Configuring trust group rights
The optimal application rights are created for different trust groups by default. The settings of rights for application groups that are in a trust group inherit values from the settings of the trust group rights.
How to change trust group rights in the Administration Console (MMC)
- Open the Kaspersky Security Center Administration Console.
- In the console tree, select Policies.
- Select the necessary policy and double-click to open the policy properties.
- In the policy window, select Advanced Threat Protection → Host Intrusion Prevention.
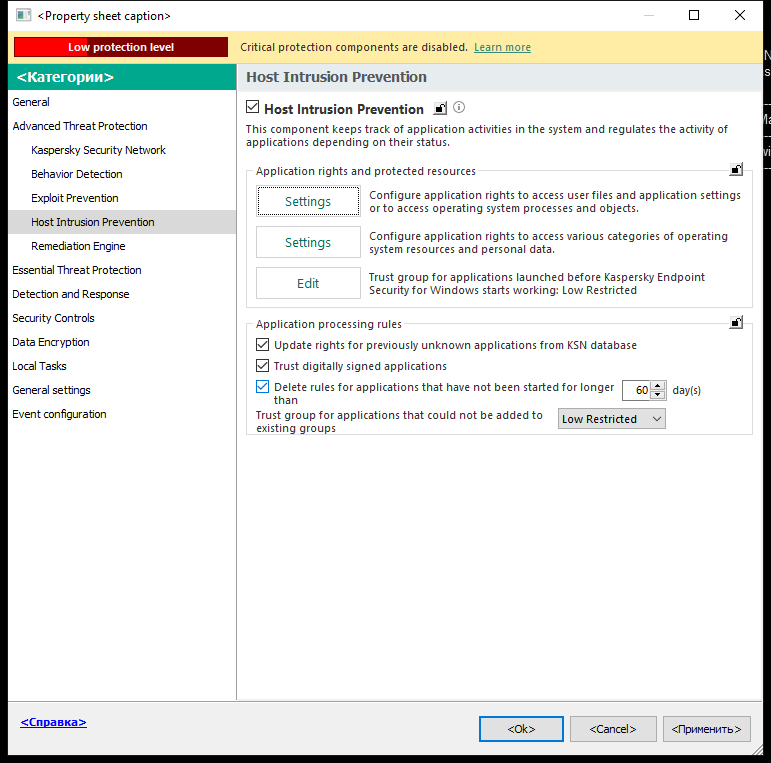
Intrusion Prevention settings
- In the Application rights and protected resources block, click the Settings button.
This opens the application rights configuration window and the list of protected resources.
- Select the Application rights tab.
- Select the necessary trust group.
- In the context menu of the trust group, select Group rights.
This opens the trust group properties.
- Do one of the following:
- If you want to edit trust group rights that regulate operations with the operating system registry, user files, and application settings, select the Files and system registry tab.
- If you want to edit trust group rights that regulate access to operating system processes and objects, select the Rights tab.
Network activity of applications is controlled by the Firewall using network rules.
- For the relevant resource, in the column of the corresponding action, right-click to open the context menu and select the necessary option: Inherit, Allow (
 ) or Block (
) or Block ( ).
). - If you want to monitor the use of computer resources, select Log events (
 /
/  ).
).Kaspersky Endpoint Security will record information about the operation of the Host Intrusion Prevention component. Reports contain information about operations with computer resources performed by the application (allowed or forbidden). Reports also contain information about the applications that utilize each resource.
- Save your changes.
How to change trust group rights in the Web Console and Cloud Console
- In the main window of the Web Console, select Devices → Policies & Profiles.
- Click the name of the Kaspersky Endpoint Security policy.
The policy properties window opens.
- Select the Application settings tab.
- Go to Advanced Threat Protection → Host Intrusion Prevention.
