Control of printing
You can use Control of printing to configure user access to local and network printers.
Local printer control
Kaspersky Endpoint Security allows configuring access to local printers on two levels: connecting and printing.
Kaspersky Endpoint Security controls local printer connection over the following buses: USB, Serial Port (COM), Parallel Port (LPT).
Kaspersky Endpoint Security controls the connection of local printers to COM and LPT ports only on the level of the bus. That is, to prevent the connection of printers to COM and LPT ports, you must prohibit the connection of all device types to COM and LPT buses. For printers connected to USB, the application exercises control on two levels: device type (local printers) and connection bus (USB). Therefore you can allow all device types except local printers to connect to USB.
You can select one of the following access modes to local printers via USB:
- Allow
 . Kaspersky Endpoint Security grants full access to local printers to all users. Users can connect printers and print documents using the means that the operating system provides.
. Kaspersky Endpoint Security grants full access to local printers to all users. Users can connect printers and print documents using the means that the operating system provides. - Block
 . Kaspersky Endpoint Security blocks the connection of local printers. The application allows connecting only trusted printers.
. Kaspersky Endpoint Security blocks the connection of local printers. The application allows connecting only trusted printers. - Depends on connection bus
 . Kaspersky Endpoint Security allows connecting to local printers in accordance with the USB bus connection status (Allow
. Kaspersky Endpoint Security allows connecting to local printers in accordance with the USB bus connection status (Allow  or Block
or Block  ).
). - By rules
 . To control printing, you must add printing rules. In the rules, you can select users or a group of users for which you want to allow or block access to printing documents on local printers.
. To control printing, you must add printing rules. In the rules, you can select users or a group of users for which you want to allow or block access to printing documents on local printers.
Network printer control
Kaspersky Endpoint Security allows configuring access to printing on network printers. You can select one of the following access modes to network printers:
- Allow and do not log. Kaspersky Endpoint Security does not control printing on network printers. The application allows access to printing on network printers to all users and does not save printing information in the event log.
- Allow
 . Kaspersky Endpoint Security grants access to printing on network printers to all users.
. Kaspersky Endpoint Security grants access to printing on network printers to all users. - Block
 . Kaspersky Endpoint Security restricts access to network printers for all users. The application allows access only to trusted printers.
. Kaspersky Endpoint Security restricts access to network printers for all users. The application allows access only to trusted printers. - By rules
 . Kaspersky Endpoint Security grants access to printing in accordance with printing rules. In the rules, you can select users or a group of users that will be allowed or prevented from printing documents on network printer.
. Kaspersky Endpoint Security grants access to printing in accordance with printing rules. In the rules, you can select users or a group of users that will be allowed or prevented from printing documents on network printer.
Adding printing rules for printers
How to add printing rules in the Administration Console (MMC)
- Open the Kaspersky Security Center Administration Console.
- In the console tree, select Policies.
- Select the necessary policy and double-click to open the policy properties.
- In the policy window, select Security Controls → Device Control.
- Under Device Control settings, select the Types of devices tab.
The table lists access rules for all devices that are present in the classification of the Device Control component.
- In the context menu for the Local printers and Network printers device types, configure the access mode for the relevant printers: Allow
 , Block
, Block  , Allow and do not log (for network printers only) or Depends on connection bus
, Allow and do not log (for network printers only) or Depends on connection bus  (for local printers only).
(for local printers only). - To configure printing rules on local and network printers, double-click the rule lists to open them.
- Select By rules as the printer access mode.
- Select the users or groups of users to which you want to apply the printing rule.
- Click Add.
This opens a window for adding a new printing rule.
- Assign a priority to the rule entry. A rule entry includes the following attributes: user account, action (allow/block), and priority.
A rule has a specific priority. If a user has been added to multiple groups, Kaspersky Endpoint Security regulates device access based on the rule with the highest priority. Kaspersky Endpoint Security allows to assign priority from 0 to 10,000. The higher the value, the higher the priority. In other words, an entry with the value of 0 has the lowest priority.
For example, you can grant read-only permissions to the Everyone group and grant read/write permissions to the administrators group. To do so, assign a priority of 1 for the administrators group and assign a priority of 0 for the Everyone group.
The priority of a block rule is higher than the priority of an allow rule. In other words, if a user has been added to multiple groups and the priority of all rules are the same, Kaspersky Endpoint Security regulates device access based on any existing block rule.
- Under Action, configure user access to printing on the printer.
- Click Users and groups and select users or groups of users for access to printing.
- Click OK.
- Save your changes.
How to add printing rules in Web Console and Cloud Console
- In the main window of the Web Console, select Devices → Policies & Profiles.
- Click the name of the Kaspersky Endpoint Security policy.
The policy properties window opens.
- Select the Application settings tab.
- Go to Security Controls → Device Control.
