
- Anti-malware protection for Android—Protects a device against infections in real time.
- Feature Control and Web Control—Help to ensure that mobile devices are used for corporate and not personal work.
Vulnerability Assessment and Patch Management
Vulnerability Assessment allows you to detect software vulnerabilities on your users' devices running Windows. Vulnerabilities are detected in the operating system and in applications made by Microsoft and third-party vendors.
Patch Management allows you to manage updates for the applications installed on your users' devices running Windows, including patches that fix software vulnerabilities detected on the devices.
Cloud security features
Some of the features mentioned in this section are available only if you activated Kaspersky Next under a Kaspersky Next EDR Optimum or XDR Expert license (please refer to the comparison of features for details).
Cloud Discovery
Cloud Discovery allows you to monitor the use of cloud services on managed devices running Windows and to block access to cloud services that you consider unwanted. Cloud Discovery tracks user attempts to gain access to these services through both browsers and desktop applications. This feature helps you to detect and halt the use of cloud services by shadow IT.
Data Discovery
Data Discovery detects critical information in files that are located in Microsoft 365 cloud storages. You can view the information about each detected file—its name, sharing type (private, within the company, or outside the company), and who edited it last.
Microsoft 365 protection
You can use your Kaspersky Next EDR Optimum or XDR Expert license to activate Kaspersky Security for Microsoft Office 365.
Kaspersky Security for Microsoft Office 365 protects your Microsoft 365 corporate email, file sharing, communication, and collaboration services against malware, phishing, spam, and other threats. The available number of mailboxes that you can protect is 1.5 times greater than the number of users in your license limit (rounded up to the nearest integer).
For information about how to work with Kaspersky Security for Microsoft Office 365, please refer to Kaspersky Security for Microsoft Office 365 Help.
Management capabilities
Some of the features mentioned in this section are available only if you activated Kaspersky Next under a Kaspersky Next EDR Optimum or XDR Expert license (please refer to the comparison of features for details).
Web Control
Web Control allows you to manage user actions on the internet, thus improving employee productivity by restricting or blocking access to specific web resources.
Device Control
Device Control ensures the security of confidential data by restricting user access to devices that might be connected to the computer.
Encryption Management
Encryption Management allows you to configure encryption of managed devices running Windows and macOS. Encryption prevents other users from gaining unauthorized access to data stored on the user's device.
Devices running Windows are encrypted by using BitLocker Drive Encryption. Devices running macOS are encrypted by using the FileVault disk encryption feature.
Root-Cause Analysis
Root-Cause Analysis allows you to detect and root out advanced attacks, perform root-cause analysis with a visualized threat development chain graph, and drill down to details for further review.
Endpoint Detection and Response
Endpoint Detection and Response monitors and analyzes threat progression, and provides you with information about possible attacks, to facilitate a timely manual response; or performs the predefined automated response.
Page top