Integrating EDR Agent with KATA (EDR)
EDR Agent is installed on workstations and servers in the IT infrastructure of the organization. On these computers, EDR Agent continuously monitors processes, open network connections, and files being modified, and sends monitoring data to the server with the Central Node component.
To integrate with EDR (KATA), you must enable the Endpoint Detection and Response (KATA) component and configure EDR Agent.
The following conditions must be fulfilled for Endpoint Detection and Response (KATA) to work:
- Kaspersky Anti Targeted Attack Platform version 5.0 or higher.
- Kaspersky Security Center version 14.2 or higher. In earlier versions of Kaspersky Security Center, it is impossible to activate the Endpoint Detection and Response (KATA) feature.
Integration with Endpoint Detection and Response (KATA) involves the following steps:
- Activating Endpoint Detection and Response (KATA)
You need to purchase a separate license for EDR (KATA) (Kaspersky Endpoint Detection and Response (KATA) Add-on).
The functionality becomes available after adding a separate key for Kaspersky Endpoint Detection and Response (KATA). Licensing for the stand-alone Endpoint Detection and Response (KATA) functionality is the same as the licensing of Kaspersky Endpoint Security.
Make sure that the EDR (KATA) functionality is included in the license and is running in the local interface of the application.
- Connecting to Central Node
Kaspersky Anti Targeted Attack Platform requires establishing a trusted connection between Kaspersky Endpoint Security and the Central Node component. To configure a trusted connection, you must use a TLS certificate. You can get a TLS certificate in the Kaspersky Anti Targeted Attack Platform console (see instructions in the Kaspersky Anti Targeted Attack Platform Help). Then you must add the TLS certificate to Kaspersky Endpoint Security (see instructions below).
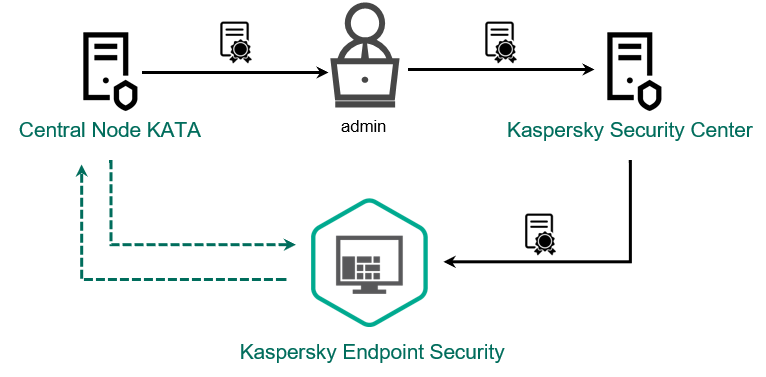
Adding a TLS certificate to Kaspersky Endpoint Security
By default, Kaspersky Endpoint Security only checks the TLS certificate of Central Node. To make the connection more secure, you can additionally enable the verification of the computer on Central Node (two-way authentication). To enable this verification, you must turn on two-way authentication in Central Node and Kaspersky Endpoint Security settings. To use two-way authentication, you will also need a crypto-container. A crypto-container is a PFX archive with a certificate and a private key. You can get a crypto-container in the Kaspersky Anti Targeted Attack Platform console (see instructions in the Kaspersky Anti Targeted Attack Platform Help).
How to connect a Kaspersky Endpoint Security computer to Central Node using the Web Console
As a result, the computer is added on the Kaspersky Anti Targeted Attack Platform console. Check the operating status of the component by viewing the Report on status of application components. You can also view the operating status of a component in reports in the local interface of Kaspersky Endpoint Security. The Endpoint Detection and Response Expert (on-premise) component will be added to the list of Kaspersky Endpoint Security components.
 .
.