- In the Device Control Settings block, click the Access rules for devices and Wi-Fi networks link.
The table lists access rules for all devices that are present in the classification of the Device Control component.
- Select the Local printers or Network printers device type.
This opens the printer access rules.
- Configure the access mode for the relevant printers: Allow, Block, Allow and do not log (for network printers only), Depends on connection bus (for local printers only) or By rules.
- If you select the By rules mode, you must add printing rules for local or network printers. To do so, click the Add button in the printing rules table.
This opens the settings of the new printing rule.
- Assign a priority to the rule entry. A rule entry includes the following attributes: user account, action (allow/block), and priority.
A rule has a specific priority. If a user has been added to multiple groups, Kaspersky Endpoint Security regulates device access based on the rule with the highest priority. Kaspersky Endpoint Security allows to assign priority from 0 to 10,000. The higher the value, the higher the priority. In other words, an entry with the value of 0 has the lowest priority.
For example, you can grant read-only permissions to the Everyone group and grant read/write permissions to the administrators group. To do so, assign a priority of 1 for the administrators group and assign a priority of 0 for the Everyone group.
The priority of a block rule is higher than the priority of an allow rule. In other words, if a user has been added to multiple groups and the priority of all rules are the same, Kaspersky Endpoint Security regulates device access based on any existing block rule.
- Under Action, configure user access to printing on the printer.
- Under Users and groups, select users or groups of users for access to printing.
- Save your changes.
How to add printing rules in the application interface
- In the main application window, click the
 button.
button. - In the application settings window, select Security Controls → Device Control.
- In the Access settings block, click the Devices and Wi-Fi networks button.
The opened window shows access rules for all devices that are included in the Device Control component classification.
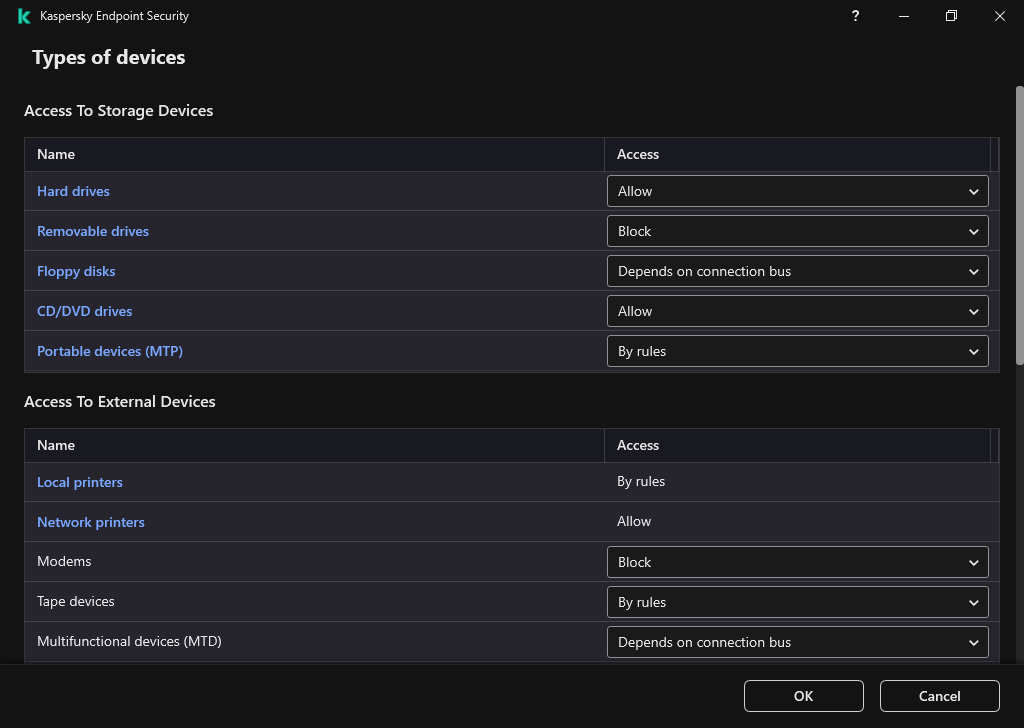
Types of devices in the Device Control component
- Under Access To External Devices, click Local printers or Network printers.
This opens a window with printer access rules.
- Under Access to local printers or Access to network printers configure the access mode for printers: Allow, Block, Allow and do not log (for network printers only), Depends on connection bus (for local printers only) or By rules.
- If you select the By rules mode, you must add printing rules for printers. Select the users or groups of users to which you want to apply the printing rule.
- Click Add.
This opens a window for adding a new printing rule.
- Assign a priority to the rule entry. A rule entry includes the following attributes: user account, permissions (allow/block), and priority.
