Using MITRE techniques
For Kaspersky Threat Data Feeds that contain the mitre field, the events added to MISP are related to MITRE techniques.
According to the MISP documentation, the tags of the following format are created during conversion:
misp-galaxy:mitre-attack-pattern=\"%technique_name% - %technique_code%\",
Where:
%technique_name%is a name of MITRE technique.%technique_code%is a code of MITRE technique from the feed'smitrefield.
The value of the tag is obtained from the technics.py file of the distribution kit.
As of the date of release, the technics.py file contains a list of MITRE techniques corresponding to version 9 of the Attack Pattern galaxy.
If needed, any missing MITRE techniques can be manually added to the technics.py file.
To properly link an event to the MITRE techniques, ensure that MISP contains the galaxy named "Attack Pattern". If this galaxy is present, then the event page will display the used MITRE techniques.
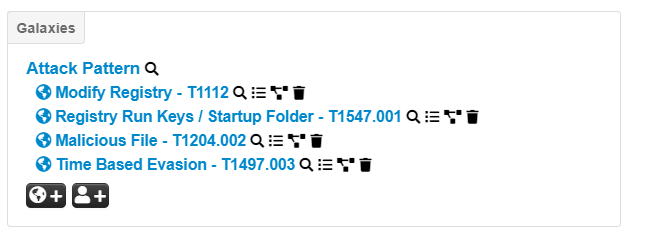
The used MITRE techniques displayed
The tags galaxy:mitre-attack-pattern will not be displayed in the list of the event tags.
If this galaxy is not present, then there will be no link to the galaxy, and the tags will be displayed in the list of the event tags.
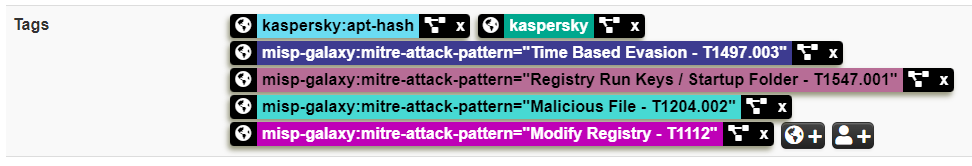
The tags displayed
For consistent linking with MITRE techniques, update the Attack Pattern galaxy before the initial download of the feed with the mitre field.
To update galaxies:
- In the MISP web interface, go to Galaxies > List Galaxies.
- Press the Update Galaxies button.