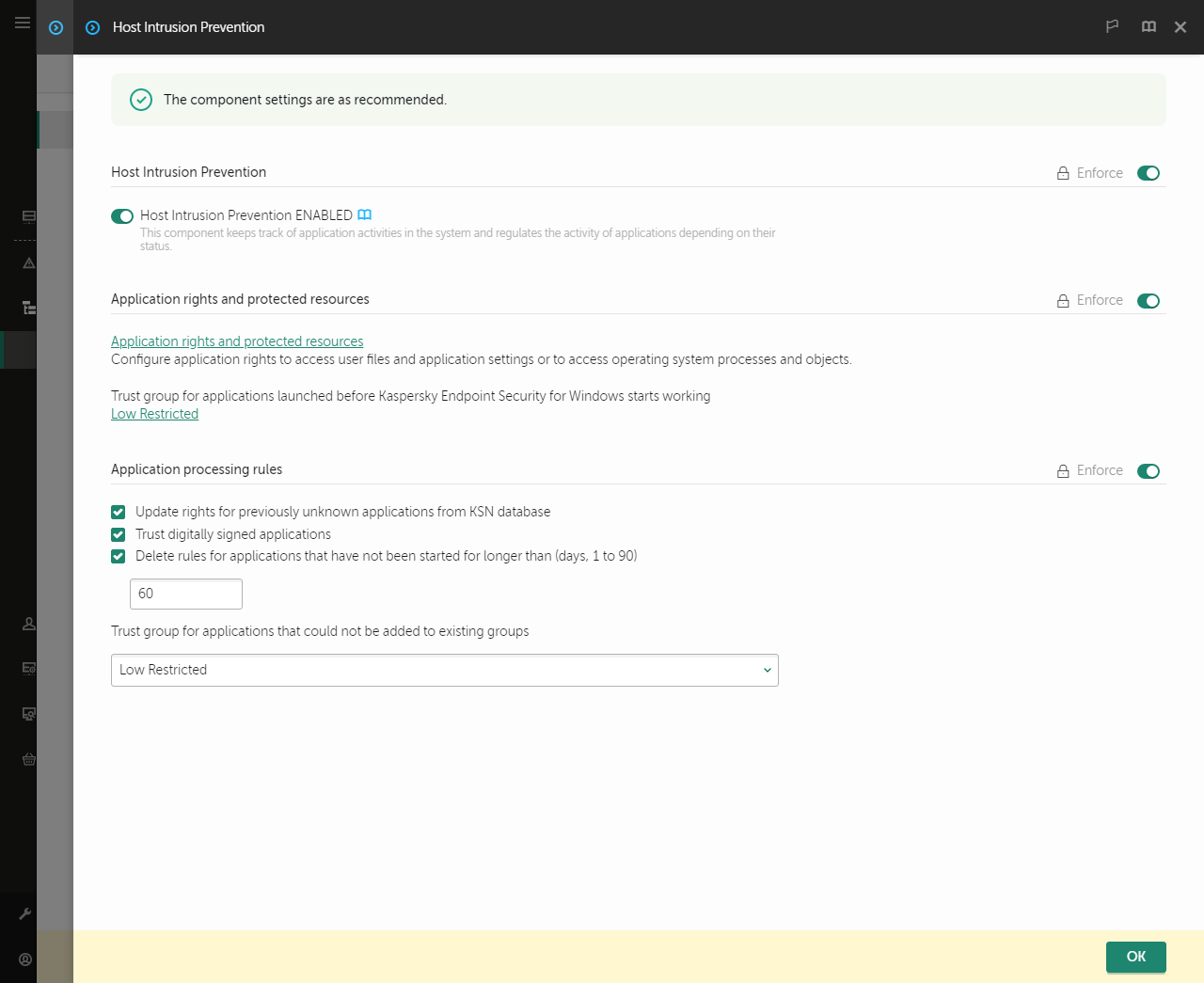
Intrusion Prevention settings
- In the Application rights and protected resources block, click the Application rights and protected resources link.
This opens the application rights configuration window and the list of protected resources.
- Select the Application rights tab.
You will see a list of trust groups on the left side of the window and their properties on the right side.
- In the left part of the window, select the relevant trust group.
- In the right part of the window, in the drop-down list, do one of the following:
- If you want to edit trust group rights that regulate operations with the operating system registry, user files, and application settings, select Files and system registry.
- If you want to edit trust group rights that regulate access to operating system processes and objects, select Rights.
Network activity of applications is controlled by the Firewall using network rules.
- For the relevant resource, in the column of the corresponding action, select the necessary option: Inherit, Allow (
 ), Block (
), Block ( ).
). - If you want to monitor the use of computer resources, select Log events (
 /
/  ).
).Kaspersky Endpoint Security will record information about the operation of the Host Intrusion Prevention component. Reports contain information about operations with computer resources performed by the application (allowed or forbidden). Reports also contain information about the applications that utilize each resource.
- Save your changes.
How to change trust group rights in the application interface
- In the main application window, click the
 button.
button. - In the application settings window, select Advanced Threat Protection → Host Intrusion Prevention.
- Click Manage applications.
This opens the list of installed applications.
- Select the necessary trust group.
- In the context menu of the trust group, select Details and rules.
This opens the trust group properties.
- Do one of the following:
- If you want to edit trust group rights that regulate operations with the operating system registry, user files, and application settings, select the Files and system registry tab.
- If you want to edit trust group rights that regulate access to operating system processes and objects, select the Rights tab.
Network activity of applications is controlled by the Firewall using network rules.
- For the relevant resource, in the column of the corresponding action, right-click to open the context menu and select the necessary option: Inherit, Allow (
 ), Deny (
), Deny ( ).
). - If you want to monitor the use of computer resources, select Log events (
 ).
).Kaspersky Endpoint Security will record information about the operation of the Host Intrusion Prevention component. Reports contain information about operations with computer resources performed by the application (allowed or forbidden). Reports also contain information about the applications that utilize each resource.
- Save your changes.
The trust group rights will be changed. Kaspersky Endpoint Security will then block the actions of the application depending on the trust group. The ![]() status (Custom settings) will be assigned to the trust group.
status (Custom settings) will be assigned to the trust group.