A rule has a specific priority. If a user has been added to multiple groups, Kaspersky Endpoint Security regulates device access based on the rule with the highest priority. Kaspersky Endpoint Security allows to assign priority from 0 to 10,000. The higher the value, the higher the priority. In other words, an entry with the value of 0 has the lowest priority.
For example, you can grant read-only permissions to the Everyone group and grant read/write permissions to the administrators group. To do so, assign a priority of 1 for the administrators group and assign a priority of 0 for the Everyone group.
The priority of a block rule is higher than the priority of an allow rule. In other words, if a user has been added to multiple groups and the priority of all rules are the same, Kaspersky Endpoint Security regulates device access based on any existing block rule.
- Under Action, configure user permissions for access to printing.
- Under Users and groups, select users or groups of users for access to printing.
- Save your changes.
Trusted printers
Trusted devices are devices to which users that are specified in the trusted device settings have full access at all times.
The procedure for adding trusted printers is exactly the same as for other types of trusted devices. You can add local printers by ID or device model. You can only add network printers by device ID.
To add a trusted local printer by ID, you will need a unique ID (Hardware ID – HWID). You can find the ID in device properties by using operating system tools (see figure below). The Device Manager tool lets you do this. The ID of a local printer may look like this: 6&2D09F5AF&1&C000. Adding devices by ID is convenient if you want to add several specific devices. You can also use masks.
To add a trusted local printer by device model, you will need its Vendor ID (VID) and Product ID (PID). You can find the IDs in device properties by using operating system tools (see figure below). Template for entering the VID and PID: VID_04A9&PID_27FD. Adding devices by model is convenient if you use devices of a certain model in your organization. This way, you can add all devices of this model.
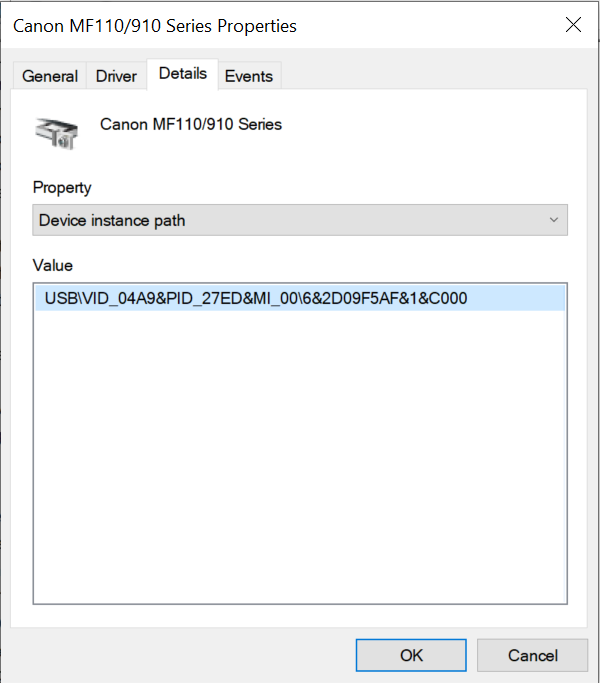
Device ID in Device Manager
To add a trusted network printer, you will need its device ID. For network printers, the device ID can be the network name of the printer (name of the shared printer), the IP address of the printer, or the URL of the printer.
Page top
 . Kaspersky Endpoint Security grants full access to local printers to all users. Users can connect printers and print documents using the means that the operating system provides.
. Kaspersky Endpoint Security grants full access to local printers to all users. Users can connect printers and print documents using the means that the operating system provides. . Kaspersky Endpoint Security blocks the connection of local printers. The application allows connecting only trusted printers.
. Kaspersky Endpoint Security blocks the connection of local printers. The application allows connecting only trusted printers. . Kaspersky Endpoint Security allows connecting to local printers in accordance with the USB bus connection status (Allow
. Kaspersky Endpoint Security allows connecting to local printers in accordance with the USB bus connection status (Allow  or Block
or Block  ).
). . To control printing, you must add printing rules. In the rules, you can select users or a group of users for which you want to allow or block access to printing documents on local printers.
. To control printing, you must add printing rules. In the rules, you can select users or a group of users for which you want to allow or block access to printing documents on local printers. . Kaspersky Endpoint Security grants access to printing on network printers to all users.
. Kaspersky Endpoint Security grants access to printing on network printers to all users. . Kaspersky Endpoint Security restricts access to network printers for all users. The application allows access only to trusted printers.
. Kaspersky Endpoint Security restricts access to network printers for all users. The application allows access only to trusted printers. . Kaspersky Endpoint Security grants access to printing in accordance with printing rules. In the rules, you can select users or a group of users that will be allowed or prevented from printing documents on network printer.
. Kaspersky Endpoint Security grants access to printing in accordance with printing rules. In the rules, you can select users or a group of users that will be allowed or prevented from printing documents on network printer.
