Data feeds from Kaspersky
This section describes Kaspersky Threat Intelligence Data Feeds.
First-tier security vendors and enterprises use long-established and authoritative Kaspersky Threat Intelligence Data Feeds to produce premium security solutions or to protect their businesses. Cyber attacks happen every day. Cyber threats are constantly growing in frequency, complexity and obfuscation, as they attempt to pierce your defenses. Adversaries currently use complicated intrusion kill chains, campaigns, and customized Tactics, Techniques and Procedures (TTPs) to disrupt your business or damage your clients.
Kaspersky offers continuously updated Threat Intelligence Data Feeds to inform your business or clients about risks and implications associated with cyber threats. The real-time updates help you to mitigate threats more effectively and defend against attacks even before they are launched.
Kaspersky Threat Feed App for ThreatConnect and security-sensitive information
No security-sensitive information (including any previously added indicators or search requests) is passed to Kaspersky as a result of using Kaspersky Threat Feed App for ThreatConnect.
Kaspersky Threat Feed App for ThreatConnect and temporary files
Kaspersky Threat Feed App for ThreatConnect does not control local storage for temporary files (feeds and certificate). Temporary files and their storage paths are managed on ThreatConnect platform.
Collection and processing of Kaspersky Threat Intelligence Data Feeds
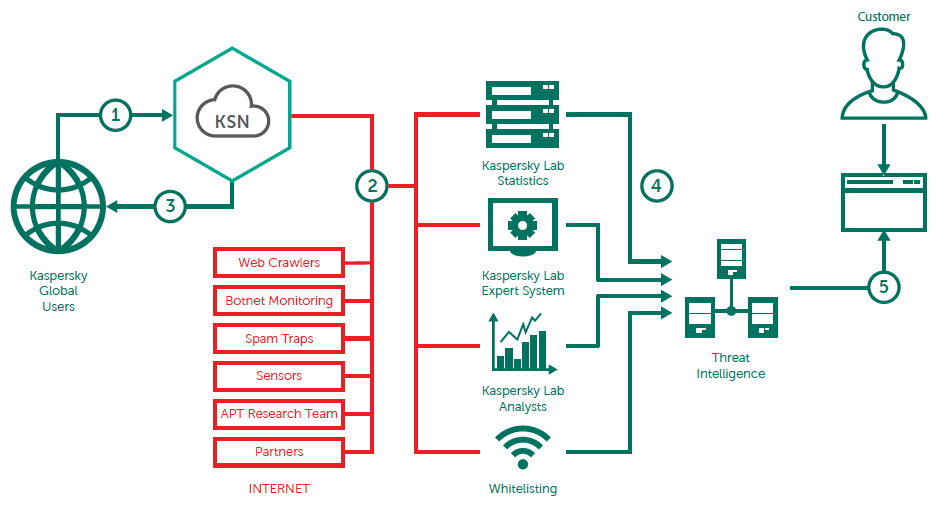
Collection and processing of Kaspersky Threat Intelligence Data Feeds
Data Feeds are aggregated from fused, heterogeneous, and highly reliable sources, such as Kaspersky Security Network and our own web crawlers, Botnet Monitoring service (24 / 7 / 365 monitoring of botnets and their targets and activities), spam traps, research teams, and partners. Then, in real-time, all the aggregated data is carefully inspected and refined using multiple preprocessing techniques, such as statistical criteria, Kaspersky Expert Systems (sandboxes, heuristics engines, multi-scanners, similarity tools, behavior profiling, and so on), analyst validation, and allowlisting verification.
About Kaspersky Threat Intelligence Data Feeds
Kaspersky Threat Intelligence Data Feeds contain information about threats and malicious objects.
The following data feeds are available:
- IP Reputation Data Feed — A set of IP addresses with context covering suspicious and malicious hosts.
- Ransomware URL Data Feed — A set of URLs and URL masks covering websites and web pages related to ransomware.
- Mobile Botnet Data Feed — A set of URLs with context covering mobile botnet C&C servers and related malicious objects.
- Malicious Hash Data Feed — A set of file hashes with corresponding context covering the most dangerous, prevalent, or emerging malware.
- Mobile Malicious Hash Data Feed — A set of file hashes with corresponding context for detecting malicious objects that infect mobile Google® Android™ and Apple® iPhone® devices.
