About Kaspersky Security protection profiles
The following protection profiles are provided in Kaspersky Security policies:
- The main protection profile is automatically created when a policy is created. Although the main protection profile cannot be deleted, you can edit its settings.
- You can create additional protection profiles after creating a policy. Additional protection profiles let you flexibly configure different protection settings for different virtual machines within the protected infrastructure. A policy can contain multiple additional protection profiles.
You can configure the following File Threat Protection settings in protection profiles:
- Security level. You can select one of the preset security levels (High, Recommended, Low) or configure your own security level (Custom). The security level defines the following scan settings:
- Scanning of archives, self-unpacking archives, embedded OLE objects, and compound files
- Restriction on file scan duration
- List of objects to detect
- Action that Kaspersky Security performs after detecting infected files.
- Protection scope (scanning of network drives during protection of virtual machines).
- Exclusions from protection (by name, by file extension or full path, by file mask or path to the folder containing files to be skipped).
A protection profile can be assigned to an individual VMware virtual infrastructure object or to the root element of the protected infrastructure, which can include an Integration Server, for example (see the figure below).
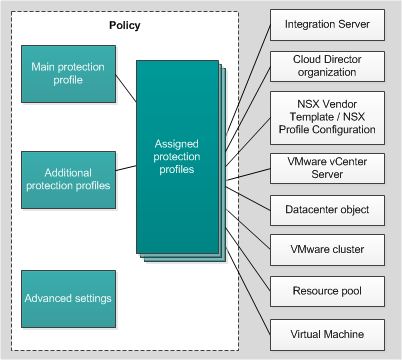
Protection profiles
By default, a protection profile assigned to the root element of a protected infrastructure is inherited by all child elements of the protected infrastructure (for example, by all VMware vCenter Servers to which the Integration Server connects). Protection profiles are also inherited according to the hierarchy of VMware virtual infrastructure objects: by default, the protection profile assigned to a virtual infrastructure object is inherited by all of its child objects, including by virtual machines. You can either assign a specific protection profile to a virtual machine, or let it inherit the protection profile that is used by its parent object.
In the main policy that defines protection settings for a virtual infrastructure managed by a single VMware vCenter Server, you can assign protection profiles to the virtual infrastructure objects either directly or by mapping protection profiles to NSX Vendor Templates or NSX Profile Configurations (depending on VMware NSX Manager type you use: VMware NSX-T Manager or VMware NSX-V Manager).
Only one protection profile may be assigned to a single virtual infrastructure object. Kaspersky Security protects virtual machines according to the settings that are specified in the protection profile assigned to these virtual machines.
Virtual infrastructure objects that have no assigned protection profile are excluded from protection.
If you exclude a virtual infrastructure object from protection, all child objects are also excluded from protection by default. You can indicate whether or not to exclude child objects that have been assigned their own protection profile.
Protection profile inheritance makes it possible to simultaneously assign identical protection settings to multiple virtual machines or exclude them from protection. For example, you can assign identical protection profiles to the virtual machines within a VMware cluster or resource pool.
Page top