Loading converted feeds into MISP
When the converter finishes processing the feeds, it creates a set of folders in the WORK_DIR folder specified during the installation. Each folder represents the MISP Feed corresponding to each feed from Kaspersky Threat Data Feeds.
To load those feeds into the MISP instance, go to Sync Actions > Feeds > Add Feed and specify all the required parameters for the feed being added:
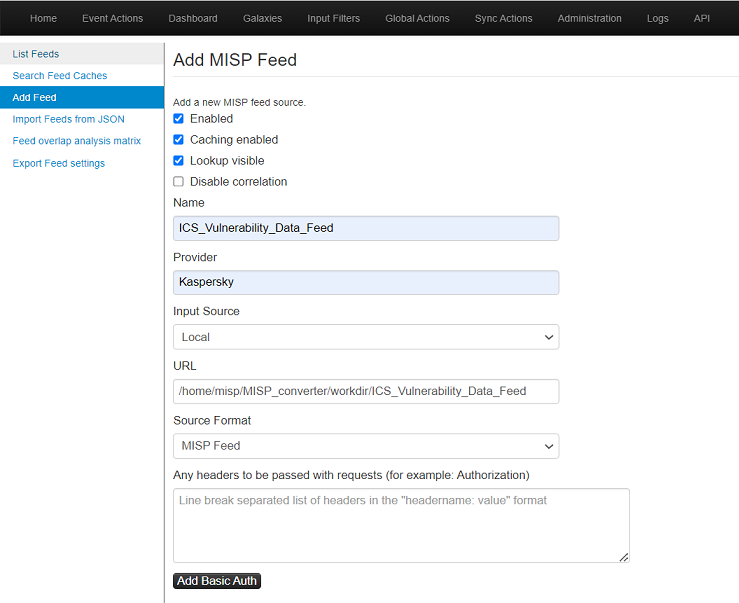
Loading feeds to MISP
Make sure that the user account that runs the MISP instance has access rights to the WORK_DIR directory so that the MISP instance can download the converted feeds.
After the feeds are added to the MISP instance, you should manually launch event fetching once by clicking the Fetch all events button in the MISP UI.
Fetching events
The initial event fetching may take several hours depending on the hardware configuration of the machine and MISP configuration (see below). Please refer to the MISP performance recommendations to get more information about the recommended settings.
Alternatively, you can use the MISP API. For example, you can use the curl utility:
curl --insecure -i -X POST -H "Authorization: %auth_key%" -H "Accept: application/json" -H "content-type: application/json" %misp_url%/feeds/fetchFromFeed/%feed_id%
In the above command, replace:
%auth_key%with the AUTH key of the MISP instance.%misp_url%with the URL or IP address of the MISP instance.%feed_id%with the feed identifier assigned to it by MISP. Feed identifiers are available in the MISP UI.
The --insecure parameter causes curl to establish insecure SSL connections. This may create security issues. Use it only for evaluation purposes.