- Malicious URL Exact Data Feed — A set of exact URLs with context covering malicious links and websites.
- Phishing URL Exact Data Feed — A set of exact URLs with context covering phishing links and websites.
- ICS Hash Data Feed — A set of hashes with corresponding context covering the malicious objects that are used to attack Industrial Control System infrastructure (ICS).
- IoT URL Data Feed — A set of URLs with corresponding context covering malware that infects IoT (Internet of Things) devices, such as IP cameras, routers, and dishwashers.
- APT Hash Data Feed — A set of hashes with corresponding context covering malicious artifacts used by APT (Advanced Persistent Threat) threat actors to conduct APT campaigns.
- APT IP Data Feed — A set of IP addresses with corresponding context that are a part of an infrastructure used in APT (Advanced Persistent Threat) campaigns.
- APT URL Data Feed — A set of URLs with corresponding context covering malicious links and websites that are a part of an infrastructure used in APT (Advanced Persistent Threat) campaigns.
- Vulnerability Data Feed — A set of hashes with corresponding context covering vulnerable software and related exploits.
- ICS Vulnerability Data Feed — A set of hashes with corresponding context covering vulnerable software and related exploits in both industrial control systems (ICS) and the commonly used IT systems integrated into ICS networks.
- Botnet C&C URL Exact Data Feed — A set of exact URLs and object hashes with context covering desktop botnet C&C servers and related malicious objects.
Malicious URL, Phishing URL, and Botnet C&C URL Data Feeds can also be used. However, it is recommended to use Malicious URL Exact (id=117), Phishing URL Exact (id=116), and Botnet C&C URL Exact (id=115) Data Feeds instead.
If your certificate is valid for an Exact and an ordinary version of the same feed, only the Exact version is processed. If your certificate is valid for ICS Vulnerability Data Feed and Vulnerability Data Feed, only ICS Vulnerability Dara Feed is processed.
Demo data feeds are also available. Demo feeds provide lower detection rates in comparison with their corresponding commercial versions. The following demo data feeds are available:
- Demo Botnet C&C URL Data Feed
This is a demo version of Botnet C&C URL Data Feed.
- Demo Malicious Hash Data Feed
This is a demo version of Malicious Hash Data Feed.
- Demo IP Reputation Data Feed
This is a demo version of IP Reputation Data Feed.
The following table features the correspondence between the data feeds, types of indicators added to ThreatConnect, and the tags.
Data feeds, indicator types, and tags
Data feed used |
ID |
Types of indicators added to ThreatConnect |
Assigned tags |
Feed fields used in tags |
IP Reputation Data Feed |
68 |
Address |
Kaspersky, IP_Reputation |
category, files/threat |
Ransomware URL Data Feed |
99 |
|
Kaspersky, Ransomware_URL |
files/threat |
Mobile Botnet Data Feed
|
139 |
|
Kaspersky, Mobile_Botnet |
category, threat |
Malicious Hash Data Feed |
66 |
File |
Kaspersky, Malicious_Hash |
threat, file_type |
Mobile Malicious Hash Data Feed |
67 |
File |
Kaspersky, Malicious_Hash |
threat |
Malicious URL Exact Data Feed
|
117 |
|
Kaspersky, Malicious_URL_Exact |
category, files/threat |
Phishing URL Exact Data Feed
|
116 |
|
Kaspersky, Phishing_URL_Exact |
industry |
ICS Hash Data Feed |
141 |
File |
Kaspersky, ICS_Hash |
file_type, threat |
IoT URL Data Feed |
126 |
|
Kaspersky, IOT_URL
|
files/threat |
APT Hash Data Feed |
89 |
File |
Kaspersky, APT_Hash |
- |
APT IP Data Feed |
90 |
Address |
Kaspersky, APT_IP |
- |
APT URL Data Feed
|
91 |
|
Kaspersky, APT_URL |
- |
Vulnerability Data Feed |
137 |
File |
Kaspersky, Vulnerability |
exploits/threat |
ICS Vulnerability Data Feed |
151 |
File |
Kaspersky, ICS_Vulnerability |
exploits/threat |
Botnet C&C URL Exact Data Feed
|
115 |
|
Kaspersky, Botnet_CnC_URL_Exact |
threat |
The indicators added to ThreatConnect contain Threat rating and Context.
Page top